
Shadow IT Explained: What Are the Risks and How Can You Mitigate Them?
A recent study from EMC suggests that data loss and downtime result in losses of $ 1.7 trillion each year.[1]
Since shadow IT is an operation that is often carried out unwittingly, companies do not focus on it as much as they should. However, this issue plays a very critical role in both the security and financial investment issues of companies.
Gartner predicted that one-third of successful attacks by 2020 were due to shadow IT.[2] Based on the same report, between 30% and 40% of IT spendings by large organizations goes to shadow IT. With the adoption of the cloud, things are even getting worse for CIO/CISOs.
What is shadow IT?
Shadow IT, by definition, includes software, applications, and services used by different departments without the company’s IT department’s knowledge and control. Today, many staff can use different software and tools, thinking that they can carry out their work faster and easier without notifying the IT department.
This applies not only to the organization’s software but also the company’s laptop, tablet, or smartphone. The internet is offering more and more applications/programs to downloads. In this case, malware installation is very possible.
What are the risks created by shadow IT?
Shadow IT creates three significant negative impacts on enterprise-scale companies. These are;
Data loss
Relevant personnel can leave data in their own software and vehicle.
Waste of time
Additional staff work required when lost data needs to be rearranged.
Investment loss
Using an alternative tool to replace the recommended one may not sound like a big deal, but for the company, it is the biggest example of a waste of money. After all, if IT buys licenses for every employee approved in the workflow and no one actually uses their own software, then the money paid for licenses is wasted. When a company and an employee have both purchased a software license, causing the company to pay for the same software twice.
Concerns with compliance
Most companies are subject to a range of rules, legislation, and industry guidelines. It is also tougher for an organization to follow these requirements because of the prevalence of unmanaged applications.
Performance problems
Some devices and solutions can be incompatible with major IT infrastructure modules, resulting in severe problems of performance.
What are the common myths about shadow IT?
The problem is not that serious
Shadow IT causes many concerns for both the IT department and the business as a whole, especially when it comes to the security of company data.
It is under control
Cloud resources can be accessed by any user from anywhere. In the Tech Pro Research survey, only 47 percent say they are using next-generation firewalls for SaaS access. Moreover, only 18 percent said they would partner with a specialist security provider to keep their IaaS resources safe.[3]
Easy to discover
First of all, log analysis is a costly and time-consuming process. Second, the logs don’t tell you what data is being transferred. Most SaaS sites use HTTPS encryption, so it may not be marked as SaaS.
Cloud services are safe
70 percent of respondents in the Tech Pro Research survey stated that IaaS providers are secure. While this is partially true, it is your responsibility to secure your applications and data while cloud security providers secure cloud infrastructure.
There will be no major breach
More than half of Tech Pro Research’s respondents did not say they were planning to invest in securing SaaS usage. Also, only 18 percent rely on third parties to secure IaaS.
What shadow IT is used for?
The most common reasons for using shadow IT are:
Efficiency
Approved software and solutions can be slower, less effective, and less productive than unsanctioned alternatives.
Compatibility
Corporate solutions may be incompatible with users’ personal devices.
Comfort
People tend to use software and solutions they’re used to.
How to create a shadow IT strategy?
Currently, in the midst of working from home and the pandemic, the risks associated with the use of unsupported apps and services are increasing. Employees are forced to adapt to new conditions and often try to find new tools that they believe are better suited to working remotely.
IT leaders cannot constantly keep track of what software and services staff are using. While it is impossible to fully control what users are doing, a successful strategy should include the following critical steps:
Monitor what’s happening in your organization
Keep track of which service is used by whom, how often, and with what types of data. Control access to insecure services and find out what users really need.
Identifying unmet needs
After identifying unauthorized systems and software, you must understand why employees don’t want to use the solutions provided by the organization. If you want to eliminate the risk of Shadow IT, you must address the core issues and provide the staff with enterprise solutions that are within your control.
Provide users the tools they need
Employees are turning to different software and services, thinking that they will do their jobs easier and faster. So, providing high-quality services and software to users, prevents them from turning to other options.
Train the users on how to process sensitive data:
Let them understand the risks of using publicly shared services. Provide information on how to properly store confidential, valuable, or personally identifiable information (PII).
What are the key questions IT security should be able to answer related to shadow IT visibility and control?
- Which services are employees and business units using overall and in each category (examples: file-sharing, social media, collaboration)?
- Which services are gaining in popularity and should be evaluated for enterprise-wide adoption?
- What is the risk level of each service in use?
- How effective are my firewalls and proxies at identifying cloud services and enforcing acceptable cloud use policies?
- Which redundant services are employees using, and are they introducing additional cost and risk or inhibiting collaboration?
- How do I quantify the risk from the use of cloud services and compare it to peers in my industry?
- Which services house sensitive or confidential data today?
- What are the security capabilities of the services storing sensitive data?
- Which partners’ cloud services are employees accessing, and what’s the risk of these partners?
What are the cloud computing security issues?
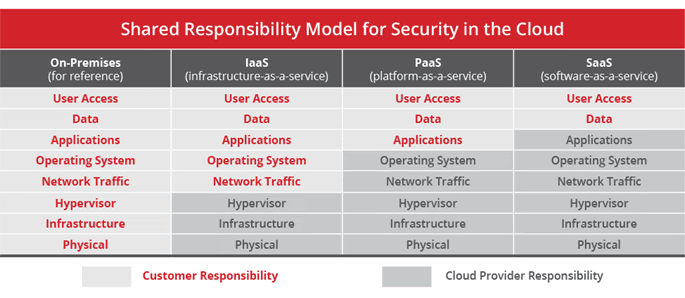
Numerous unique security problems and threats are raised in cloud computing. Data is processed in the cloud and accessible over the internet via a third-party provider. This implies that there is little access and control of this data. It also wonders if it can be guarded properly. It is important for all to consider their respective positions and cloud-based security concerns.
