
ScienceLogic SL1 0-Day from Rackspace Breach Added to CISA KEV (CVE-2024-9537)
A critical security vulnerability was recently discovered in the ScienceLogic SL1 Portal (formerly EM7), exploited as a zero-day by attackers. The Cybersecurity and Infrastructure Security Agency (CISA) has recently added the vulnerability, identified as CVE-2024-9537, to its Known Exploited Vulnerabilities (KEV) Catalog.
Rackspace first disclosed the incident last month, informing customers of a temporary disruption in their ability to view monitoring graphs on the MyRack portal. While no direct impact on monitoring services occurred, the downtime was necessary to test an update to resolve the vulnerability.
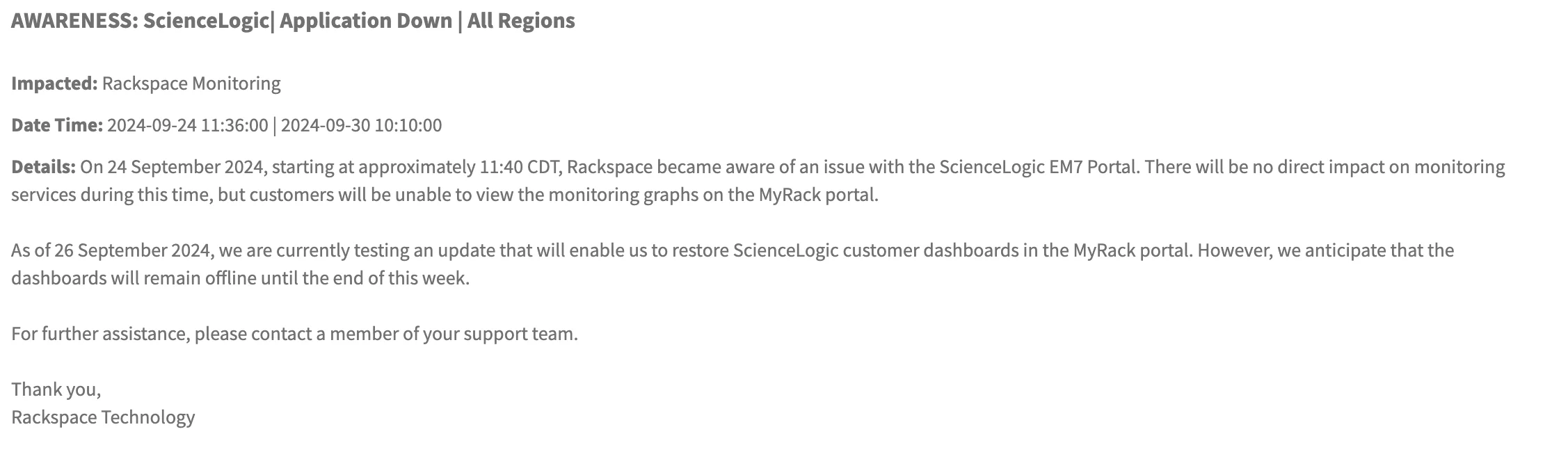
Notice by Rackspace: ScienceLogic | Application Down (Source)
What Happened? Details of the Rackspace Zero-Day Attack
In late September 2024, Rackspace identified a serious breach involving a zero-day vulnerability, affecting a third-party component integrated with the ScienceLogic EM7 Portal. This flaw allowed attackers to gain unauthorized access to three internal Rackspace monitoring servers, leading to Remote Code Execution (RCE), and exposure of certain internal data.
While customer performance monitoring services were not disrupted, the attackers accessed limited information, such as customer account names, usernames, device details, and encrypted internal credentials. Despite the breach, Rackspace emphasized that no other products or services were affected.
The compromised servers were immediately taken offline, and Rackspace collaborated with ScienceLogic to quickly develop and deploy a patch. Customers were informed of the situation, with Rackspace assuring them that there was no need for immediate action on their part.
As an extra precaution, the company initiated the rotation of internal credentials to ensure additional security.
Details of the ScienceLogic SL1 Vulnerability: What is CVE-2024-9537?
CVE-2024-9537 is a high-severity vulnerability (CVSS 9.3) that affects the ScienceLogic SL1 platform, formerly known as EM7. The flaw stems from a third-party component integrated within the platform, which enables Remote Code Execution (RCE). If exploited, an attacker could potentially gain full control over vulnerable systems by executing malicious code remotely.
This vulnerability became a significant concern after attackers used it to target Rackspace’s internal monitoring systems, which utilize ScienceLogic’s technology for performance tracking.
