New Advanced Attack Technique Exploiting “search-ms” URI Protocol Handler
The Windows operating system boasts a robust search feature for locating files and folders; there also is a less-known element, “search-ms” URI protocol handler. The handler enhances local searches and allows for queries on file shares situated on remote hosts. However, researchers discovered that attackers have found a new way to exploit it in attacks.
How Are Attackers Leveraging the “search-ms” Protocol Handler?
In the past, attackers exploited this handler by using malicious documents, but a recent investigation has shown a more advanced approach.
Researchers at Trellix found that attackers are now leading users to websites that use JavaScript hosted on the page to exploit the search-ms functionality. To make matters worse, this technique has been extended to HTML attachments, broadening the scope of potential targets.
In their investigation, the researchers also explored the capabilities of the “search” protocol, which the operating system uses to launch the default desktop search application. By combining the power of both protocols, the attackers were able to use the search functionality in different script files like Batch, Visual Basic, PHP, and PowerShell. This shows how versatile and effective this attack technique is, as it leverages the features of both search protocols for malicious activities.
During an attack using the “search” / “search-ms” URI protocol handler, threat actors may send deceptive emails containing hyperlinks or email attachments that redirect users to attacker controlled websites. Once users visit these websites, malicious Javascripts are triggered, which initiate searches on a remote server using the “search” / “search-ms” URI protocol handler.
The search results display remotely hosted malicious shortcut files disguised as PDFs or other trusted icons, just like local search results in Windows Explorer. This makes it harder for users to identify the malicious intent, making the attack more effective.
The Attack Scheme
Researchers have discovered phishing emails that employ the search-ms handler to download a malicious payload. These emails aim to trick recipients by posing as urgent quotation requests from sales managers and contain HTML or PDF attachments.
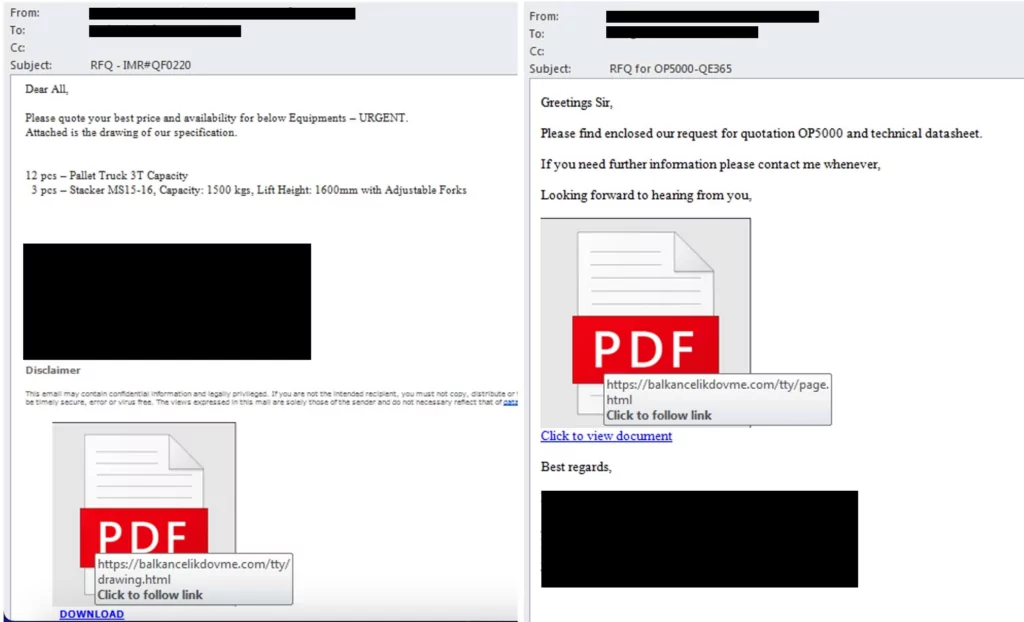
If the recipient clicks the link in the email or the attachment, it redirects them to a website that exploits the search-ms handler.
