
Pre-Auth RCE Vulnerability in Apache OFBiz (CVE-2024-38856) Is Under Active Exploitation, CISA Warns
[Update] September 6, 2024: “New RCE Vulnerability (CVE-2024-45195) Discovered in Apache OFBiz, Patch Now”
The Cybersecurity and Infrastructure Security Agency (CISA) has recently included a vulnerability in Apache OFBiz in its Known Exploited Vulnerabilities (KEV) Catalog, citing ongoing active exploitation.
This flaw, identified as CVE-2024-38856, is classified as critical and enables remote attackers to execute malicious code.
Given that Apache OFBiz is a widely used Enterprise Resource Planning (ERP) solution, the implications of this vulnerability could significantly impact numerous businesses if not addressed promptly.
What is CVE-2024-38856?
CVE-2024-38856, rated with a CVSS score of 8.1, represents a critical pre-authentication vulnerability that allows Remote Code Execution (RCE) within the popular ERP system, Apache OFBiz.
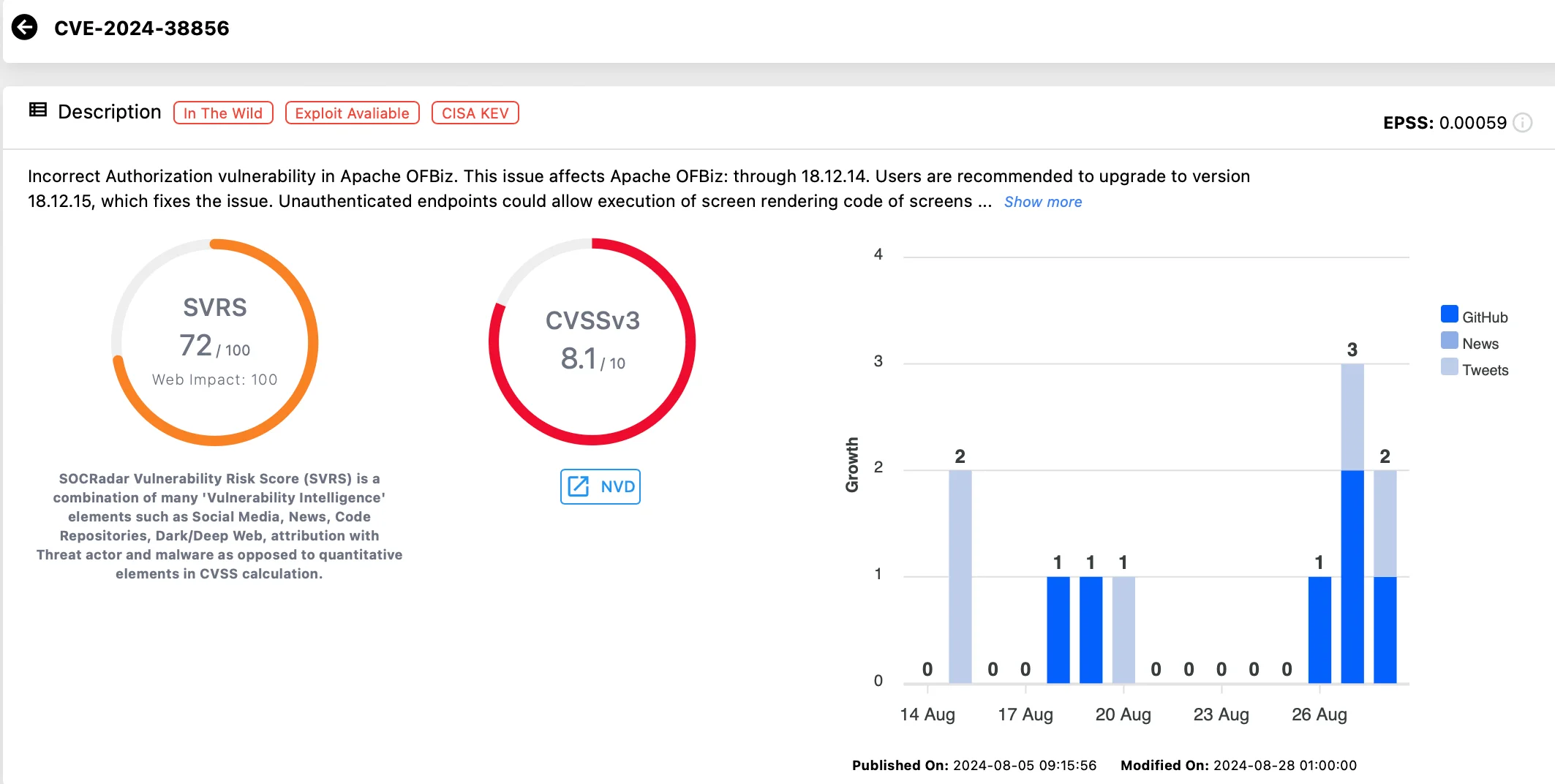
Vulnerability card of CVE-2024-38856 (SOCRadar Vulnerability Intelligence)
The vulnerability arises from incorrect authorization, permitting an unauthenticated attacker to inject a malicious Groovy payload through specific endpoints.
