
The Dangers of Third-Party App Stores: Risks and Precautions
When downloading applications, smartphone users typically consider the pre-installed Apple App Store or Google Play. However, there are other third-party app stores to get apps, and there is a growing interest in those alternative marketplaces due to their extensive range of applications. Despite their diverse selection, obtaining apps from unofficial app stores can pose potential risks. This post will discuss the risks associated with third-party app stores and ways to mitigate them.
What are third-party app stores?
Third-party app stores are digital platforms that offer apps for mobile devices and other computing platforms. The official device manufacturer or operating system does not own or operate them. There are numerous third-party app stores, such as Amazon App Store, GetJar, and Aptoide, to name a few. These stores offer an alternative to official app stores like Apple’s App Store or Google Play for users to download and install apps. This type of download is often referred to as sideloading.
Why are third-party app markets so popular?
These markets offer a variety, including free and modified/pirated versions of popular apps and games, productivity tools, and more. They allow users to access applications prohibited by official app stores because of policy violations or geographical restrictions. Furthermore, they do not require users to sign up to download an app.
What are the Risks?
Although third-party marketplaces seem to provide many benefits for users, they also present critical risks for users and official app owners. According to the Nokia Threat Intelligence Report, Android devices continue to be the primary focus of malware attacks due to their open ecosystem and the presence of third-party app stores. They make up 50% of all compromised devices, as seen in Figure 1.
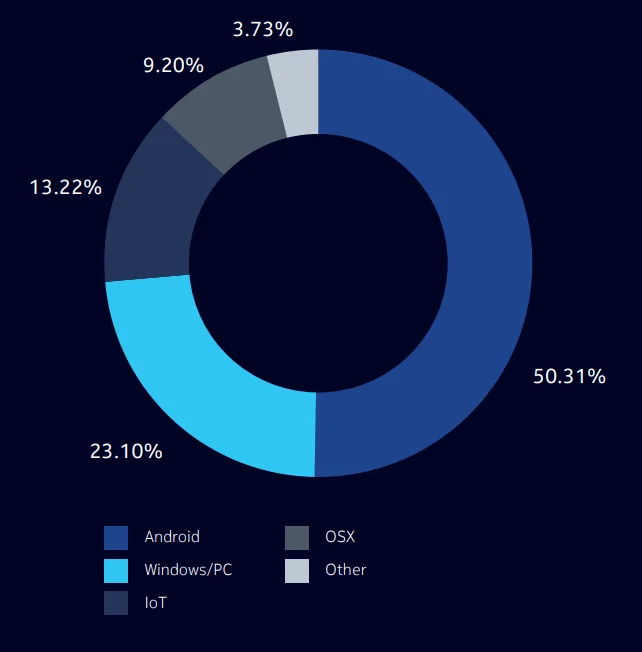
Figure 1 – Infections by device operating system (Nokia Threat Intelligence Report 2021)
To gain a better understanding of the risks, we will categorize them.
Lack of app review process
Security threats in mobile apps can risk user safety. Thus, app stores like App Store and Google Play have strict review processes. These processes are vital to prevent security threats from reaching consumers and ensure that apps in these stores are safe. However, app review protections aren’t always available when sideloading apps from third-party stores. Due to relaxed app submission and review policies, hosting malicious or counterfeit apps can become easier on those marketplaces. For example, In November 2022, a group of Android apps that appeared to be harmless file managers were found malicious and infecting users with the Sharkbot banking trojan. The Bitdefender analysts discovered and reported the new Android trojan apps to Google. Then, Google removed them from the Play Store. However, one of the Sharkbot loader apps, Phone AID, is still available on third-party app stores (See Figure 2).

Figure 2 – Malicious app hosted in third-party app store
The primary objective of SharkBot is to trigger unauthorized financial transfers from compromised devices through Automatic Transfer Systems (ATS), circumventing multi-factor authentication. SharkBot allows attackers to obtain sensitive banking information such as login credentials, personal details, and current balances. It uses overlay attacks to steal sensitive data and intercept legitimate banking communications via SMS.
Brand impersonation and reputation damage
Counterfeit apps in third-party stores can heighten the risk of brand impersonation, potentially harming the brand’s reputation and causing dissatisfaction among loyal customers due to subpar app performance or malware linked to the brand. Consumers might confuse it with the official app, encountering issues that range from minor technical hiccups to severe malware infections. Even if users are not exposed to malware, they may opt to use a competitor’s app due to the poor performance of the fake app.
Repackaging attacks
Threat actors obtain original apps from official app stores, inject malicious code into them, and then distribute these evil versions via third-party app stores to steal the user’s identity, credentials, or payment details.
Out-of-date versions of original apps
Companies update their mobile apps frequently to enhance user experience and bolster security. However, third-party app stores host older versions of updated apps, which can lead to inferior user experiences or put users at risk of identity theft or payment fraud.