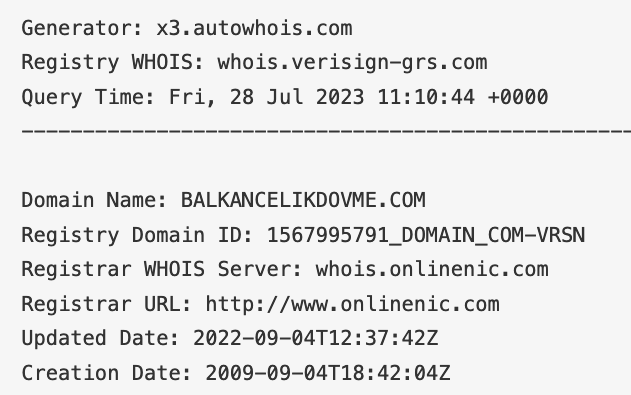
These websites have been previously compromised by the attackers; for example, in the phishing email shown by researchers, the website to which the recipient is redirected (balkancelikdovme[.]com) was originally created in 2009, as evidenced here:
On the website, a malicious script activates the handler to perform a search operation. The scripts sets the window.location.href property to initiate the search for items related to “Review” within the specified location, which is the attacker-controlled remote file server.
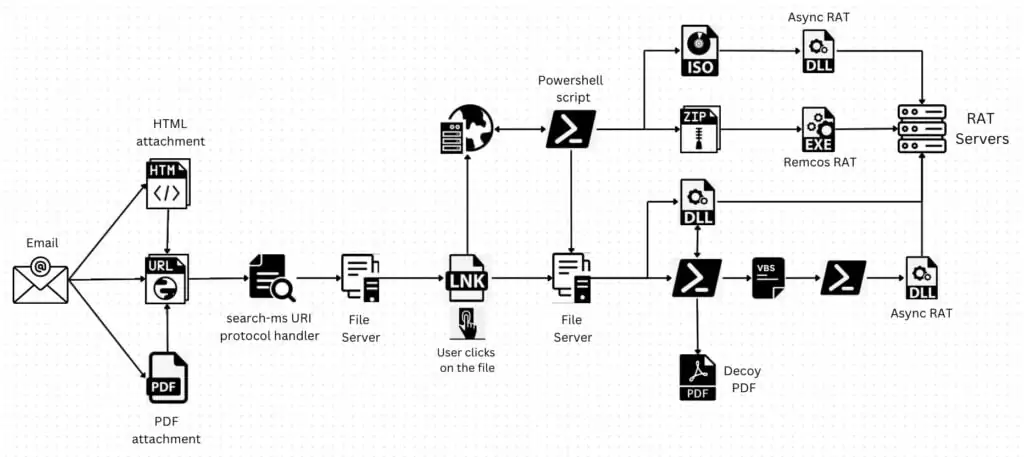
Upon receiving properties of the shortcut file (Review_200630_DeletedItem.lnk), the GET method retrieves the file’s content. Attackers manipulate icons and file names for shortcut files to effectively deceive the victims. Furthermore, each variant of the shortcut file may have a distinct signature or fingerprint, making it more difficult for security software to detect. The attacker also employs SSL (Secure Sockets Layer) encryption for all network activity, thereby circumventing network security measures.
If the victim clicks on the opened shortcut file, the regsvr32[.]exe utility executes a referenced malicious DLL file in the command line. The downloaded payloads are remote access trojans (RATs), specifically Async RAT and Remcos RAT. After successfully infecting a target with a RAT, the attackers can engage in various malicious activities, including stealing sensitive information, monitoring user activity, executing commands, and spreading to other connected devices.
Notably, the EXE payload of Remcos RAT employs null byte injection. By injecting null bytes into the executable file, the RAT can bypass security mechanisms that rely on file signatures and patterns, enabling it to operate undetected and increase its chances of successful infiltration and persistence.
Use administrative privileges to run the command below and disable the “search”/ “search-ms” URI protocol handler:
- reg delete HKEY_CLASSES_ROOTsearch /f
- reg delete HKEY_CLASSES_ROOTsearch-ms /f
How Can SOCRadar Help?
Since email is a common distribution method for malware, SOCRadar’s Malware Analysis module becomes a vital tool for comprehensive understanding and rapid identification of malware samples. This feature equips security teams with powerful functionalities, including static analysis to examine code structures, threat intelligence integration for IoC correlation, and detailed reporting with visualizations for effective decision-making and collaboration.