
Major Cyber Attacks in Review: January 2025
In January 2025, high-profile cyber incidents affecting industries ranging from healthcare and telecommunications to AI and finance made headlines.
From the breach at Community Health Center (CHC) exposing over a million patient records to the ransomware attack on New York Blood Center Enterprises (NYBCe), the healthcare sector remained a primary target. Meanwhile, AI platform DeepSeek faced multiple cyber threats, including a large-scale DDoS attack and exposed databases, while cryptocurrency exchange Phemex lost $69 million in a suspected cyber heist.
Other major breaches included the alleged theft of millions of TalkTalk customer records, PowerSchool’s massive data compromise, and Otelier’s exposure of hotel guest reservations. This article examines the biggest cybersecurity incidents of January 2025, their implications, and what organizations can learn from these attacks.
CHC Data Breach Exposed Over One Million Patients’ Information
Community Health Center, Inc. (CHC) experienced a significant data breach, compromising the personal information of over one million individuals. The breach was identified on January 2, 2025, after CHC detected unusual activity on its network, prompting an investigation by security experts.

CHC Data Breach Exposed Over One Million Patients’ Information
The investigation revealed that a skilled attacker had infiltrated CHC’s systems and accessed or exfiltrated sensitive patient records. The compromised data included names, addresses, birthdates, Social Security numbers (SSNs), phone numbers, email addresses, test results, diagnosis details, treatment information, and health insurance records. The breach impacted both current and former patients, as well as individuals who received COVID-19 tests or vaccines at CHC clinics.
CHC confirmed that ransomware was not deployed in the attack and that data was not deleted, allowing the organization to continue its daily operations. The healthcare provider stated that the attacker’s access was halted within hours, and no ongoing threats remain.
CHC has not disclosed details about the attacker’s identity or potential extortion attempts, and no ransomware group has publicly claimed responsibility for the breach.
NYBCe Ransomware Attack Disrupted Blood Center Operations
In January 2025, a ransomware attack targeting New York Blood Center Enterprises (NYBCe) forced the organization to take certain IT systems offline. The attack impacted blood donation centers that supply more than 400 hospitals nationwide, potentially delaying processing times and requiring rescheduling of some donation activities.
The breach was detected when NYBCe identified suspicious activity on its IT systems. In response, the organization engaged third-party cybersecurity experts to investigate and restore its systems while also notifying law enforcement. Despite the disruption, NYBCe continued accepting blood donations and worked closely with hospitals to implement workarounds and fulfill orders.
SOCRadar’s Supply Chain Intelligence monitors third-party companies and tracks their exposure levels, assessing the risk they may pose to your organization.
The attack highlights ongoing cybersecurity risks in the healthcare sector, where ransomware incidents have been escalating, often causing severe operational disruptions. The organization has not disclosed the full extent of the attack or a timeline for system restoration.
DeepSeek Faced Cyber Attacks, Data Exposure, and Malware Threats
Chinese AI platform DeepSeek experienced multiple cybersecurity incidents, gaining significant attention in January 2025, disrupting operations and raising concerns over data security. The company first faced a large-scale cyberattack, likely a Distributed Denial-of-Service (DDoS) attack, forcing it to disable new registrations on its DeepSeek-V3 chat platform.
Shortly after, researchers discovered that DeepSeek had left two critical databases exposed online, potentially compromising over a million log entries containing user chats. While DeepSeek promptly secured the databases after disclosure, it remains unclear whether malicious actors had accessed the sensitive information before the fix.
Adding to the threats, cybersecurity researchers identified two malicious Python packages, “deepseeek” and “deepseekai,” on the Python Package Index (PyPI). These packages masqueraded as legitimate DeepSeek tools but instead functioned as infostealers. Despite swift removal from PyPI, over 200 developers had already downloaded the compromised packages.
DeepSeek’s rapid rise has made it a prime target for cyber threats, illustrating the risks AI platforms face as they gain global prominence.
Phemex Lost $69 Million in Suspected Cyber Attack
Cryptocurrency platform Phemex suffered a major security breach, resulting in the theft of over $69 million in digital assets. The incident led to a temporary pause in platform operations as the company worked to assess the damage and restore services.
