Mozilla Responds to Critical Vulnerability: Urgent Firefox Update
In a rapid response to a similar vulnerability with Google Chrome, Mozilla has issued an update for its Firefox browser on Windows to address a newly discovered critical security vulnerability. This update follows Chrome’s recent patch for an analogous flaw that had been actively exploited as a zero-day.
TL;DR: Key Points
- Mozilla urgently updated Firefox for Windows to fix a critical security flaw (CVE-2025-2857) in its IPC code.
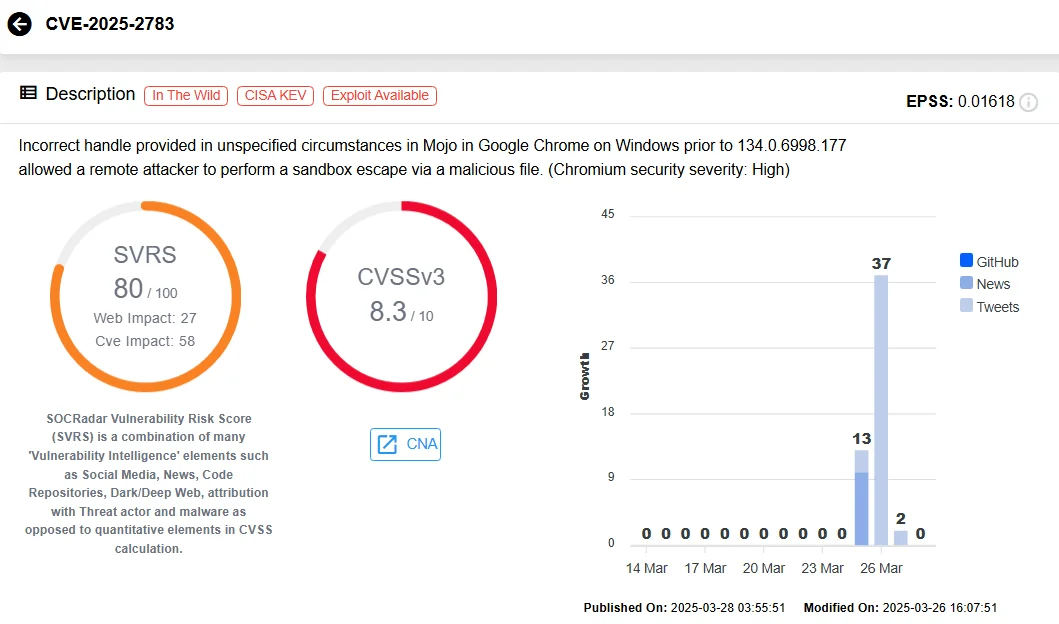
- The vulnerability, similar to Chrome‘s recent sandbox escape bug (CVE-2025-2783), could allow a compromised process to break out of the browser sandbox.
- This only affects Firefox on Windows. Other operating systems are unaffected.
- Fixed versions: Firefox 136.0.4, Firefox ESR 115.21.1, and Firefox ESR 128.8.1.
- This update follows Chrome’s patch for a similar flaw, which was exploited in targeted attacks.
- CISA has added the Chrome vulnerability to its KEV catalog and mandated federal agencies to update by mid-April 2025.
The Vulnerability in Detail
The security flaw, CVE-2025-2857, arises from an improper handle management issue in Firefox’s Inter-Process Communication (IPC) code. According to Mozilla’s advisory, this issue could allow a compromised child process to inadvertently pass an overly permissive handle to its parent process—potentially enabling an escape from the browser’s sandbox environment. Such an escape would allow an attacker to break out of the isolated environment designed to limit the scope of any potential breach.
Mozilla noted that their developers spotted this vulnerability after observing a similar pattern in Chrome’s sandbox escape bug (CVE-2025-2783). While CVE-2025-2857 poses significant risks in theory, there is currently no evidence to suggest that it has been exploited in real-world attacks.
Updates and Affected Versions
In response to this discovery, Mozilla has rolled out fixes across multiple versions:
- Firefox 136.0.4
- Firefox ESR 115.21.1
- Firefox ESR 128.8.1
Users of the standard and Extended Support Release (ESR) versions are encouraged to update immediately to mitigate potential risks.
Context from the Chrome Front
This update from Mozilla follows closely on the heels of Google’s own patch for a 0-day, CVE-2025-2783, which affected Chrome on Windows. Google’s patch came after cybersecurity experts in Kaspersky reported.
