
SAP Security Patch Day May 2024: Critical CVE-2024-33006 Vulnerability Could Lead to System Takeover
On May 14, 2024, SAP delivered its monthly security updates, which included 14 new Security Notes alongside updates to 3 previously released notes.
SAP Security Patch Day May 2024 updates address a wide spectrum of vulnerabilities that could potentially compromise SAP systems. These include Cross-site Scripting (XSS), SQL Injection, Memory Corruption, and Missing Authorization Checks – each presenting unique risks that could disrupt operations if left unaddressed.
A notable issue among these updates is CVE-2024-33006, a severe vulnerability that, if exploited, could cause a complete system takeover.
Which Critical Vulnerabilities Were Addressed in SAP Security Patch Day May 2024?
SAP Security Patch Day May 2024 addressed several high-priority vulnerabilities with the following security notes:
Security Note #3455438 (CVSS: 9.8) – Critical Vulnerabilities in SAP Customer Experience (CX) Commerce
Security Note #3455438 (CVSS: 9.8) involves critical vulnerabilities affecting external libraries used by SAP CX Commerce, namely CVE-2019-17495 and CVE-2022-36364.
The first vulnerability, CVE-2019-17495, is a CSS injection vulnerability in Swagger UI versions before 3.23.11. It allows attackers to exploit the Relative Path Overwrite (RPO) technique, enabling CSS-based input field value exfiltration, such as CSRF token values.
This flaw arises due to the embedding of untrusted JSON data from remote servers, which poses significant security risks.
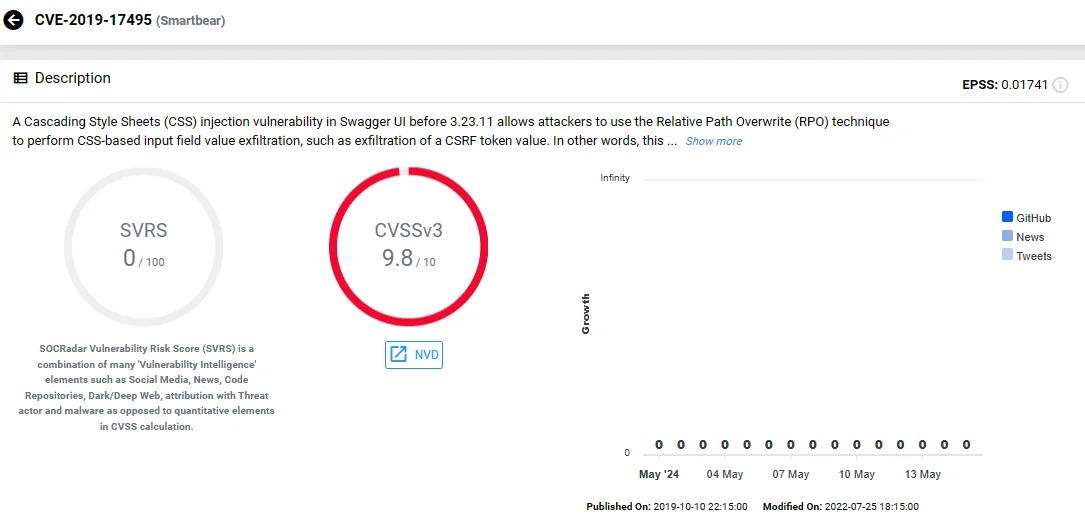
Vulnerability card of CVE-2019-17495 (SOCRadar)
The second vulnerability under this security note, CVE-2022-36364, affects the Apache Calcite Avatica JDBC driver.
CVE-2022-36364 involves creating HTTP client instances based on class names provided through the httpclient_impl connection property. The driver fails to verify if the class implements the expected interface before instantiation, potentially leading to code execution through arbitrary class loading.
Exploitation, however, requires specific privileges to control JDBC connection parameters and the presence of a vulnerable class in the classpath, adding layers of complexity to potential attacks.