This vulnerability, published on August 5, 2024, also serves as a patch bypass for a previous vulnerability, CVE-2024-36104, which had a higher CVSS score of 9.1. With the risk of exploitation so high, CISA has mandated that all Federal Civilian Executive Branch (FCEB) agencies patch this vulnerability by September 17, 2024.
SOCRadar’s Vulnerability Intelligence module offers a comprehensive solution for monitoring and responding to critical vulnerabilities in real-time. By continuously tracking CVE and exploitation trends, this powerful tool provides organizations with an extensive database and advanced analytics capabilities to stay ahead of emerging threats.
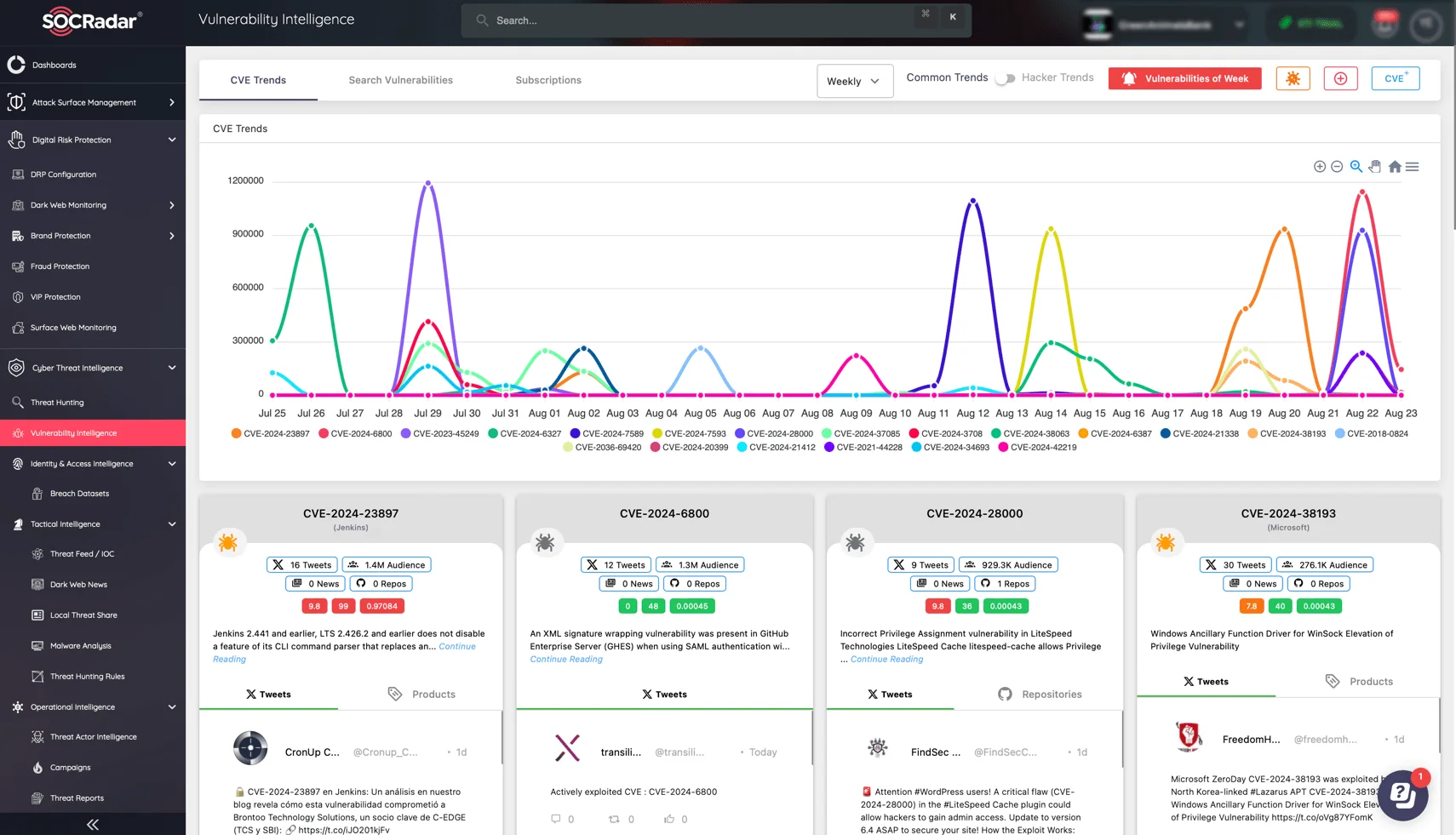
CVE and exploitation trends on SOCRadar’s Vulnerability Intelligence module
Exploitation Mechanism of CVE-2024-38856
The CVE-2024-38856 vulnerability stems from a discrepancy in the way the ControlServlet and RequestHandler functions handle different endpoints. Ideally, these functions should process the same endpoints consistently.
By crafting a raw URL without any path traversal vector, an attacker can gain unauthorized access to the ProgramExport endpoint. This is achieved by combining the ProgramExport endpoint with other endpoints which don’t require authentication, as reported by SonicWall.
Some of the vulnerable URLs identified are as follows:
- POST /webtools/control/forgotPassword/ProgramExport
- POST /webtools/control/main/ProgramExport
- POST /webtools/control/showDateTime/ProgramExport
- POST /webtools/control/view/ProgramExport
- POST /webtools/control/TestService/ProgramExport
Which OFBiz Versions Are Affected?
All versions of Apache OFBiz up to 18.12.14 are vulnerable to CVE-2024-38856.
Exploit Available for CVE-2024-38856
Proof-of-Concept (PoC) exploit codes and scanners for the CVE-2024-38856 vulnerability are publicly available, increasing the urgency for organizations to act.
These exploits can be quickly weaponized by attackers, potentially leading to widespread malicious activity. Continuous monitoring of CVE and exploitation trends is essential for effective vulnerability management.
An example of an exploit and scanner can be found on GitHub. Additionally, a Shodan search reveals approximately 72,000 exposed Apache OFBiz instances, indicating the potential attack surface.