Rooting or jailbreaking widens the attack surface
In addition to all the above risks, users may need to root (Android) or jailbreak (iOS) their devices to install apps from third-party stores, which can void warranties and introduce additional security risks.
How to mitigate the risk?
The first precaution that comes to mind is that users should not install applications from third-party application stores, but as you can imagine, it isn’t easy to convince users of this. Furthermore, malicious actors employ various strategies to lure people towards unauthorized third-party websites, deceiving users into downloading malicious software.
Therefore, app developers or app owner companies should take several steps to mitigate the risks. First, companies must monitor third-party app stores automatically, as manual monitoring is impractical. Secondly, if any fake or copycat app is detected, this app should be taken down from that marketplace immediately. However, removing an app from an app store is not simple and requires more than sending an email request.
How can SOCRadar help?
SOCRadar Alarm Management periodically monitors third-party app markets and alerts you if it encounters your apps’ names. A sample alarm notification is shown in Figure 3.
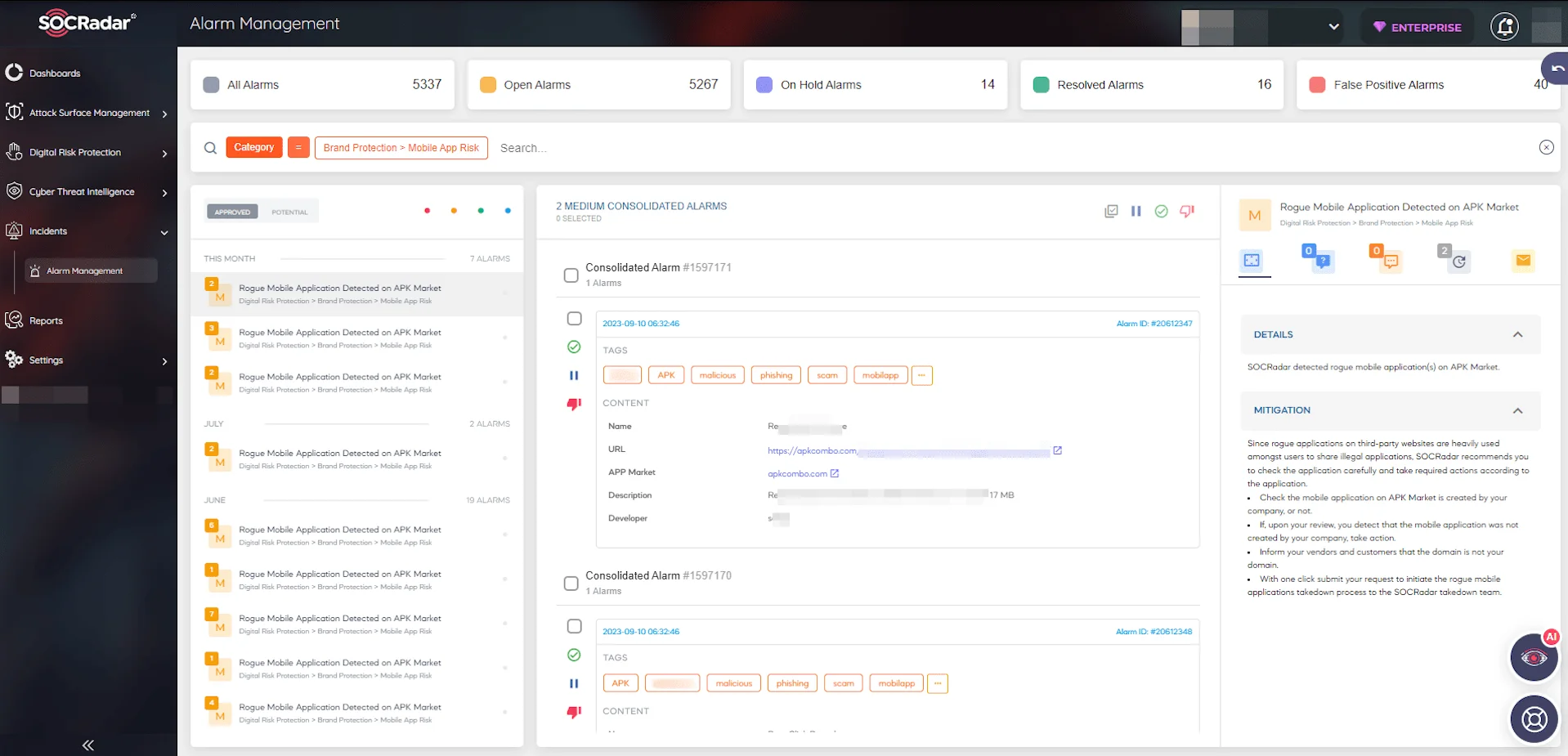
Figure 3 – Rogue mobile application detected alarm sample
Once a rogue app has been detected, evaluating its associated risks is essential. After the risk assessment, if you decide to take down the app, you can easily send a takedown request via the SOCRadar Brand Protection page (See Figure 4). Once the request has been submitted, the SOCRadar Takedown Team will take over and work towards removing the app.