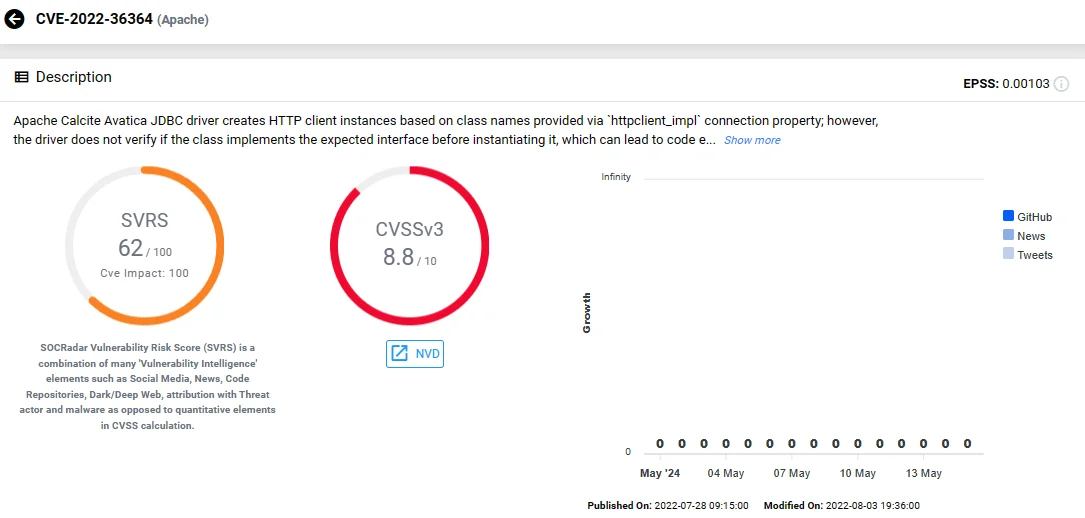
Vulnerability card of CVE-2022-36364 (SOCRadar)
Security Note #3448171 (CVSS: 9.6) – File Upload Vulnerability in SAP NetWeaver Application Server ABAP and ABAP Platform
Security Note #3448171 (CVSS: 9.6) addresses a critical file upload vulnerability, tracked as CVE-2024-33006, in the SAP NetWeaver Application Server ABAP and ABAP Platform.
CVE-2024-33006 allows an unauthenticated attacker to upload a malicious file to the server. If accessed by a victim, this could lead to complete system compromise and potential takeover.
This vulnerability spans across various SAP_BASIS versions from 700 to 758. Unlike the previously mentioned external library vulnerabilities, this issue is inherent within the SAP platform itself.
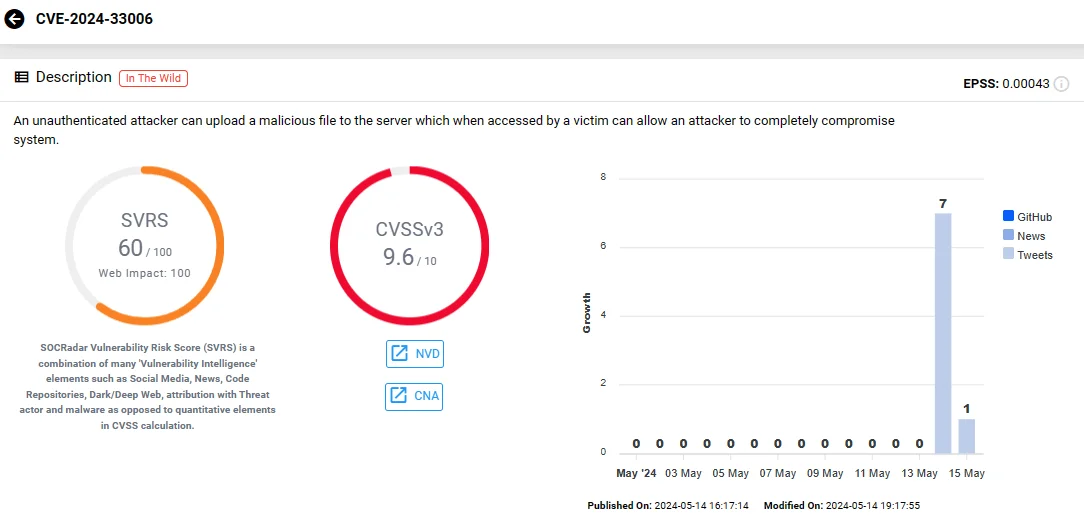
Vulnerability card of CVE-2024-33006 (SOCRadar)
In addition to these critical security notes, a high-severity note, Security Note #3431794 (CVSS: 8.1), was released to tackle a Cross-site Scripting (XSS) vulnerability in the SAP BusinessObjects Business Intelligence Platform, identified as CVE-2024-28165. This vulnerability could allow attackers to inject malicious scripts into web pages viewed by other users, posing a risk of data breaches and information leakage.
To access details on any vulnerability and track related activities such as exploitation and hacker trends, you can use SOCRadar’s Vulnerability Intelligence feature.
