
Privilege Escalation Risks in ‘needrestart’ Utility Threaten Linux Systems; OSS-Fuzz Finds 26 Hidden Flaws
Recent findings have exposed high-severity flaws in the needrestart utility, a key component in Ubuntu Server installations.
The utility’s primary function is to check if a system or its services require a restart after software updates, especially when shared libraries are updated. Without a restart, older versions of libraries may remain in use, leaving systems vulnerable despite the updates.
While vital for system maintenance, the tool’s expanded capabilities and integration with Python and Ruby interpreters since 2014, have inadvertently introduced exploitable vulnerabilities. These vulnerabilities enable local privilege escalation, putting system integrity and security at risk.
Additionally, Google’s OSS-Fuzz platform marked a significant advancement, leveraging AI-powered fuzzing to identify 26 hidden vulnerabilities, including one in the popular OpenSSL library.
What Are the Vulnerabilities in the ‘needrestart’ Utility?
Recent findings have exposed five high-severity vulnerabilities in the needrestart utility, posing a serious risk to system security. These flaws allow unprivileged users to escalate their privileges and gain root access, granting full control over affected systems. Exploiting such access, attackers could compromise sensitive data, deploy malware, or disrupt operations entirely.
The root cause of these vulnerabilities lies in how needrestart interacts with interpreters such as Python and Ruby. In the case of CVE-2024-48990 and CVE-2024-48992, attackers can manipulate environment variables like PYTHONPATH and RUBYLIB, tricking needrestart into executing malicious code during interpreter initialization.
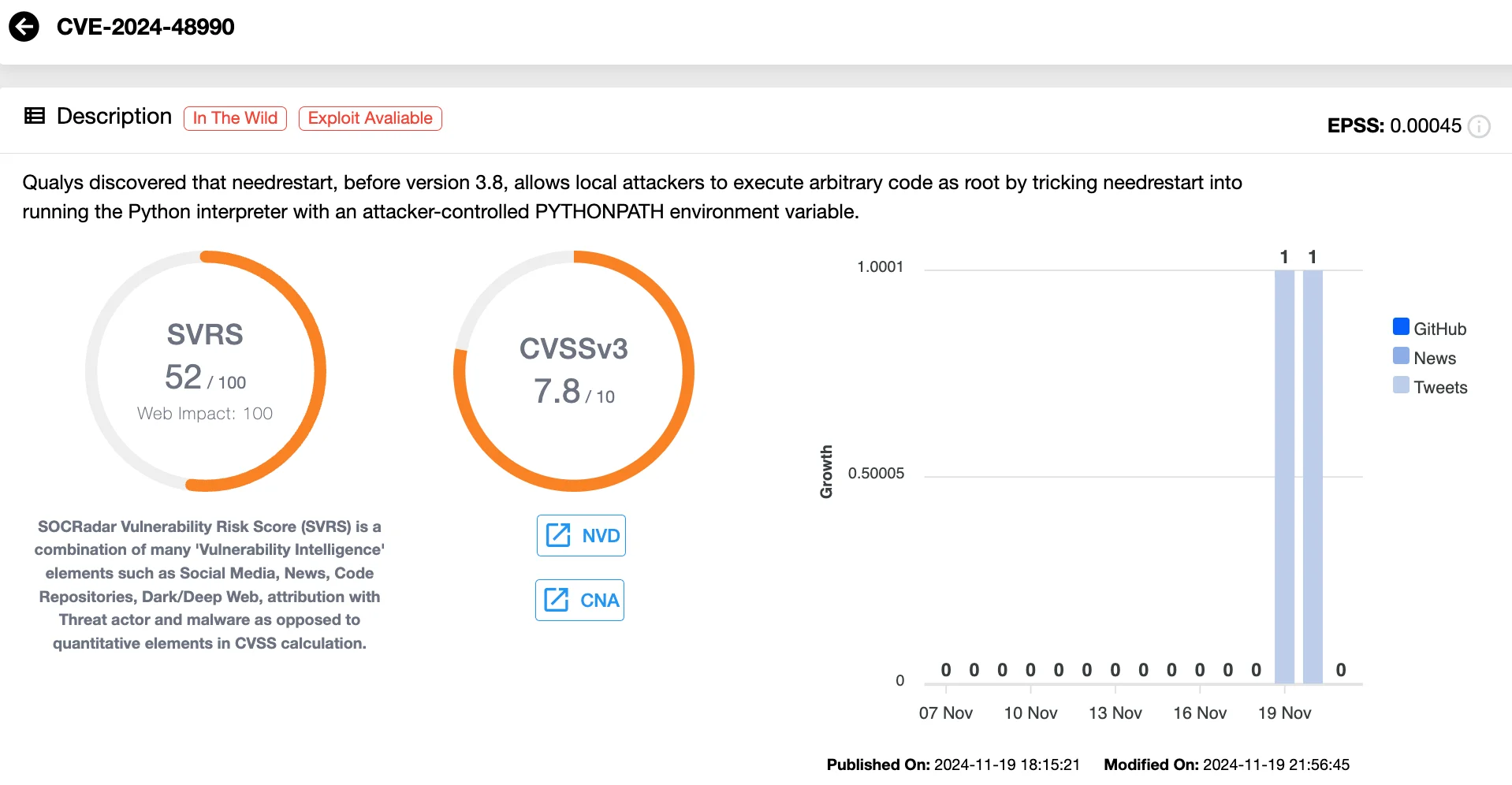
Details of CVE-2024-48990 (SOCRadar Vulnerability Intelligence) – According to the module, a PoC exploit for the flaw is already available.
