
Major Cyber Attacks in Review: January 2024
As January 2024 dawned, the digital atmosphere braced itself for another year’s cybersecurity challenges. Throughout the month, organizations experienced a number of noteworthy cyber incidents, showcasing the ever-present threat landscape.
In this blog post, we are going to glance at the key cybersecurity events that marked January 2024, their significance, and the lessons they can provide us about securing our digital future.
Additionally, we highly encourage you to check out our recent blog post on Cybersecurity Predictions for the current year. Drawing insights from Fortinet’s report and referencing key occurrences from 2023 that caught our eye, the article offers a glimpse into the threat landscape of 2024, providing valuable context for envisioning the cybersecurity challenges that lie ahead.
PJ&A Breach Impacted Therapy Provider and Millions of Patients

Concentra Health Services, a Texas-based therapy provider, disclosed a data breach impacting nearly 4 million patients due to a hack targeting medical transcriber Perry Johnson & Associates (PJ&A).
The breach compromised personal data, including names, birthdates, addresses, medical records, and, in some cases, Social Security numbers and clinical information.
The incident, reported to the U.S. Department of Health and Human Services, affected at least 14 million individuals across various clients. Furthermore, it spurred numerous lawsuits against PJ&A and its clients, alleging negligence in data security.
Hackers find medical transcription firms like PJ&A appealing due to the vast volume of detailed patient data they handle and historically weak security measures. Healthcare organizations are advised to prioritize cybersecurity policies for such business associates to mitigate breach risks.
Akira Claimed Theft of 110GB Data from UK Cosmetics Giant Lush
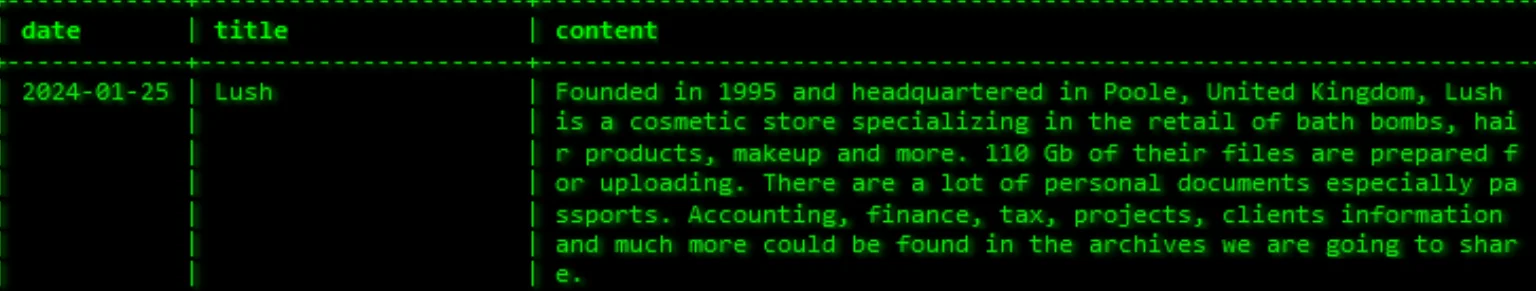
Akira’s victim listing for Lush
In January 2024, Akira claimed to have stolen 110 GB of data from Lush, a UK-based global cosmetics brand. The data comprises company documents pertaining to accounting, finances, tax, projects, and clients, and threat actors have threatened to disclose it publicly.
Furthermore, the stolen data allegedly contains numerous personal documents, including passport scans which Lush collects for identity verification during its hiring process. This suggests that Akira’s affiliate may have had access to a system containing staff-related information.
There is currently no evidence indicating exposure of customer data.
Whether Lush’s systems were encrypted remains unclear; the Akira gang mostly engages in extortion-only schemes. Nonetheless, there have been no evident disruptions to Lush’s operations, suggesting that encryption may not be a significant factor in this incident.
15 Million Trello Account Information Exposed

On January 16, a threat actor posted a Trello database on a hacker forum, containing 15,115,516 entries, including emails, usernames, full names, and other account details from Trello.com. The threat actor intended to sell this data to a single buyer via Telegram.
While the majority of the data in the database can be obtained from public sources, the associated email addresses should have been private information.
