What’s MITRE PRE-ATT&CK and How To Use It in Threat Intelligence?
Founded in 1958, MITRE is a non-profit company whose mission is to solve the problem of a safer world. A new curated knowledge base, known as MITRE ATT&CK, which stands for adversarial tactics, techniques, and common knowledge is a platform that organizes and categorizes tactics, techniques, and procedures (TTPs) used by threat actors in the digital world to help organizations identify gaps in their cyber defenses.
MITRE ATT&CK can provide actionable information that helps decision-makers to customize their defenses, give them a threat-focused understanding, and facilitates the prioritization of resources and plans an organization’s cybersecurity program.
The ATT&CK Matrix for Enterprises describes what an attacker normally does when infiltrating a corporate network. The information collected during an attack is presented in the form of a matrix of TTPs as well as information about the tactics, techniques, and procedures of the attacker.
These techniques represent the various ways in which a cyber attacker can achieve goals, goals, and tactics. It can provide a comprehensive solution to prevent and mitigate cybersecurity threats. By combining these two solutions, an organization’s defenses can be improved by counteracting enemy actions at all stages of the attack lifecycle.
The information in the ATT&CK matrix is part of a continuously updated collection of data to understand various methods of cybersecurity. MITRE has joined forces in its ongoing cybersecurity work and was originally developed for internal project deployment. It includes information about cybercriminals who use various attack techniques, tactics, techniques, and procedures of cyber attackers.
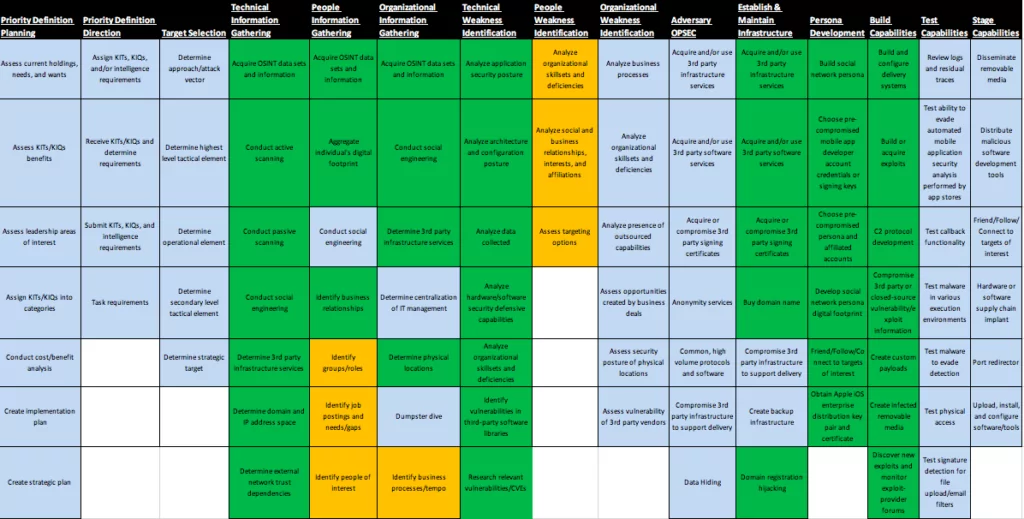
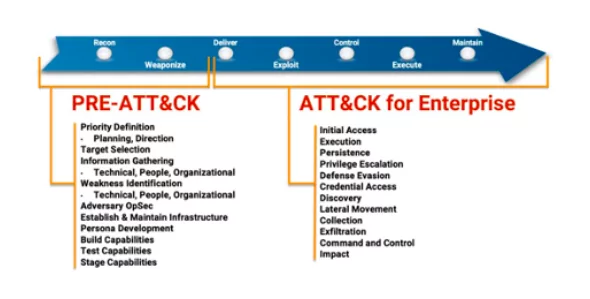
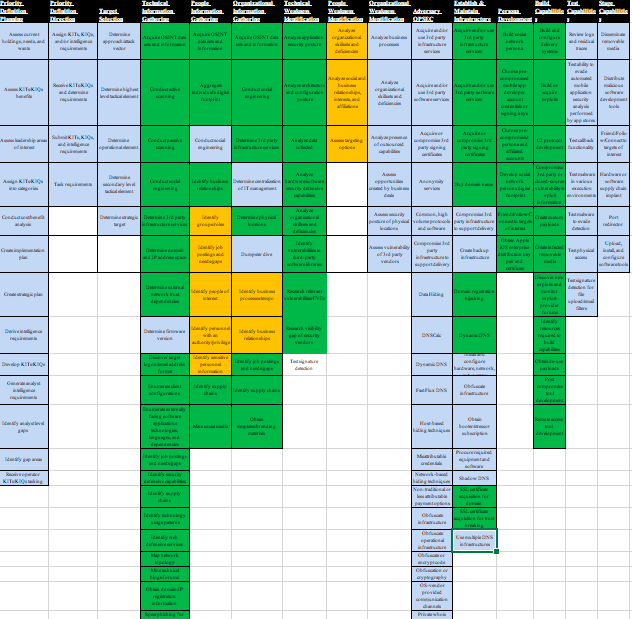
Building on ATT&CK, PRE-ATT&CK provides the ability to prevent an attack before the adversary has a chance to get in. The 15 tactic categories for PRE-ATT&CK was derived from the first two stages (recon and weaponize) of a seven-stage Cyber Attack Lifecycle (aka Lockheed Martin’s Cyber Kill Chain) as shown in figure 1.
Cyber attackers target organizations by using information available on the Internet and their third party relationships.
For this reason, cyber defenders should identify and track actions that are outside the boundaries of their businesses.
PRE-ATT&CK captures the tactics, techniques, and procedures used by competitors to select a target, gain information and launch a campaign, by providing the structure and breadth required for advocates to track attackers’ behavior and evaluate their data on adversaries’ activities.
