
New RaaS Emerged, RDP Access, Database, and Credit Card Sales
Welcome to this week’s dark web news summary. We uncover a new ransomware tool called “NoEscape” on the dark web. Credit cards from Saudi Arabia are being sold, raising concerns about financial fraud. Additionally, unauthorized Remote Desktop Protocol (RDP) accesses are traded, posing risks to multiple companies.
Join us as we explore these incidents and their potential effects on the threat landscape.
Find out if your data has been exposed.
Find out if your data has been exposed.
Unauthorized RDP Accesses Sale is Detected for Many Companies
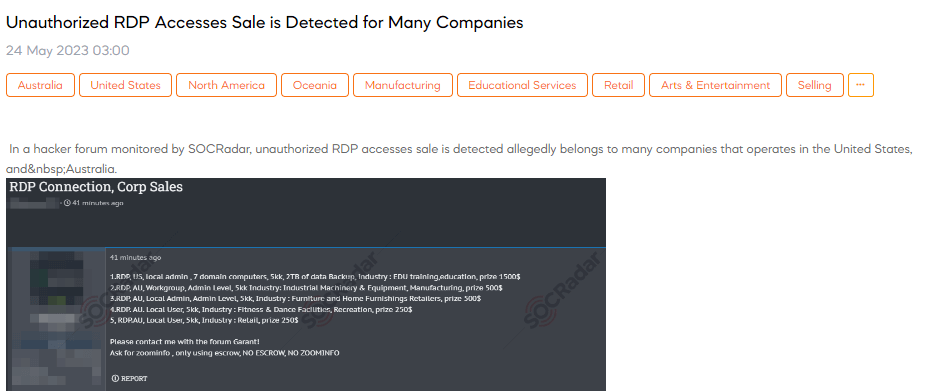
SOCRadar dark web analysts have detected a post that a threat actor claims to have detected the sale of unauthorized RDP accesses, allegedly belonging to numerous companies operating in the United States and Australia. These accesses include RDP type, location (US or AU), user privileges (local admin, admin level, or local user), number of domain computers, data backup size, industry sectors, and corresponding prices.
Credit Cards Belonging to Saudi Arabia are on Sale
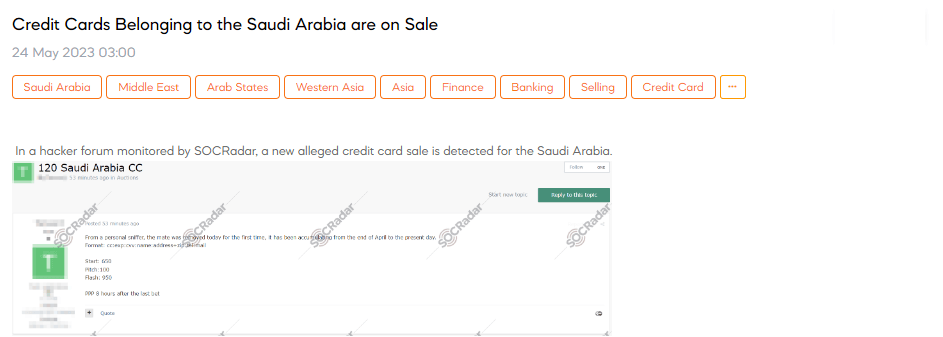
A SOCRadar researcher has discovered an alleged credit card sale has been detected for Saudi Arabia. According to the source, a personal sniffer revealed that the accumulated credit card information, including card number, expiration date, CVV, name, address with zip code, telephone number, and email, has been collected since the end of April until now. The sale format follows the pattern: cc:exp:cvv:name:address+zip:tel:mail. The credit card information’s starting price is 650, with increments of 100. The flash price, which is the final price, is 950.
Database of Federal Bank is Leaked
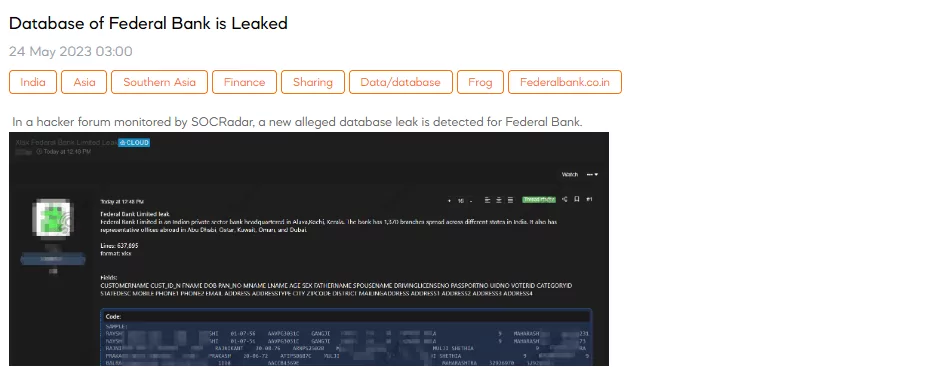
SOCRadar dark web team has detected a post that the threat actor claims a new alleged database leak for Federal Bank Limited, revealing sensitive information. The leaked database reportedly contains 637,895 lines of data in an xlsx format. The fields included in the leaked data are as follows: customer name, customer ID, date of birth, PAN information, age, gender, father’s name, spouse’s name, driving license number, passport number, UID number, voter ID, category ID, state description, mobile number, primary phone, email address, physical address.
