
Multiple Zero-Day and RCE Vulnerabilities Aboard: AutoCAD, SolarWinds ARM, Bricks Builder Under Risk
The Zero Day Initiative (ZDI) has reported several vulnerabilities affecting Autodesk AutoCAD; these vulnerabilities may allow the execution of arbitrary code and cause disruptions.
AutoCAD is a Computer-Aided Design (CAD) software, developed by Autodesk. AutoCAD software is an industry standard, with widespread recognition and use in fields such as architecture and engineering.
What Are the Zero-Day Vulnerabilities in Autodesk AutoCAD Software?
The recently disclosed zero-day vulnerabilities could be used by attackers to execute code in the context of the current process when a user visits a malicious page or interacts with a compromised file.
The vulnerabilities are classified as high-severity in Autodesk’s advisory, with a severity rating of 7.8 in CVSS. The first set of vulnerabilities can be exploited by an attacker to induce a system crash, write sensitive data, or execute arbitrary code within the current process context:
- CVE-2024-0446: Maliciously crafted STP, CATPART, 3DM, or MODEL files parsed through Autodesk AutoCAD may trigger an Out-of-Bound Write.
- CVE-2024-23120: Parsing a maliciously crafted SLDPRT or CATPART file in Autodesk AutoCAD can result in a Stack-based Overflow.
- CVE-2024-23121: Vulnerability arises from parsing maliciously crafted MODEL, SLDASM, SLDPRT, or PRT files in Autodesk AutoCAD, potentially leading to a Heap-based Overflow.
Furthermore, the following vulnerabilities, when combined with others, could result in code execution within the current process:
- CVE-2024-23122: Parsing maliciously crafted MODEL, 3DM, STP, SLDASM, or SLDPRT files in Autodesk AutoCAD may lead to memory corruption via write access violation.
- CVE-2024-23123: A user-after-free vulnerability in Autodesk AutoCAD Maliciously crafted IGS or SLDPRT files.
- CVE-2024-23124: Parsing a maliciously crafted STP file in Autodesk AutoCAD may lead to dereferencing an untrusted pointer.
Autodesk has stated that these security vulnerabilities will be addressed in an upcoming release.
With SOCRadar’s Vulnerability Intelligence, you can stay up to date on hacker trends and obtain detailed information about disclosed vulnerabilities. Additionally, you can easily verify with the module whether any exploits have been found for a specific vulnerability.