PRE-ATT&CK provides defenders with the ability to answer questions such as:
- Are there signs that the adversary might be targeting you?
- What commonly used techniques does the adversary use against you?
- How should you prioritize cyber threat intelligence data acquisitions and analytics to gain additional insights to “see” the adversary before the exploit occurs?
ATT&CK and PRE-ATT&CK comparison
PRE-ATT&CK is associated with ATT&CK since it adopts the same model structure and complements ATT&CK by focusing on the left of exploit stages of the Cyber Attack Lifecycle. PRE-ATT&CK and ATT&CK have several fundamental differences, namely:
ATT&CK is tightly coupled to a specific enterprise network (e.g., Microsoft Windows, Linux, or mobility environment) and therefore provides detailed technical information relative to the adversary actions and defender mitigations for each technique. PRE-ATT&CK is agnostic to these differences since the adversary can operate across any of these environments for their pre-compromise preparation activities.
The mitigations in ATT&CK can be very specific and effective. PRE-ATT&CK mitigations are under development and will encompass technical and policy-based mitigations. In many cases, these mitigations will not be as precise or comprehensive given the inability to fully capture all adversary activities, data, and tools.
While many of the ATT&CK mitigations required increased endpoint monitoring, PRE-ATT&CK largely requires additional data sources to obtain information about adversarial objectives and activities.
In summary, MITRE ATT&CK is a high-performance open-source tool for understanding and classifying tactics, techniques, and procedures of cyber attackers. It enables cyber-defense teams to assess risks, prioritize and address vulnerabilities in cyber defenses, and design security controls against likely threats using tactics and techniques. There you will see data that provides information about malware associated with the use of techniques by cyber attackers.
SOCRadar with PRE-ATT&CK
For a comprehensive and ideal security plan, the entire life cycle of the cyber attacker should be understood, not just the process of the attack on the system.
In order to stay ahead of the cyber attackers, more organizations are turning to threat intelligence solutions to be able to detect the threats as early as possible and to reduce risk.
SOCRadar uses PRE-ATT&CK while collecting information to protect your future environment by providing you with managed threat intelligence services, detecting malicious activities and activities related to your company.
Take a look at how SOCRadar can help your organization to identify potential threats to your valuable infrastructure and sensitive data.