
Pumakit: A Sophisticated Linux Rootkit Targeting Critical Infrastructure
In recent months, Pumakit, a stealthy Linux rootkit, has emerged as a significant threat, targeting critical infrastructure across industries such as telecommunications, finance, and national security.
Identified by Elastic Security Labs, Pumakit operates at the kernel level, employing advanced evasion techniques that make detection nearly impossible. Its capabilities highlight the growing sophistication of malware threats against Linux environments.
Technical Overview of Pumakit
Pumakit is a sophisticated rootkit designed to manipulate system-level operations, making it difficult to detect and remove. By targeting kernel-level processes, it ensures stealthy and persistent control over compromised systems. Below are the key capabilities that enable its effectiveness:
- System Call Interception: Pumakit modifies kernel-level system calls to manipulate file and network activity, evading traditional monitoring tools and remaining hidden from administrators and security systems.
- Persistence Mechanisms: Embedded within the kernel, Pumakit retains its functionality even after system reboots, allowing for long-term exploitation.
- Log Evasion: The rootkit tampers with logging mechanisms, concealing malicious activities and complicating forensic investigations.
- Data Exfiltration and Remote Access: the campaign facilitates data theft and provides attackers with a backdoor, allowing for continued access and exploitation.
- Evasion Techniques: The rootkit uses advanced anti-detection strategies, including disabling security tools and avoiding static or dynamic analysis methods. By masking its processes and suppressing security alerts, it operates covertly, even in highly monitored environments.
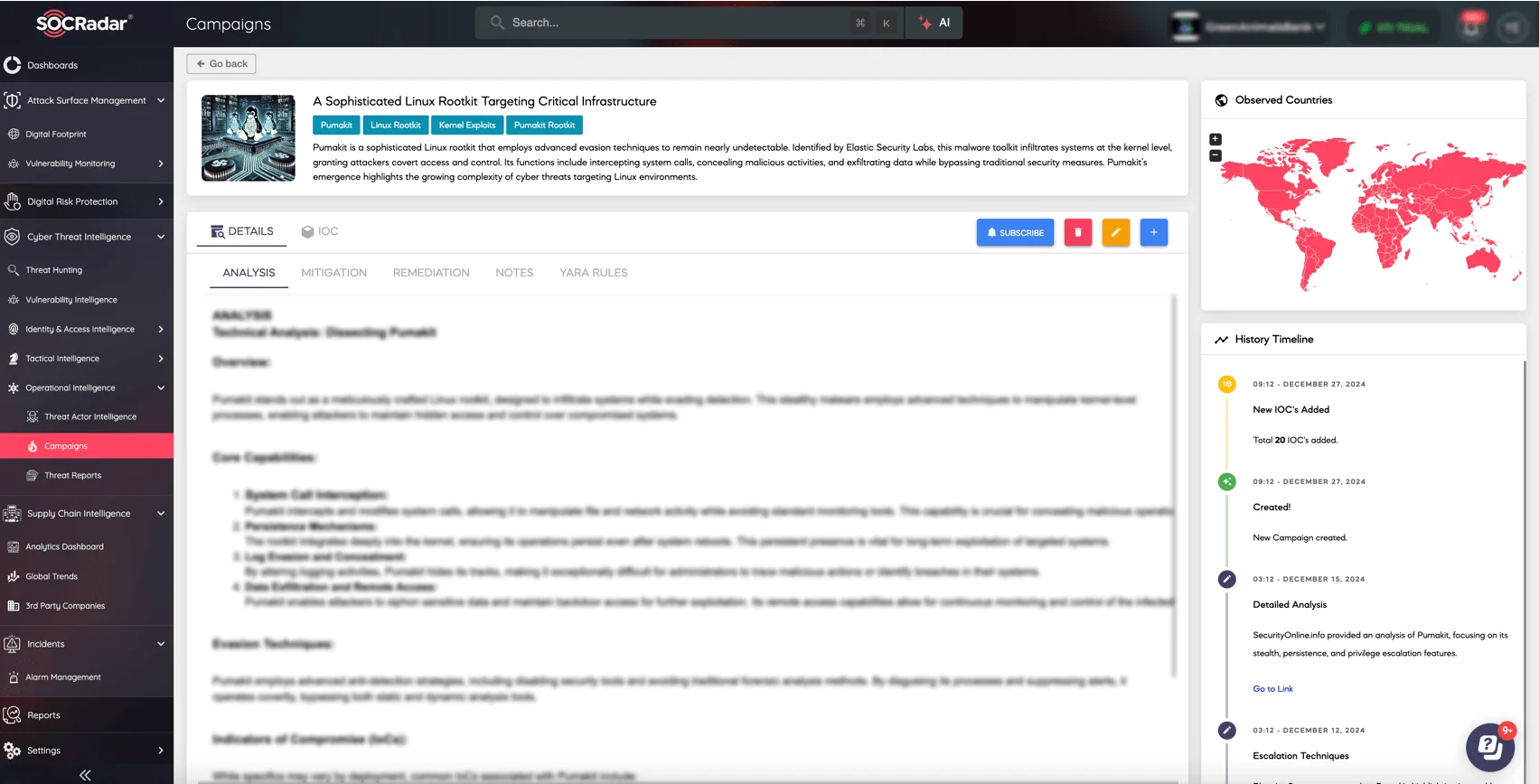
Pumakit Campaign page on the SOCRadar XTI platform
To understand the methods and strategies used in the Pumakit campaign, visit SOCRadar LABS’ Campaigns page. There, you can explore comprehensive reports on this and various other malicious operations and access valuable intelligence to strengthen your organization’s defense measures.
