
Qualcomm Addresses Exploited Zero-Day and a Critical RCE in October 2024 Security Bulletin
Just yesterday, Qualcomm rolled out its latest monthly security bulletin, addressing numerous vulnerabilities, 5 affecting proprietary software and 15 related to open-source components.
Of note, the advisory highlights one critical vulnerability from its proprietary issues, the only one rated as critical, and another from the open-source vulnerabilities that may be under active exploitation, as flagged by Google’s Threat Analysis Group (TAG). These issues impact key products like the widely used Snapdragon mobile platforms and FastConnect solutions.
Qualcomm, a leading global technology company, designs wireless telecommunications products and services, including processors, chipsets, and SDKs. Since its acquisition of VMware in 2022, Qualcomm has also expanded its influence across the cloud computing and virtualization sector.
In this blog post, we’ll examine the latest security vulnerabilities patched by Qualcomm, explore their implications, and point out how you can protect your systems from these potential threats.
CVE-2024-43047: Zero-Day Vulnerability in Qualcomm FastConnect
One of the vulnerabilities addressed in the October 2024 bulletin is CVE-2024-43047, a high-severity Use-After-Free flaw in the DSP Service (CVSS Score: 7.8). This vulnerability, discovered in late July 2024, has been confirmed to be under limited, targeted exploitation in the wild, according to reports from Google Project Zero, Amnesty International Security Lab, and Google’s Threat Analysis Group (TAG).
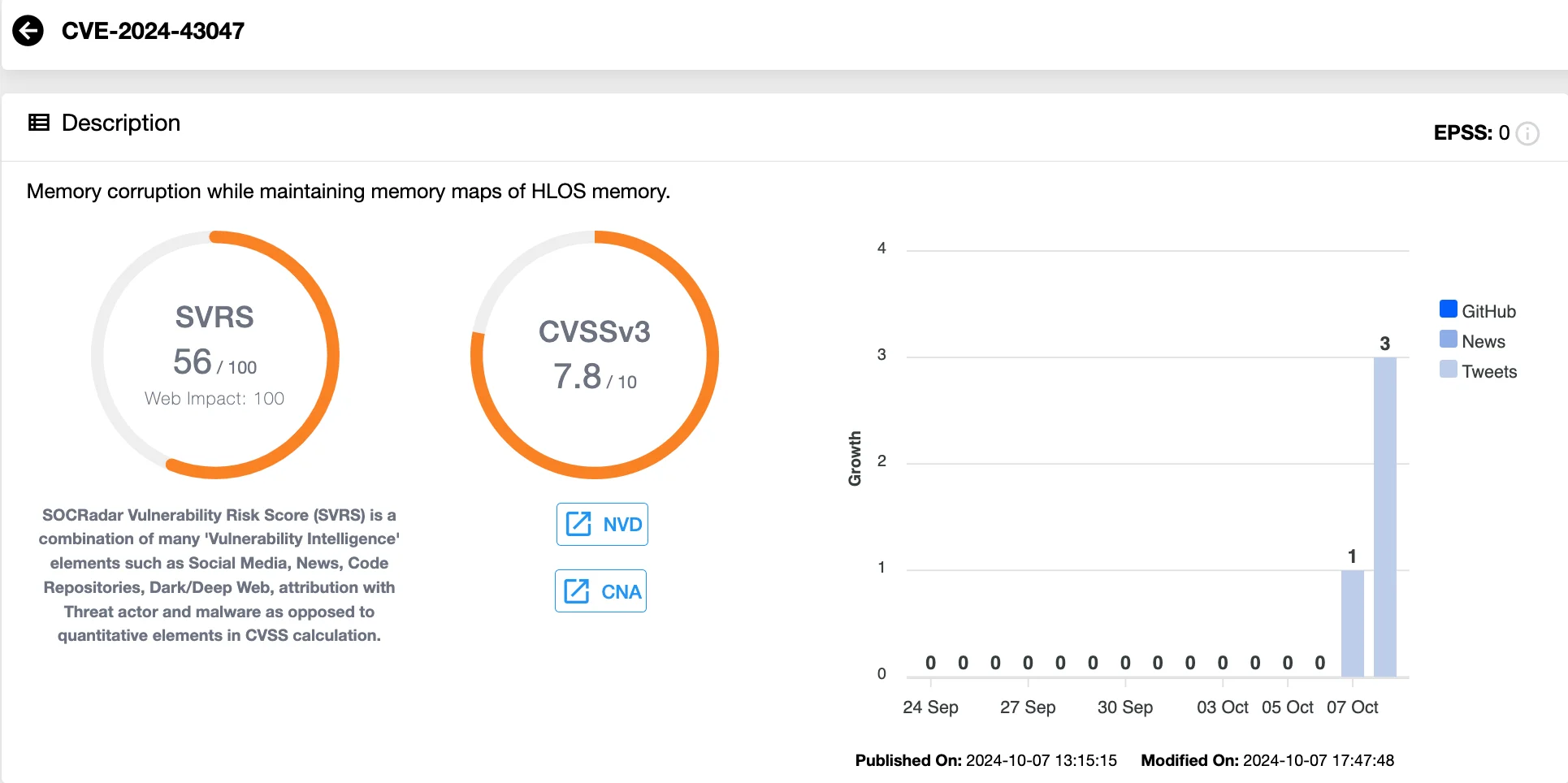
Details of CVE-2024-43047 (SOCRadar Vulnerability Intelligence)