Blockchain security firms first detected suspicious transactions, with Cyvers identifying an initial $29 million outflow, while PeckShield later confirmed the total losses exceeded $69 million, including Ethereum (ETH), Bitcoin (BTC), and Binance Coin (BNB). Phemex CEO Federico Variola acknowledged the breach, stating that restoring withdrawals was a priority and that manual reviews of transactions would be conducted to ensure security.

Phemex Lost $69 Million in Suspected Cyber Attack
The company did not provide details on the nature of the attack or the identity of the threat actor but assured users that a snapshot of account balances had been taken to facilitate future compensation.
Alleged Data Breach of 18.8 Million TalkTalk Customers
U.K. telecom giant TalkTalk launched an investigation into a potential data breach after a hacker, using the alias “b0nd,” claimed to have stolen the personal data of over 18.8 million current and former customers. The stolen information, allegedly offered for sale on a cybercrime forum, included names, email addresses, IP addresses, phone numbers, and subscriber PINs.
TalkTalk disputed the hacker’s claim, stating that the reported figure was “wholly inaccurate and very significantly overstated,” noting that the company currently has around 2.4 million customers. The breach was linked to a third-party supplier, later identified as CSG’s Ascendon platform, which TalkTalk uses for subscription management.
CSG acknowledged that an external party had gained unauthorized access to a provider’s data on its platform but asserted that its own systems were not compromised. TalkTalk confirmed that no billing or financial information was affected.
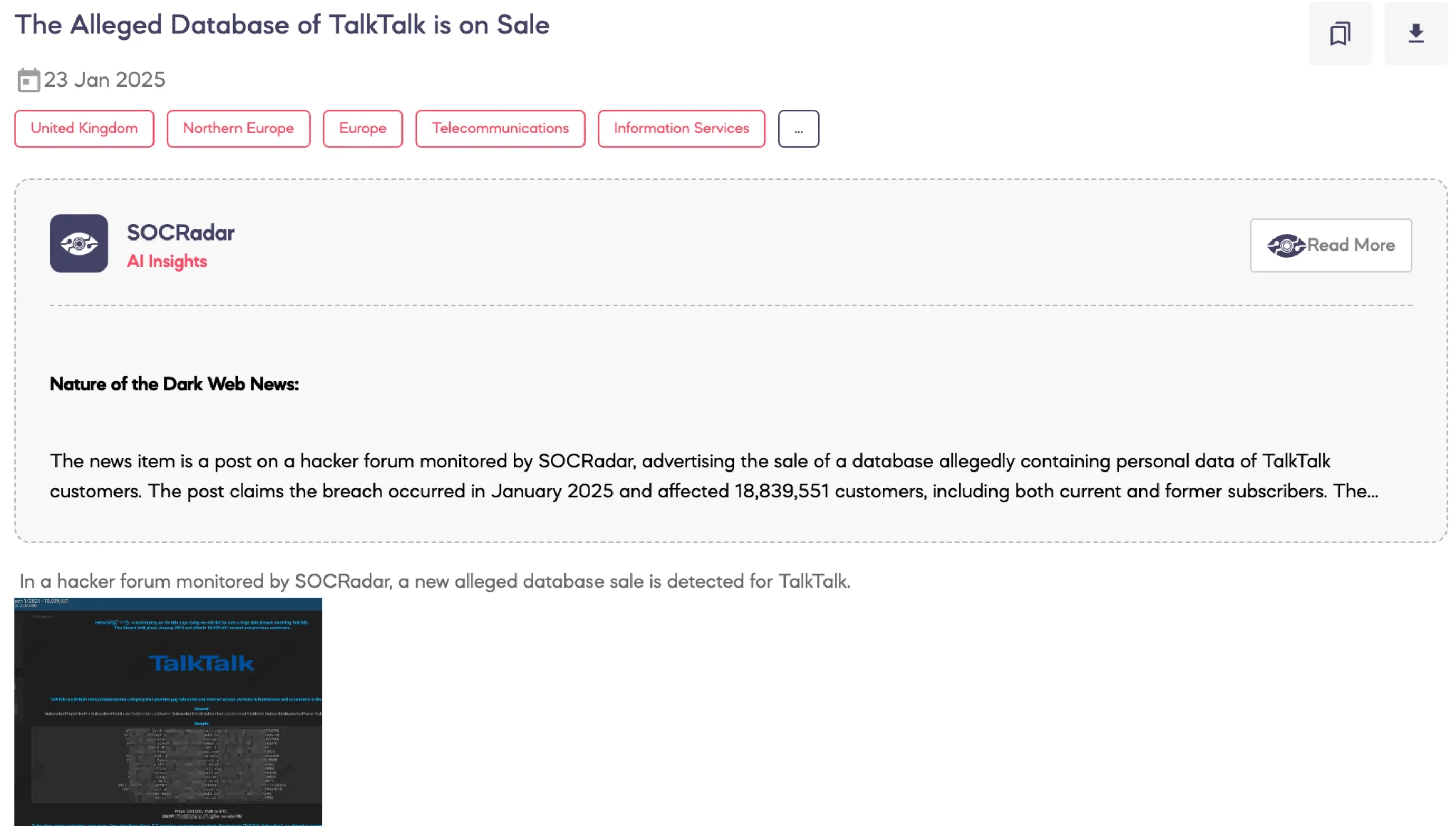
Initial Dark Web post alert regarding the alleged TalkTalk breach (SOCRadar Dark Web News)
PowerSchool Data Breach Impacted Over 62 Million Students
Education technology provider PowerSchool suffered a massive data breach after a hacker used stolen credentials to infiltrate its customer support portal. The attacker leveraged a maintenance access tool to extract student and teacher data from PowerSIS databases, ultimately claiming to have stolen information on 62.4 million students and 9.5 million teachers across 6,505 school districts.
The breach, disclosed by PowerSchool on January 7, exposed varying types of personal data depending on district policies, with some records including Social Security numbers (SSNs), medical details, and academic information. In response to the breach, PowerSchool opted to pay a ransom to prevent the public release of the stolen data after viewing evidence of its deletion by the threat actor.