Indicators of Compromise (IoC)
| Indicator Type | Details |
| Kernel-level modules | Modules with unusual names or attributes |
| System modifications | Unexpected changes to system call handlers |
| Hidden assets | Concealed files, processes, or network connections |
| Suspicious hosts | 89.23.113.204 and domains like rhel.opsecurity1.art |
| File Hashes | Examples: 4375998ea157a8a21e1ead13052bad8a, 810f4b422b9c0a6718e9461de3a2edda |
Mitigation Strategies
Below are some of the techniques used in the Pumakit campaign, along with recommended mitigation methods to protect your organization from these sophisticated attacks:
| ID | Technique | Recommended Mitigation |
| T1574.006 | Hijack Execution Flow: Dynamic Linker Hijacking | Execution Prevention: Block malicious libraries and payloads through robust application control solutions. |
| T1055 | Process Injection | Behavior Prevention on Endpoint: Configure security solutions to detect process injection activities. |
| T1078.001 | Valid Accounts: Default Accounts | Multi-factor Authentication (MFA): Enforce MFA for default accounts to prevent unauthorized access. |
| T1562.001 | Impair Defenses: Disable or Modify Tools | Restrict File and Registry Permissions: Limit permissions to avoid tampering with security tools and configurations. |
Improvement Recommendations
To effectively mitigate the risk of Pumakit and similar threats, the following improvement recommendations are essential:
- System Hardening: Regularly apply patches and updates to minimize exploitable vulnerabilities.
- Access Management: Limit administrative access to critical systems and enforce strict account policies to reduce unauthorized access.
- Monitoring and Analytics: Implement continuous behavior analysis and anomaly detection tools to identify suspicious activity early.
- Incident Response Planning: Establish robust protocols to effectively handle rootkit infections and system compromises, ensuring a swift and coordinated response.
YARA Rule for Detection
rule Linux_Trojan_Pumakit_b86138c3 {
meta:
author = “Elastic Security”
id = “b86138c3-c7b3-4f86-a695-bf8195f2458c”
fingerprint = “c5cba5975be26ebcb14871527533d1f8f082b37f2d8b509904b608569fdb8b24”
creation_date = “2024-12-09”
last_modified = “2024-12-11”
threat_name = “Linux.Trojan.Pumakit”
reference_sample = “30b26707d5fb407ef39ebee37ded7edeea2890fb5ec1ebfa09a3b3edfc80db1f”
severity = 100
arch_context = “x86, arm64”
scan_context = “file, memory”
license = “Elastic License v2”
os = “linux”
strings:
$str1 = “PUMA %s”
$str2 = “Kitsune PID %ld”
$str3 = “/usr/share/zov_f”
$str4 = “zarya”
$str5 = “.puma-config”
$str6 = “ping_interval_s”
$str7 = “session_timeout_s”
$str8 = “c2_timeout_s”
$str9 = “LD_PRELOAD=/lib64/libs.so”
$str10 = “kit_so_len”
$str11 = “opsecurity1.art”
$str12 = “89.23.113.204”
condition:
4 of them
}
Conclusion
Pumakit highlights the advanced threats targeting critical infrastructure today, using stealthy, kernel-level techniques to evade detection. This highlights the importance of implementing proactive defense strategies. With SOCRadar Extended Threat Intelligence (XTI), organizations can gain actionable insights, enabling early detection and swift mitigation of such threats.