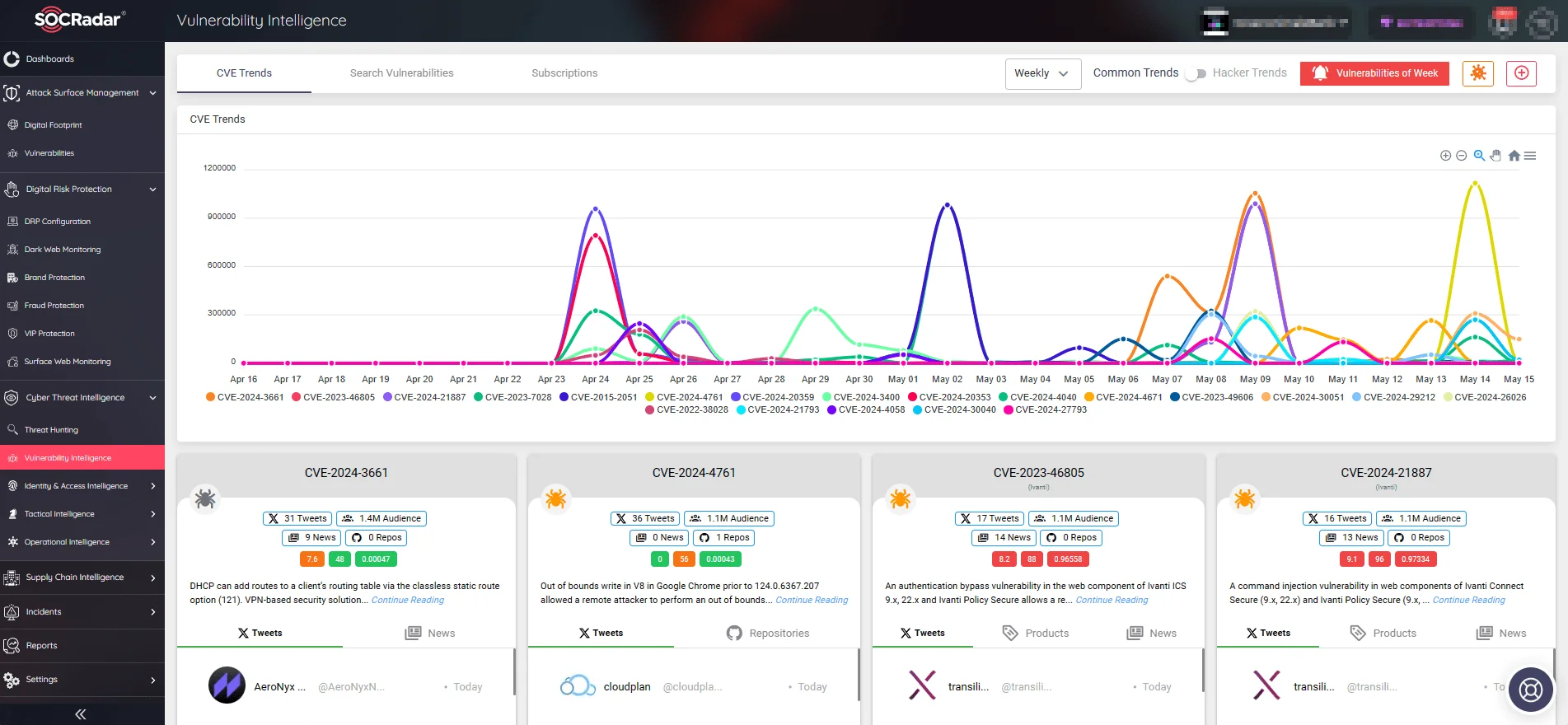
SOCRadar’s Vulnerability Intelligence can monitor new vulnerabilities and hacker trends for your organization, providing every detail
Updates to Previous Notes in SAP Security Patch Day May 2024
A notable update this month is the revision of the ‘Hot News’ security note (Note #2622660), which carries a CVSS score of 10.0. This particular note focuses on the Chromium browser component within the SAP Business Client, a recurring theme in SAP updates due to the frequent discovery of vulnerabilities in the Chromium project.
The latest update covers 23 new security vulnerabilities found in Chromium, reflecting the rapidly evolving threats to browser security. Addressing these vulnerabilities is crucial as they can significantly impact the security of client applications that depend on the Chromium engine.
Additionally, two medium-priority security notes received updates during this patch cycle. Security Note #2745860 and Security Note #2174651 both pertain to the Enterprise Services Repository and SAP Process Integration, respectively. These notes address Information Disclosure vulnerabilities, which, although not as severe as other types of vulnerabilities, can still provide attackers with valuable information that could be used to orchestrate more targeted and effective attacks.
