
An Overview of the Nominet Security Breach Tied to Ivanti VPN Vulnerability (CVE-2025-0282)
[Update] January 17, 2025: “PoC Exploit Released for Ivanti Connect Secure CVE-2025-0282 Vulnerability”
Nominet, the official .UK domain registry, recently confirmed a breach of its network, raising concerns about the security of critical internet infrastructure. The company, which manages over 11 million domain names, detected suspicious activity linked to an Ivanti VPN zero-day vulnerability.
While investigations continue, the swift detection of the intrusion and immediate countermeasures highlight the evolving challenges of securing large-scale operations in today’s threat landscape.
What Happened?
The official domain registry Nominet disclosed a breach of its network attributed to a zero-day vulnerability in Ivanti VPN software. The incident came to light during the week of December 30, 2024, when the company detected suspicious activity on its systems.
Although Nominet has found no evidence of data breaches or backdoors, the vulnerability exploited allowed unauthorized access to its network. In response, the company reported the attack to relevant authorities, including the UK’s National Cyber Security Centre (NCSC), and implemented measures such as restricting VPN access.
Nominet’s Response
When Nominet detected suspicious activity on its network, it acted quickly to reduce potential risks. The organization confirmed that the intrusion was caused by a zero-day vulnerability in their third-party VPN software, which was supplied by Ivanti. Despite the breach, Nominet pointed out that its restricted access protocols and firewalls played a vital part in protecting its core registry systems and ensuring domain registration and management services remained operational.
The company also stated that no evidence of data leak or backdoors had been found thus far. To further secure its infrastructure, Nominet implemented additional precautions, such as limiting VPN access to its systems. External cybersecurity experts were brought in to assist with the ongoing investigation and strengthen defensive measures. The company continues to closely monitor its systems.
The Exploited Zero-Day: CVE-2025-0282
The entry point for the Nominet breach was a zero-day vulnerability in Ivanti Connect Secure, tracked as CVE-2025-0282 (CVSS 9.0). This critical flaw is a stack-based buffer overflow vulnerability that allows unauthenticated Remote Code Execution (RCE). Threat actors began exploiting this flaw in December 2024, before Ivanti revealed it with a patch on January 8, 2025, alongside another vulnerability (CVE-2025-0283).
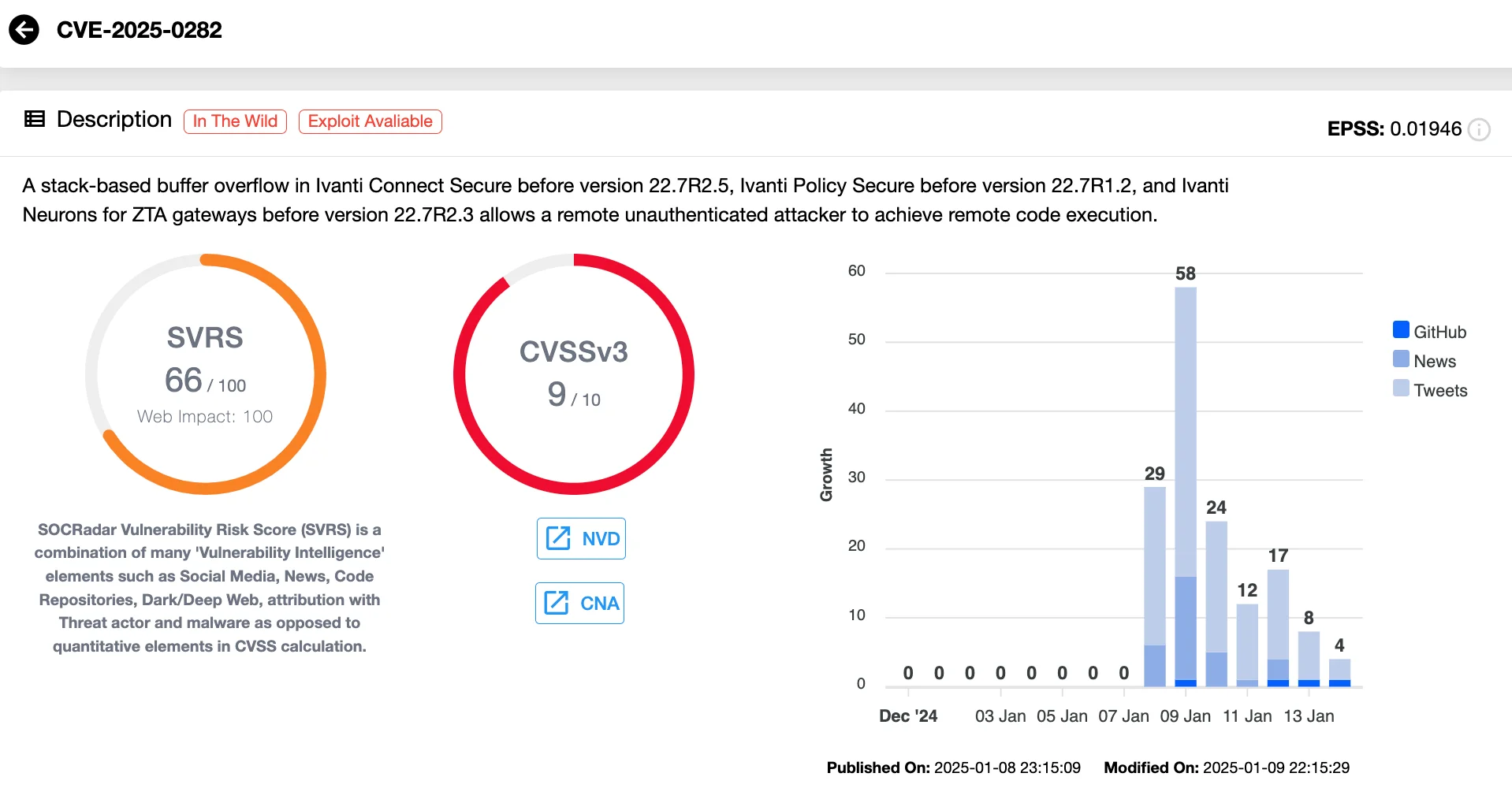
Vulnerability card of CVE-2025-0282 (SOCRadar Vulnerability Intelligence)
Researchers have noted that attackers leveraged the vulnerability through a structured process, conducting reconnaissance using repeated HTTP requests and exploiting the Host Checker Launcher to identify vulnerable systems. Once inside, they could disable SELinux, block syslog forwarding, and deploy malicious web shells like PHASEJAM. These tactics allowed for unauthorized access and the potential for lateral movement across networks.