Through its Cyber Threat Intelligence capabilities, SOCRadar offers valuable insights into Pumakit’s and similar campaigns’ Tactics, Techniques, and Procedures (TTPs), equipping organizations to outpace adversaries. By incorporating modules like Advanced Dark Web Monitoring and Attack Surface Management, cybersecurity teams can stay ahead of evolving malware campaigns and protect essential assets.
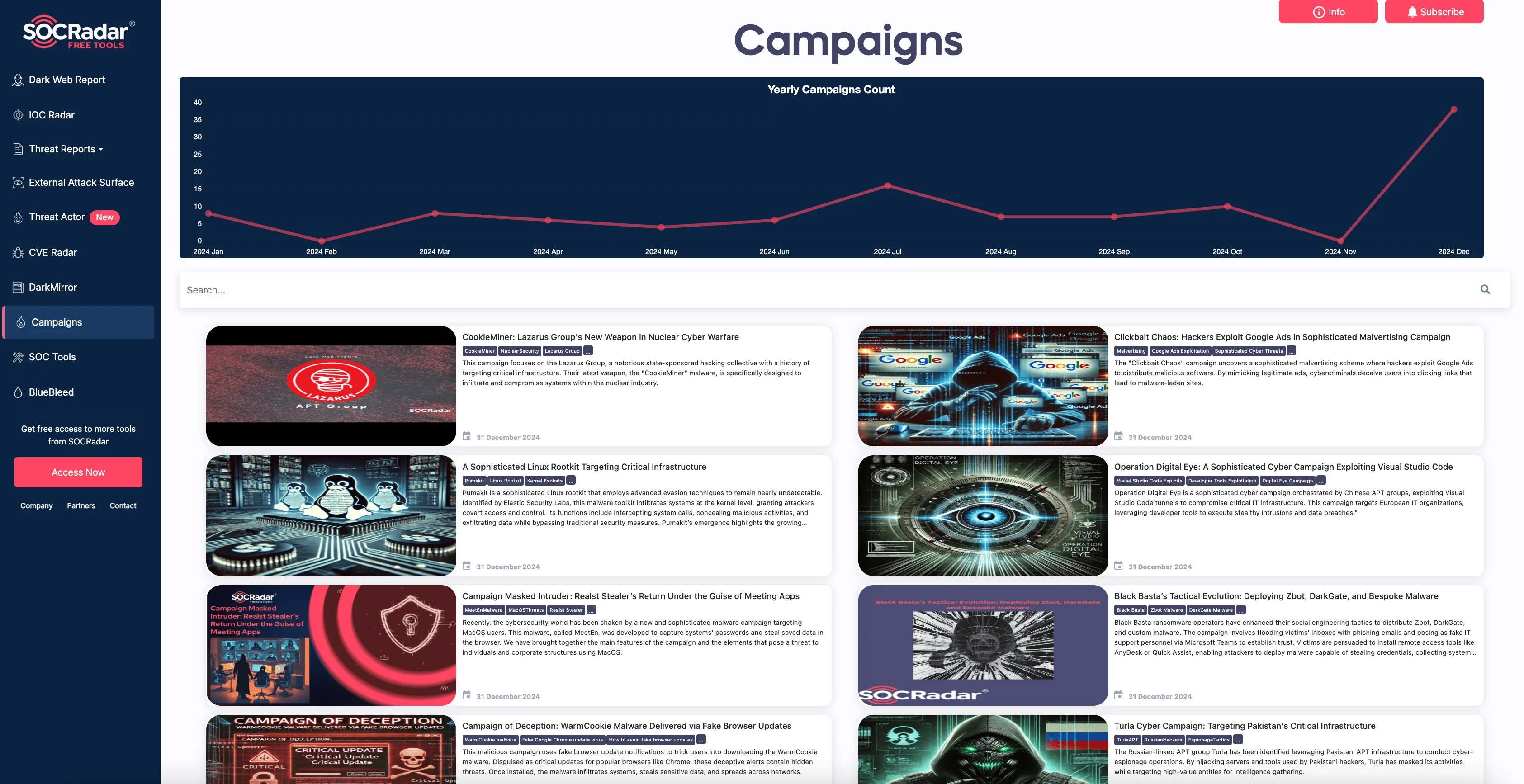
Campaigns page, available on SOCRadar LABS
SOCRadar LABS also provides a dedicated Pumakit campaign page, delivering detailed analysis, IoC data, and up-to-the-minute information to help businesses prepare for and counteract this persistent threat.




