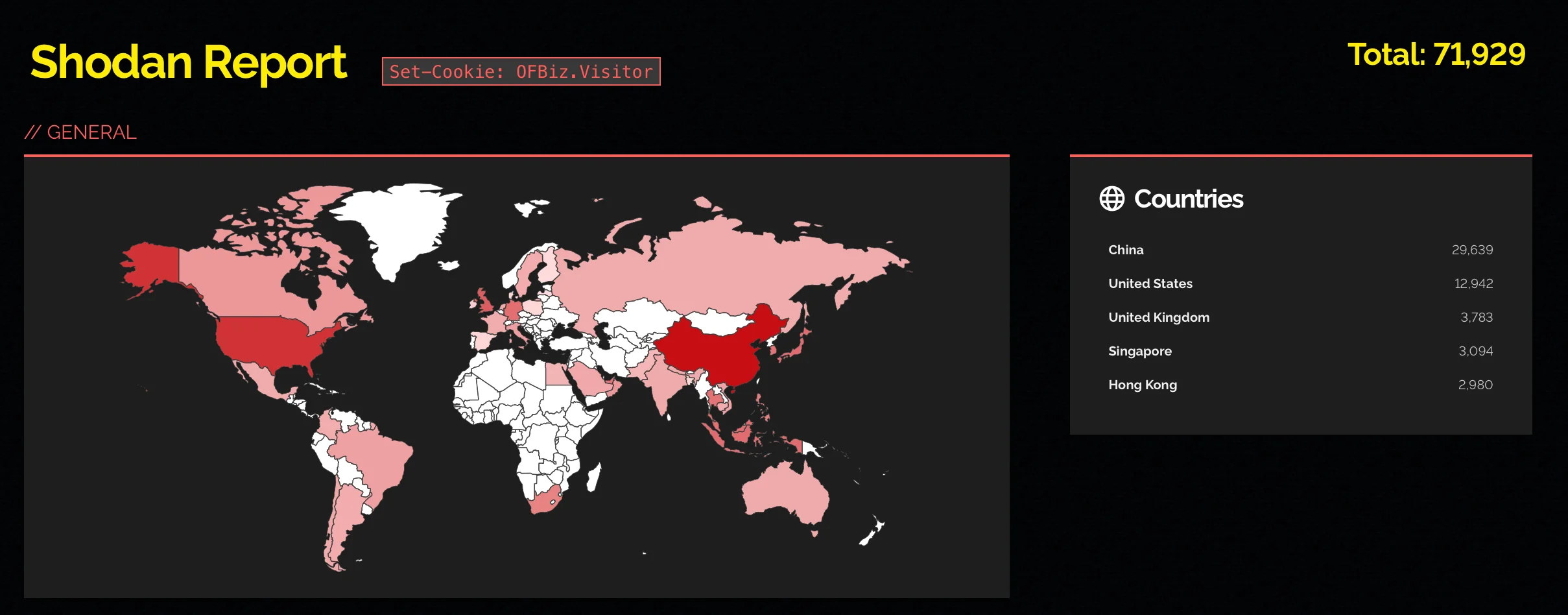
Shodan search results for exposed Apache OFBiz instances
Patch CVE-2024-38856 Now!
Organizations are strongly advised to upgrade to version 18.12.15 to mitigate this critical security threat. The latest updates and release notes can be found on the Downloads page of the Apache OFBiz website.
For further details and root cause analysis of the vulnerability, refer to the official research blog.
New RCE Vulnerability (CVE-2024-45195) Discovered in Apache OFBiz, Patch Now
A new vulnerability, CVE-2024-45195, has been discovered in Apache OFBiz software. This critical Remote Code Execution (RCE) flaw affects both Linux and Windows servers and was found to bypass previous patches for vulnerabilities CVE-2024-32113, CVE-2024-36104, and CVE-2024-38856.
The issue arises from a forced browsing weakness that allows unauthenticated attackers to exploit missing view authorization checks and execute arbitrary code on vulnerable servers.
CVE-2024-45195 essentially shares the same root cause as the prior vulnerabilities – controller-view map fragmentation – allowing attackers to execute code or SQL queries without authentication.
The latest OFBiz vulnerability has been patched in version 18.12.16 of OFBiz by adding necessary authorization checks. All OFBiz users are strongly advised to upgrade their installations immediately to prevent potential exploitation of this new vulnerability, which continues the security risks initially posed by CVE-2024-38856 and others.
To ensure continuous monitoring and enhance the protection of your digital assets, you can rely on SOCRadar’s Attack Surface Management (ASM) module.
The ASM module offers continuous, in-depth surveillance of your digital environment, enabling the identification and prioritization of security vulnerabilities. It provides detailed, actionable insights through timely alerts, assisting in effectively mitigating risks before they can be exploited.