CVE-2024-43047 results in memory corruption due to improper handling of memory maps in the High-Level Operating System (HLOS) memory, posing a significant risk to system integrity. Qualcomm’s advisory emphasizes the urgency of patching, as the vulnerability is actively exploited.
Patches for this vulnerability, affecting the FASTRPC driver, have been provided to OEMs, with Qualcomm strongly recommending immediate deployment. The fix addresses the handling of DMA handle references, ensuring that the map for the FD is only freed when a valid reference is found, effectively mitigating the Use-After-Free condition. See the patch commit here for more details.
Which Chipsets Are Affected by CVE-2024-43047?
The CVE-2024-43047 vulnerability impacts a broad range of Qualcomm chipsets, spanning across mobile platforms, video collaboration platforms, modem systems, and audio components. Some of the affected products include:
- FastConnect Series: 6700, 6800, 6900, 7800
- QCA Series: QCA6174A, QCA6391, QCA6426, QCA6436, QCA6574AU, QCA6595, QCA6688AQ, QCA6696
- QCS Series: QCS410, QCS610, QCS6490
- Snapdragon Mobile Platforms: Snapdragon 660, 680 4G, 685 4G (SM6225-AD), 8 Gen 1, 865 5G, 870 5G, 888 5G
- Snapdragon Auto: Auto 5G Modem-RF, Auto 5G Modem-RF Gen 2
- Video Collaboration Platforms: Qualcomm® VC1 and VC3
- Audio and Wireless: WCD9335, WCN3980, WSA8810
The list here is not exhaustive; many other chipsets from Qualcomm are also impacted. Users with affected devices should update their Snapdragon components to the latest firmware version as soon as possible to protect against potential exploitation.
Staying ahead of such security threats is a daily challenge, especially as new vulnerabilities emerge rapidly. Without consistent monitoring, organizations risk leaving critical security gaps open to attackers. Tracking vulnerabilities and following attacker trends helps maintain proactive defenses.