For CVE-2024-48991, attackers exploit a time-of-check to time-of-use (TOCTOU) race condition within the Python interpreter’s initialization. Then, they can hijack the process to execute arbitrary commands, gaining unauthorized access to system functions.
Lastly, in the case of CVE-2024-10224 and CVE-2024-11003, needrestart’s interaction with the Module::ScanDeps Perl module is exploited to achieve root privileges. Attackers provide crafted inputs, which the module processes to execute malicious shell commands.
These vulnerabilities, except for CVE-2024-10224, are rated as high severity with CVSS scores of 7.8. CVE-2024-10224, with a medium severity rating of 5.3, does not independently enable privilege escalation. However, it becomes a serious issue when combined with CVE-2024-11003, as needrestart passes attacker-controlled inputs to Module::ScanDeps with root permissions.
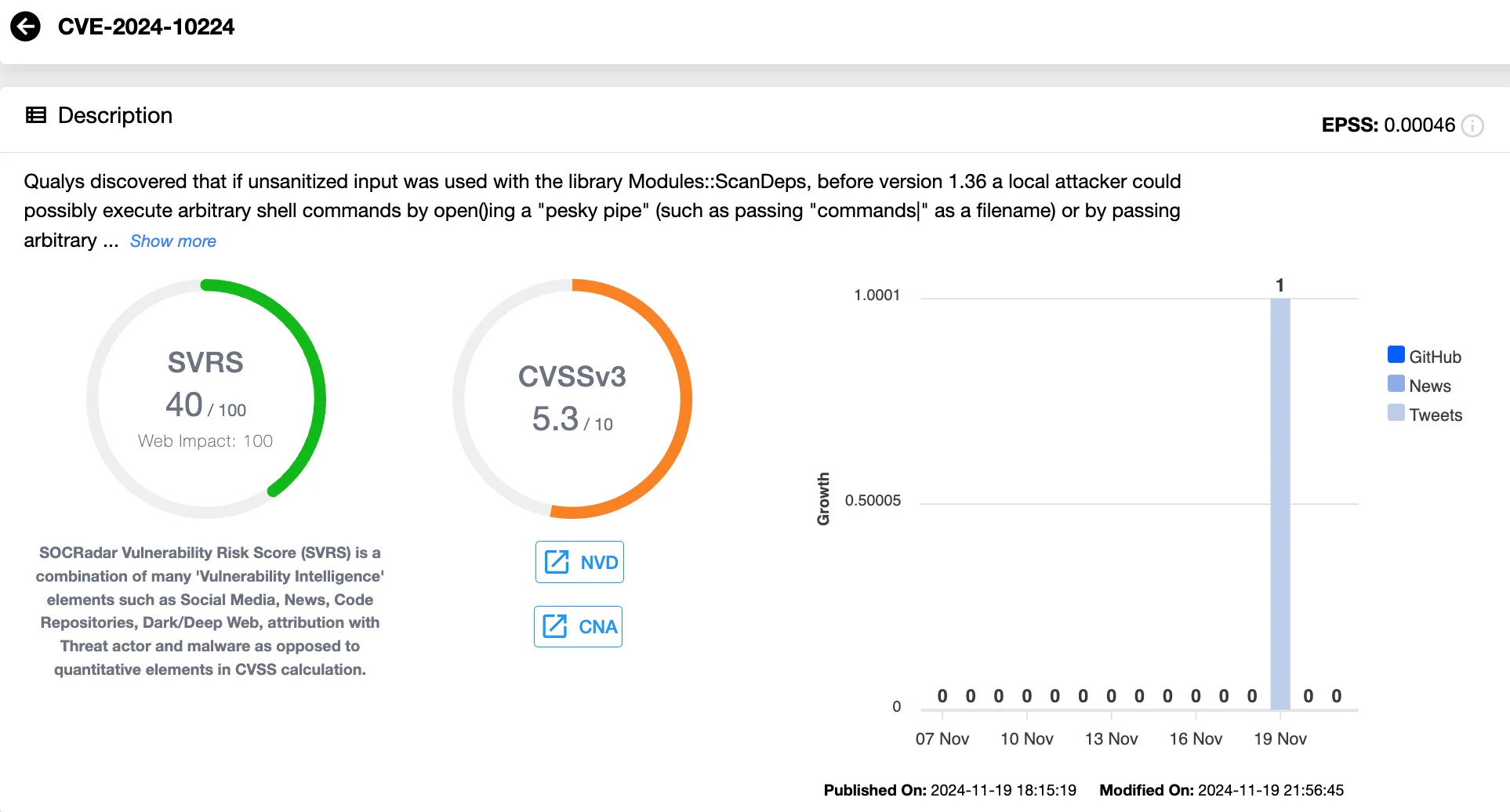
Details of CVE-2024-10224 (SOCRadar Vulnerability Intelligence)
Another alarming aspect of these flaws is their accessibility. No user interaction is required for exploitation – once attackers gain local access, they can easily exploit these CVEs.
