
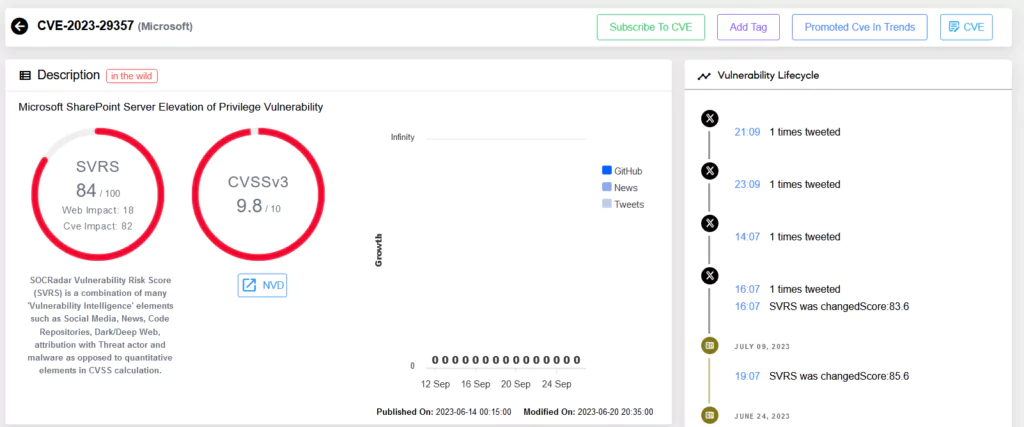
Microsoft SharePoint Server Elevation of Privilege Vulnerability Exploit (CVE-2023-29357)
[Update] January 11, 2024: “SharePoint Vulnerability Has Been Added to the KEV Catalog by CISA”
[Update] September 29, 2023: See the subheading: “Proof-of-Concept Exploit Is Available for SharePoint Server Vulnerability (CVE-2023-29357).”
In June 2023, Microsoft released a patch for a critical elevation of privilege vulnerability in SharePoint, identified as CVE-2023-29357. An attacker exploiting this flaw could gain administrator-level privileges without requiring any prior authentication. The vulnerability permits attackers to spoof JWT authentication tokens, enabling them to execute a network attack, bypassing authentication processes, and accessing privileges of an authenticated user. It is imperative to note that this does not necessitate any interaction from the user.
From Discovery to Exploitation: The SharePoint Pre-Auth RCE Chain
A StarLabs researcher, Nguyễn Tiến Giang, unveiled a thorough analysis of a compound exploit chain targeting SharePoint during the Pwn2Own Vancouver 2023 event. The chain involves two key vulnerabilities:
- Authentication Bypass: A sinister attacker can impersonate any SharePoint user by generating valid JWTs and utilizing the ‘none’ signing algorithm. This tactic effectively sidesteps signature validation checks when verifying JWT tokens during OAuth authentication processes.
- Code Injection: SharePoint users possessing ‘Owners’ permissions can inject arbitrary code. Specifically, they can replace the /BusinessDataMetadataCatalog/BDCMetadata.bdcm file, causing the injected code to compile into an assembly executed by SharePoint subsequently.
The primary challenge, however, was leveraging the Authentication Bypass flaw to access only the SharePoint API, then identifying a post-auth RCE chain via this AP
Exploit in the Wild
A public exploit script for the SharePoint vulnerability has recently been released on GitHub. The script is designed to exploit CVE-2023-29357, allowing attackers to elevate privileges on affected SharePoint Server installations. Moreover, malicious actors could chain this with another RCE vulnerability to severely compromise a system’s confidentiality, integrity, and availability.
To offer a broader perspective, the GitHub exploit script facilitates:
- User Impersonation: This lets attackers execute arbitrary code as the SharePoint application, potentially causing a denial of service (DoS).
- Detailed Outputs: The script reveals admin users with elevated privileges and can function in both single and mass exploit modes.
However, it is crucial to emphasize that the script is designed for educational purposes, legal testing, and ethical use only.
Affected Versions: Is Your SharePoint at Risk?
The vulnerabilities, particularly CVE-2023-29357, directly affect SharePoint Server 2019. The tested version, where the exploit chain was proven successful, was SharePoint 2019 (version 16.0.10396.20000). Additionally, the tests incorporated the March 2023 patches (KB5002358 and KB5002357).
Defensive Measures
For organizations running SharePoint Server, especially version 2019, immediate action is vital. Microsoft recommends installing all security updates related to the software in use. The first patch addressing this vulnerability can be accessed here.
While patching was the primary and most recommended means of protection against this vulnerability, Microsoft had also highlighted some mitigating factors that can be of assistance:
- AMSI Integration and Microsoft Defender: Microsoft reports that customers who have activated the AMSI (Antimalware Scan Interface) integration feature and employ Microsoft Defender across their SharePoint Server farms are safeguarded against this vulnerability. This security layer offers another level of protection. For those interested in implementing AMSI with their SharePoint Server, a step-by-step guide can be found on Microsoft’s official documentation: Configure AMSI integration with SharePoint Server.