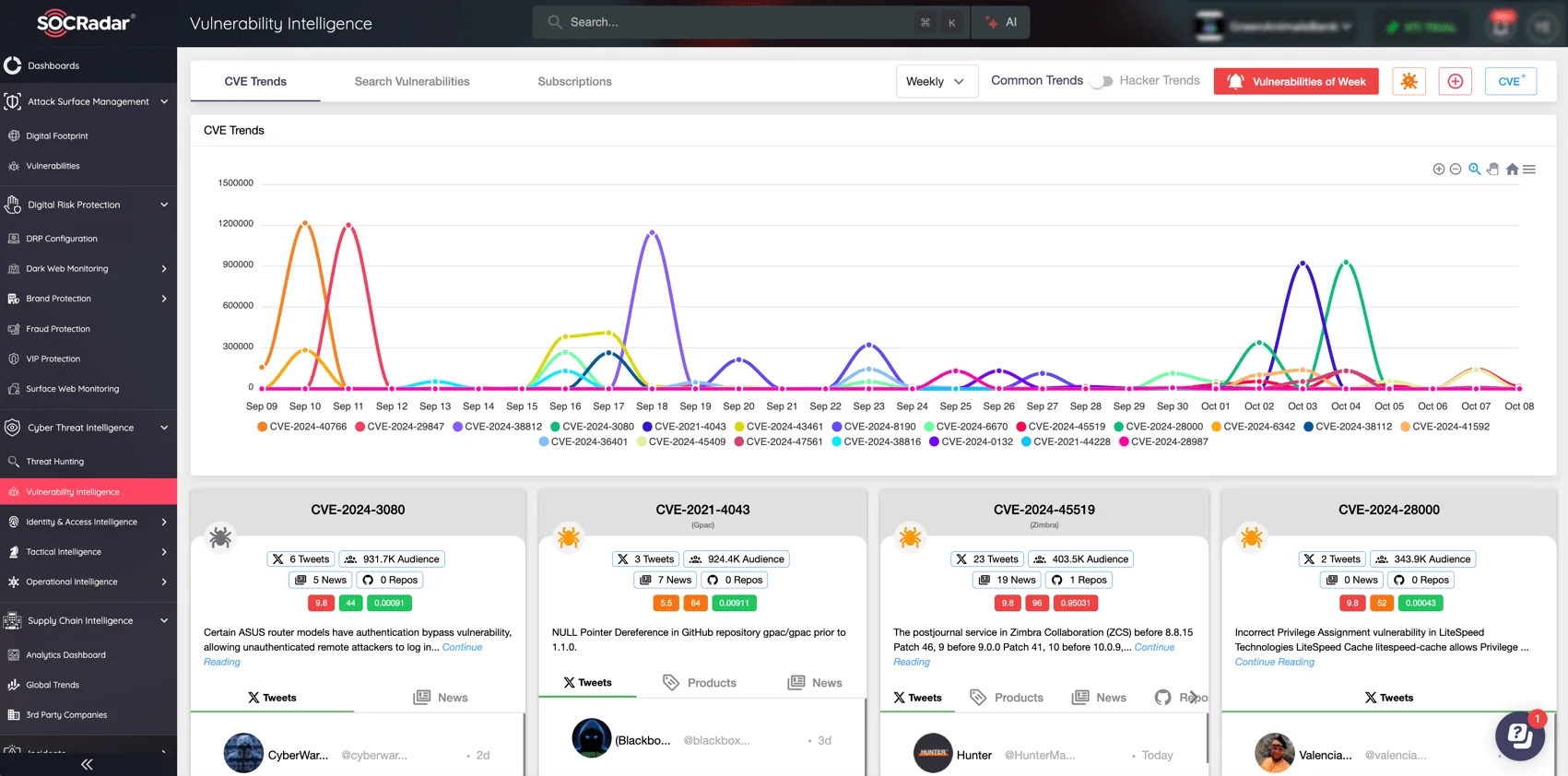
SOCRadar’s Vulnerability Intelligence module
With SOCRadar’s Vulnerability Intelligence module, you can stay informed with real-time alerts about the latest security threats. SOCRadar continuously monitors vulnerabilities, exploit updates, and hacker trends, helping you prioritize risks and make timely updates, ensuring that your systems remain secure in an evolving threat landscape.
CVE-2024-33066: Critical RCE Vulnerability in SnapDragon
Another significant issue addressed in Qualcomm’s advisory is CVE-2024-33066, a critical vulnerability with a CVSS score of 9.8. This flaw, found in the WLAN Resource Manager, arises from improper input validation.