Which Ubuntu Releases Are Impacted?
The needrestart vulnerabilities affect multiple Ubuntu releases, as well as other Linux distributions including Debian, including both server and desktop environments where the utility is installed. The impacted versions are tied to specific package releases:
- needrestart: Versions up to 3.6-8ubuntu4
- libmodule-scandeps-perl: Versions below 1.35-1
These vulnerabilities are particularly concerning for Ubuntu Server installations of Jammy (22.04), Noble (24.04), and Oracular (24.10), where needrestart is installed by default. Desktop installations and older server versions, such as Focal (20.04), are only vulnerable if the utility was manually installed.
Check if Your System Is Vulnerable
Users can verify if their system is running an affected version of needrestart or libmodule-scandeps-perl by running the following command:
apt list –installed | grep “^(needrestart|libmodule-scandeps-perl)”
Compare the output with the affected versions listed above. If your system matches any of these versions, immediate action is required to mitigate potential risks.
How Can You Address the Vulnerabilities in needrestart?
Addressing the needrestart vulnerabilities is critical to maintaining system security and preventing potential exploitation. Users are strongly advised to take the following actions:
The most effective solution is to update the affected packages to their patched versions. To update your system, run:
sudo apt update && sudo apt upgrade
Alternatively, if a full upgrade isn’t feasible, target the specific vulnerable packages:
sudo apt update && sudo apt install –only-upgrade needrestart libmodule-scandeps-perl
For systems with unattended-upgrades enabled (default in Ubuntu 16.04 LTS and later), these patches will be applied automatically within 24 hours.
If updates cannot be applied immediately, a temporary mitigation is to disable the vulnerable interpreter scanning feature in needrestart. To do this:
- Edit the configuration file: sudo nano /etc/needrestart/needrestart.conf
- Add or modify the following line: $nrconf{interpscan} = 0;
- Save and exit the editor.
This disables the interpreter scanning feature, reducing exposure to exploitation. However, this is not a permanent solution, and you should restore the original configuration after applying the updates.
Act Now – Update Vulnerable Systems Without Delay
With the high-risk potential of needrestart vulnerabilities, immediate updates are essential, particularly for server images like Jammy, Noble, and Oracular where needrestart is installed by default. In environments where the utility was added manually, verify its installation and address vulnerabilities promptly to avoid potential exploits.
For a proactive approach to managing vulnerabilities, SOCRadar’s Vulnerability Intelligence and Attack Surface Management (ASM) modules work together, enabling your organization to:
- Identify critical vulnerabilities early with real-time alerts and actionable insights.
- Prioritize risks to focus on vulnerabilities that pose the greatest threat.
- Visualize your attack surface, uncovering exposed assets that could be targeted by attackers.
- Streamline mitigation efforts by integrating seamlessly into your security workflows for faster resolution.
Quickly address issues like needrestart vulnerabilities before attackers exploit them and strengthen your defenses against evolving threats.
SOCRadar’s Vulnerability Intelligence module page
Stay informed and secure with SOCRadar’s intelligence-driven platform. Also, for more technical information on these vulnerabilities and remediation steps, refer to the following resources:
Acting promptly can safeguard systems from privilege escalation and broader compromises.
AI Finds Decades-Old OpenSSL Vulnerability with Fuzzing (CVE-2024-9143 and More)
After examining the critical vulnerabilities in needrestart, attention now shifts to 26 previously hidden vulnerabilities identified by Google’s OSS-Fuzz platform. Leveraging AI-powered fuzzing techniques, these findings highlight AI’s potential to uncover long-standing security flaws that traditional methods have overlooked.