For more information, see SAP’s official security note here: SAP Security Patch Day May 2024.
Improve Your Security Posture with SOCRadar
The barrage of emerging vulnerabilities can be overwhelming for organizations. While efficient patch management is important, it can be burdensome without the right tools. Recognizing this challenge, SOCRadar offers sophisticated solutions designed to streamline the monitoring of organizational perimeters and the broader vulnerability landscape, thus alleviating the stress associated with maintaining security in the digital age.
SOCRadar’s Attack Surface Management (ASM) module is engineered to enhance an organization’s awareness of its digital footprint and potential vulnerabilities. By providing timely alerts about threats to organizational assets, this module helps security teams stay one step ahead of potential breaches.
The ASM tool does more than just monitor; it provides actionable insights that enable organizations to swiftly respond to vulnerabilities before they are exploited by malicious actors.
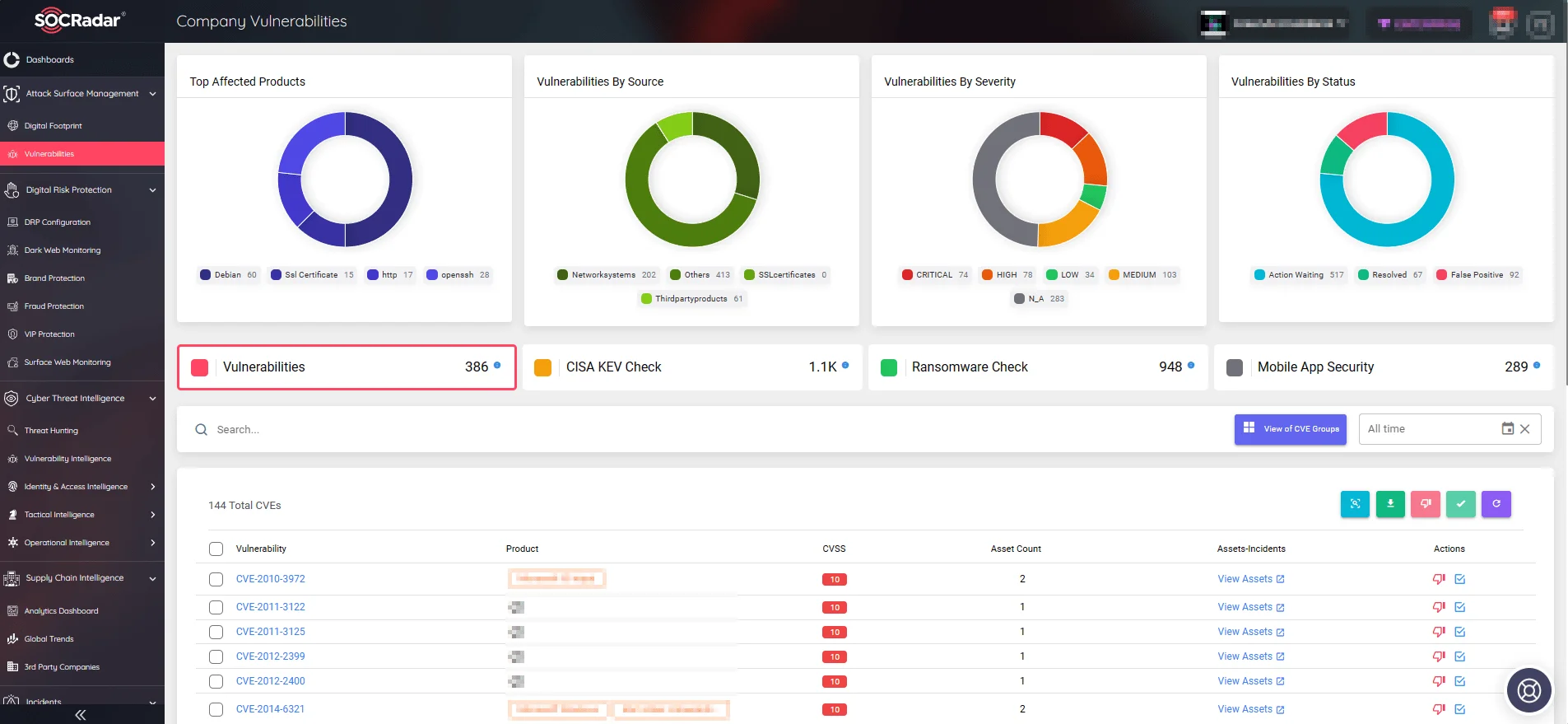
View Company Vulnerabilities and take quick actions through the ASM module (SOCRadar)
With its advanced tools like ASM and the Vulnerability Intelligence feature, the SOCRadar platform offers an in-depth look at emerging threats and exploitable vulnerabilities specific to your environment. It tracks the latest in security vulnerabilities, delivering customized alerts that allow organizations to prioritize and address the most critical issues first.