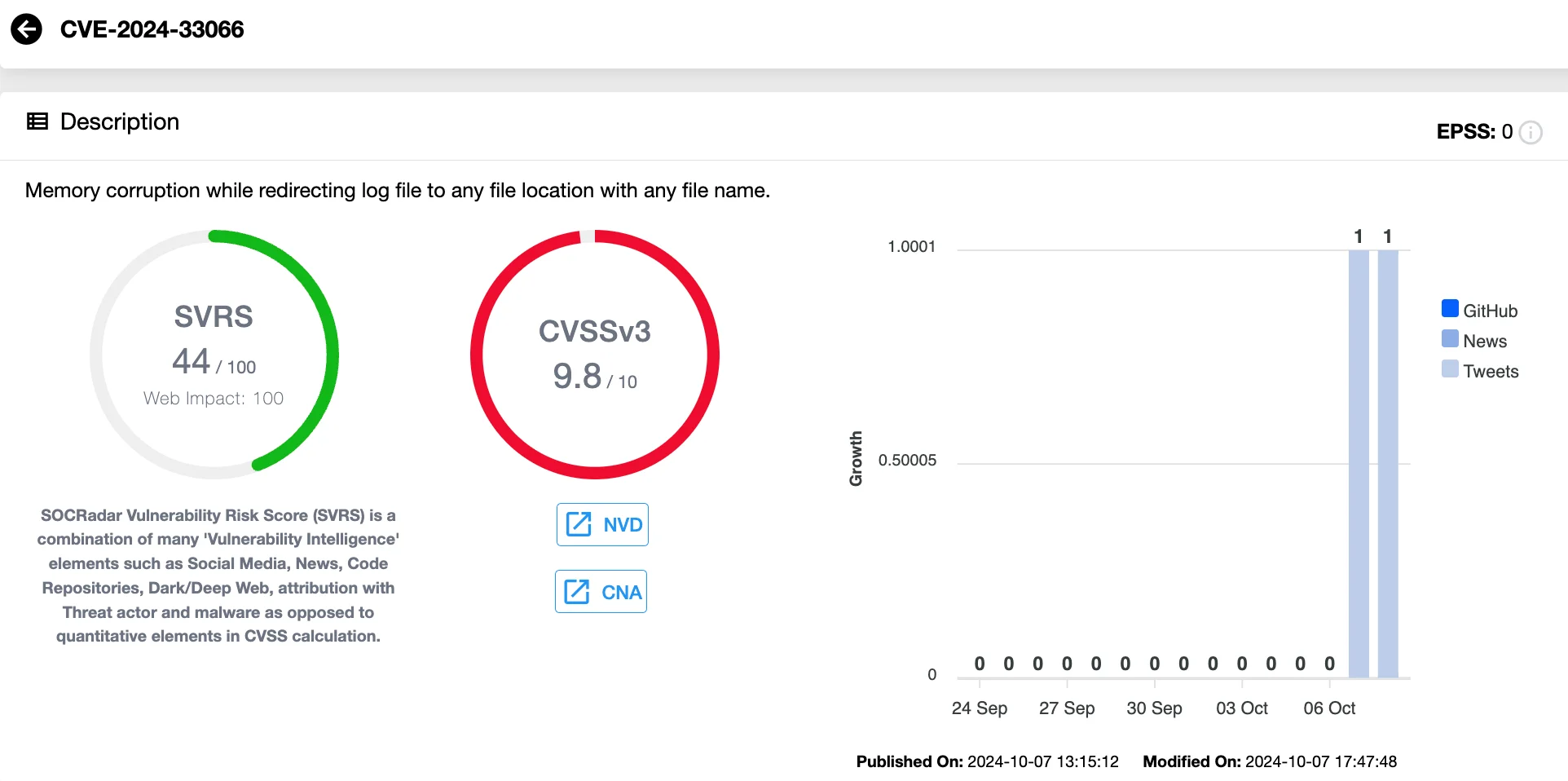
Details of CVE-2024-33066 (SOCRadar Vulnerability Intelligence)
If exploited, CVE-2024-33066 could lead to memory corruption by redirecting log files to arbitrary locations with any file name. This creates an opportunity for attackers to execute Remote Code Execution (RCE), potentially allowing them to fully compromise the affected device.