Database Purchasing Announcement is Detected for the Bulgarian Military
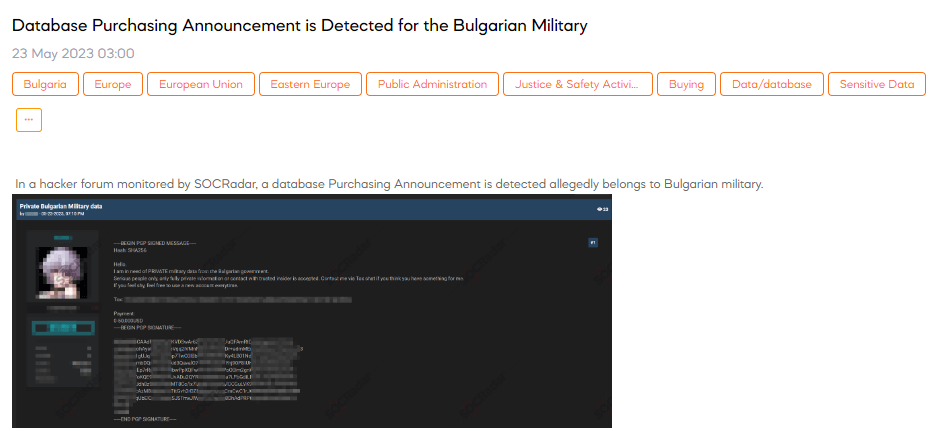
On May 23, A SOCRadar researcher discovered a post about a threat actor’s database purchasing announcement, allegedly belonging to the Bulgarian military. The post indicates a request for private data, specifically from individuals or sources within Bulgaria. The threat actor emphasizes the need for serious people and insists on obtaining fully private information or establishing contact with a trusted insider. They provide a Tox chat as a means of communication and suggest using new accounts for anonymity. The post concludes by mentioning the payment range, which is stated as 0 – 50,000 USD.
New RaaS Detected
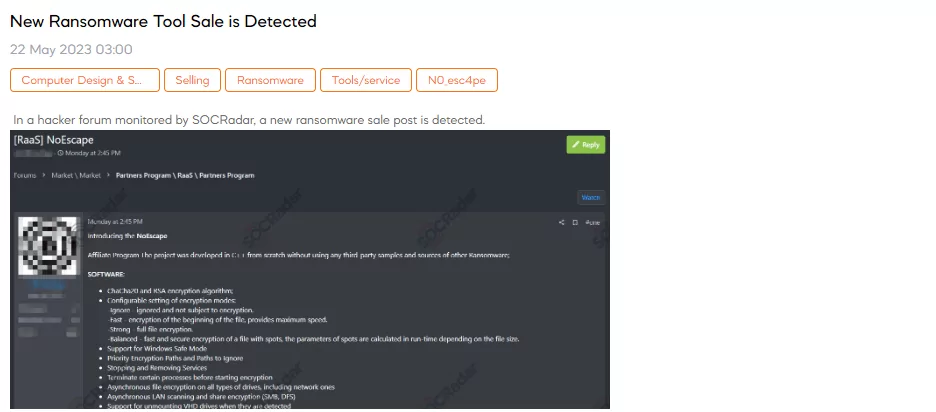
SOCRadar dark web analyst has discovered a post introducing the NoEscape Affiliate Program, a new ransomware for sale. The program is developed in C++ without using third-party sources, offering features such as encryption algorithms, configurable encryption modes, Windows safe mode compatibility, LAN scanning, and more. The post also mentions a Tor admin panel, private chats for secret communication, and DDoS/call/spam services. The ransomware is compatible with various operating systems but not applicable to CIS countries.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































