
How Star Blizzard Exploits WhatsApp in Spear Phishing Campaign
Cybersecurity experts are sounding the alarm over a novel spear phishing campaign by the Russian state-sponsored group known as Star Blizzard (a.k.a. UNC4057, Callisto, and ColdRiver). Historically targeting diplomats, government officials, and organizations tied to Ukraine, this threat actor has shifted focus to exploiting WhatsApp accounts through malicious QR codes.
This blog will outline the methods Star Blizzard employed in their latest campaign, the potential risks it poses, and the proactive measures organizations and individuals can take to defend against such threats.
A Tactical Shift From Diplomats to WhatsApp Users
Previously, Star Blizzard employed spear phishing campaigns primarily targeting government officials, NGOs, and individuals supporting Ukraine. These efforts were disrupted in October 2024, when Microsoft and the U.S. Department of Justice dismantled over 180 phishing domains linked to the group. However, Star Blizzard quickly adapted, introducing new methods to circumvent detection.
The latest campaign, detected by Microsoft Threat Intelligence in November 2024, represents a strategic shift. For the first time, Star Blizzard exploited WhatsApp as an attack vector. By leveraging malicious QR codes, the group sought to compromise victims’ accounts and exfiltrate sensitive data, underscoring the increasing sophistication of state-sponsored cyberattacks.
It is worth noting that the Cybersecurity and Infrastructure Security Agency (CISA) had previously warned about Star Blizzard’s spear phishing schemes in a December 7, 2023 advisory. This CISA advisory highlighted the group’s consistent success in evolving their tactics to maintain effectiveness – a trend that continues with this latest campaign.
How Did Star Blizzard Exploit WhatsApp?
Star Blizzard’s new method employs a layered phishing scheme designed to manipulate victims at multiple points of interaction:
- Initial Email: Targets receive emails impersonating U.S. government officials, inviting them to join WhatsApp groups supporting Ukrainian NGOs. The emails include broken QR codes that cannot be scanned successfully, intentionally prompting recipients to engage further.
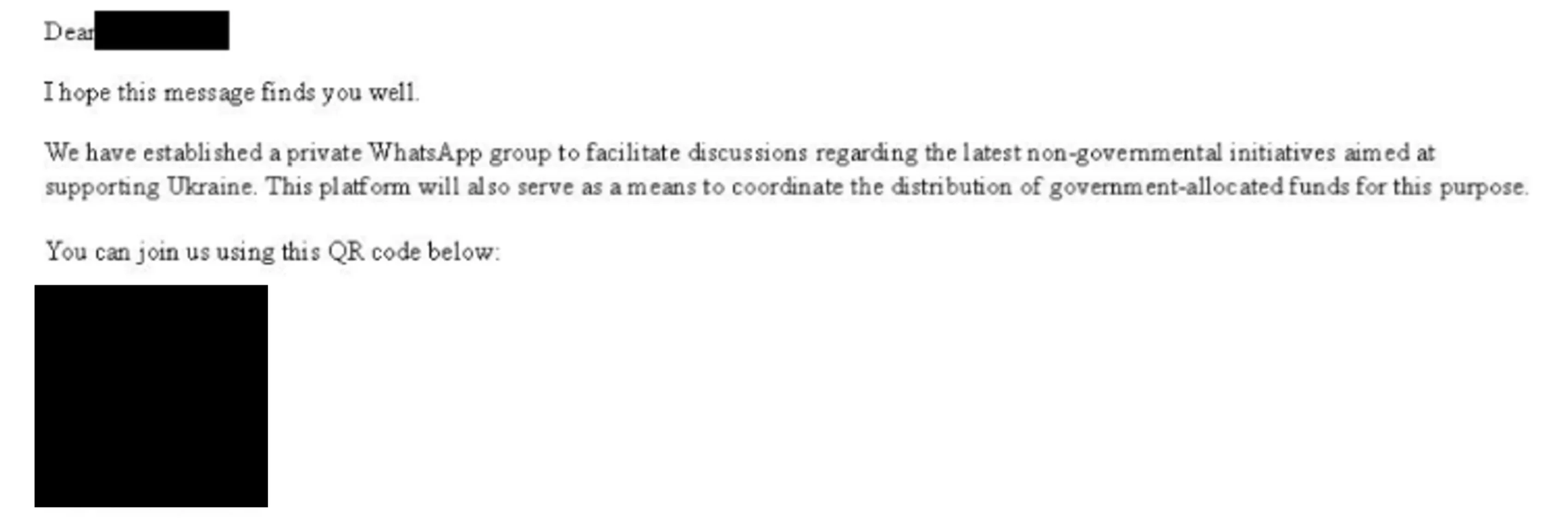
Initial phishing email by the attackers (Microsoft)
- Follow-Up Communication: When victims respond to the broken link, attackers send a second email containing a shortened URL (e.g., via “t.ly”). This URL leads to a fraudulent page posing as a legitimate WhatsApp invitation, carefully designed to appear authentic.
