Improve Your Network Security
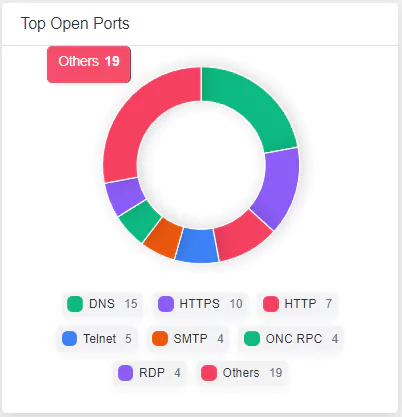
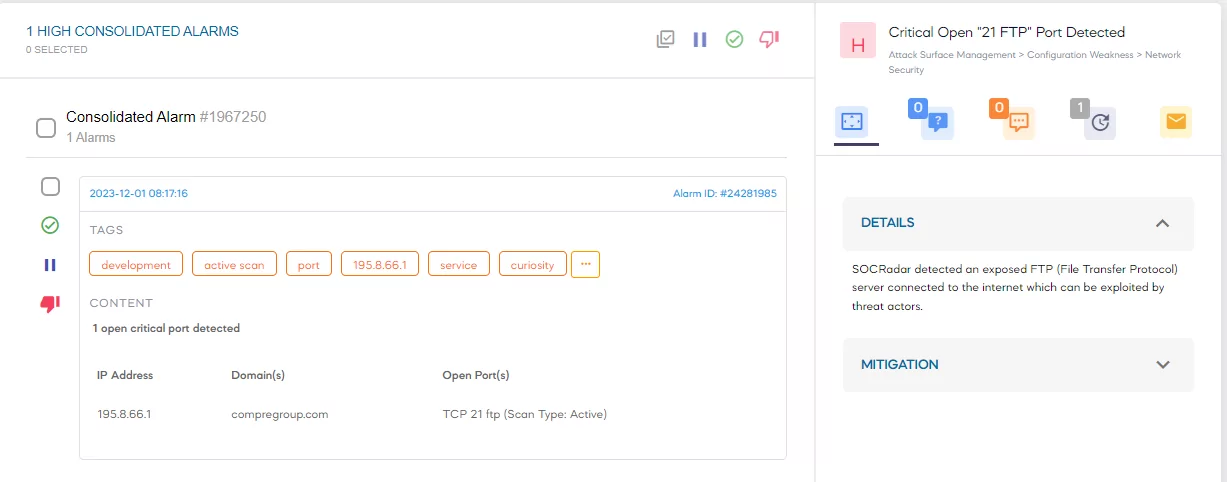
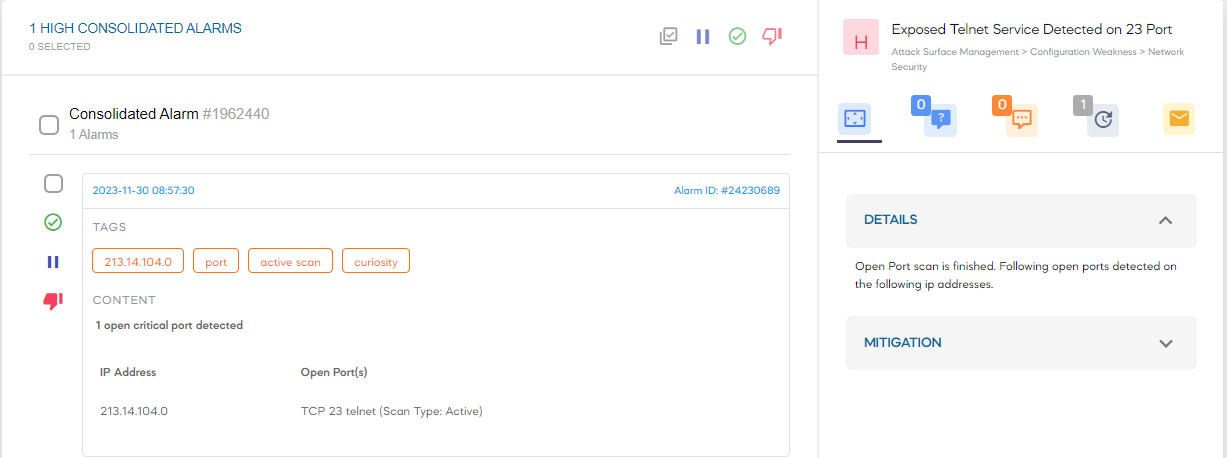
Ports act as communication gateways where network interactions originate and terminate. SOCRadar identifies open ports that lack adequate protection or proper configuration, preventing them from becoming exploitable vulnerabilities for threat actors. By leveraging SOCRadar’s capabilities, you can proactively block unsecured ports to become starting points for network security breaches.
Reduce Your Attack Surface
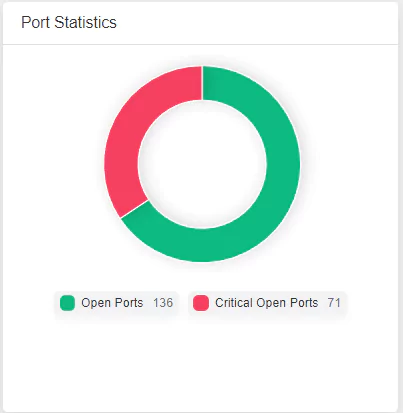
Various successful cyberattacks or any prevalent cyber threat are due to open ports visible to threat actors. Many organizations have numerous unused or improperly secured ports, creating a vast attack surface. SOCRadar enables you to reduce and manage your organization’s attack surface by frequently scanning it, generating and sending you alarms when it detects open ports related to your IPs monitored on your Digital Footprint, and ensuring you have only the required ports available and accessible.
Proactively Defend Against Ransomware Attacks
Vulnerabilities like open Remote Desktop Protocol (RDP) ports and unpatched Server Message Block (SMB) protocols are pivotal tools exploited by ransomware attackers. Recognizing the susceptibility of SMB ports and potential risks associated with misconfigured RDP, proactive defense strategies become imperative. SOCRadar’s critical port detection feature continuously monitors and analyzes network traffic, identifies open and unpatched SMB ports, and exposes RDP ports. This real-time visibility allows for swift action; Thus, you can gain crucial early warning and take decisive action to mitigate ransomware attack risks.
Enhance Regulatory Compliance
Detecting and disabling unwanted ports is a crucial part of a comprehensive cybersecurity strategy. SOCRadar’s advanced Critical Port Detection feature empowers organizations to achieve compliance with critical regulations that require you to detect and disable unwanted ports, such as Payment Card Industry Data Security Standard (PCI DSS), North American Electric Reliability Corporation (NERC) ‘s Critical Infrastructure Protection (CIP) standards, Health Insurance Portability and Accountability Act (HIPAA), and Center for Internet Security (CIS).