Affected Products and Patch Availability
The Ivanti zero-day vulnerability CVE-2025-0282 affects the following products:
- Ivanti Connect Secure: Versions prior to 22.7R2.5
- Ivanti Policy Secure: Versions prior to 22.7R1.2
- Ivanti Neurons for ZTA Gateways: Versions prior to 22.7R2.3
Although patches for Ivanti Connect Secure were made available on January 8, 2025, customers using Ivanti Policy Secure and Neurons for ZTA Gateways must wait until January 21, 2025, for a patch.
For more information about the latest Ivanti vulnerabilities (CVE-2025-0282 and CVE-2025-0283) and mitigation strategies, check out SOCRadar’s article: “Ivanti Zero-Day Exploited in Connect Secure”
The broader implications of the exploited zero-day vulnerability highlight the importance of proactive monitoring and timely patching. Organizations relying on Ivanti Connect Secure must apply the latest patches immediately and assess their environments for signs of exploitation.
SOCRadar’s Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence module provides actionable insights to help organizations identify, prioritize, and mitigate critical vulnerabilities like CVE-2025-0282. With real-time alerts and detailed threat analysis, you can proactively protect your systems and stay a step ahead of attackers.
PoC Exploit Released for Ivanti Connect Secure CVE-2025-0282 Vulnerability
A Proof-of-Concept (PoC) exploit for the critical CVE-2025-0282 vulnerability in Ivanti Connect Secure has been made available, along with technical details. The PoC, written in Ruby, demonstrates how attackers can exploit this flaw to gain full control over affected systems.
The vulnerability, found in code handling IF-T connections, affects Ivanti Connect Secure, Policy Secure, and Neurons for ZTA Gateways. Following Ivanti’s patch release, the PoC highlights the potential ease with which the vulnerability can be exploited, underscoring the urgency for organizations to update their systems.
Proactively Secure Your Attack Surface with SOCRadar
The Nominet breach highlights the dangers of zero-day vulnerabilities, particularly in critical software such as Ivanti Connect Secure. While the intrusion’s rapid detection likely mitigated its impact, the incident serves as a reminder of the essential role of timely patching, proactive monitoring, and vulnerability management.
Nominet’s response, which included collaboration with authorities and the implementation of additional safety measures, exhibits the significance of a coordinated and well-executed incident response plan. However, as attackers continue to exploit zero-day vulnerabilities such as CVE-2025-0282, organizations must remain attentive in order to protect their digital assets and prevent lateral movement across their networks.