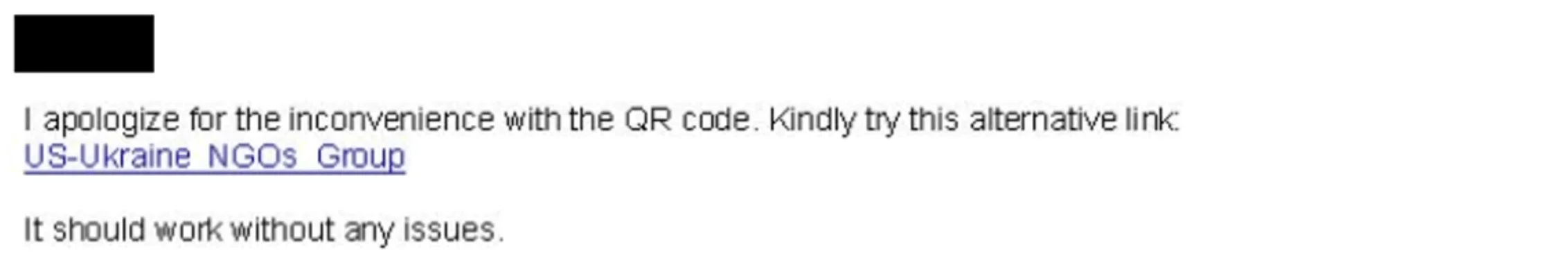
Follow-up phishing email (Microsoft)
- Malicious QR Code: Victims are instructed to scan a QR code on the fake page. Unbeknownst to them, this QR code enables attackers to link their device to the victim’s WhatsApp account via WhatsApp Web. Once linked, attackers gain access to private messages, conversations, and sensitive information, which can then be exfiltrated using browser plugins.
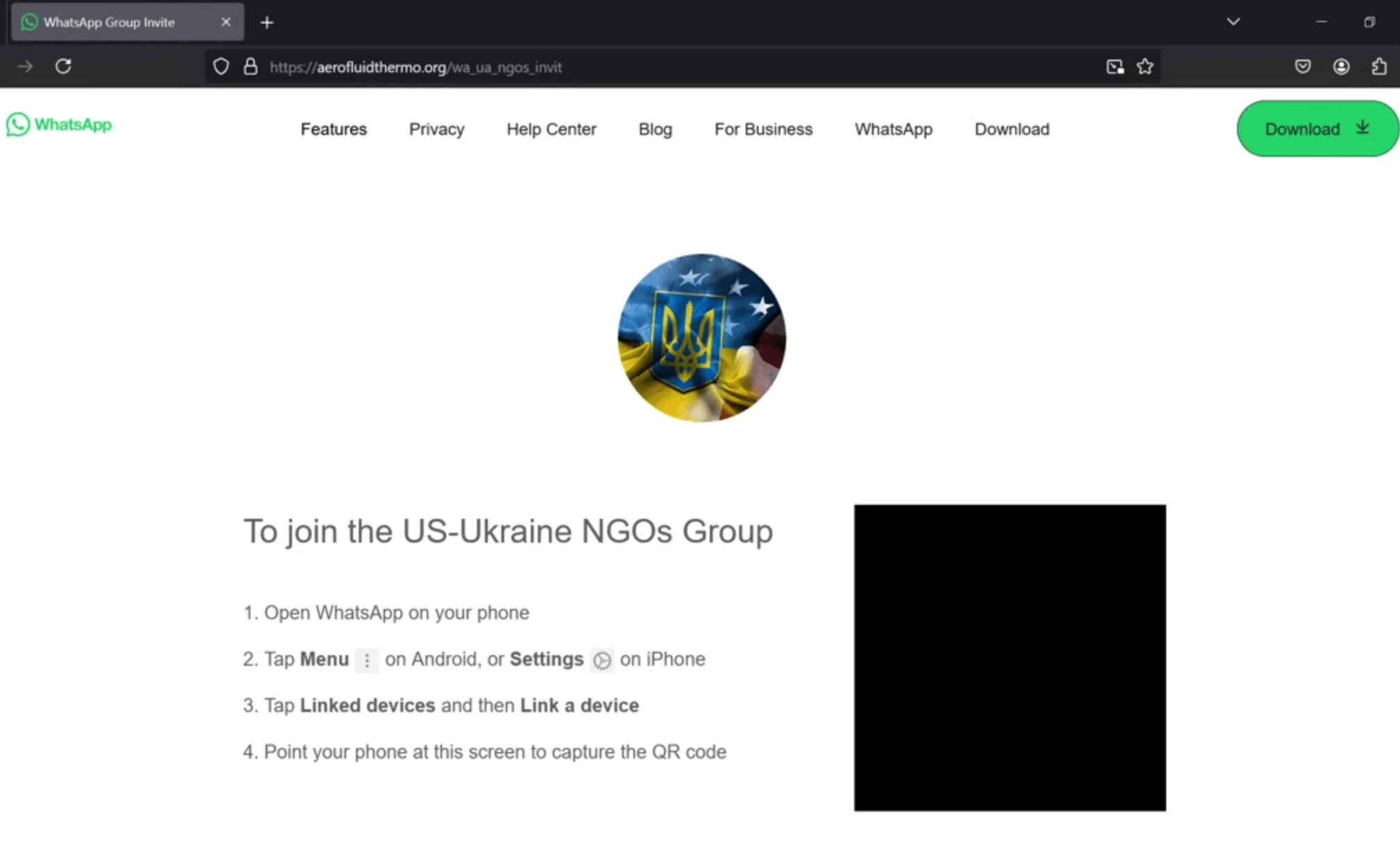
Fake WhatsApp invite page and the malicious QR code (Microsoft)
This attack is particularly insidious because it relies on social engineering rather than malware, making it more challenging for traditional antivirus tools to detect. Furthermore, reliance on QR codes has made users more accustomed to scanning them without hesitation, creating an opportunity for exploitation.
SOCRadar’s Brand Protection module monitors for impersonation attempts across phishing websites, fake social media accounts, and fraudulent applications. Combined with Phishing Radar in SOCRadar LABS, organizations gain advanced detection capabilities to identify malicious domains and emerging phishing campaigns targeting their brand.
Phishing Radar is a free SOC Tool available in SOCRadar LABS, providing insights into malicious domains and phishing activities.
Adaptation After 2024 Disruption