In these attacks, Kaspersky Lab noted that the exploit chain involved an additional unknown vulnerability, combined with the sandbox escape, to facilitate remote code execution via malicious links embedded in phishing emails.
Responses & Recommendations
CISA has taken note of these developments by adding the Chrome-related vulnerability to its Known Exploited Vulnerabilities (KEV) catalog. CISA has mandated that federal agencies deploy the necessary updates by mid-April 2025 to protect against these risks.
Staying updated is critical for all users. Whether you use Firefox or Chrome, installing the latest patches ensures that your browser—and your personal data—remains secure against these emerging threats.
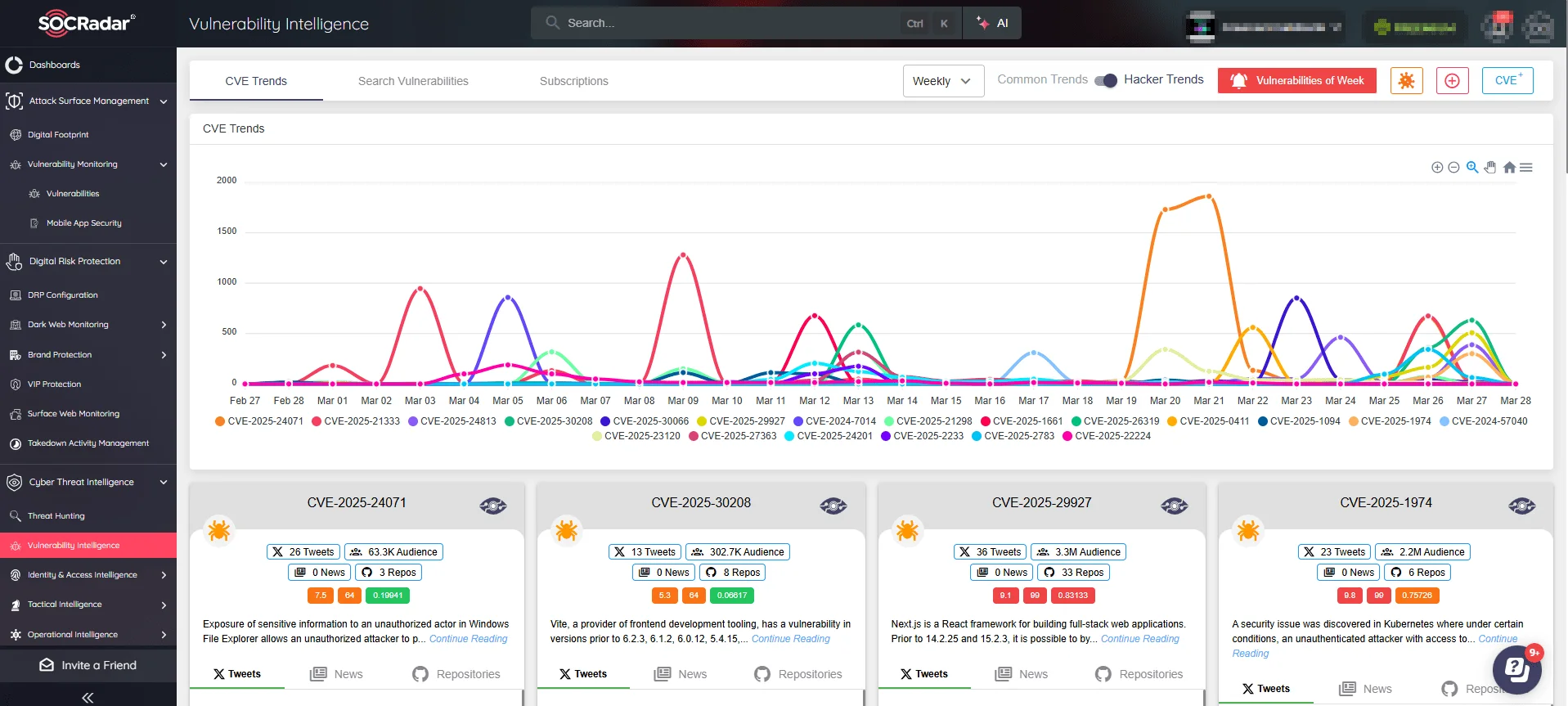
