
The Role of Threat Intelligence in Anti-Fraud Efforts
In an age where our lives are seamlessly intertwined with the digital realm, tales of unexpected encounters with scammers have become all too familiar. The unsettling scam call appears to be from a legitimate government agency, demanding personal information for supposed social insurance matters.
It’s the bewildering message you’ve never interacted with from a Facebook account, pleading for financial help in dire circumstances. And then there’s the bizarre and unlikely scenario of receiving a message from a celebrity’s social media account, earnestly asking you to purchase and send them a gift card or money.
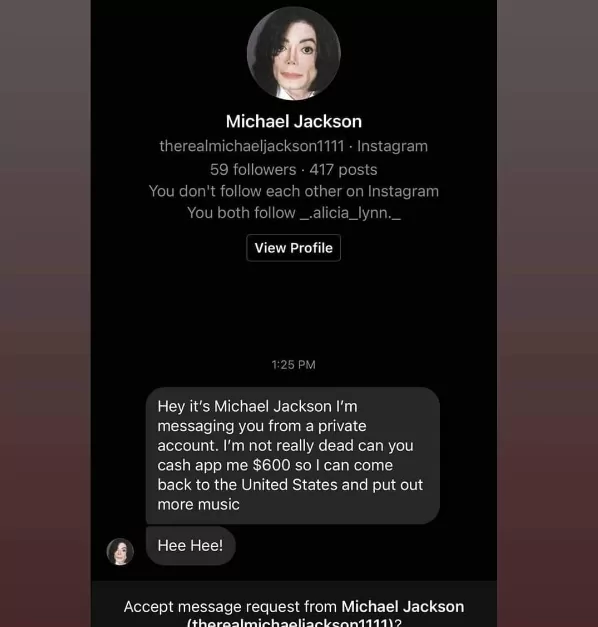
These encounters aren’t just mere anecdotes; they’re glimpses into the sprawling world of digital fraud. The increasingly intricate ways scammers infiltrate our lives reveal a harsh truth – our digital footprints have become trails that opportunistic criminals are eager to follow. However, amid the disconcerting experiences, a powerful tool emerges: knowledge.
Navigating the Landscape of Digital Scams
The digital age has ushered in unprecedented levels of convenience and connectivity, but it has also opened the doors to a proliferation of scams and fraudulent activities. As we explore the multifaceted world of digital fraud, we must grasp the diverse scams cybercriminals employ to exploit unsuspecting individuals. Here are some of the most prevalent types of digital scams.
- Impersonation Scams – Deceptive Disguises
Impersonation scams capitalize on trust and familiarity to deceive victims. Whether it’s a scam call purportedly from a government agency or a message from a friend’s compromised social media account, scammers are masters of disguise.
- Payment Fraud – Concealed Culprits
Another formidable threat is Payment fraud, including credit card fraud and unauthorized bank account usage. Cybercriminals steal sensitive financial information and conduct unauthorized transactions, causing substantial financial losses for individuals and organizations.
- Investment Fraud – Illusions of Grandeur
Investment fraud often takes the form of enticing promises of high returns, trapping victims in schemes that ultimately lead to financial ruin. These scams prey on individuals’ desires for financial success and security.
- Chargeback Scams – Twisted Reversals
Chargeback scams are a cunning technique where fraudsters exploit the chargeback process of credit card transactions. They make legitimate-seeming purchases, only to later claim that the transaction was unauthorized, leading to the payment reversal. This leaves both the purchased item and the money in the scammer’s hands.
As our lives intertwine with the digital realm, the risk of falling victim to these scams becomes increasingly accurate. The numbers and stories behind these scams highlight the pressing need for effective strategies to detect and prevent digital fraud. In the following sections, we will delve into the tools and practices that can empower individuals and organizations to navigate the intricate landscape of digital fraud armed with knowledge and resilience.
Deciphering the Inner Workings of Digital Fraud
In the labyrinthine digital fraud world, one motive is money. It’s the driving force behind the intricate web of scams and schemes that cybercriminals weave to exploit the unsuspecting. But what lies beneath the surface, enabling these fraudsters to execute their nefarious plans? Let’s dive into the mechanics of digital fraud, guided by insights from “The Little Book of Big Scams – 5th Edition” by the Metropolitan Police of the UK.
Fuel for the Fraud: The Precious Loot
At the core of almost every digital scam lies the pursuit of sensitive data – the golden key that unlocks victims’ financial assets and personal lives. Cybercriminals crave information such as credit card numbers, bank account details, passwords, usernames, and personal identifiers. Armed with this treasure trove, they can orchestrate various fraudulent activities, from unauthorized financial transactions to identity theft.
The Pathways to Data: Direct and Indirect Routes
Acquiring the coveted data follows two primary routes: directly from victims or indirectly through various means. Direct acquisition often involves social engineering and psychological manipulation of individuals to divulge confidential information willingly. Victims are coaxed or coerced into revealing passwords, personal identification numbers, or even granting device access.
