
Remote Administration Tool Sale, Ledger Database Leak, and Dark Strom DDoS Attack
In this week’s dark web roundup, we bring you a series of concerning developments that the SOCRadar Dark Web Team has flagged. From the sale of sophisticated remote administration tools to a substantial database leak relating to Ledger, the stakes continue to rise in cybersecurity. Meanwhile, the Dark Strom Team escalates its efforts with a targeted DDoS attack. An unauthorized RDP access is offered for a Polish construction company, and a new hacking operation is afoot targeting websites in Denmark and Sweden.
Read on for the critical details of each incident.
Find out if your data has been exposed.
Remote Administration Tool Sale is Detected
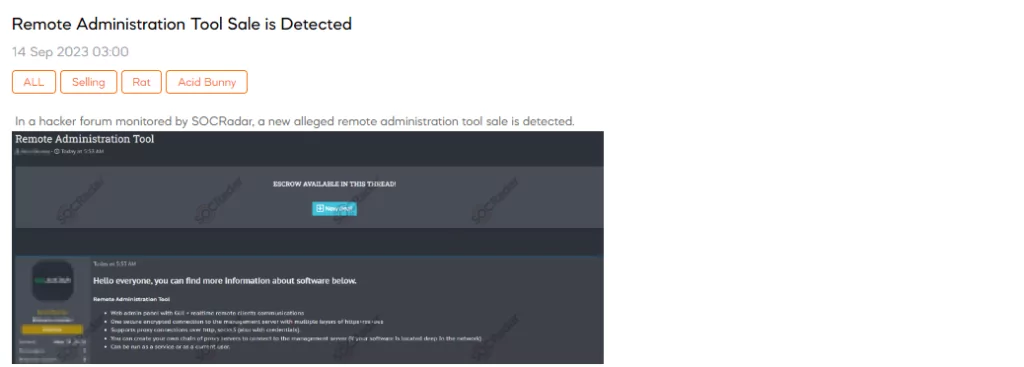
On September 14, the SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor advertising the sale of a remote administration tool. The tool is described as having several features, including a web admin panel with a graphical user interface, secure encrypted connections, support for proxy connections, and a plugin system for various functionalities such as a command line, file manager, keylogger, and more.
Database of Ledger is Leaked
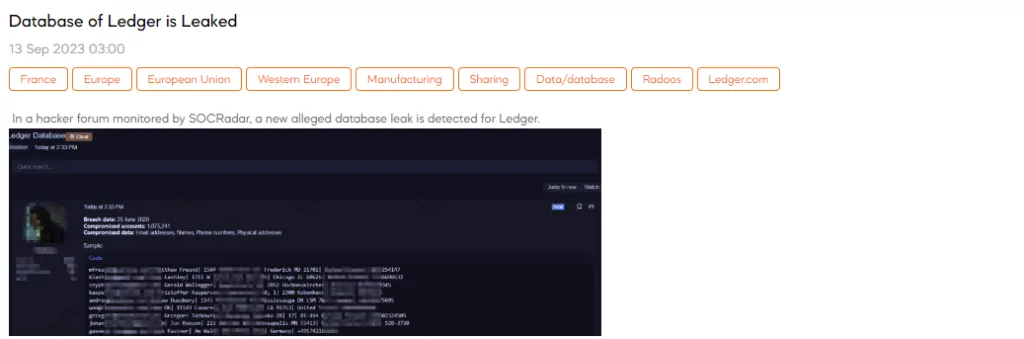
A SOCRadar analyst has identified a post on a hacker forum regarding an alleged database leak related to Ledger. Ledger is a French company that develops hardware wallets and software solutions for securing and managing crypto assets. According to the threat actor who shared this information, the breach is dated June 25, 2020, and involves a significant number of compromised accounts, totaling 1,075,241. The compromised data reportedly includes email addresses, names, phone numbers, and physical addresses.
Dark Strom Team Hackers Target The Northern Sea Port
The SOCRadar Dark Web Team has identified a post in a Telegram channel that a threat actor claims that the pro-Russia hacking group known as Dark Strom Team conducted a coordinated Distributed Denial-of-Service (DDoS) campaign against The Northern Sea Port.
Unauthorized RDP Access Sale is Detected for a Polish Construction Company
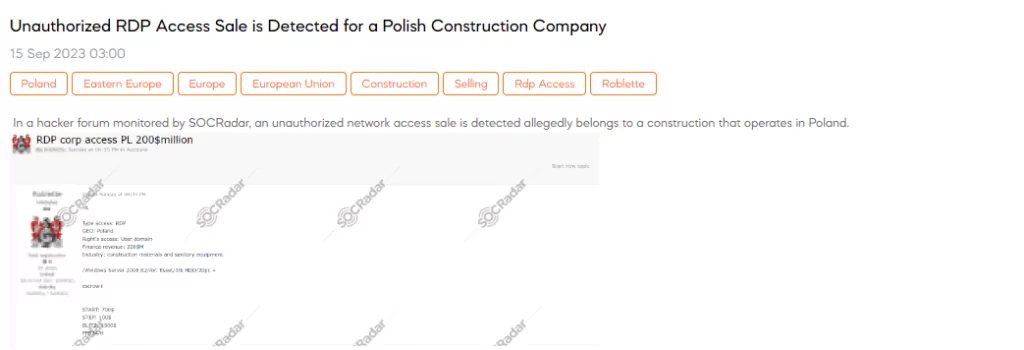
SOCRadar Dark Web Team uncovered a post in a hacker forum where a threat actor is openly advertising the unauthorized sale of RDP (Remote Desktop Protocol) access to a Polish construction company. This illegal offer includes details such as the location of the compromised network, the specific access rights provided (user domain), and alarming financial statistics, with the company’s revenue cited at $200 million.
New Hack Announcement is Detected for Denmark and Sweden Websites
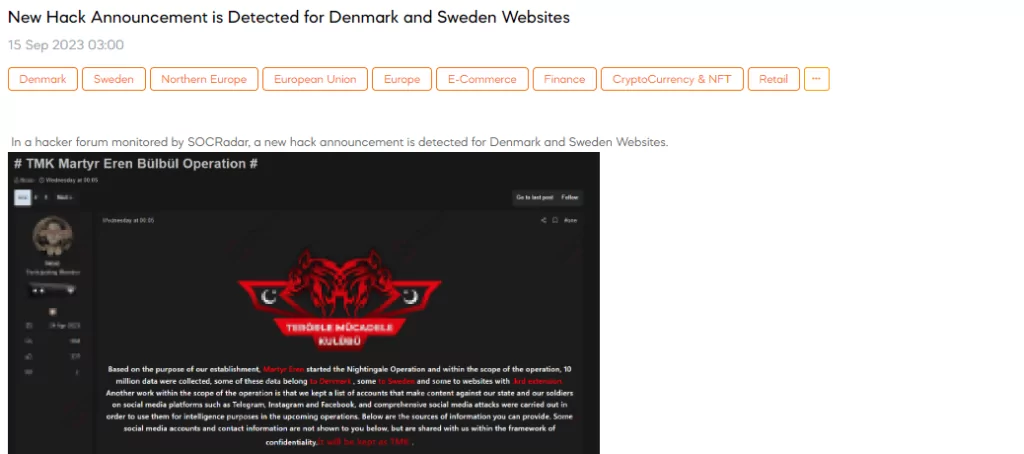
SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor has announced a new hacking operation targeting websites in Denmark, Sweden, and those with the .krd extension. The threat actor claims to have collected 10 million pieces of data as a result of this operation, with data from Denmark, Sweden, and websites using the .krd domain extension being included.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