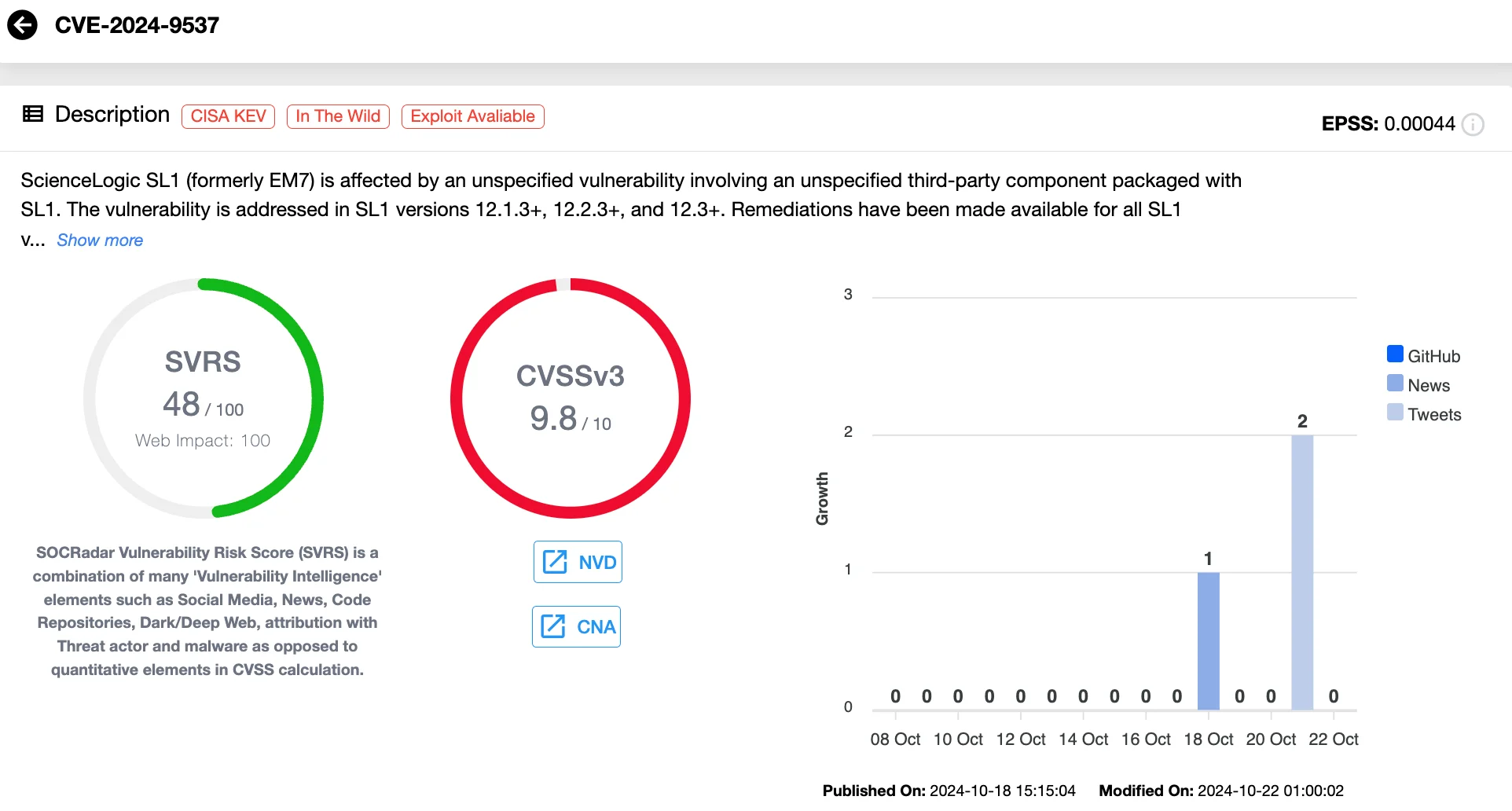
Details of the CVE-2024-9537 flaw (SOCRadar Vulnerability Intelligence)
The flaw lies in the way certain communications are handled within the third-party component, enabling attackers to bypass protections and relay malicious commands.
CISA Urges Patching Against CVE-2024-9537, Adds it to the KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has officially added CVE-2024-9537 to its Known Exploited Vulnerabilities (KEV) Catalog, underscoring the urgency of addressing this vulnerability.
With the latest addition to the KEV Catalog, CISA is strongly advising organizations using the ScienceLogic SL1 platform to apply available patches immediately. This directive is particularly critical for Federal Civilian Executive Branch (FCEB) agencies, which are mandated to implement the fix by the due date: November 11, 2024.
Fixed Versions of ScienceLogic SL1
Although the specific third-party utility involved has not been publicly named, Rackspace and ScienceLogic worked together to deliver patches across affected versions. The vulnerability has been resolved in the following versions of ScienceLogic SL1:
- 12.1.3
- 12.2.3
- 12.3 and later versions
In addition to these versions, fixes have also been made available for earlier releases, including:
- 10.1.x
- 10.2.x
- 11.1.x
- 11.2.x
- 11.3.x
Organizations running outdated versions of SL1 are strongly advised to update to these fixed releases to prevent potential exploitation. The updates address the vulnerability within a third-party component that had been bundled with the platform, closing the door to potential attacks exploiting this flaw.
Access Real-Time Vulnerability Intelligence with SOCRadar
In the face of growing cyber threats, staying ahead of vulnerabilities is critical to safeguarding your business. Without real-time insights, your organization could be left exposed to dangerous exploits.
SOCRadar’s Vulnerability Intelligence module helps you monitor, identify, and prioritize vulnerabilities across your IT infrastructure. It delivers actionable insights on newly discovered vulnerabilities, known exploits, and emerging threats so you can stay ahead of attackers.
Protect your systems by patching vulnerabilities promptly and reducing your attack surface with focused intelligence. (SOCRadar Vulnerability Intelligence)
By integrating SOCRadar’s Vulnerability Intelligence into your security strategy, you gain real-time alerts and in-depth analyses that allow you to address the most critical risks before they are exploited.


