It was later revealed that a publicly exposed API was utilized to link email addresses with public Trello profiles. Trello provides a REST API for its integration into applications, and one of the API endpoints allows developers to request public information about a profile using users’ Trello ID or username.
However, the threat actor behind the database post discovered that querying this API endpoint with an email address also fetched associated account details. They compiled a list of millions of email addresses to check for associations, leading to the creation of the leaked Trello database.
16.6 Million Customers’ Data Compromised in loanDepot Ransomware Incident
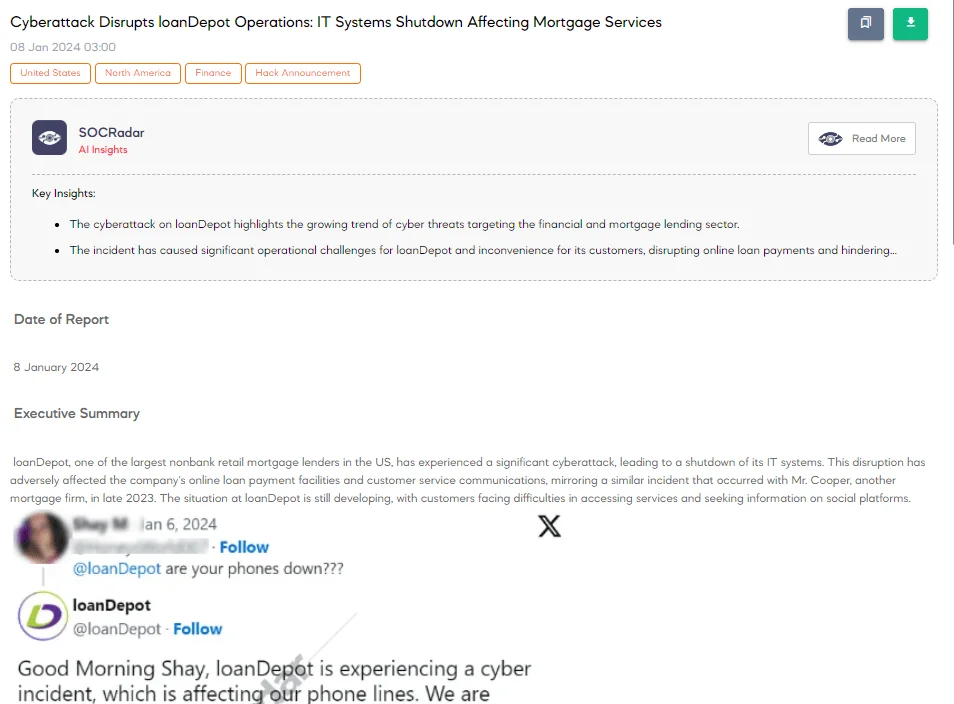
Cyberattack on loanDepot (SOCRadar Dark Web News)
In January 2024, a cyberattack targeted loanDepot, compromising the sensitive personal data of approximately 16.6 million customers. The attack is labeled as a ransomware incident.
Details regarding the specific customer data stolen were not disclosed by loanDepot. Despite efforts to restore some customer portals, several online services remained inaccessible into the second week following the attack. By this time, affected customers reported difficulties making payments or accessing their online accounts since the incident unfolded around January 8. Despite that, loanDepot reported progress in swiftly restoring systems and resuming normal business operations.
Ransomware Striked VF Corp.: Breach Compromised Data of 35.5 Million Customers

In December, a cyberattack targeted VF Corp. the parent company of brands like Vans, Supreme, and The North Face, leading to the compromise of the personal data of 35.5 million customers. The specific data stolen remains undisclosed. However, the company emphasized it does not include sensitive customer data such as social security numbers, bank details, and payment card information; there is also no evidence suggesting password theft.
Previous acknowledgments from VF Corp. hinted at operational disruptions possibly linked to a ransomware attack. Subsequently, the cybercriminal group ALPHV, also known as BlackCat, claimed responsibility for the breach.
Ukrainian Man Arrested for Operating 1 Million Virtual Servers, Amassing $2 Million Through Cryptojacking

Authorities apprehended a 29-year-old man in Ukraine, accused of orchestrating a large-scale cryptojacking operation, amassing $2 million in cryptocurrency through 1 million virtual servers created from hacked accounts.