Last year, Microsoft and the U.S. Department of Justice (DoJ) took action against the Russian hacking group Star Blizzard, dismantling numerous domains used in spear phishing campaigns targeting U.S. government employees and nonprofits worldwide. Although this takedown operation in October 2024 dealt a significant blow, Star Blizzard has since adapted, shifting tactics to exploit WhatsApp as a new attack vector. This move highlights their resilience and ability to evade detection.
While the campaign reportedly ended in November 2024, cybersecurity experts warn of its potential resurgence or adoption by other threat actors. Microsoft’s analysis indicates that exposing Star Blizzard’s tactics often triggers significant changes in their tradecraft, emphasizing the need for constant vigilance.
SOCRadar’s Threat Actor Intelligence, under the Cyber Threat Intelligence module, offers in-depth insights into cybercriminal groups, state-sponsored operations, and their preferred attack vectors. Stay ahead of adversaries by uncovering their TTPs, IOCs, and latest operations.
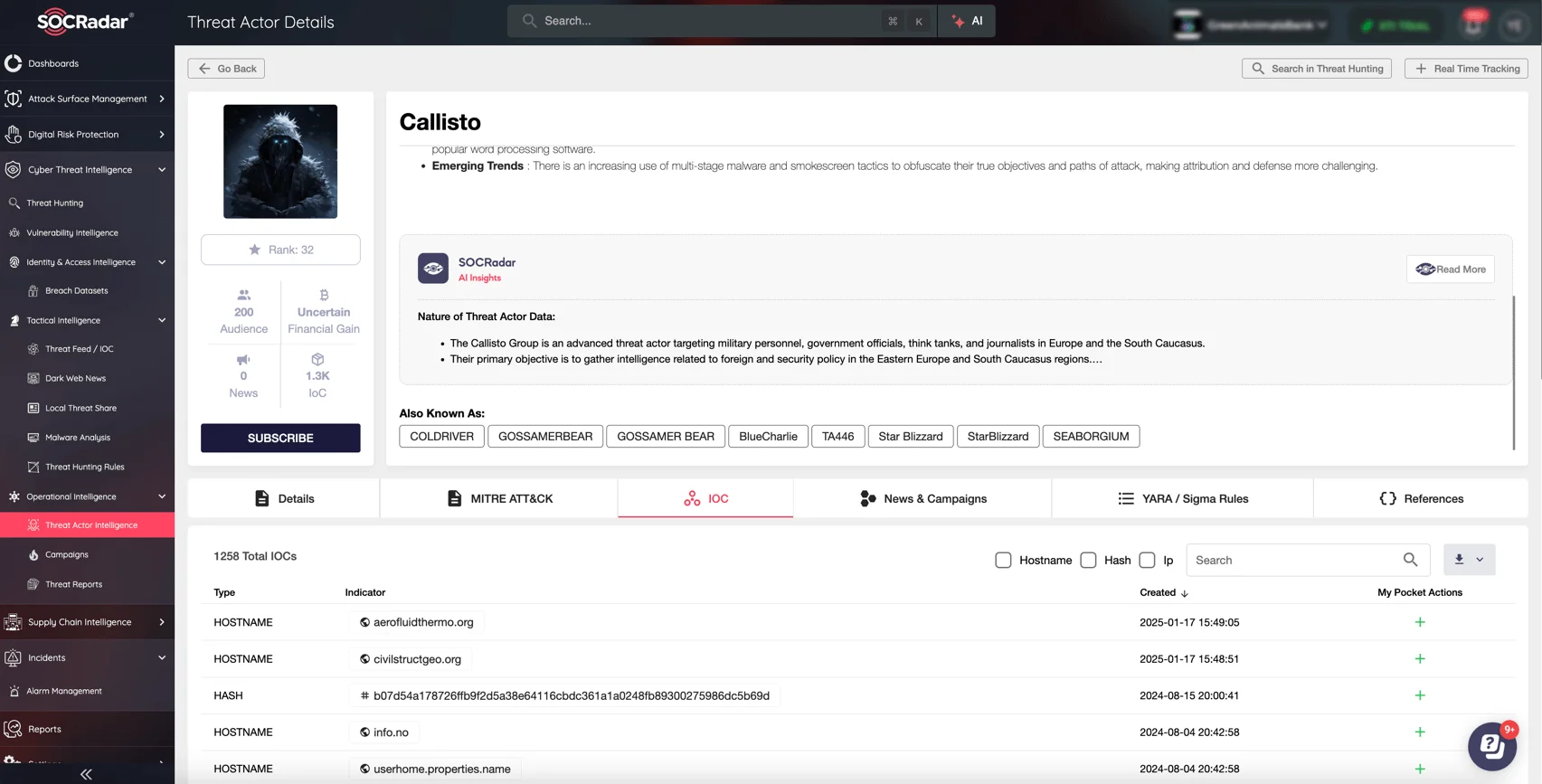
Details of Star Blizzard (a.k.a. Callisto, UNC4057) on SOCRadar Threat Actor Intelligence
Here are the key benefits the Threat Actor Intelligence feature provides:
- Threat Actor Profiling: Detailed information on cybercriminal organizations, including motivations and methods.
- Malware Analysis: Insights into malware families used in campaigns, such as those employed by state-backed groups.
- Contextual Intelligence: Understand the broader impact of emerging threats on your industry.
Recommendations for Mitigating the Threat
To defend against Star Blizzard’s tactics, cybersecurity professionals and individual users must adopt proactive measures to enhance their digital defenses and minimize risk exposure:
- Verify the authenticity of emails from unknown senders, especially those containing links or QR codes. Hover over links to preview their destination before clicking. Unshorten shortened links to see the original page link.
- Avoid scanning QR codes from unsolicited sources. When in doubt, contact the sender using a known communication channel to verify the message’s authenticity.
- Use phishing-resistant Multi-Factor Authentication (MFA), such as hardware security keys, to provide an added layer of protection.
- Conduct regular cybersecurity training sessions to educate employees on recognizing phishing red flags and preventing unauthorized access.
- Regularly check the “Linked devices” section in WhatsApp to identify and remove unauthorized devices linked to your account.
Phishing domains pose a serious risk to your organization. Taking swift action is essential to identify and eliminate these threats before they inflict damage. Complementing the Brand Protection module, SOCRadar’s Phishing Domain Takedown Service ensures rapid mitigation of active phishing campaigns. Additionally, with the new Takedown Activity Management dashboard on the SOCRadar XTI platform, your security team gains unparalleled visibility into takedown operations, enabling a more streamlined and effective response to phishing threats.