The other issue to note of addressed in the Qualcomm advisory is the critical CVE-2024-33066 (CVSS Score: 9.8) vulnerability. Residing in the WLAN Resource Manager, and stemming from improper input validation, CVE-2024-33066 could lead to memory corruption while redirecting log file to any file location with any file name. This could allow attackers to perform Remote Code Execution (RCE), potentially leading to a complete takeover of the device.
Which Chipsets Are Affected by CVE-2024-33066?
The following chipsets are impacted by the flaw:
- Immersive Home Platforms: 214, 216, 316, 318, 3210, 326
- IPQ Series: IPQ5010, IPQ5028, IPQ5300, IPQ5302, IPQ5312, IPQ5332, IPQ6000, IPQ6010, IPQ6018, IPQ6028, IPQ8070A, IPQ8071A, IPQ8072A, IPQ8074A, IPQ8076, IPQ8076A, IPQ8078, IPQ8078A, IPQ8173, IPQ8174, IPQ9008, IPQ9554, IPQ9574
- QCA Series: QCA4024, QCA8075, QCA8081, QCA8082, QCA8084, QCA8085, QCA8386, QCA9888, QCA9889
- QCF Series: QCF8000, QCF8001
- QCN Series: QCN5022, QCN5024, QCN5052, QCN5122, QCN5124, QCN5152, QCN5154, QCN5164, QCN6023, QCN6024, QCN6112, QCN6122, QCN6132, QCN6402, QCN6412, QCN6422, QCN6432, QCN9000, QCN9022, QCN9024, QCN9070, QCN9072, QCN9074, QCN9100, QCN9160, QCN9274
- QXM Series: QXM8083
- SDX Series: SDX55, SDX65M
- Snapdragon: X65 5G Modem-RF System
Other Notable Vulnerabilities From Qualcomm’s October 2024 Security Bulletin
In addition to the critical issues, the October 2024 bulletin addresses several high-severity vulnerabilities. These include memory corruption vulnerabilities in proprietary software, such as CVE-2024-23369, triggered by invalid length inputs from HLOS, and CVE-2024-33065, which involves memory corruption during snapshot creation by the camera driver.
For open-source components, the advisory highlights severe vulnerabilities like CVE-2024-38399, leading to memory corruption while processing user packets, and CVE-2024-33064 and CVE-2024-33073, both causing information disclosure during the parsing of wireless protocol fields.
Apply the Latest Patches for FastConnect, SnapDragon, and Other Software
Qualcomm strongly advises OEMs to implement the necessary patches promptly to mitigate potential exploitation risks.
Users are encouraged to update their devices to the latest firmware versions and should reach out to their device manufacturers to confirm the patch status for their specific models.
For more detailed information, refer to theQualcomm October 2024 Security Bulletin.
Other Developments: October 2024 Android Security Update
Coinciding with Qualcomm’s bulletin, Google has also released the October 2024 Android security update, addressing 26 high-severity vulnerabilities. The update, split into two parts (2024-10-01 and 2024-10-05) fixes elevation of privilege, denial-of-service (DoS), and remote code execution flaws across various components. While none of these vulnerabilities are actively exploited, users are urged to update their devices promptly. For more details, refer to theAndroid Security Bulletin.
Reduce Vulnerability Risk with SOCRadar’s Attack Surface Management
Vulnerabilities in widely-used products, such as mobile platforms, chipsets, and connectivity solutions, can have extensive and serious consequences. According to Qualcomm, its Snapdragon processors are embedded in over a billion smartphones worldwide, including premium devices from Samsung, Xiaomi, OnePlus, and Vivo.
As always, failing to patch security vulnerabilities on time leaves both businesses and individuals exposed to significant threats, including ransomware, data theft, and network infiltration. Keeping your systems updated is critical, but tracking vulnerabilities across your entire infrastructure can be an overwhelming task. SOCRadar’s Attack Surface Management (ASM) module offers a great solution to this challenge.