Indirect acquisition, on the other hand, is often executed through data breaches. Cybercriminals target online platforms, retailers, or organizations to harvest massive amounts of data, capitalizing on vulnerabilities in their digital defenses. Recent years have seen high-profile data breaches that exposed sensitive information, leaving millions of individuals at risk.
Laundering the Loot: The Final Frontier
The path to profiting from ill-gotten gains doesn’t end with data acquisition. Cybercriminals must navigate the challenge of laundering their funds to avoid detection. Enter the concept of “money mules.” These unwitting individuals are often coerced or deceived into allowing their bank accounts to be used to funnel stolen money. Criminals leverage these accounts as intermediaries, making it difficult for law enforcement to trace the origins of the illicit funds.
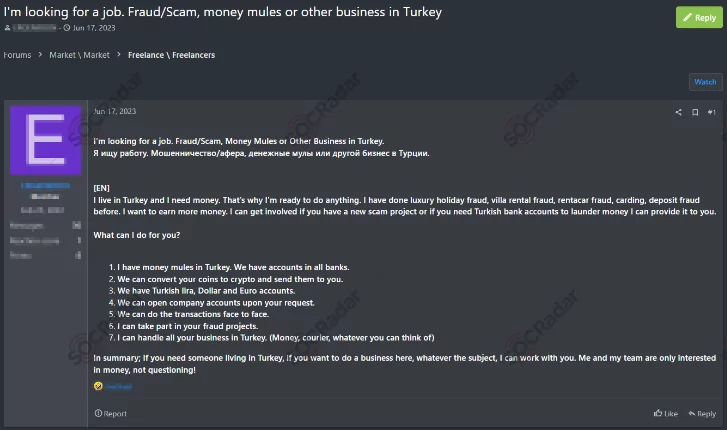
In essence, the journey of digital fraud encompasses the acquisition of data, the orchestration of scams, and the laundering of stolen money. Understanding these mechanics is the first step in comprehending the complexities of digital fraud. In the next section, we will delve into the countermeasures and strategies that can fortify individuals and organizations against the ever-evolving tactics of cybercriminals.
Turning the Tide: Unleashing Timing, Intelligence, and Disruption
In an era where data breaches can appear inevitable, and the persuasive tactics of scammers remain distressingly effective, completely eradicating these threats might seem insurmountable. Yet, our focus should shift towards minimizing the frequency and impact of these events.
It’s essential to recognize that cybercriminals rarely operate in isolated silos. These malevolent actors function within an intricate ecosystem where different players assume distinct roles. Some specialize in orchestrating data breaches, others curate and compile stolen information, and others concentrate on validating the accuracy of credit card data. This intricate division of labor necessitates collaboration, communication, and data exchange platforms, which often manifest as hidden forums on the dark web or channels on encrypted messaging platforms.
This reality, however dire, also presents a unique window of opportunity for defenders. While we might not be able to halt every data breach or eliminate the gullibility of potential victims, we can substantially mitigate the damage inflicted. How, you might ask? Through a blend of precise timing and proactive intelligence.
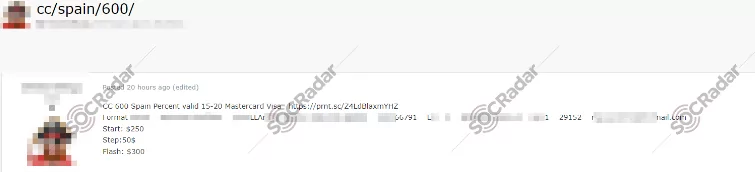
Consider this scenario: credit card numbers are spotted for sale on a shadowy corner of the internet. Swift action can be taken to nullify the card before it is misused, effectively reducing the potential financial loss. The defenders’ ability to detect and respond to such a development can directly impact the outcome, turning the tables on the criminals who now find themselves with worthless information.
Similarly, imagine identifying a newly registered domain that impersonates a reputable brand. The quicker such instances are detected and acted upon, the sooner the fraudulent website can be dismantled. By proactively hunting for malicious domain registrations and keeping a vigilant eye on emerging online threats, defenders can initiate a swift takedown process, sparing unsuspecting users from falling victim to elaborate scams.
But beyond direct intervention, the true game-changer is disruption. The objective isn’t necessarily to apprehend every fraudster or shut down every market and forum. Instead, it’s about making the business of fraud inherently unprofitable. This entails dismantling the architecture supporting these illicit activities, reducing the avenues for scammers to monetize their exploits. By disrupting their financial incentives and channels of operation, we not only prevent current attacks but also create an environment that dissuades potential criminals from entering the fray.
Through vigilant threat intelligence, rapid response, and strategic disruption, we cannot only thwart digital fraud attempts but also reshape the landscape of cybercrime itself.
Fortifying Defenses with SOCRadar: Your Shield Against Digital Fraud
In the ever-evolving battle against digital fraud, a comprehensive defense strategy becomes imperative for businesses seeking to protect themselves and their customers from falling victim to the myriad scams and schemes of threat actors. This is where threat intelligence solutions like SOCRadar come into play, offering a robust arsenal of tools designed to empower organizations to detect and respond to fraud attempts and proactively disrupt cybercriminal operations.
