
OpenWrt’s Attended SysUpgrade (ASU) Vulnerability Exposes Routers to Malicious Firmware Attacks
OpenWrt, a popular open-source Linux-based embedded operating system, recently discovered a critical vulnerability (CVE-2024-54143) in its Attended SysUpgrade (ASU) server. The ASU service, which was designed to speed up firmware updates with custom builds, had flaws that allowed attackers to compromise firmware integrity, exposing users to potential security risks.
In this blog, we’ll look at the vulnerabilities that affect the ASU service, discuss their potential impact, and outline actionable steps for securing devices and mitigating risks effectively.
About OpenWrt
OpenWrt is a highly customizable Linux-based operating system that is widely used for network devices such as routers and access points. It is popular for its advanced features and flexibility, including a writable filesystem and package management capabilities that allow users to create custom firmware solutions for their devices. OpenWrt works with hardware from a variety of manufacturers, including ASUS, D-Link, and Zyxel, and is a reliable alternative to stock firmware for many.
The Attended SysUpgrade feature simplifies firmware updates by generating custom images that include pre-installed packages and user configurations.
The OpenWrt Vulnerabilities: A Critical Exploit Chain
Command Injection in Imagebuilder
One of the vulnerabilities in OpenWrt’s Attended SysUpgrade (ASU) server resulted from a command injection flaw in the ImageBuilder service. This flaw enabled attackers to insert arbitrary commands during the firmware build process, resulting in the creation of malicious firmware images. These images may be signed with legitimate build keys, making them appear trustworthy to unsuspecting users.
Truncated SHA-256 Hash Collisions
The second vulnerability, CVE-2024-54143 (CVSS score of 9.3), involves truncating SHA-256 hashes to 12 characters during the caching process. This significant reduction in hash length reduces entropy, making it possible for attackers to cause hash collisions. Malicious actors can exploit this vulnerability to replace legitimate firmware builds with compromised ones, effectively poisoning the artifact cache.
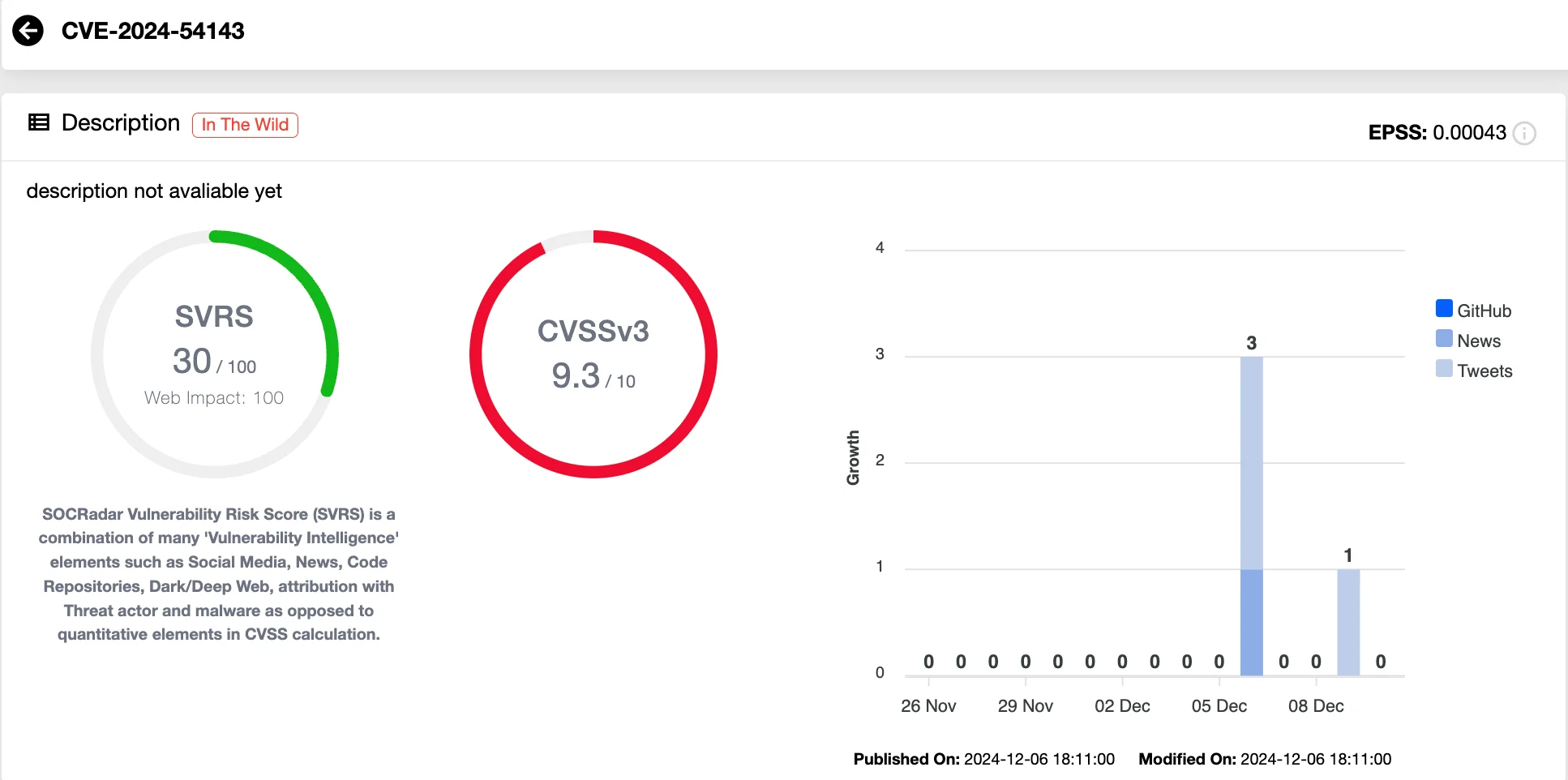
Details of CVE-2024-54143 (SOCRadar Vulnerability Intelligence)
Discover and Secure Your Digital Perimeter with SOCRadar ASM
Unmonitored assets and misconfigurations can serve as open doors for attackers. SOCRadar’s Attack Surface Management (ASM) provides continuous visibility into your exposed assets and potential attack vectors. ASM helps you:
- Map your entire attack surface, including IoT devices, firmware, and third-party dependencies.
- Identify misconfigurations, vulnerabilities, and overlooked digital assets.
- Receive alerts for newly exposed entry points, ensuring rapid remediation.
SOCRadar’s Attack Surface Management (ASM)
Proof of Concept (PoC): Demonstrating the Exploit
