Proactive Exploration of Your Digital Landscape
In the digital realm, where threats evolve rapidly, SOCRadar’s Digital Footprint module offers more than just surveillance; it provides an insightful exploration of your online presence with a hacker’s mindset. Adopting potential attackers’ perspectives, our service dives into every corner of your digital landscape. This methodical exploration uncovers known and unknown attack surfaces, bringing to light aspects of your digital presence that were either overlooked or previously unseen. Our approach ensures that you receive a comprehensive and continuously updated view of your public-facing digital assets.
In-Depth Analysis for Comprehensive Protection
Our meticulous analysis goes beyond surface-level assessments. We investigate each component of your digital presence, identifying vulnerabilities that could be exploited. This includes analyzing web applications, network infrastructure, and even social media footprints. By understanding the intricacies of your digital landscape, we uncover potential security gaps and offer strategic recommendations to strengthen your defenses.
Transforming Weaknesses into Strengths
Our proactive approach to managing your digital footprint transforms vulnerabilities into enhanced security opportunities. Gaining clarity and control over your digital presence allows you to proactively address and neutralize risks before they escalate into threats. We empower you to turn these identified weaknesses into robust defenses, ensuring your digital assets are protected and resilient against cyber threats.
Comprehensive Identification of Digital Blind Spots
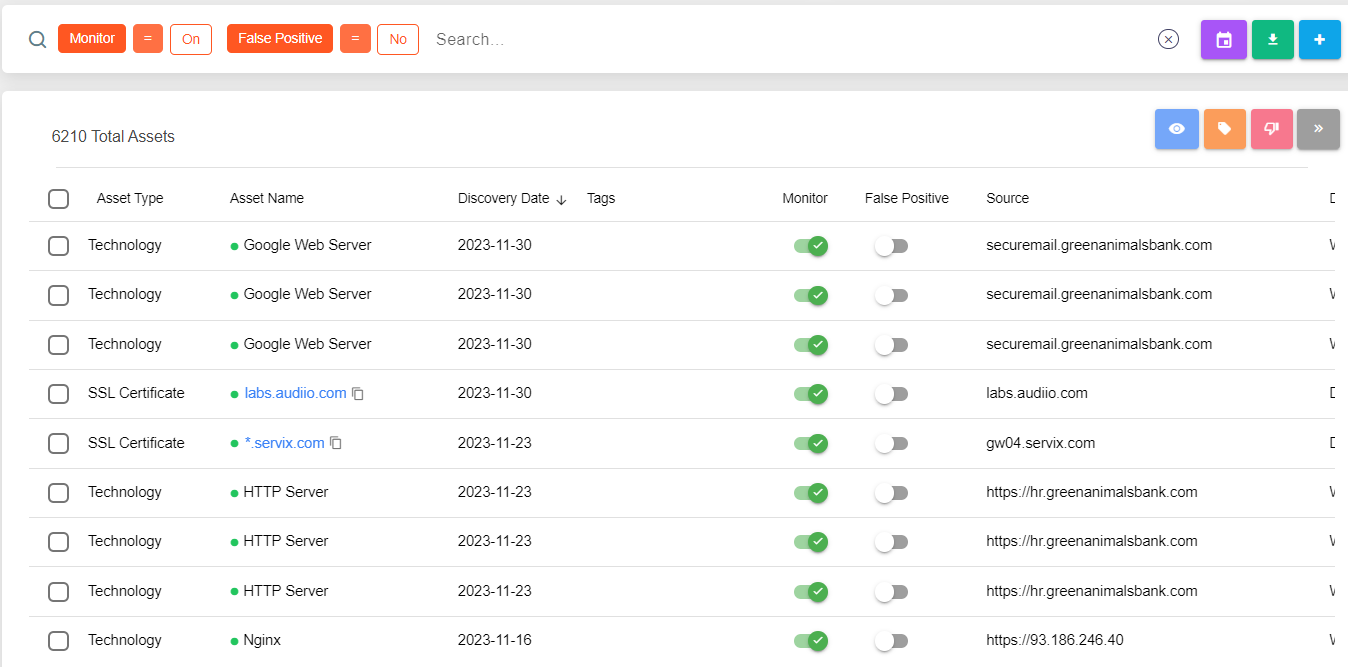
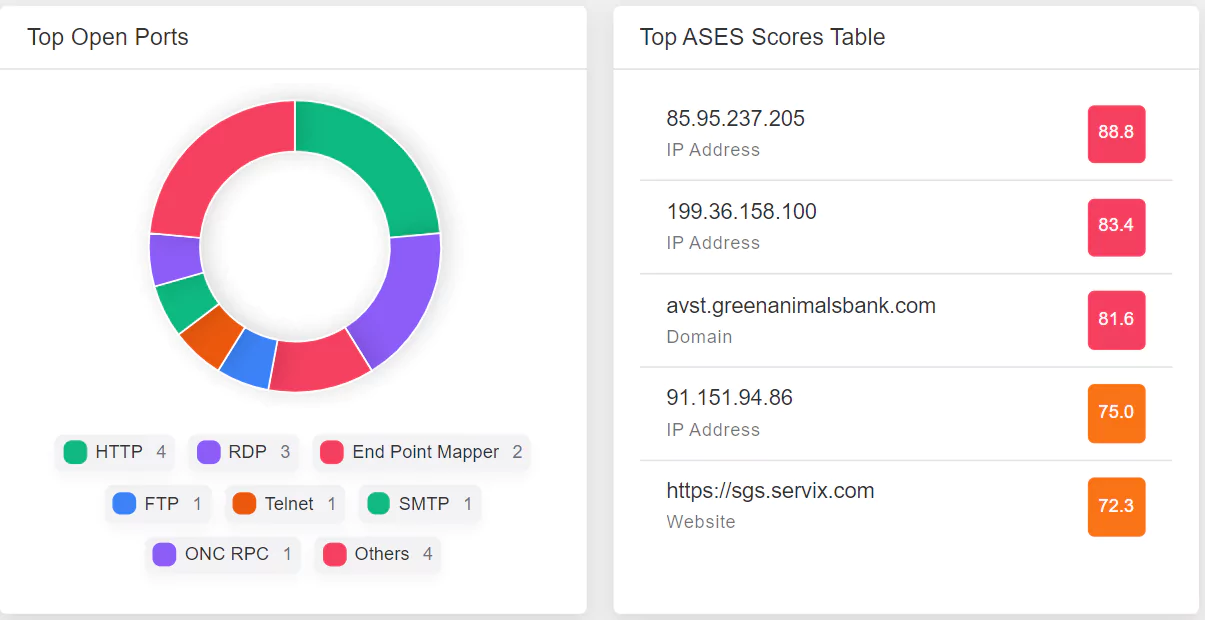
We conduct a thorough identification process to pinpoint and address digital blind spots swiftly. Our service rigorously examines various aspects of your digital footprint. This includes inspecting open ports that may be inadvertently exposed, verifying the validity of SSL/TLS certificates, and identifying any publicly exposed employee data. We also scrutinize outdated or unpatched technologies, vulnerable JavaScript frameworks, CMS applications, unprotected login forms, and shadow cloud services.
Uncovering Overlooked Digital Assets
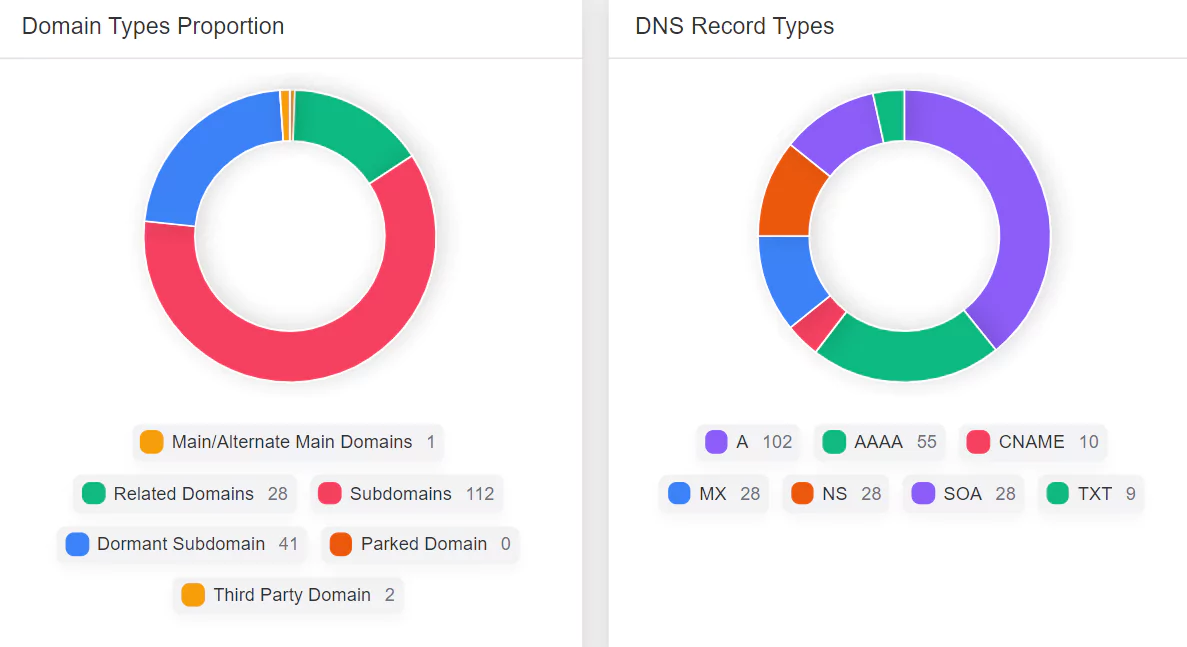
Our investigation extends to forgotten domains or websites and domains registered by different departments within your organization. We also pay close attention to unattended subdomains and dormant subdomains susceptible to takeover attacks. By monitoring these often-overlooked digital assets, we provide a complete picture of your digital exposure, helping you secure every aspect of your online presence.