Europol disclosed the suspect’s arrest, labeling him the alleged mastermind behind a large-scale scheme, which exploits cloud computing resources for crypto-mining.
The investigation unfolded after a cloud service provider reported compromised accounts in January 2023. Europol, collaborating with Ukrainian law enforcement and the provider, collected operational intelligence to track and identify the hacker.
With administrative access from the compromised accounts, the perpetrator spawned over a million virtual computers for crypto mining. Ukrainian officials confirmed the suspect’s use of TON cryptocurrency wallets to funnel the illegal proceeds, tallying approximately $2 million.
On January 9, 2024, authorities seized computer equipment, bank cards, SIM cards, electronic media, and other evidence of the activity. The suspect’s cyber activities were found to date back to 2021, when he automated password-cracking tools to breach 1,500 accounts of a global e-commerce subsidiary, although the specific entity remains unidentified.
Hathway Data Breach Exposed Millions of User Accounts
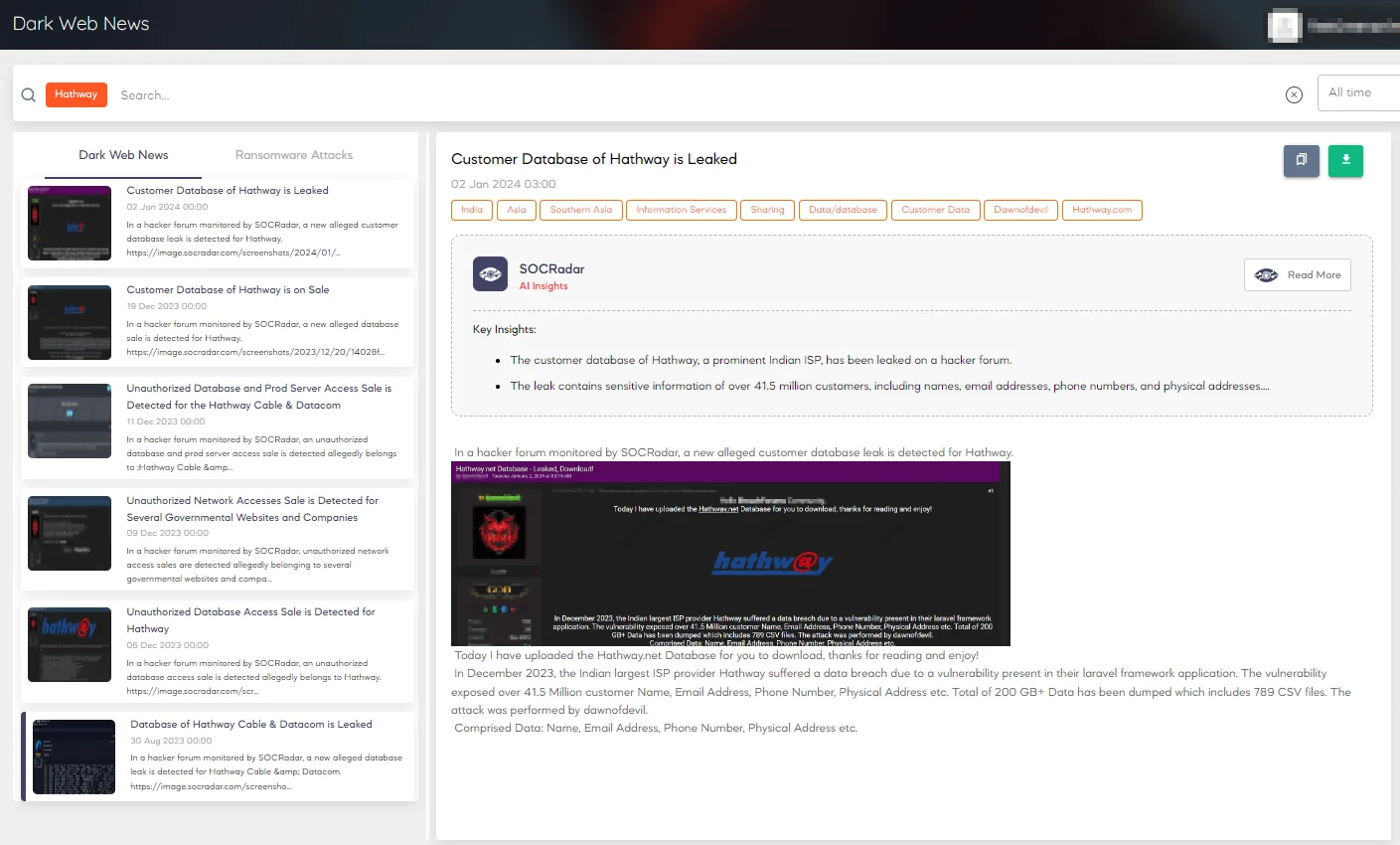
Hathway breaches on SOCRadar Dark Web News
A threat actor, named ‘dawnofdevil,’ orchestrated a data breach targeting Hathway, a prominent Indian ISP, in December 2023, exploiting vulnerabilities in their Laravel framework.