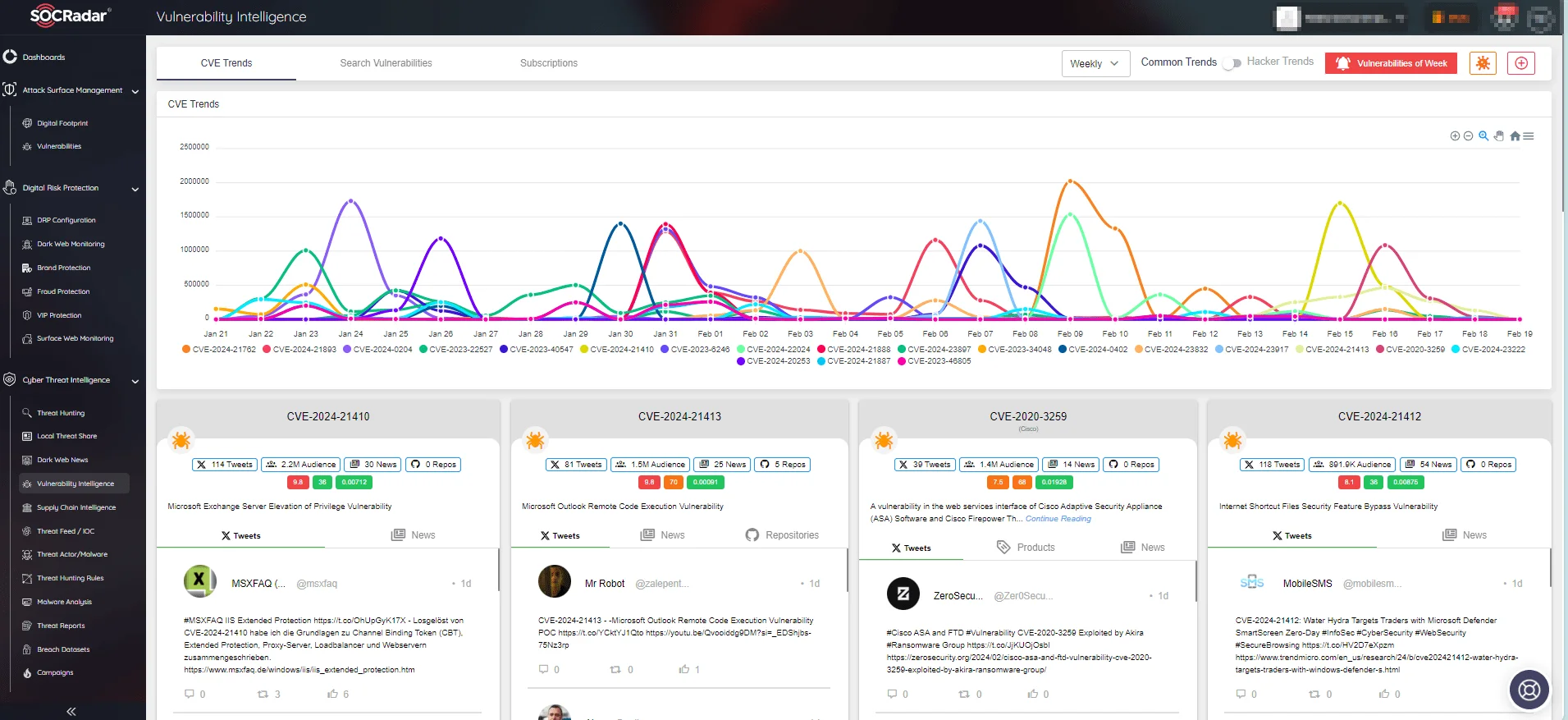
SOCRadar’s Vulnerability Intelligence
Which Autodesk Products Are Affected?
The recently discovered zero-day vulnerabilities affect versions 2021, 2022, 2023, and 2024 of the following products:
- Autodesk AutoCAD
- Autodesk AutoCAD Architecture
- Autodesk AutoCAD Electrical
- Autodesk AutoCAD Map 3D
- Autodesk AutoCAD Mechanical
- Autodesk AutoCAD MEP
- Autodesk AutoCAD Plant 3D
- Autodesk AutoCAD LT
- Autodesk Civil 3D
- Autodesk Advance Steel
As stated by Autodesk, the vulnerabilities discussed in their advisory only apply to the affected products’ Windows versions; other platforms are unaffected.
Are There Mitigation Methods Available?
These vulnerabilities require user interaction, which adds some difficulty to their exploitation. Also, despite the lack of updates at the time of disclosure, there are some mitigation methods available:
- Refrain from using the import feature.
- To prevent the import of certain file types (3dm, abc, CATPart, iges, igs, model, prt, sldasm, sldprt, step, sstp, x_t), disable imports by renaming acTranslators[.]exe in the AutoCAD installation folder.
- Import files exclusively from trusted sources.
For more information on the recent AutoCAD zero-days and guidance, visit the Autodesk advisory here.
Latest Critical Vulnerabilities in SolarWinds ARM: Risk of RCE Attacks
SolarWinds has recently released security updates to address vulnerabilities affecting its Access Rights Manager (ARM) product. Notably, the vulnerabilities in the update could lead to Remote Code Execution (RCE) attacks, and among them are three critical CVEs that demand urgent attention.
SolarWinds Access Rights Manager (ARM) is a software designed to help IT and security administrators manage user access privileges to various systems, data, and files, thereby assisting organizations in protecting against potential data breaches.
The vulnerabilities affect SolarWinds ARM versions 2023.2 and earlier.
Two of the critical vulnerabilities, CVE-2024-23476 and CVE-2024-23479, carry CVSS scores of 9.6 and stem from directory traversal issues. Unauthenticated attackers may exploit these vulnerabilities to perform RCE.