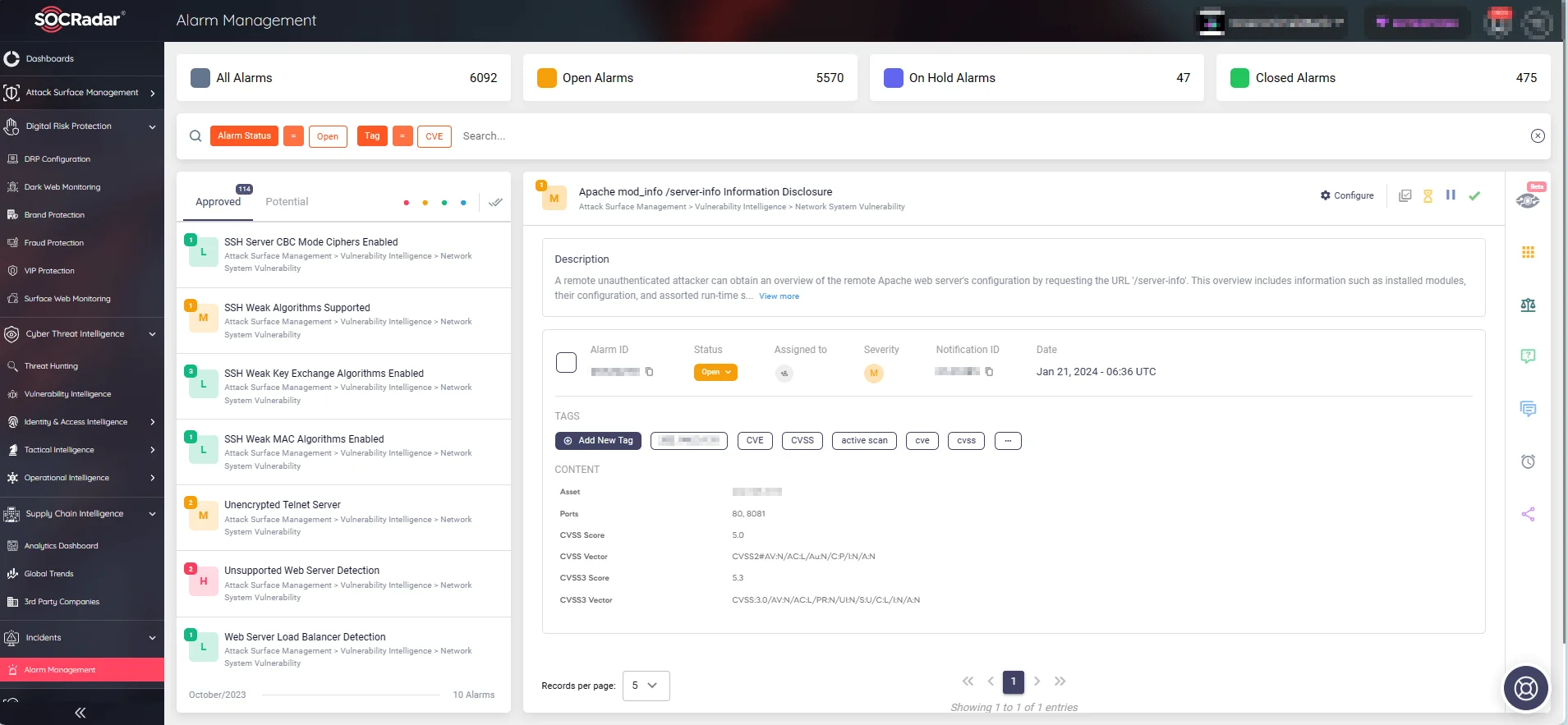
SOCRadar’s Alarm Management page
The integration of SOCRadar’s tools into your security operations can transform how threats are managed. From visualizing your attack surface to receiving customized alerts that match your specific security needs, SOCRadar enhances your ability to safeguard critical assets effectively.
With the Free Edition, you can check out the SOCRadar XTI platform’s features.




































