What Identity & Access Intelligence Can Reveal
Threat actors continue to take advantage of credentials. According to Verizon, nearly a third of breaches involved the use of stolen credentials in the past decade. Over the years, SOCRadar has had massive data of compromised credentials (from data leaks, breaches, stealer logs, and dark web sources). By utilizing this vast data pool, SOCRadar Identity & Access Intelligence provides insights into compromised credentials and user access patterns, empowers users to detect which identity is seen, and analyzes the access information such as URL, username, mail address, etc. seen on an identity.
Access Intelligence: The Missing Piece of Your Security Puzzle
Is just knowing which key (identity) is stolen enough to secure your company building? Identity intelligence helps you determine which keys of which of your users have been stolen, but Access Intelligence is crucial for knowing when, how, and where those keys are stolen.
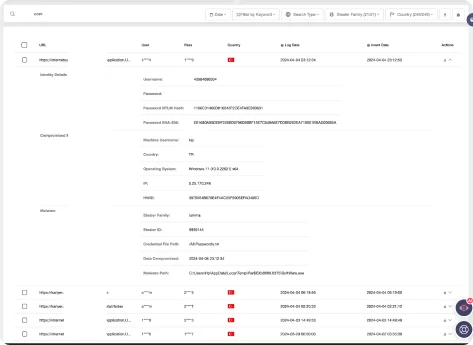
SOCRadar equips users with detailed access information, including on which date, in which info stealer malware, from which computer, from which IP address the compromised credentials are exposed.
The Power of Analyzing Info Stealer Logs with SOCRadar
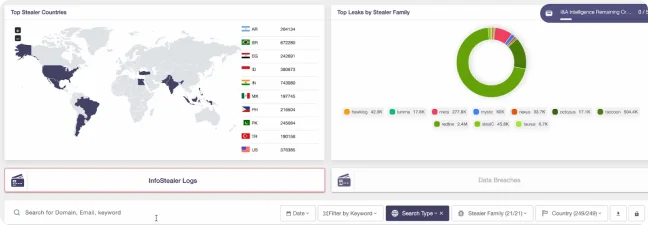
Among the most exploited data sources in cybercrime, stealer logs provide attackers with a treasure trove of stolen credentials and other sensitive information. Analyzing these logs is critical for protecting your business.
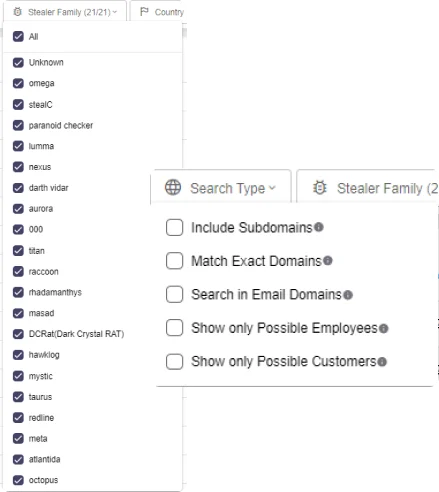
SOCRadar empowers you to gain deep insights from info stealer data. Search by keywords, domains, and emails. Utilize filters like “Stealer Family” and “Country” to refine your search. Additionally, analyze data from the perspective of “Possible Customers” or “Possible Employees” to identify compromised accounts and prevent further damage.
SOCRadar’s Exposure Timeline Visualization provides a clear picture of info stealer activity over the past month, helping you swiftly understand the distribution of potential compromises among your customers and employees.
Comprehensive Exploration of Breach Datasets
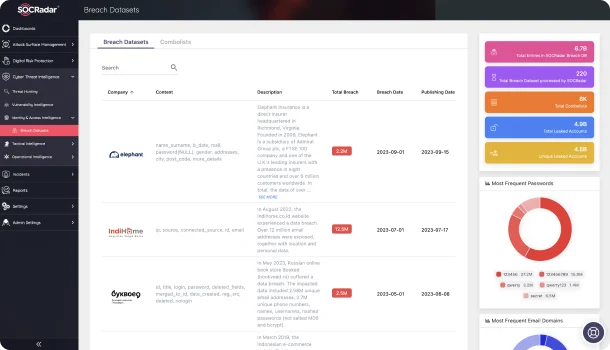
In today’s digital landscape, rapidly identifying and understanding compromised data is vital for ensuring security and privacy. SOCRadar’s Breach Datasets act as a robust search engine, granting access to extensive collections of breached data, including sensitive documents, credit card details, and personally identifiable information (PII), providing a critical resource in the fight against data breaches.
Navigate through the depths of the dark web with SOCRadar’s Breach Datasets. Discover compromised data and safeguard your organization’s sensitive information.