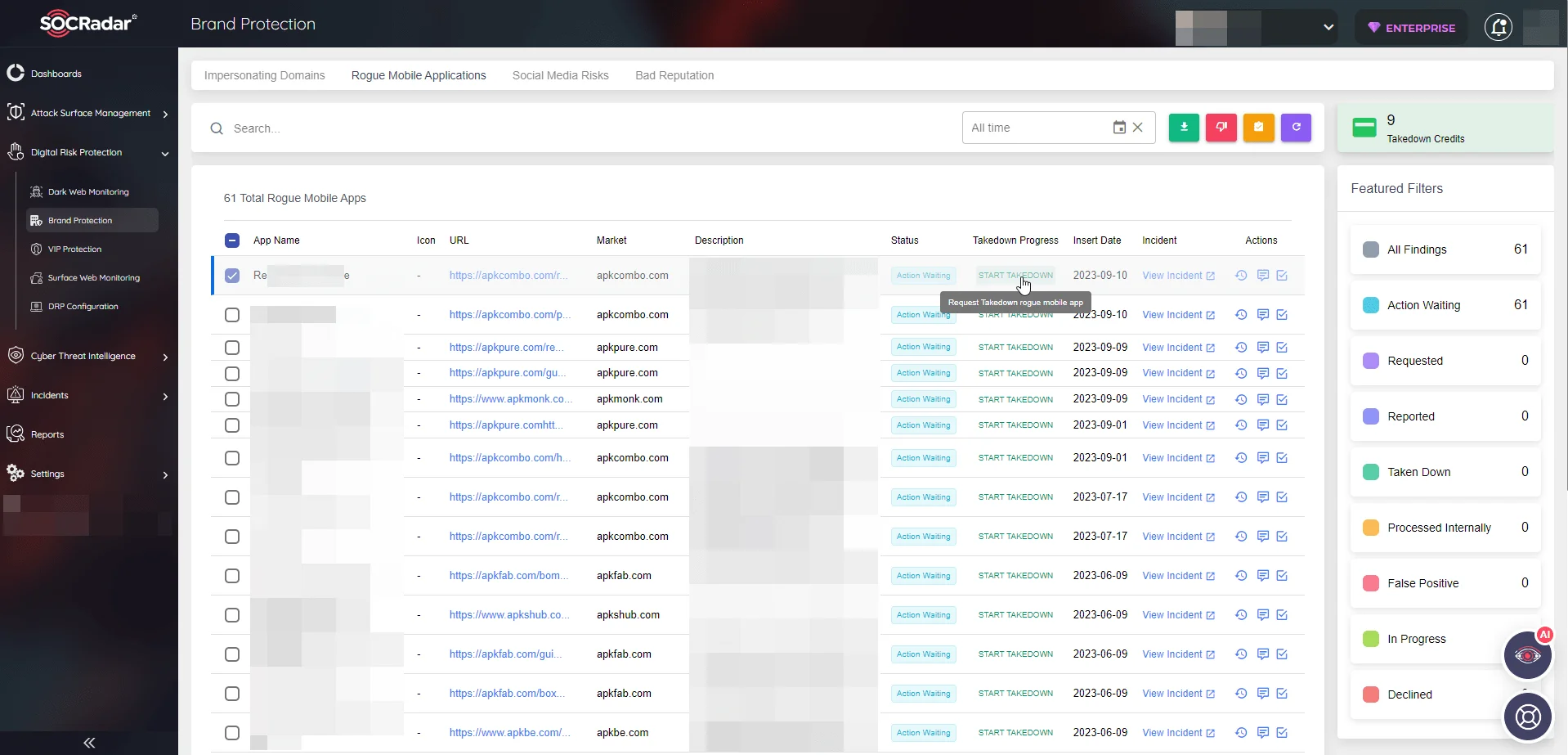
Figure 4 – Rogue mobile app dashboard and takedown option
You can also check our blog post about how to Better Protect Your Mobile App with SOCRadar MAS Module.
In today’s smartphone-dominated landscape, mobile applications have emerged as vital cornerstones for companies and creators seeking to develop profitable connections with their customers. Therefore, tracking fake or copied applications and restricting customer access to them as much as possible is necessary to ensure a healthier customer experience and to avoid revenue loss.




