While PowerSchool has acknowledged the breach in a private customer FAQ, it has not publicly confirmed the exact number of affected individuals, frustrating parents, educators, and administrators seeking clarity.

PowerSchool Data Breach Impacted Over 62 Million Students (Source)
Despite these efforts, the breach underscores how cloud-based platforms holding vast amounts of sensitive data remain prime targets for cybercriminals.
Cloudflare Blocked Record-Breaking 5.6 Tbps DDoS Attack
Cloudflare successfully detected and mitigated a massive 5.6 Terabit per second (Tbps) distributed Denial-of-Service (DDoS) attack, marking the largest attack ever reported. The attack occurred on October 29, 2024, targeting an unnamed Internet Service Provider (ISP) in Eastern Asia.
The attack, originating from a Mirai-variant botnet, lasted just 80 seconds but involved over 13,000 compromised IoT devices. On average, 5,500 unique source IP addresses participated per second, each contributing approximately 1 Gbps of traffic.
This incident surpassed the previous record for the largest volumetric DDoS attack, which Cloudflare had also reported earlier in October 2024, peaking at 3.8 Tbps.
Otelier Breach Exposed Millions of Hotel Guest Records
Hotel management platform Otelier suffered a major data breach after attackers infiltrated its Amazon S3 cloud storage, compromising personal details and reservations of millions of guests from major hotel brands, including Marriott, Hilton, and Hyatt. The breach, active from July to October 2024, led to the theft of 7.8 TB of data.
Attackers gained access using stolen credentials obtained via malware, breaching Otelier’s Atlassian server and leveraging internal support tickets to extract further credentials. This granted them access to sensitive S3 buckets containing guest reservations, transactions, employee emails, and financial reports.
Otelier confirmed the breach, stating it engaged cybersecurity experts, disabled affected accounts, and strengthened security measures. Marriott suspended automated services with Otelier pending the investigation but emphasized that its own systems remained secure.
Security researchers found at least 1.3 million unique email addresses in the stolen data. While no passwords or payment information were exposed, potential phishing attacks could target affected individuals.