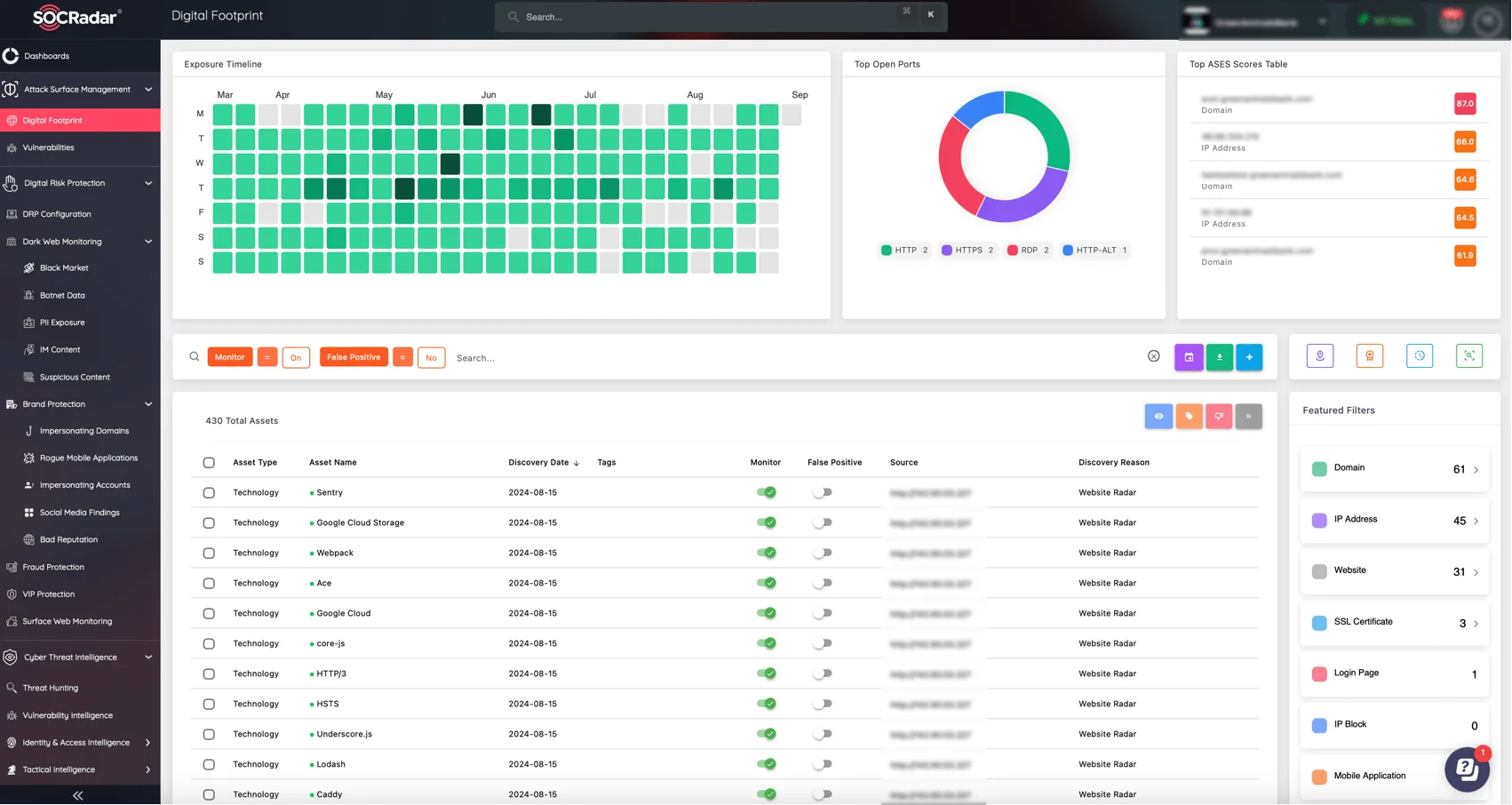
SOCRadar’s ASM module
By continuously monitoring your external assets for vulnerabilities and attack vectors, SOCRadar’s ASM helps you stay ahead of potential exploits. The platform provides real-time alerts, in-depth reports, and actionable insights, ensuring your organization can respond to threats before they escalate.



