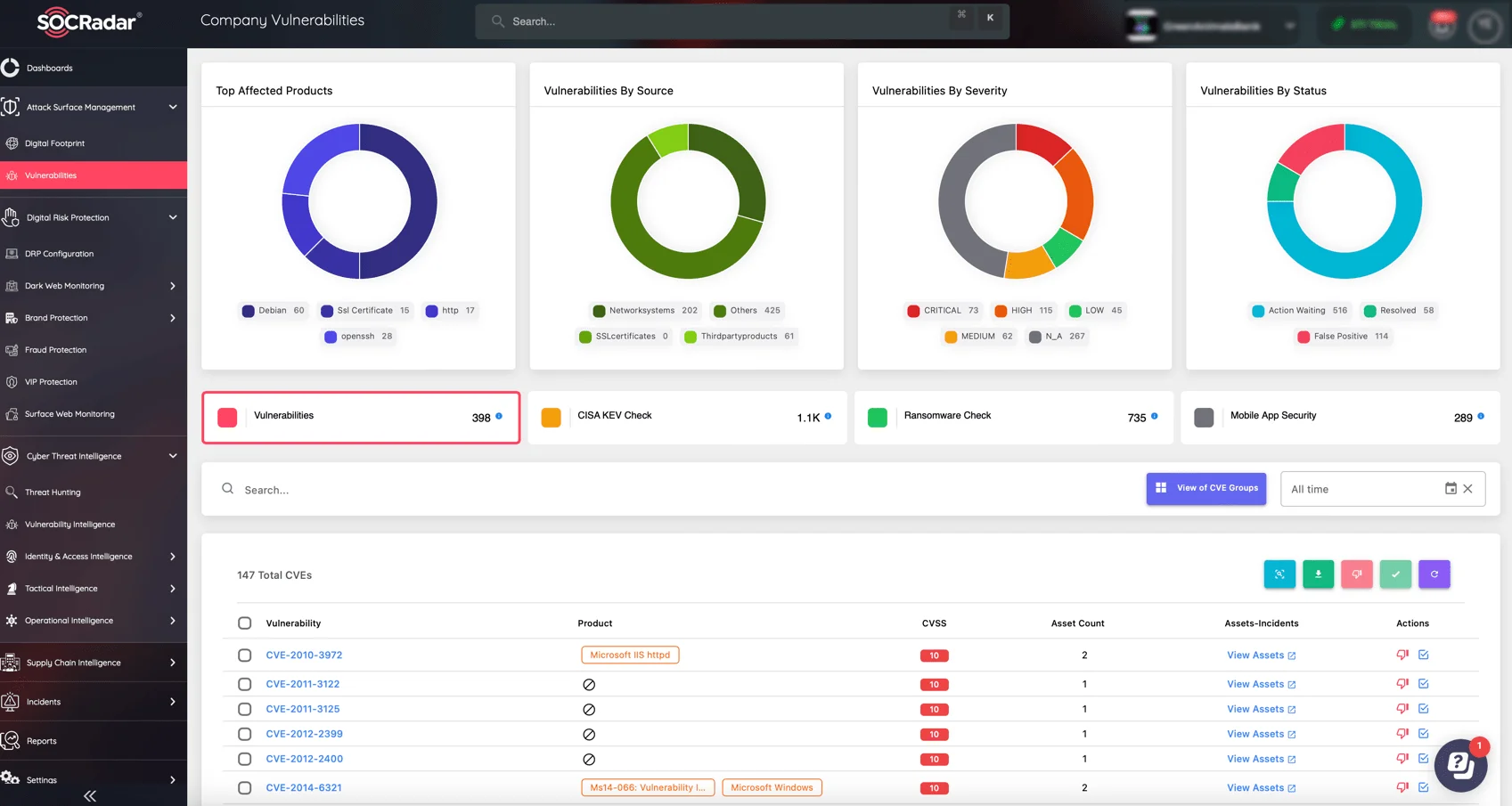
Monitor the vulnerabilities affecting your assets through SOCRadar’s Attack Surface Management (ASM) module, ensure quick response by your security team
By integrating the capabilities of the Vulnerability Intelligence and ASM modules, your organization can proactively manage and address emerging threats.



