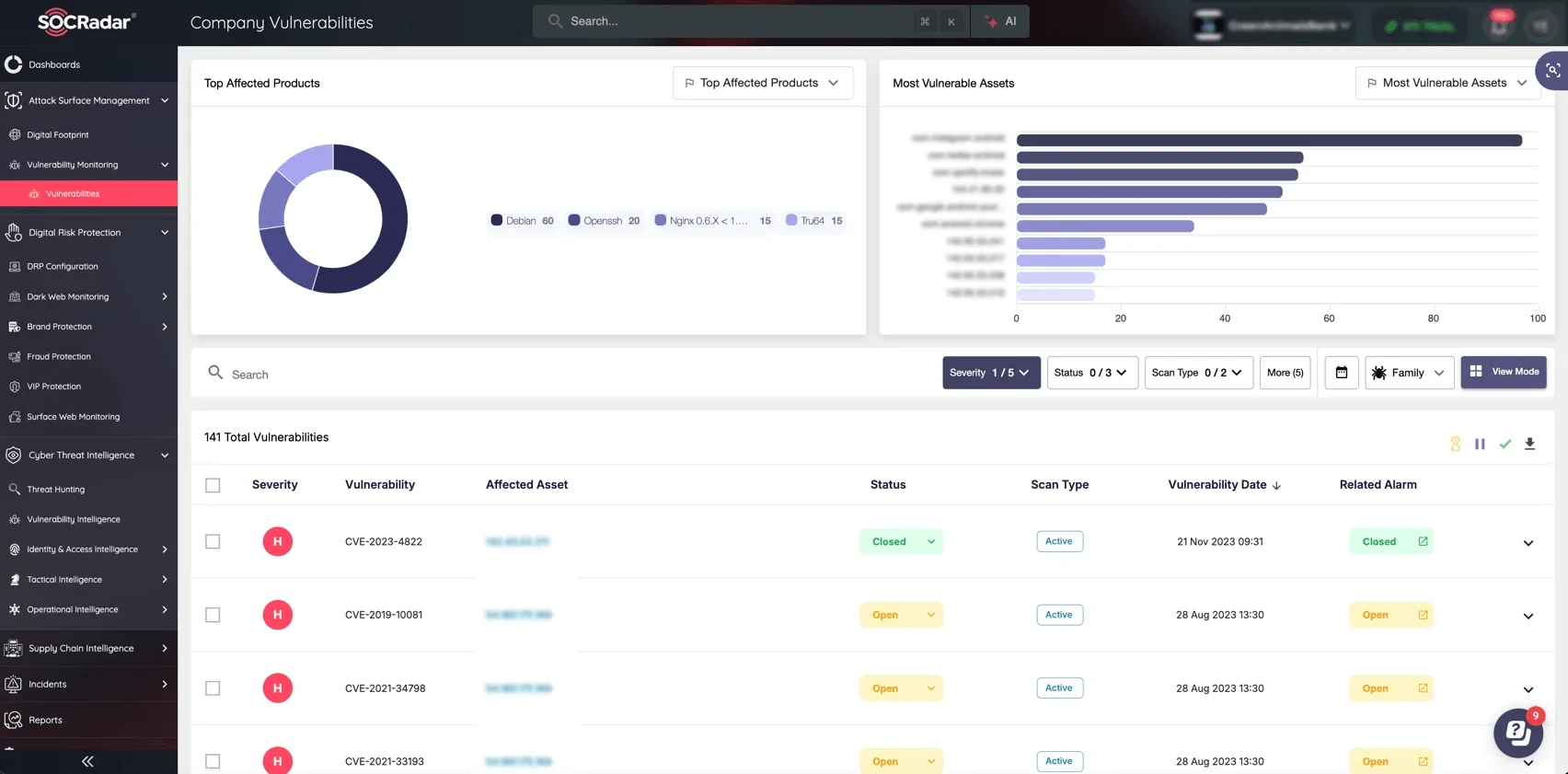
For businesses relying on web applications, tools like SOCRadar’s Vulnerability Intelligence and Attack Surface Management (ASM) can help identify and monitor vulnerable software versions across your infrastructure.
Proactively detect and remediate vulnerabilities in Chrome and Firefox, ensuring attackers cannot exploit them before action is taken. (SOCRadar’s ASM)
Proactively detect exposed browser vulnerabilities and prioritize remediation efforts to minimize the risk of exploitation. By leveraging SOCRadar’s ASM, security teams can gain continuous visibility into outdated software, misconfigurations, and unpatched systems, enabling a more proactive defense against evolving threats.