SOCRadar’s Attack Surface Management (ASM) module and Digital Footprint tracking enable businesses to remain ahead of possible threats. These tools assist you in thoroughly securing your environment by identifying exposed assets, monitoring for vulnerabilities, and providing real-time insights.
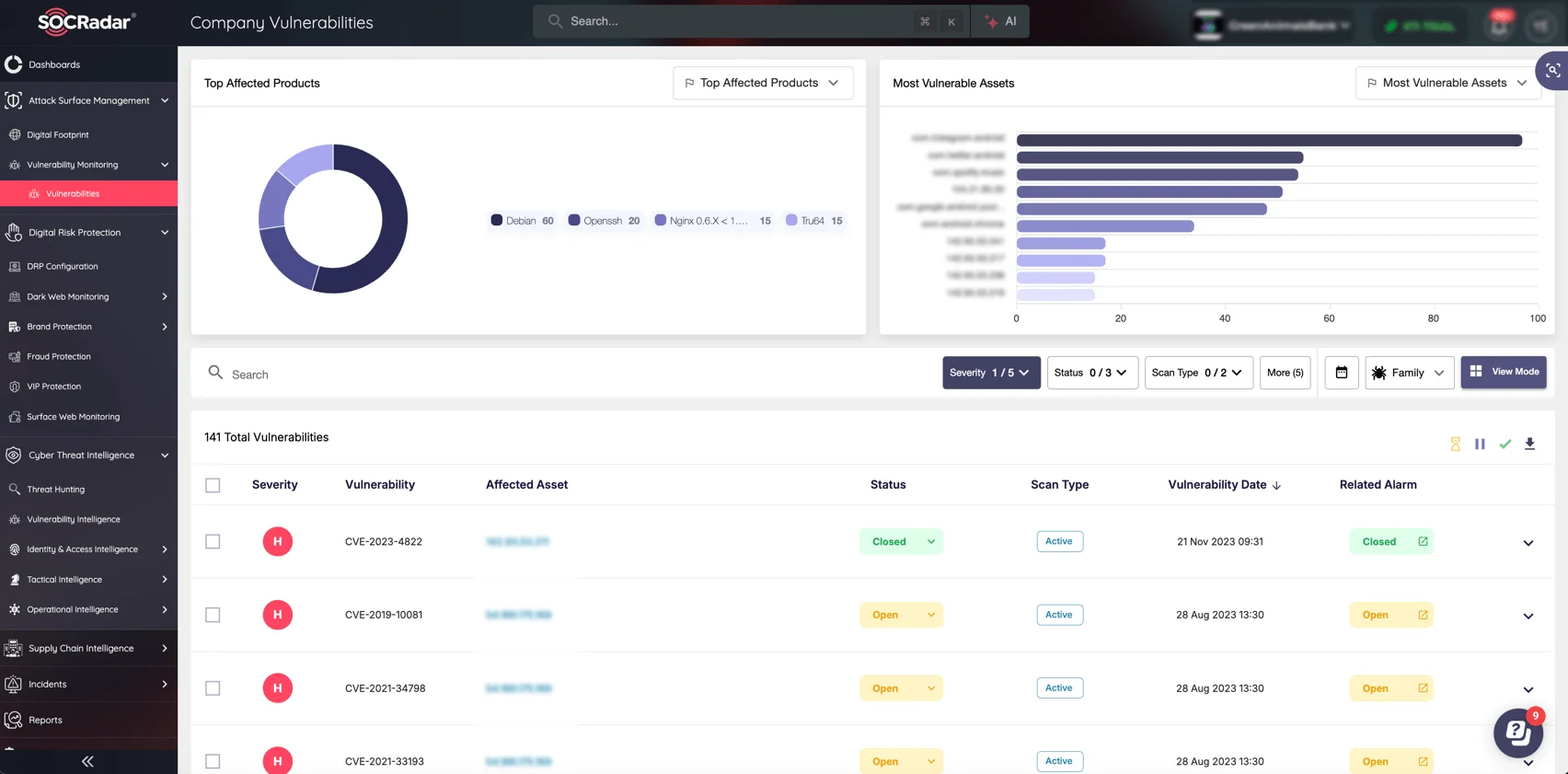
Easily monitor your assets’ status and vulnerabilities affecting your organization (SOCRadar ASM module)
With SOCRadar, your organization gains a reliable partner in risk reduction and resilience to constantly evolving cyber threats.




































