
SolarWinds Releases Crucial Fixes for ARM Security Vulnerabilities (CVE-2023-35182, CVE-2023-35185, and CVE-2023-35187)
In the ever-evolving landscape of cybersecurity, staying ahead of threats is paramount for security professionals. Recently, SolarWinds Access Rights Manager (ARM), a comprehensive access management solution, has been the focus due to multiple discovered vulnerabilities. This post provides a quick look at these vulnerabilities, emphasizing the critical ones, their severity, and implications.
SolarWinds ARM is instrumental for organizations, simplifying the management and auditing of user access rights across various IT environments. It’s particularly significant for its role-based access control, Active Directory integration, and visual feedback capabilities. However, the recent discovery of eight vulnerabilities, with three deemed critical, has put users and cybersecurity professionals on high alert.
Critical Vulnerabilities in SolarWinds ARM
Recent assessments have uncovered a total of eight security vulnerabilities in SolarWinds ARM, three of which are deemed critical due to their potential to enable remote code execution with SYSTEM privileges. SYSTEM, an internal account for Windows operating systems, possesses the highest level of privileges, implying that exploitation of these vulnerabilities could offer attackers unrestricted control over affected installations.
- CVE-2023-35182 – Deserialization Flaw Leading to RCE: Tagged with a CVSS score of 9.8 by ZDI, this critical vulnerability allows remote, unauthenticated attackers to execute arbitrary code with SYSTEM privileges. The flaw resides in the ‘createGlobalServerChannelInternal’ method, lacking proper validation of user-supplied data, leading to the deserialization of untrusted data.
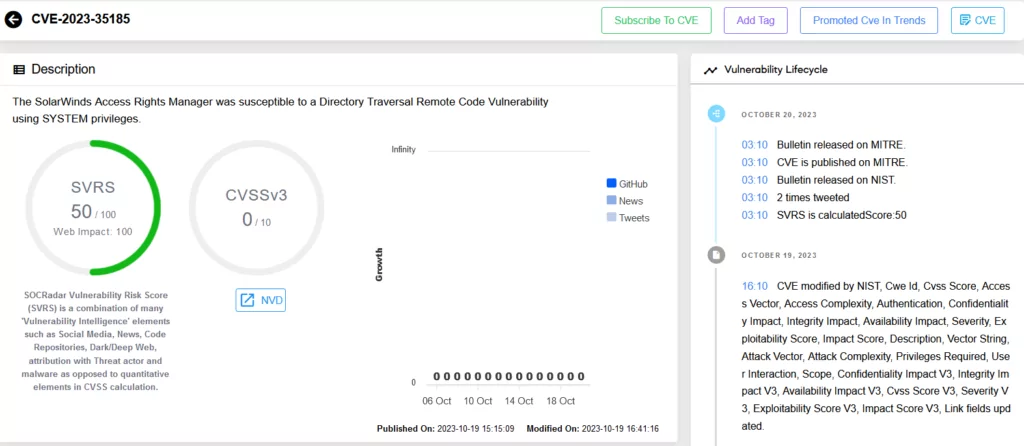
- CVE-2023-35185 – Directory Traversal to RCE: Another critical vulnerability with a CVSS score of 9.8, this security flaw enables remote attackers to perform a directory traversal attack, allowing the execution of arbitrary code in the SYSTEM context. The vulnerability stems from the ‘OpenFile’ method, which doesn’t adequately validate user-supplied paths.
- CVE-2023-35187 – RCE via the ‘OpenClientUpdateFile’ Method: Also scoring 9.8 on the CVSS scale, this vulnerability can be exploited by unauthenticated remote attackers. The issue lies within the ‘OpenClientUpdateFile’ method, with inadequate validation of user-supplied paths, allowing attackers to execute arbitrary code with SYSTEM privileges.
High-Severity Vulnerabilities
While not marked as critical by SolarWinds, the following vulnerabilities still pose a significant risk:
- CVE-2023-35180 and CVE-2023-35186: Both allow authenticated users to perform a remote code execution through the abuse of the SolarWinds ARM API.
- CVE-2023-35181 and CVE-2023-35183: These vulnerabilities can be exploited by users to perform privilege escalation due to incorrect folder permissions.
- CVE-2023-35184: This allows an unauthenticated user to execute remote code by abusing a SolarWinds service.
There’s a noticeable discrepancy in how SolarWinds and ZDI have rated these vulnerabilities. While ZDI identifies three vulnerabilities with a critical severity score of 9.8, SolarWinds has classified the highest severity rating as 8.8, reserved for high-severity issues. This difference underscores the need for organizations to consider multiple perspectives when assessing threats and to not solely rely on vendor-provided information.
Recent Fixes and Recommendations
In response, SolarWinds has issued fixes in their latest patch, Access Rights Manager 2023.2.1, addressing not only these vulnerabilities but also several functional issues such as an error in the AD Logga, problems with OneDrive scans, and an HTTP failure error during Directories File system permissions analysis.
A SolarWinds has also issued a statement: “SolarWinds has developed a patch for these issues and communicated with customers about the steps needed to apply the fix to harden their environments. We are not aware of any evidence that any of these vulnerabilities have been exploited.”
Staying Vigilant with SOCRadar Vulnerability Intelligence
These discoveries reinforce the necessity for continuous vigilance and proactive measures in cybersecurity. Tools like SOCRadar’s Vulnerability Intelligence can play a crucial role in real-time threat detection and maintaining robust security postures. By leveraging such advanced solutions, organizations can better navigate the complexities of vulnerabilities, regardless of discrepancies in external ratings, ensuring fortified security protocols and immediate response to potential threats.




