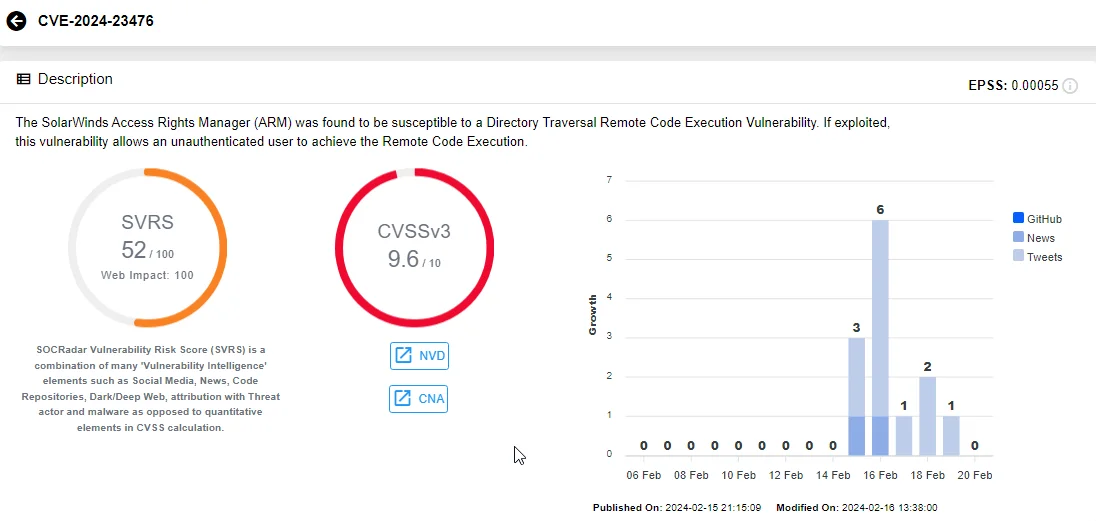
Vulnerability card of CVE-2024-23476, SOCRadar Vulnerability Intelligence
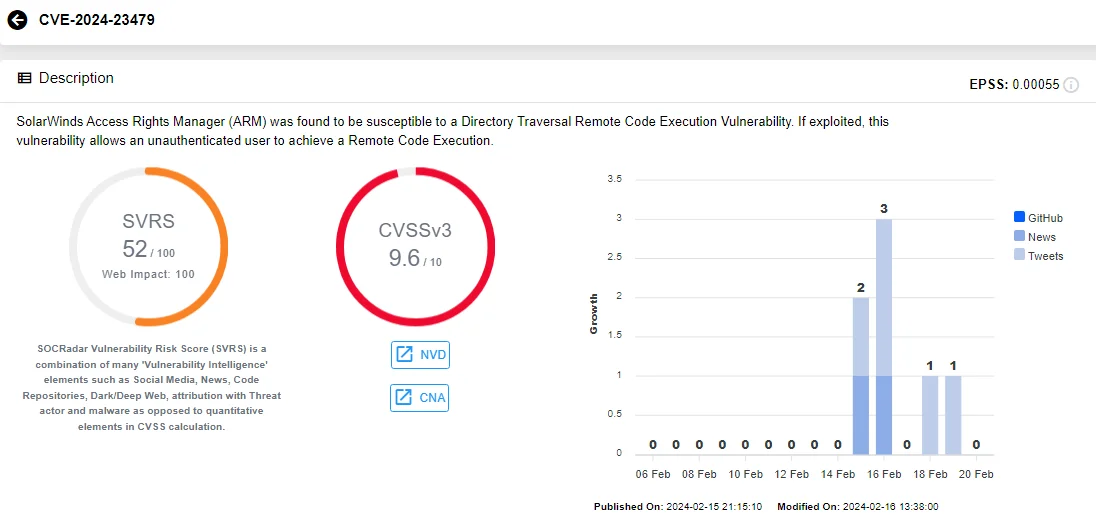
Vulnerability card of CVE-2024-23479, SOCRadar Vulnerability Intelligence
The third critical vulnerability, CVE-2023-40057 (CVSS: 9.0), is an input validation issue. Exploiting the vulnerability, an authenticated attacker can abuse a SolarWinds service to perform RCE.
