
The Difference Between Data, Information and Intelligence
Data. Information. Intelligence. Oftentimes confused by people, these very different terms can not be used interchangeably but have a tight connection between each other. The order goes like this: Data is collected, then assembled into information, and only then handed to a human analyst to analyze and transform it into intelligence.
They all have the same importance – collect the wrong data and you get meaningless information or give the wrong context to the information and you get – guess what – worthless intelligence, or even worse, intelligence that leads you to irrelevant or even catastrophic decisions.
Of course, it is not that simple, there is more to each of these terms, and there is more to the differences they have with each other. We have prepared this blog to discuss this issue and point out the importance of their differences. We’ll also provide some key takeaways for you.
Now, let’s dive deeper into them separately, and give you examples about each.
What is data?

The rawest fact that gives a clue about an event is called data. That event can be anything – an interaction with your company assets, a transmission, or any other observed activity, suspicious or not. It is the start point of an idea, an opinion, or a discussion. We can think of all data as suspicious, but only when they become information you can understand if that suspicion was true or false.
Data is a very generous term, but thinking about it only in the cybersecurity aspect, data we collect is IPs, Domain names, URLs, malware hashes, system file changes, DNS record changes, and other indicators of compromise (IoCs). All of these are important to generate information for intelligence, but data alone doesn’t mean there is a compromise.
Takeaway 1: Data is a raw fact that gives a clue about an event. It can be an IP, a domain name, a malware hash, and so forth.
Now that you have got a huge volume of unprocessed data in hand, you need to arrange it into useful collections to be able to answer your questions. This way, you obtain information. Simply put, information is processed, organized, and combined meaningful and useful data that draws your security experts nearer to decision-making.
There are millions of information-retrieving sources. However, relying on that information can sometimes be challenging. You need to understand its validity, then give context to it. The contextualized information you produce is the decision-making intelligence you want.
Let’s say you get a huge number of IPs requesting to connect to a server, hence you understand that’s the reason the server’s performance is low. This information can be useful to lead you to decision-making intelligence.
Takeaway 2: As you move from data to information, the volume of the outputs decreases but its value increases.
What is threat intelligence?

Finally, intelligence is what all companies need for accurate decision-making. Threat intelligence feeds have become a major component for many of them. These feeds help companies in the prediction of potential cyber-attacks and taking proactive measures. They also give them insight into threat actors and allow them to be aware of their malicious activities.
Intelligence is the interpretation (usually) a human analyst does, after processing large volumes of data collections and later analyzing the information in hand. If we continue with the previous example, a human analyst would suggest taking immediate action because all the signs indicate that the targeted server is probably experiencing a DDoS attack.
Takeaway 3: There are some misconceptions about what the difference between information and intelligence is. Intelligence assists the decision-making process by transforming “what”, “how” into “why”, when”.
However, to transform information into intelligence, the analyst needs to know the company or object that is being discussed very well, or else made decisions and taken actions can be catastrophic.
Going from data to intelligence is a complicated process. It is very challenging too, but the value it adds to your business is immense. During this transformation process, the quantity of the outputs decreases. Yet, the value of the output increases exponentially.
Takeaway 4: Threat intelligence helps organizations predict potential cyber-attacks and take proactive measures.
Why is this difference even important?
Most of the time, it is difficult for security experts to make decisions. Your company security resources need to be careful when cutting through potential threat data to understand what that threat is, and most importantly if that threat data is an actual threat. You can’t just accept that data as sufficient to make decisions.
You need to understand how to put the pieces together and get information out of the potential threat data you collect. Besides, when you get a report about a bad IP address in your SIEM tool, you don’t get much intelligence. You need to leverage at least human analysis, if possible, even artificial intelligence, to give context to that threat data. This way, you are more likely to reveal tools, tactics, and procedures (TTPs) that the threat actor is using.
According to the Pyramid of Pain, understanding the TTPs of threat actors gives you the privilege to cause them the highest level of pain. When you know the way an adversary accomplishes its attacks, you can understand the value of intelligence and will be sure how to act upon it.
You need to know the order of the processes that transform data into intelligence. Even more important is to understand where you stand with your security resources.
Takeaway 5: Threat intelligence is important, but without the right context, it is just information, which can not lead to decisions.
Learn more about SOCRadar’s perspective of transforming data into intelligence
Monitoring a wide variety of internet sources and layers pose difficult challenges, but SOCRadar accurately crawls, analyzes, and interprets data from many sources to identify leaked credentials and other confidential data. Only with the top crew of cybersecurity specialists and state-of-the-art tools can you take action to protect your business against sophisticated cyber attacks.
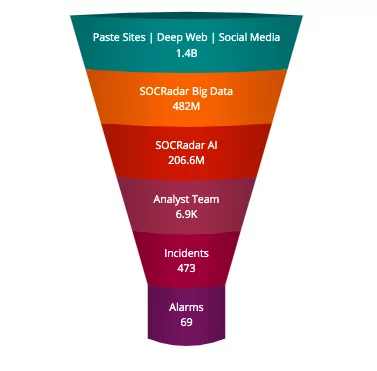
SOCRadar’s historical precision and growing robust database help analysts cut through the noise, narrowing down relevant security items and prioritizing SOC analyst time and energy on the most critical security incidents.
SOCRadar offers a broad variety of threat feeds including the malware hashes, 0-day vulnerabilities, malicious domains, IP addresses, hacked websites, and host-based indicators of compromise (IoCs).
Proactively monitor the surface, deep and dark web for data exposures relevant to your organization.


