The threat actor attempted to sell the data for $10,000 before leaking it on Breach Forums. The breach exposed the data including names, email addresses, phone numbers, and KYC (Know Your Customer) details. They later developed a dark web search engine, allowing potential victims to check if their data was affected.
Eliminating the duplicates, the initial count of compromised user accounts revealed 4 million unique records.
Users are warned against phishing attempts related to the incident but reassured that passwords were not included in the leak.
SEC’s Cyber Breach Through SIM Swapping Triggered Bitcoin Price Surge
The U.S. Securities and Exchange Commission (SEC), the very institution entrusted with overseeing financial markets and protecting investors, faced a cyber breach.
On January 9, an unauthorized party accessed SEC’s official account on X (Twitter). The attacker behind the breach made a deceitful announcement, falsely claiming SEC approval for the first-ever spot Bitcoin Exchange-Traded Funds (ETFs). This led to Bitcoin prices surging to nearly $48,000 from a daily low of just above $45,000, before plummeting below $46,000 when the SEC clarified no such approval was granted.
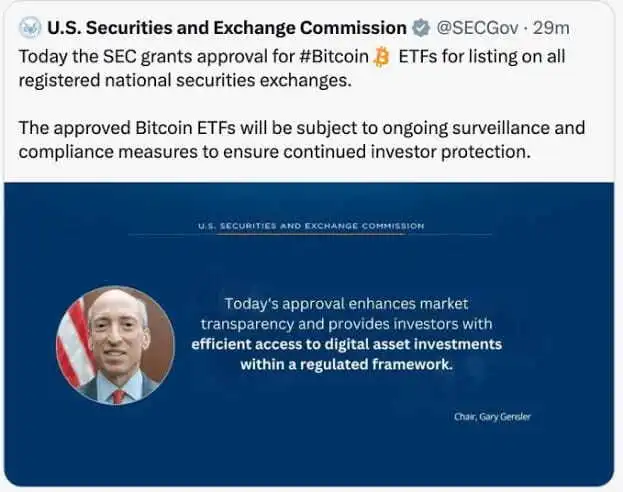
Following investigations, it was found that the unauthorized party gained control of SEC’s cell phone number associated with the compromised account through a “SIM swap” attack.
You can find more details about the dangers of SIM swapping attacks and the specific incident that affected SEC through our blog post: What is SIM Swapping?
