
The Week in Dark Web – 05 March 2021 – Paypal & Fortune 500 Company Access Leaked
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. Paypal user credentials leak, Fortune 500 company network access sale, ransomware attacks on various companies from different backgrounds like e-commerce and crypto firms Here is the details of the major events that took place on the deep web this week:
Customer Database of Stellar.org on Sale
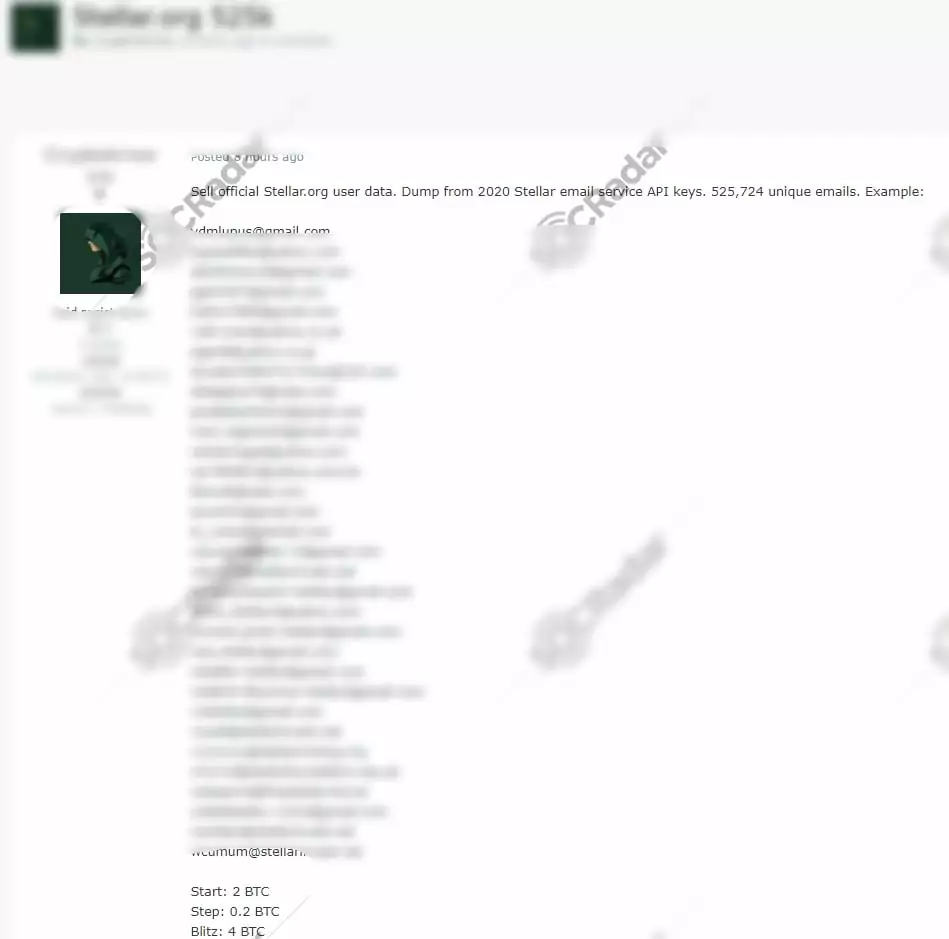
On March 2, 2021, on a dark web forum monitored by SOCRadar, the actor put a database on sale for 2 BTC assertedly obtained from Stellar.org. Stellar.org is an open-source network that uses the protocol Stellar, a blockchain protocol for the digital currency that enables cross-border transactions between various currencies. People register on Stellar.org with their email and bank accounts, then they can build wallets. The threat actor allegedly has the user database of Stellar.org containing 525.725 users’ email and according to SOCRadar Analyst, these emails can be targeted by phishing and social engineering attacks. According to the actor, who claimed to dump the database from 2020 Stellar email service API keys, including emails all data is official.
Login Informations of PayPal Accounts On Sale

On March. 2, 2021, new login credential data of the FinTech giant PayPal was leaked by the actor on a dark web forum monitored by SOCRadar. Claiming to have obtained the database by spamming, the threat actor would share the login credentials of 3000 users. Further, the samples clearly show that as well as credential data the buyer could reach IP addresses, user agents, emails and phone numbers.