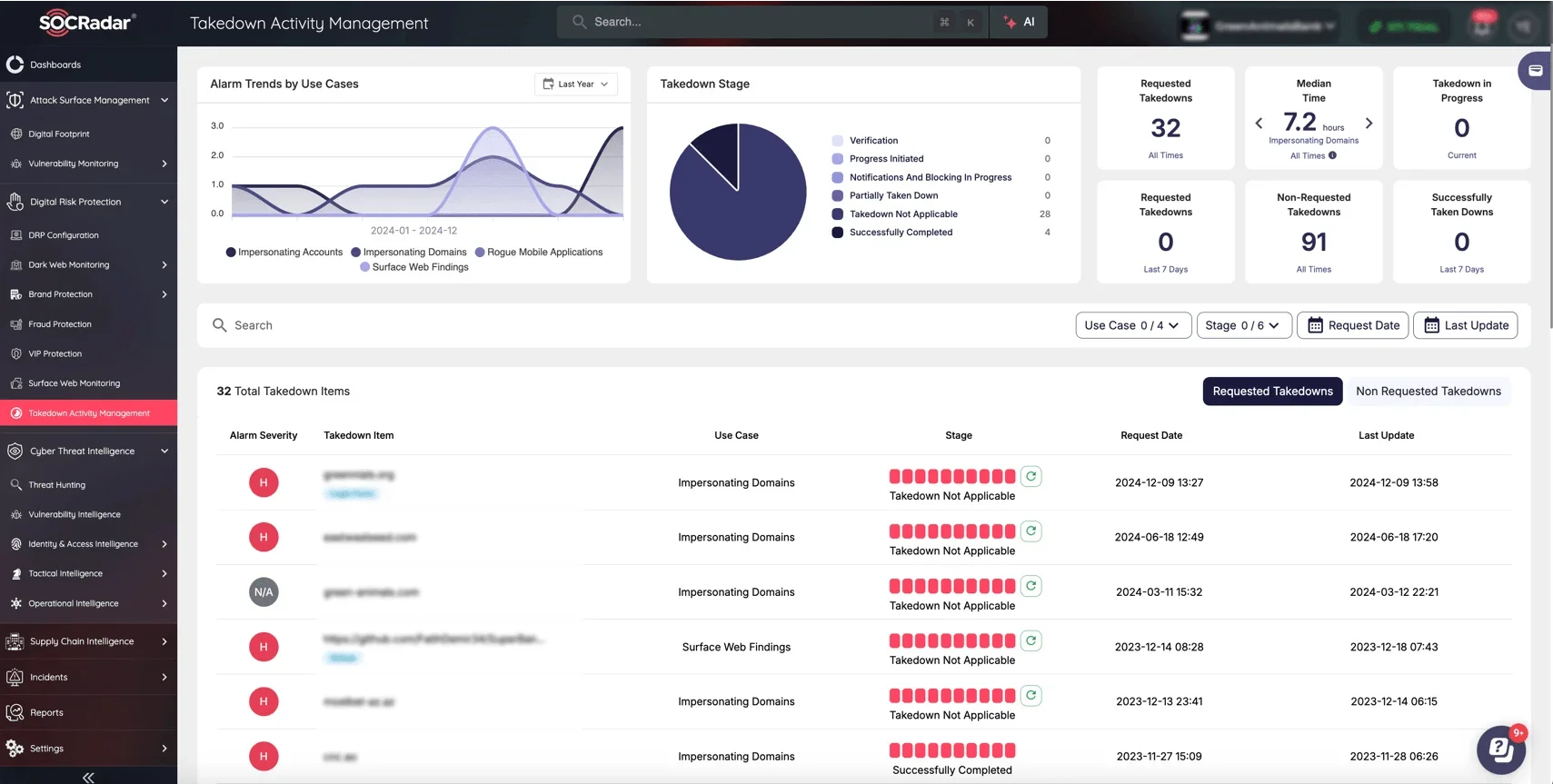
Takedown Activity Management dashboard on SOCRadar XTI platform
How Can You Detect Compromise?
Detecting compromise early is critical to mitigating the potential damage from Star Blizzard’s campaigns. Indicators of Compromise (IoCs) related to this campaign include domains such as civilstructgeo[.]org and aerofluidthermo[.]org, which were associated with the group’s previous phishing infrastructure. Monitoring for connections to these domains or similar suspicious activities can help identify threats.
A threat hunting query is also available, designed to be used with Microsoft Defender XDR to identify surface events that may have communicated with Star Blizzard’s Command and Control (C2) infrastructure. This query can identify potential compromises by analyzing DNS and URL click events, among other things. The query is available on Microsoft’s blog, along with additional details on the campaign.
Organizations should utilize these resources alongside advanced email security solutions and endpoint detection tools to strengthen their ability to detect and respond to threats from Star Blizzard and other sophisticated actors. By remaining proactive, individuals and entities can minimize their risk and enhance overall cybersecurity resilience.



































