
The Royal Ransomware’s Latest Victim, Micro-Star International, KuCoin, and Kuwaiti Citizens Data Sales
Powered by DarkMirror™
This week,
KillNet announced a series of high-impact Distributed Denial of Service (DDoS) attacks. The Royal ransomware group also added Stanley Electric to its victim list. Data of Micro-Star International, KuCoin Kuwaiti Citizens are on sale.
Find out if your data has been exposed.
Cyber Threats Evolve: KillNet Declares War on NATO
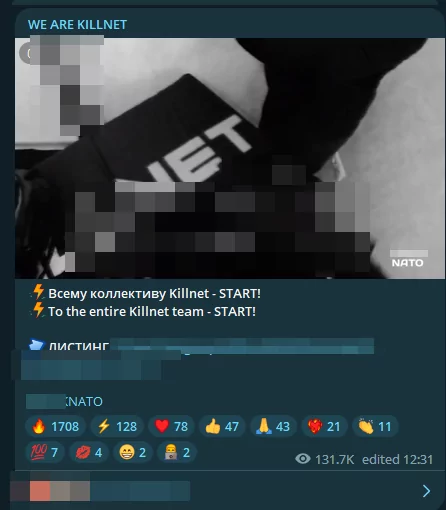
SOCRadar detected a post that the notorious threat actor KillNet had announced a series of high-impact Distributed Denial of Service (DDoS) attacks on NATO’s critical infrastructure. Following a poll on their Telegram channel, the group declared war on NATO, pledging allegiance to Russia. They claim to have breached 40% of NATO’s electronic infrastructure and leaked personal data. KillNet collaborated with other threat actors such as NoName057, Anonymous Russia, and Anonymous Sudan to increase the impact of the attacks.
The New Ransomware Victim of Royal: Stanley Electric
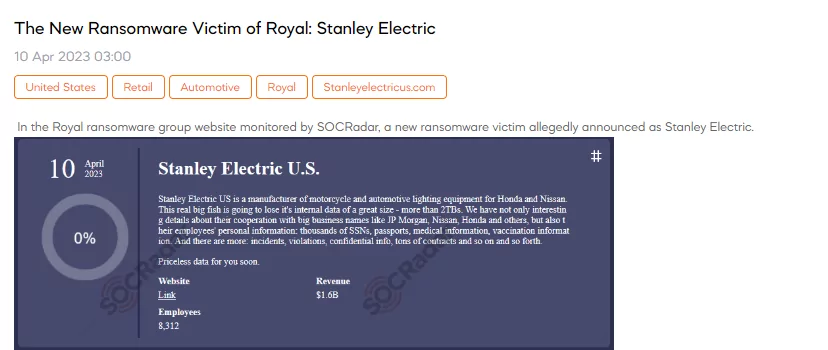
A SOCRadar dark web researcher discovered a post claiming that The Royal ransomware group had added Stanley Electric to its victim list. The threat actor claims that the data belonging to Stanley Electric US includes sensitive data belonging to Stanley Electric customers such as JP Morgan, Nissan, and Honda, as well as confidential information and contracts belonging to Stanley Electric. Cybercriminals also claim to have employee data. Royal ransomware announced that it had 2TB of compromised data.
Data of Micro-Star International are on Sale
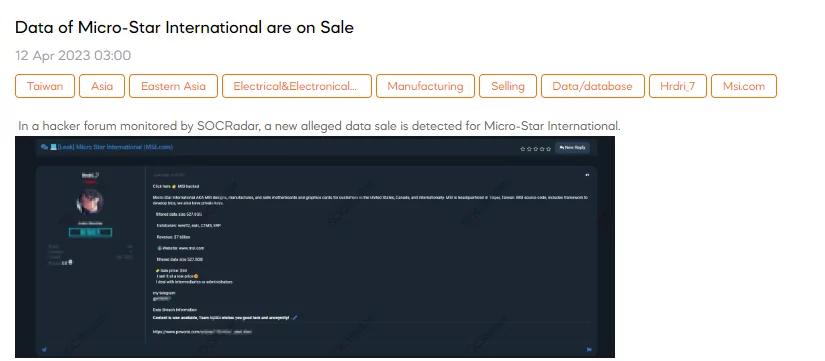
On April 12, a SOCRadar researcher detected a data sale allegedly belonging to Micro-Star International. The threat actor claims the filtered data is 527.8GB and contains sensitive data such as source code. On April 5, the Money Message ransomware gang added MSI to its list of victims. Immediately after the Money Message group’s announcement, MSI confirmed a data breach on their network.
Data KuCoin is on Sale
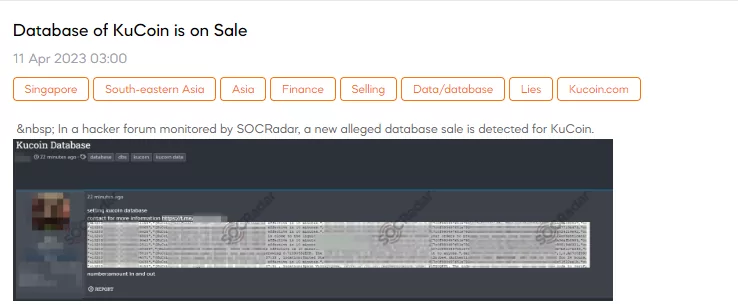
On April 11, SOCRadar detected a database sale allegedly belonging to KuCoin. The cybercriminal shared a database sample, claiming it belonged to him. The threat actor redirects those who want more information about the database to Telegram.
Database of Kuwaiti Citizens is on Sale
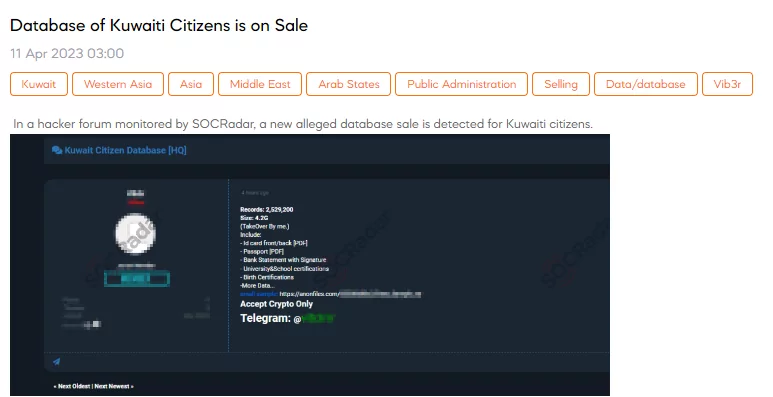
The SOCRadar dark web team detected the sale of a database allegedly belonging to Kuwaiti citizens. According to the perpetrator, the file, which is 4.2GB, comprises 2.5 million records, including front and back PDFs of ID cards, passports, bank statements with signatures, university and school certifications, birth certificates, and additional data. The attacker shared a sample of the data as proof, and cryptocurrency is the payment method specified for this cybercrime.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