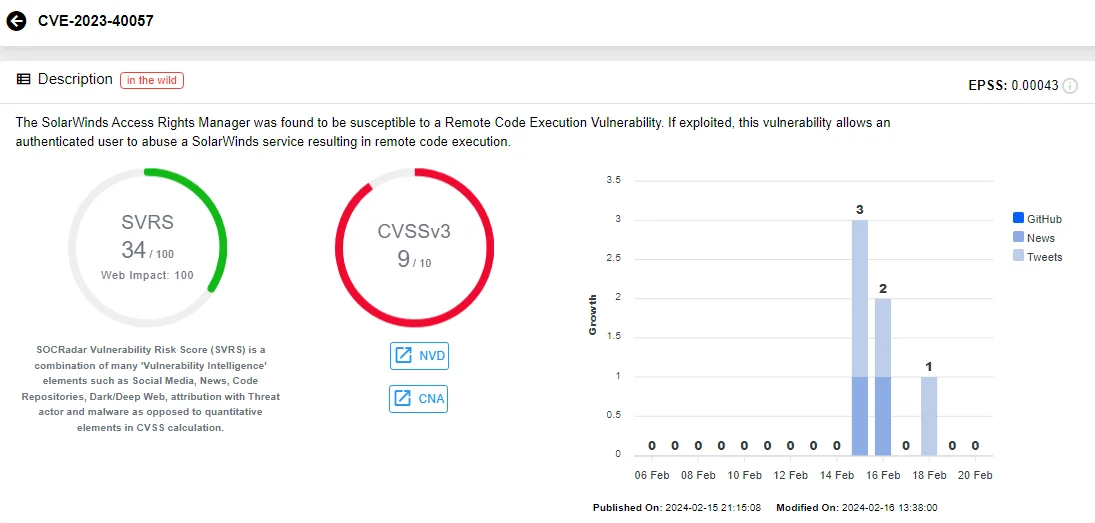
Vulnerability card of CVE-2023-40057, SOCRadar Vulnerability Intelligence
The remaining two vulnerabilities, tracked as CVE-2024-23477 (CVSS: 7.9) and CVE-2024-23478 (CVSS: 8.0), are rated as high-severity issues.
Users and administrators of affected product versions are advised to update to the latest version immediately to prevent the exploitation of these vulnerabilities. For more information and update guidance, visit the SolarWinds advisory.
Yet Another RCE: WordPress’ Bricks Builder Theme Flaw Is Under Attackers’ Radar
A critical vulnerability, tracked as CVE-2024-25600, has been uncovered in the Bricks Builder Theme for WordPress, putting approximately 25,000 active installations at risk. This vulnerability allows attackers to execute malicious PHP code, posing a severe threat to affected websites.
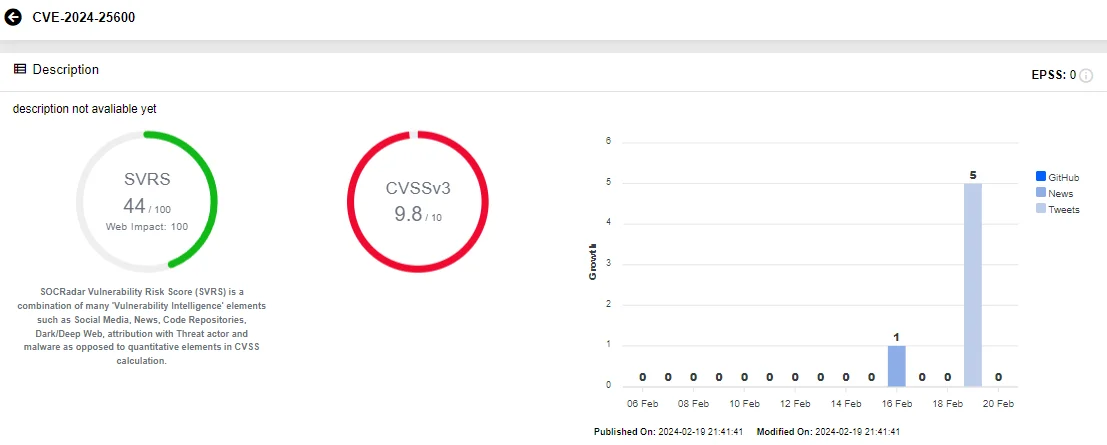
Vulnerability card of CVE-2024-25600, SOCRadar Vulnerability Intelligence
Discovered by researcher ‘snicco’ on February 10, CVE-2024-25600 exploits an eval function call in the ‘prepare_query_vars_from_settings’ function, enabling unauthenticated users to execute arbitrary PHP code.
Attackers leverage REST API endpoints for server-side rendering, bypassing nonce checks and gaining unauthorized access. Notably, the attackers utilize malware that disables security plugins like Wordfence and Sucuri, intensifying the risk.
Bricks Builder swiftly responded to the threat by releasing an update on February 13, containing crucial patches to mitigate the vulnerability. Despite initial assurances of no exploitation, active attacks were detected as of February 14.