Cross Switch Breach Led to Compromise of 3.6 Million Users’ Personal Data
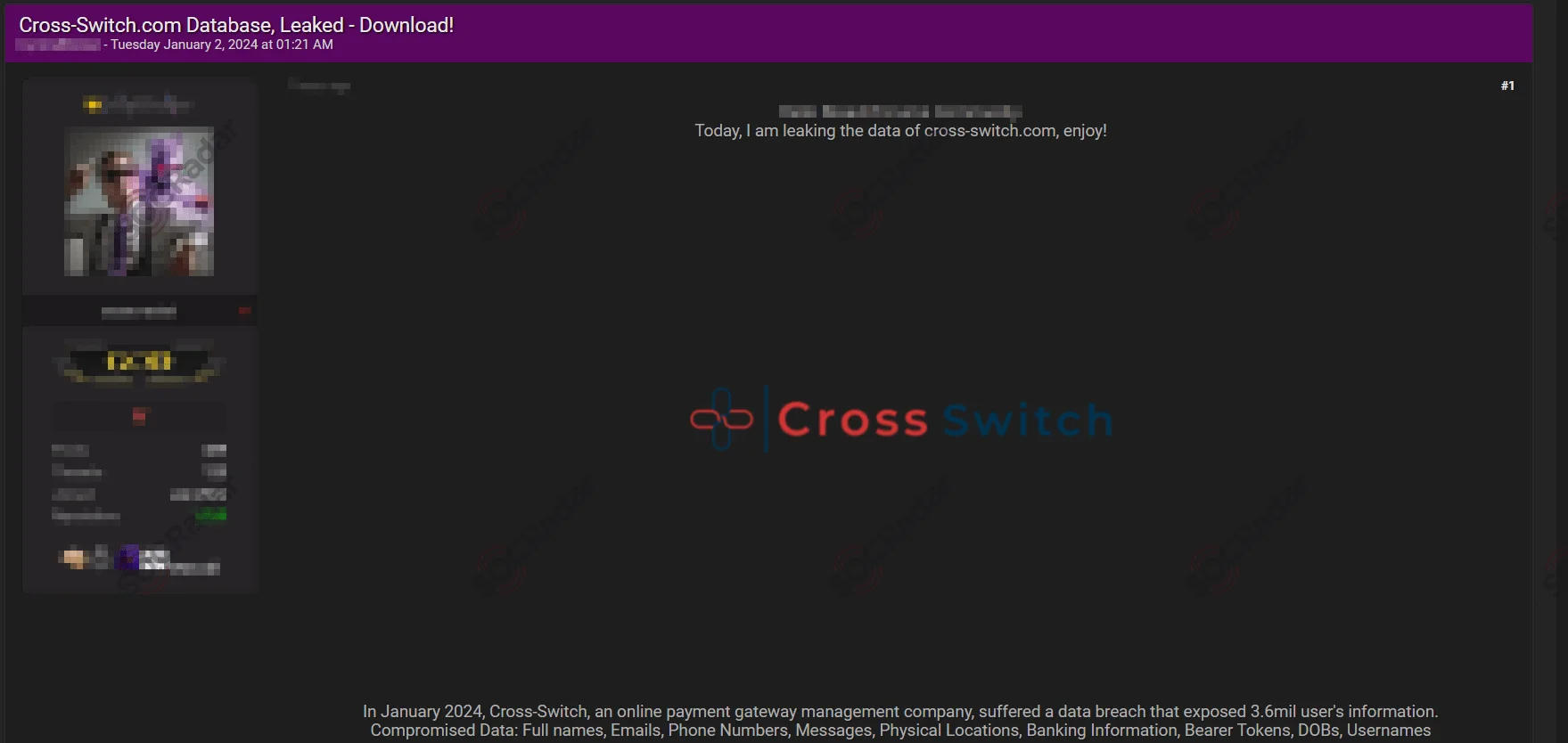
Cross-Switch database leak post (SOCRadar Dark Web News)
Cross Switch, an online payment gateway management platform, faced fallout from a significant data breach allegedly orchestrated by a threat actor called ‘IntelBroker’, who compromised the personal details of 3.6 million users.
IntelBroker disclosed the breach on forums, sparking concerns about cybersecurity and user privacy. Exposed information includes names, usernames, phone numbers, banking details, emails, locations, and dates of birth.
Elevate Your Cybersecurity Defense with SOCRadar XTI
SOCRadar Extended Threat Intelligence (XTI) employs advanced monitoring algorithms to track threat actors, malware, vulnerabilities, and associated trends, providing real-time insights.
Combining asset monitoring, alerts, and actionable intelligence provided by SOCRadar, organizations can effectively prevent cyber threats and strengthen their defenses.
SOCRadar’s Alarm Management – Get alerted to critical security events with SOCRadar XTI.
Sign up for SOCRadar Freemium to stay vigilant against evolving threats and strengthen your security posture.



