One key discovery, CVE-2024-9143, involves an out-of-bounds memory flaw in OpenSSL’s elliptic curve APIs. This vulnerability, capable of enabling attackers to execute arbitrary code or crash applications, had remained undetected for decades until its identification through AI-powered fuzzing.
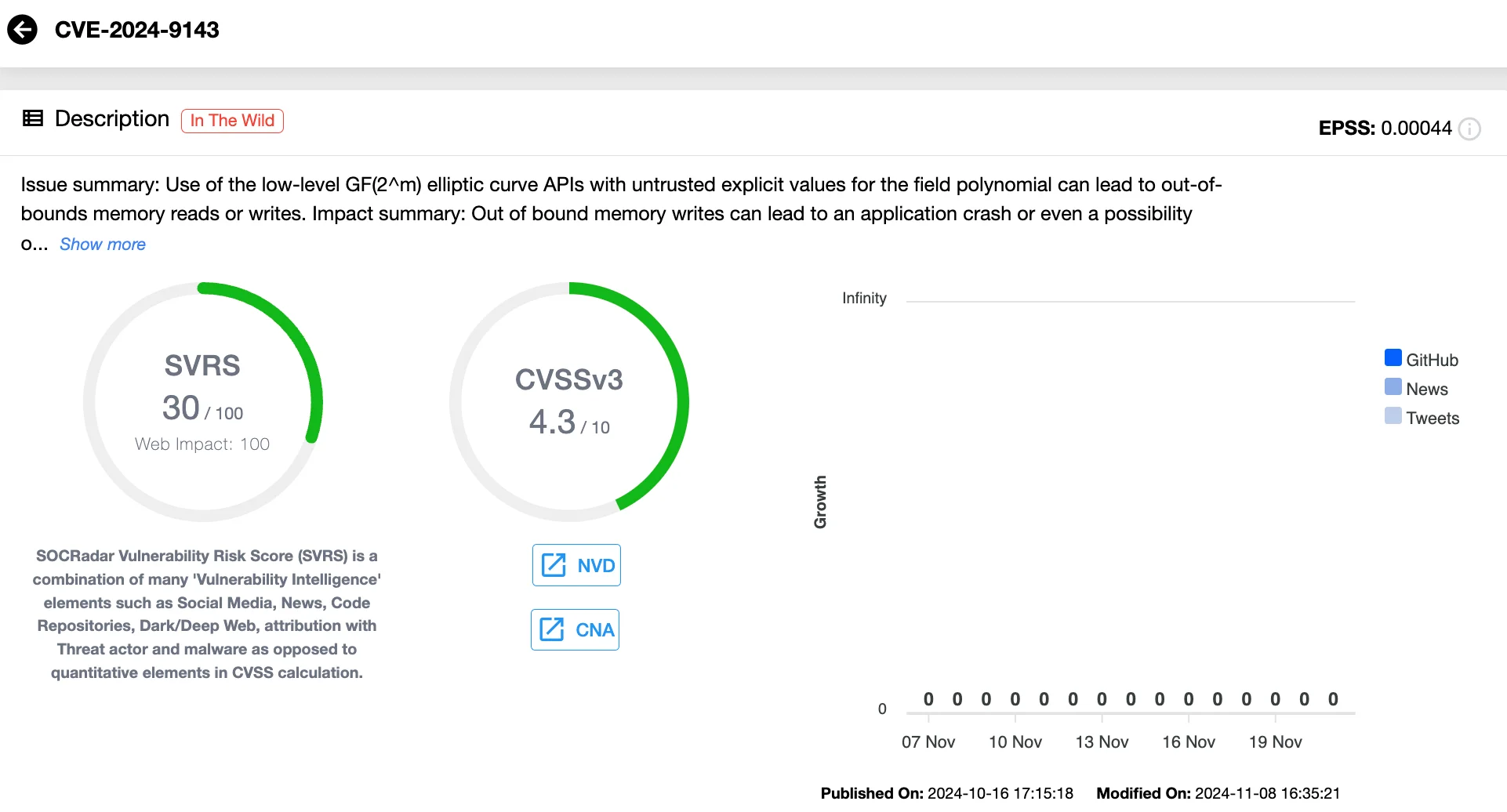
Details of CVE-2024-9143 (SOCRadar Vulnerability Intelligence)
Since August 2023, OSS-Fuzz has utilized Large Language Models (LLMs) to improve fuzz target coverage, uncovering flaws even in code previously tested by humans. Google’s future plans for OSS-Fuzz include advancing triaging automation for reliable vulnerability reporting, integrating debugging tools for quicker resolutions, and eventually automating patch generation.
For further details, visit Google’s security blog.





































