Operational Intelligence
Gain a powerful ally to transform raw threat data into a powerful weapon in your security arsenal.
Master the art of adversary tracking with SOCRadar’s Operational intelligence. Get dynamic, real-time insights into operational trends and effectively adapt to the ever-changing threat landscape.
A Real-Time Overview: Track Actors, Attacks, and Reports
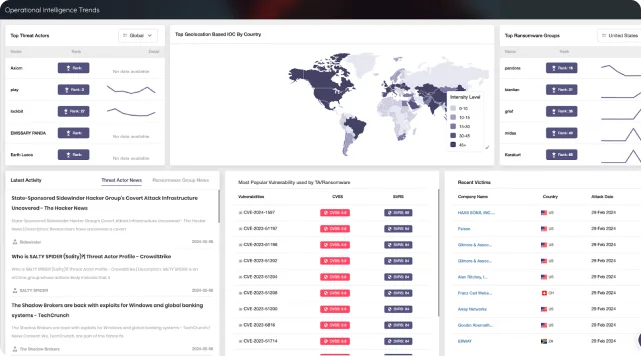
SOCRadar equips you with real-time awareness. Operational Intelligence Trends Dashboard provides dynamic, real-time insights into;
- The rise and fall of prominent ransomware groups
- Geographical trends in threat actor activity and targeted regions
- Various threat reports to gain a holistic understanding of the evolving threat landscape
- Most Popular Vulnerabilities used by threat actors/Ransomware groups
- Recent Victims
- Latest Campaigns
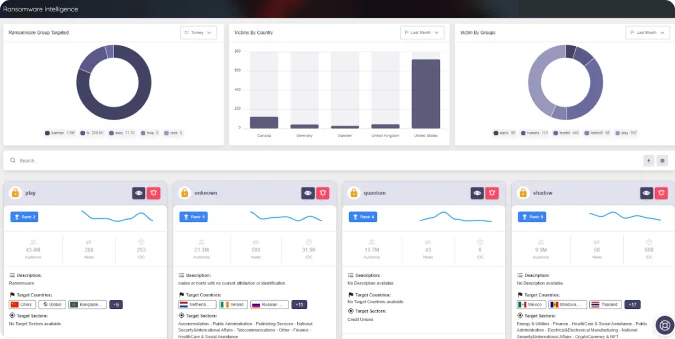
Combat Evolving Ransomware
Ransomware isn’t just a threat; it’s one of the top cyber threats today. That’s why SOCRadra provides a dedicated ransomware intelligence page, empowering you to stay ahead of these ever-evolving attacks.
SOCRadar empowers you to fight against ransomware with ‘detailed ransomware group profiles,’ ‘MITRE ATT&CK visualizer,” Indicators of Compromise (IOCs),’ and more.
See What Matters Most
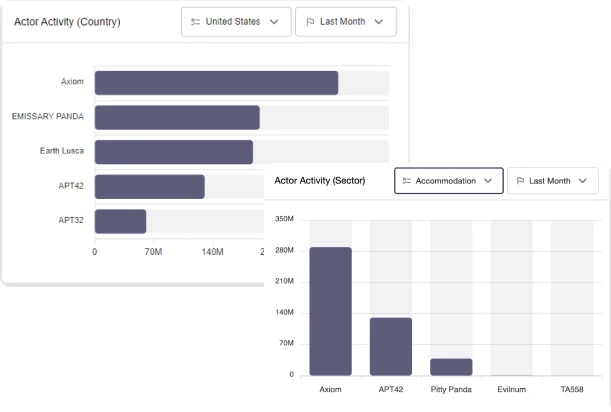
Map your cyber threat landscape tailored to you and confidently navigate the evolving threat landscape.
The SOCRadar operational intelligence module empowers you to see beyond generic threats in both the threat actor intelligence and ransomware intelligence pages. We provide a comprehensive overview, including the most targeted countries and sectors, along with customized data relevant to your specific needs. Customized data allows you to gain invaluable insights into the most prominent threat actor/ransomware groups operating within your industry or country. Filter and explore even deeper to uncover additional details crucial for your security posture.
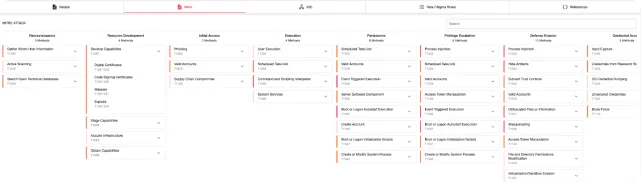
MITRE ATT&CK Framework-Based Mapping Approach
The MITRE ATT&CK framework is an essential tool for cybersecurity professionals. It provides a constantly updated knowledge base of adversary tactics and techniques, allowing you to stay one step ahead of evolving threats.
SOCRadar empowers you to leverage the power of MITRE ATT&CK with actionable visualizations. Within detailed threat actor profiles, SOCRadar’s visualizations translate the raw data into actionable insights. That visualization allows users to apply sequential procedures and align their response strategies with threat actors’ tactics, thus maximizing their effectiveness in mitigating threats.