In-Depth Examination of Technology and Web Assets
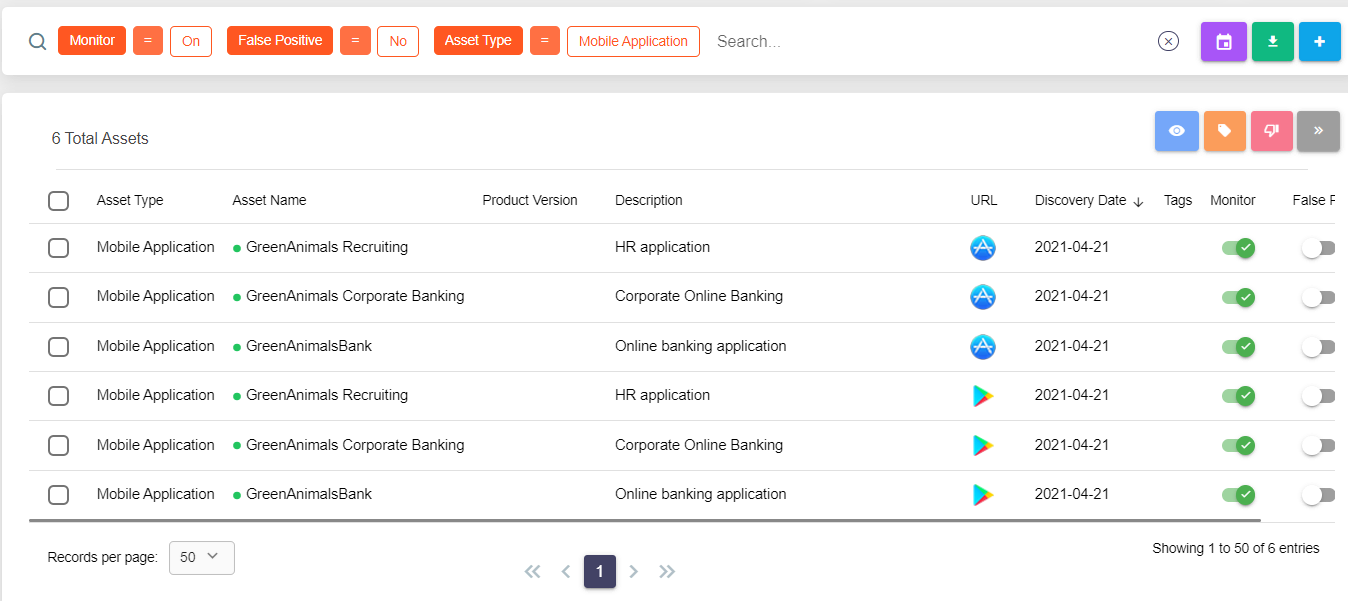
Our comprehensive examination of your technology stack and web assets leaves no stone unturned. We assess everything from the software you use to your digital properties, ensuring they are up-to-date and secure. Our team analyzes your entire digital infrastructure for vulnerabilities, offering insights and solutions to fortify your online presence.
Covering Your Digital Identity
We prioritize the security of your digital identity by continuously monitoring and protecting it against emerging threats. Our service includes safeguarding against unauthorized domain usage and mitigating the risk of subdomain takeovers. We ensure that every aspect of your digital identity is protected, maintaining its integrity and preventing potential cyber incidents.