Wordfence confirmed 37 detections within the past 24 hours, underscoring the severity and immediacy of the threat. IP addresses associated with these attacks include:
- 200.251.23[.]57
- 92.118.170[.]216
- 103.187.5[.]128
- 149.202.55[.]79
- 5.252.118[.]211
- 91.108.240[.]52
To safeguard against exploitation, users must update Bricks Builder to version 1.9.6.1 immediately. Websites must remain fortified against emerging threats, even within trusted themes and plugins. Delaying updates increases the risk of compromise, as attackers actively exploit the vulnerability.
SOCRadar’s Attack Surface Management (ASM) module can automate the monitoring of vulnerabilities impacting your assets and components. The platform cleverly sends alerts for emerging security issues, offering rapid insights to help better prioritize patching operations.
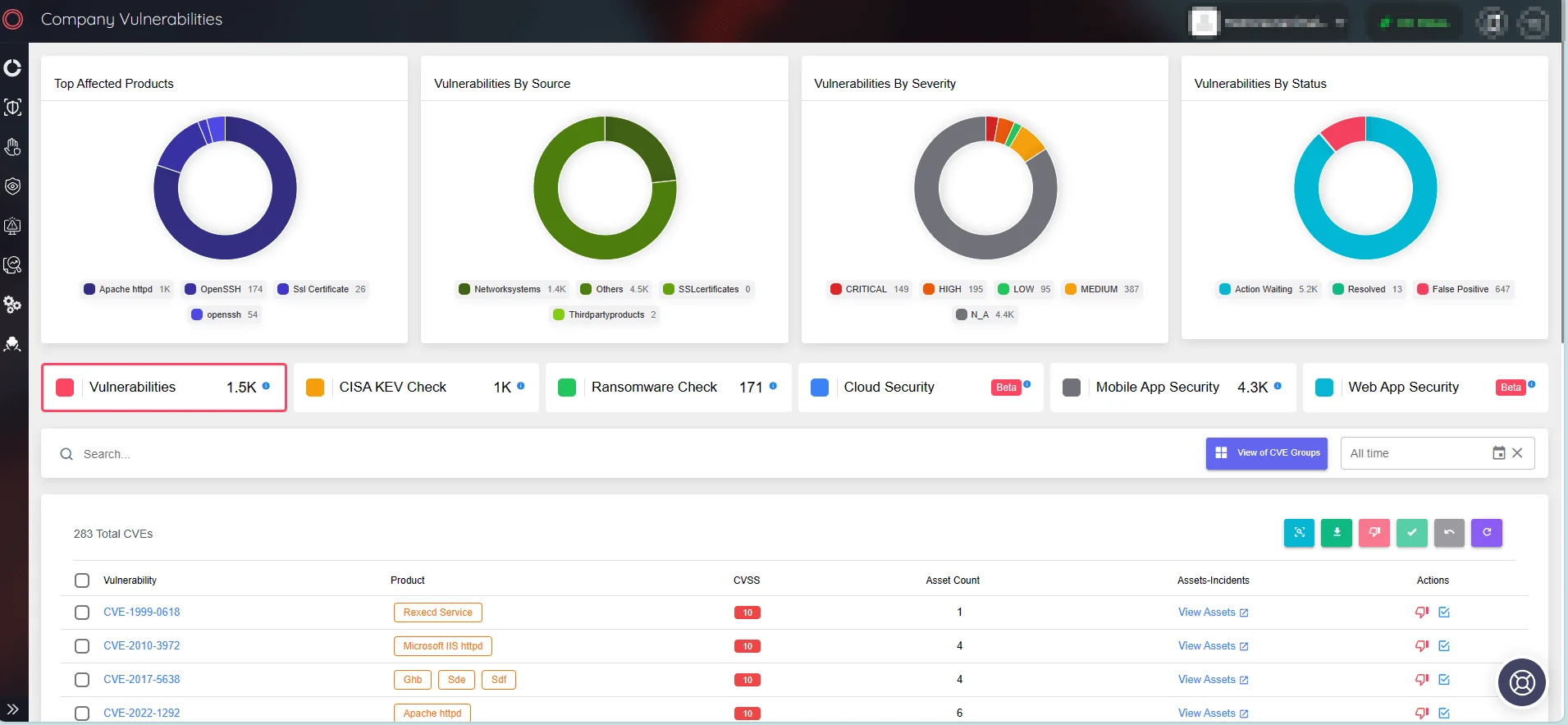
SOCRadar’s Attack Surface Management/Company Vulnerabilities
Register for the free edition of SOCRadar XTI to benefit from its features and enhance your vulnerability management approach.




