Cloud services assume general responsibility for cloud protection problems and risks. This model covers the protection of the cloud itself, and the consumer ensures what it contains. The cloud computing customer is still responsible for safeguarding their data against safety risks and control access to any cloud service—from software-as-a-service (SaaS) such as Microsoft Office 365 and Infrastructure-as-a-Service (IaaS) like Amazon Web Services (AWS).
Most common SaaS cloud security issues
SaaS Cloud protection concerns are, of course, data and connectivity, as these two are left to SaaS customers by other mutual safety management models. It is the duty of each company to consider what data they bring into the cloud, who will access it, and the degree of security they have implemented (and the cloud service provider).
- Lack of visibility into what data is within cloud applications
- Theft of data from a cloud application by a malicious actor
- Incomplete control over who can access sensitive data
- Inability to monitor data in transit to and from cloud applications
- Cloud applications being provisioned outside of IT visibility (e.g., shadow IT)
- Lack of staff with the skills to manage security for cloud applications
- Inability to prevent malicious insider theft or misuse of data
- Advanced threats and attacks against the cloud application provider
- Inability to assess the security of the cloud application provider’s operations
- Inability to maintain regulatory compliance
The function of the SaaS provider is also important to consider as a possible entry point to the data and processes of the organization. Developments like XcodeGhost and GoldenEye Ransomware stress that the importance of applications and cloud services as a way to target greater objects can be understood by attackers. This has contributed to a rising concentration of attackers on this possible vulnerability. Be sure to scrutinize the protection programs of your cloud provider to secure your company and its records. Set the requirement that third-party audits will be predictable with shared results, and insist that reporting terms for technological solutions will be violated.
Most common IaaS cloud security issues
In IaaS, data security is important. With user liability expanding to software, network traffic, and operating systems, there are more risks. The recent trends in attacks that go beyond data should be regarded by organizations as centers of IaaS risk. Adversaries are taking hostile computing tools to mine cryptocurrency and use these services as a vector of assault against other components and third parties of the business infrastructure.
- Cloud workloads and accounts being created outside of IT visibility (e.g., shadow IT)
- Incomplete control over who can access sensitive data
- Theft of data hosted in cloud infrastructure by a malicious actor
- Lack of staff with the skills to secure cloud infrastructure
- Lack of visibility into what data is in the cloud
- Inability to prevent malicious insider theft or misuse of data
- Lack of consistent security controls over multi-cloud and on-premises environments
- Advanced threats and attacks against cloud infrastructure
- Inability to monitor cloud workload systems and applications for vulnerabilities
- Lateral spread of an attack from one cloud workload to another
It is important to determine your ability to deter fraud and monitor access while designing the infrastructure in the cloud. Determining who will access data into a server, monitoring improvements to the services to detect suspicious behaviors, safe and harden orchestrated instruments, and network mapping as a possible indicator for compromise are becoming increasingly routine steps to safeguard the implementation of the cloud infrastructure.
Most common private cloud security issues
The finely-tuned control accessible in private cloud environments is an important element in the decision-making process of distributing services to the public or private cloud. Other restrictions to private clouds can be compensated by extra control layers and add-on security and can lead to a realistic shift from monolithic server-based data centers.
- Lack of consistent security controls spanning over the traditional server and virtualized private cloud infrastructures
- The increasing complexity of infrastructure resulting in more time/effort for implementation and maintenance
- Lack of staff with skills to manage security for a software-defined data center (e.g., virtual compute, network, storage)
- Incomplete visibility over security for a software-defined data center (e.g., virtual compute, network, storage)
- Advanced threats and attacks
Around the same time, companies should take into account the difficulty under maintaining fine power, at least beyond the growth of the public cloud. Today, cloud providers are making tremendous strides to preserve their networks. By abstracting controls, cloud users can simplify security monitoring and reduce complexity. This unifies public and private cloud systems through physical and simulated worlds and hybrids.
How to mitigate common cloud computing security issues?
There are three best practices that all companies can work for to reduce cloud infrastructure security risks:
DevSecOps phase
Repeating code consistency, reducing exploits and vulnerabilities, and increasing the pace of program creation and functionality implementation is illustrated by DevOps and DevSecOps on many occasions. The incorporation into the business unit and the application team of development, QA, and Security processes, rather than depending on the independent security verification team, is critical for the speed at which today’s business climate demands.
Automated application deployment and management tools
The lack of security expertise and the growing frequency and speed of security risks mean that even the most skilled safety specialist cannot remain up to date. An essential component of modern IT operations is automation which eliminates mundane tasks and increases human benefits with machine advantages.
Centralized security for all facilities and suppliers with centralized control
No product or seller can produce it, but some management tools make slipping through too easy. A centralized management framework with an open integration fabric eliminates the complexity of the components integrated and workflows simplified.
Discover your shadow IT with SOCRadar
Discover and monitor all your forgotten external-facing assets including CMSs, network applications, SSL certificates, and JavaScript libraries to get timely alerts of the latest critical vulnerabilities.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
References
[1] Over 1.7 Trillion Lost Per Year from Data Loss and Downtime According to Global IT Study, DELL
[2] Gartner’s Top 10 Security Predictions – 2016, Gartner
[3] Your Business Must Think Long-term and Short-term When it Comes to IT, Pace Technical
[4] Cloud Computing Security Issues, McAfee
Cover image by David Werbrouck on Unsplash



