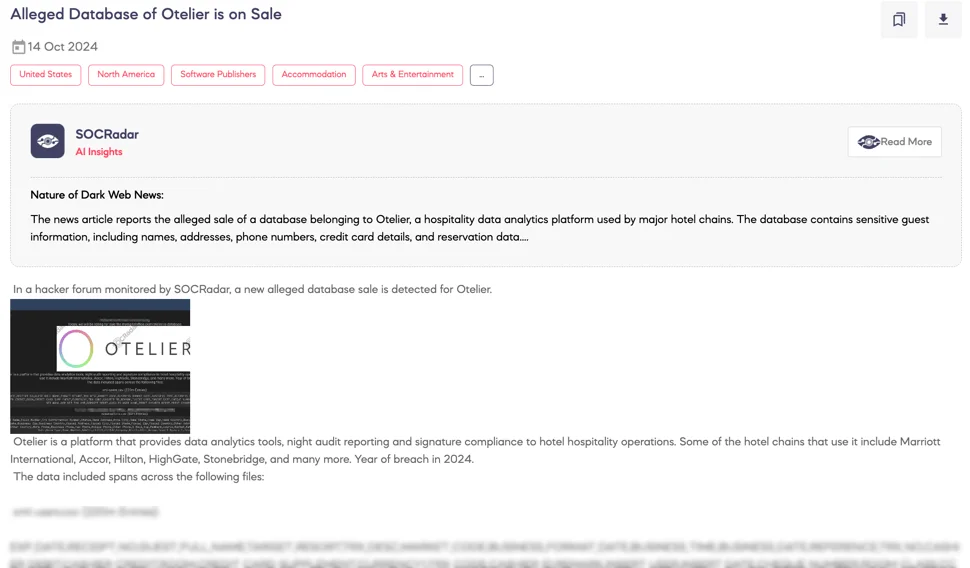
Alleged database of Otelier is on sale (SOCRadar Dark Web News)
Wolf Haldenstein Data Breach Exposed 3.4 Million Individuals’ Personal Information
Law firm Wolf Haldenstein Adler Freeman & Herz LLP suffered a data breach in December 2023, exposing the personal information of more than 3.4 million individuals. The breach was discovered on December 13, 2023, after suspicious network activity was detected, prompting an investigation with third-party cybersecurity experts.
By January 2, 2024, the firm confirmed that an unauthorized actor had accessed sensitive files. The compromised data included names, Social Security numbers (SSNs), employee identification numbers, medical diagnoses, and medical claim details. While the affected individuals span multiple states, official notifications were filed with attorneys general in Maine, Texas, and Vermont.
Despite identifying some victims by December 2024, the firm was unable to locate addresses for direct notification, delaying alerts for nearly a year. To mitigate potential risks, Wolf Haldenstein implemented stronger data privacy measures and offered complimentary credit monitoring services. However, there is no evidence that the stolen data has been misused, and the identity of the threat actor remains unknown.

Wolf Haldenstein Data Breach Exposed 3.4 Million Individuals’ Personal Information
Suspected Rostelecom Data Breach by Silent Crow
Russian telecommunications provider Rostelecom launched an investigation into a suspected cyber attack after the hacker group Silent Crow claimed to have leaked its customer data. The group published a data dump allegedly containing thousands of customer emails and phone numbers stolen from Rostelecom.
The breach reportedly targeted a contractor responsible for maintaining Rostelecom’s corporate website and procurement portal. While the company stated that an initial review found no evidence of highly sensitive personal data being leaked, it advised users of the affected websites to reset passwords and enable Two-Factor Authentication (2FA) as a precaution.

Suspected Rostelecom Data Breach by Silent Crow
Russia’s Ministry of Digital Development confirmed that the incident did not impact the state services portal or expose sensitive subscriber data. Silent Crow, an emerging hacker group that does not appear to demand ransoms, has previously claimed responsibility for attacks on Russian government agencies. However, its origins and motives remain unclear.
Proactively Manage Cybersecurity Risks with SOCRadar’s Integrated Tools
Mitigate your organization’s risk with SOCRadar’s comprehensive Vulnerability Intelligence and Attack Surface Management (ASM) modules. Continuously monitor your digital ecosystem, from internal networks to third-party vendors, and uncover vulnerabilities across your entire attack surface.
SOCRadar’s Attack Surface Management (ASM) module
SOCRadar provides up-to-the-minute insights into exploitable weaknesses, empowering your security team to prioritize and address risks before they can be weaponized. Through ASM, gain full visibility into your digital assets and proactively manage exposure to emerging threats. Strengthen your security framework with SOCRadar’s unified approach to risk management.






