With the exploit now publicly accessible, the likelihood of malicious entities leveraging it has substantially increased. Prompt implementation of the recommended patches and mitigations is crucial to curbing potential security infringements and data breaches.
Proof-of-Concept Exploit Is Available for SharePoint Server Vulnerability (CVE-2023-29357)
A Proof-of-Concept (PoC) exploit script for the CVE-2023-29357 vulnerability has been released. The script enables the execution of arbitrary code within the SharePoint application pool and SharePoint server farm account. It can reveal the details of admin users with elevated privileges, such as Title, Email, NameId, and NameIdIssuer. It is noted that the script can operate in both single and mass exploit modes.
Although the script’s focus is on privilege elevation, an attacker can potentially chain the exploit for the CVE-2023-29357 vulnerability with CVE-2023–24955 (SharePoint Server Remote Code Execution vulnerability) to compromise the target system’s integrity, availability, and confidentiality.
The usage specifics of the script to replicate the vulnerability can be found on GitHub.
Furthermore, on a Twitter post, a user shared failed exploit attempts related to the CVE-2023-29357 vulnerability.
IIS log GET /_api/web/siteusers - 443 - x.x.x.x python-requests/2.28.1 - 401 0 0 544 GET /_api/web/siteusers/web/siteusers - 443 - x.x.x.x python-requests/2.28.1 - 401 0 0 72 GET /_api/web/siteusers - 443 - x.x.x.x python-requests/2.28.1 - 401 0 0 591
This log entry indicates that three “GET” requests were made to different URIs under the path “/_api/web/siteusers” from the same client IP address (it has been redacted as x.x.x.x). They were made by a Python script, using the requests library. All three requests appear to have resulted in a “401 Unauthorized” response, suggesting that access to these resources was denied.
PoC Released for SharePoint Server Exploit Chain (CVE-2023-29357 and CVE-2023-24955)
STAR Labs researcher Nguyễn Tiến Giang (Jang) previously revealed an exploit chain exploiting Microsoft SharePoint Server vulnerabilities, CVE-2023-29357 and CVE-2023-24955, enabling Remote Code Execution (RCE). Jang detailed the process in a blog post, emphasizing the year-long research and effort invested. (A video demonstration showcasing the exploit chain is accessible on YouTube.)
On December 15, Jang announced via Twitter that Microsoft had finally responded to their email, granting permission to share more details about the SharePoint vulnerabilities used in Pwn2Own Vancouver 2023. The PoC exploit code is now publicly available on GitHub.
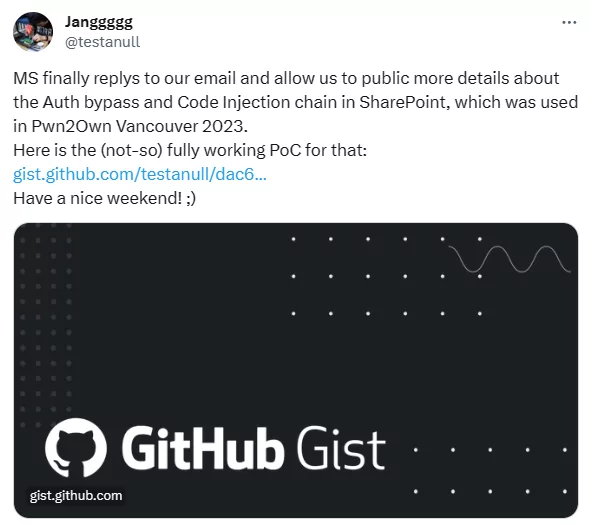
The exploitation steps for the first vulnerability (CVE-2023-29357) outline the actions an attacker could take, such as impersonating any user, identifying site admins, and eventually performing actions with escalated privileges. Importantly, the second vulnerability (CVE-2023-24955) necessitates an authenticated site owner for exploitation. Thereby, the exploitation of CVE-2023-29357 serves as the initial access point for a potential attacker who wants to exploit CVE-2023-24955 in the SharePoint API to achieve RCE.
It is important to note that the shared PoC does not directly enable RCE. However, threat actors could potentially modify it for use in attacks.
SharePoint Vulnerability Has Been Added to the KEV Catalog by CISA
CISA has included the SharePoint Server Privilege Escalation vulnerability, CVE-2023-29357, in its Known Exploited Vulnerabilities (KEV) Catalog due to confirmed instances of active exploitation. Emphasizing the critical nature of such vulnerabilities as common targets for threat actors, the agency urges organizations to apply the necessary patch by January 31, 2024.
Conclusion: Leveraging SOCRadar Vulnerability Intelligence
In this dynamic digital era, vulnerabilities can emerge from any corner. That’s where platforms like SOCRadar’s Vulnerability Intelligence come into play. With real-time monitoring, analysis, and updates on various vulnerabilities and threats, organizations can stay one step ahead, ensuring the safety and security of their digital infrastructure.
Always remember, awareness combined with timely action can be the best defense against any cyber threat.




