External Attack Surface Management by SOCRadar: Unveiling Your Digital Footprint
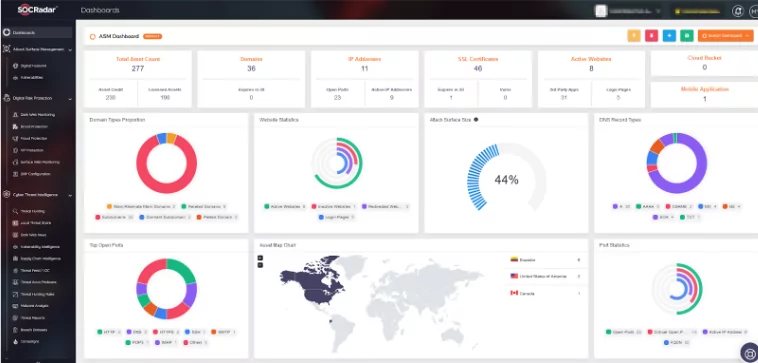
Understanding your digital landscape is the first line of defense against cyber threats. Yet, in today’s cloud-driven environment, manually maintaining an up-to-date inventory of your assets is arduous. Supplying continuous and dynamic inventory is where SOCRadar shines. Our External Attack Surface Management suite provides real-time insights into your organization’s assets and, more importantly, highlights those of critical importance. This insight empowers you to fortify your defenses where they matter most, minimizing the chances of overlooking vulnerable entry points that threat actors could exploit.
Digital Risk Protection: Shielding Your Brand and Assets
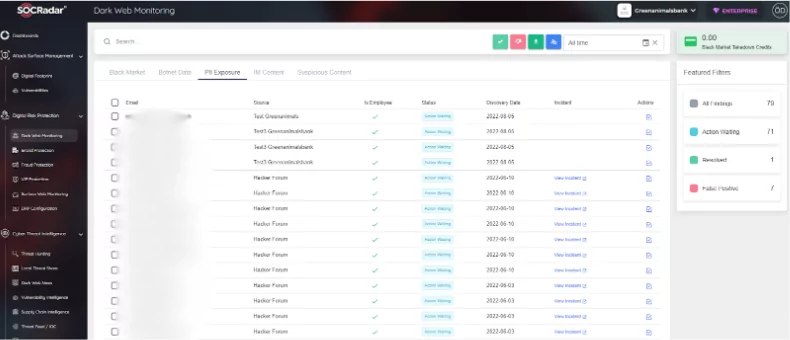
Once you identify your digital assets, the next step is to ensure they are not hijacked, abused, or impersonated. From credit card numbers to impersonating domain registrations, even seemingly harmless information can become powerful tools for cybercriminals. Moreover, personal email addresses of your employees found in breached datasets could become entry points for phishing attacks.
Here, SOCRadar’s Digital Risk Protection services step in, offering a vigilant eye over the dark web and beyond, constantly monitoring for any reference to your organization. This proactive stance detects potential threats and allows for swift mitigation before they escalate into damaging breaches.
Threat Intelligence by SOCRadar: Staying Ahead of the Game
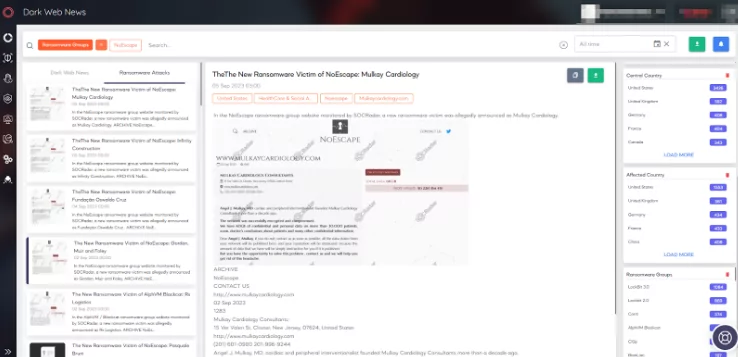
Yet, protecting your immediate assets is only a part of the equation. To stay ahead of cyber threats, you must be aware of global trends within your industry, the latest tactics used by threat actors, and emerging risks that might target your region. This is where SOCRadar’s Threat Intelligence suite proves invaluable. By aggregating and analyzing vast amounts of data from across the digital landscape, our platform equips your organization with the critical insights needed to anticipate threats, adapt your defenses, and minimize risk exposure.
In a digital landscape fraught with scams and fraud, it’s not just about safeguarding your assets but your future. SOCRadar’s comprehensive suite of solutions empowers businesses to take charge of their security, detect threats early, and proactively disrupt cybercriminal activities. By partnering with SOCRadar, you’re not just investing in a solution; you’re investing in a shield that fortifies your brand, assets, and growth. Together, we can turn the tables on cybercriminals and pave the way for a safer digital future.



