RyotaK, a security researcher, conducted a Proof of Concept (PoC) to exploit OpenWrt’s vulnerabilities, which included command injection and SHA-256 hash collision flaws. By running a local instance of the Attended SysUpgrade (ASU) server, the researcher discovered that insufficient input sanitization enabled attackers to inject arbitrary commands into the firmware build process. Malicious package names, for example, could execute commands in the containerized build environment, resulting in firmware that contains malicious code.
To take advantage of the hash collision flaw, the researcher used a powerful GPU (NVIDIA RTX 4090) and Hashcat to brute-force 12-character truncated SHA-256 hashes. This method generated collisions with legitimate firmware builds’ cache keys, allowing valid images to be replaced with compromised ones. Using this exploit chain, attackers could distribute malware-infected firmware, avoiding detection mechanisms because it appears to be a signed and legitimate update.
This approach demonstrates the risks associated with any system that relies on shortened hashes and user-supplied inputs for critical processes. Attackers can easily exploit such vulnerabilities to spread malware on a large scale, targeting both individual devices and enterprise infrastructure, potentially resulting in widespread compromise.
OpenWrt’s Swift Response
After receiving the vulnerability report, the OpenWrt team acted quickly to resolve the issue. They applied patches to the Attended SysUpgrade server within hours. Security improvements included the use of full SHA-256 hashing and improved input sanitization to prevent future exploitation.
While the team discovered no evidence of malicious activity in the available build logs from the previous seven days, the automatic cleanup of older records limited their ability to fully evaluate historical incidents. Users were advised to update to the most recent patches as soon as possible.
Identify and Prioritize Threats with SOCRadar Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence module equips organizations with real-time insights into emerging vulnerabilities. By continuously monitoring critical exploits, such as the OpenWrt flaws, it enables your team to:
- Detect vulnerabilities in your infrastructure before they are weaponized.
- Access actionable intelligence on CVEs, including severity scores and mitigation steps.
- Prioritize responses based on threat likelihood and potential impact.
SOCRadar’s Vulnerability Intelligence
With SOCRadar, security teams can stay ahead of emerging risks, ensuring timely patch management and enhanced readiness against the most critical vulnerabilities.
The OpenWrt Sysupgrade flaw emphasizes the importance of strict security protocols in firmware update mechanisms. OpenWrt has set a good example of transparency and responsiveness by quickly addressing these vulnerabilities. Users must remain vigilant, ensuring that their devices are up to date and that their configurations are secure, to protect themselves from potential future exploits.




