Customer Database of a Korean E-Commerce Junggos Leaked
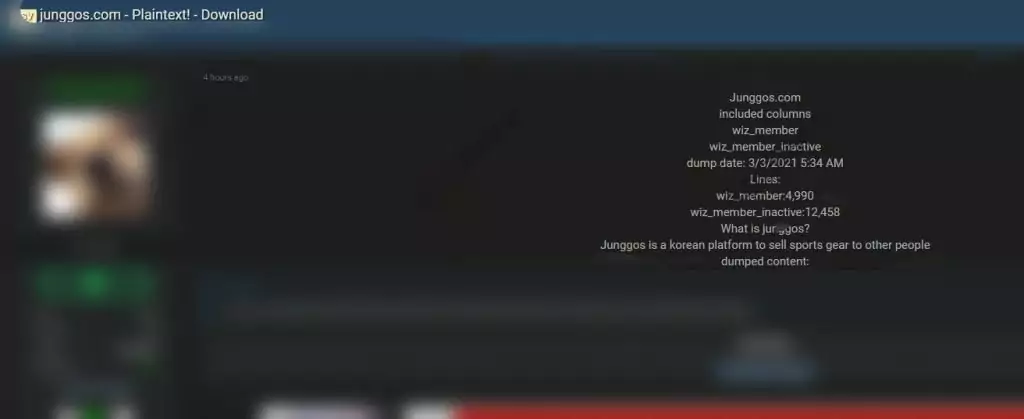
On March 4, 2021, on a dark web forum monitored by SOCRadar, the threat actor attempted to sell a database of a Korean startup Junggos.com. Junggos.com is a Korean e-commerce platform to sell sports material to people and has a revenue of over $6 million. According to the threat actor’s claim, the database, dumped on 03/03/2021, contained credentials and PII (Personal Identifiable Information) data like birthday date, scholarship, income of 17.000 users as plain text.
Customer Database of VO Company From UK on Dark Web
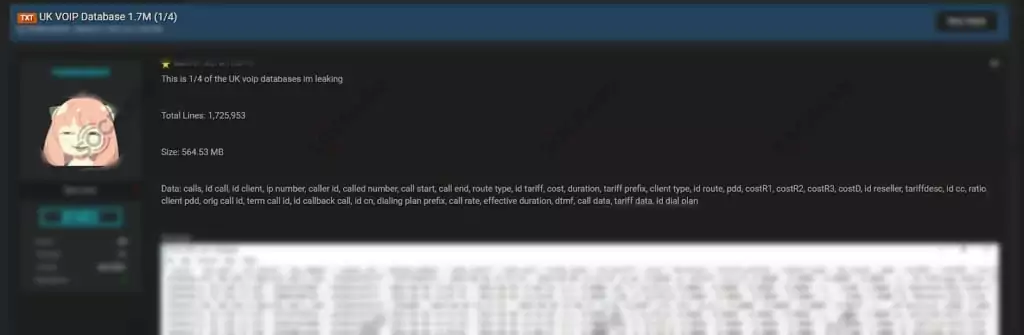
On March 3, 2021, the actor offered to sell network access for allegedly belonging to a telecommunication company operating in the United Kingdom on a dark web forum monitored by SOCRadar. According to the threat actor, the VoIP database included calls, IP numbers, caller IDs, and many data of 4.8 calls.
AWS Cloud Keys Sale Detected for a United States Fortune 500 Company
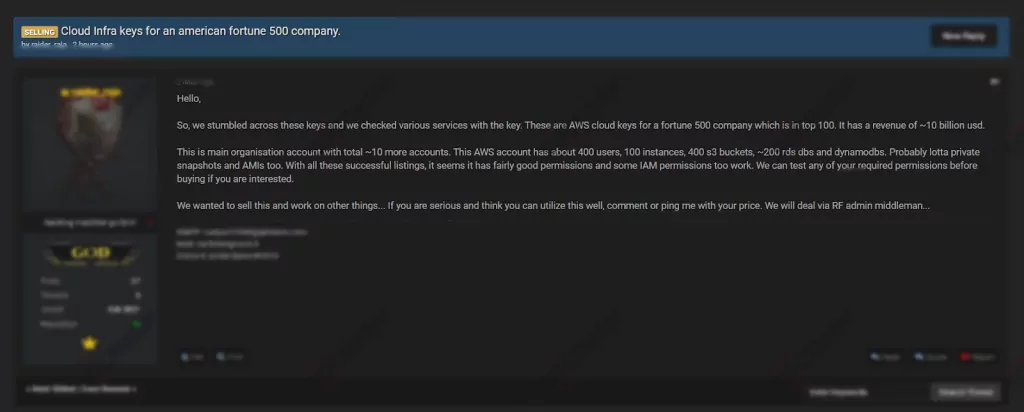
On March 4, 2021, an unauthorized network access is on sale allegedly belonging to a Fortune 500 company on a dark web forum monitored by SOCRadar. According to the threat actor’s claim, the company is in the top 100 of Fortune 500 and has revenue of $10 billion. The actor asserted to have AWS cloud account keys of the company and these accounts, seized by the main organization, have about 400 users. Moreover, the buyer could have permission to AMI and IAM. The actor underlined that they are open to test any permission before selling.
Customer Database of LiteBit Is on Sale
LiteBit: industry / revenue / employee? / company / how use
Dumped in 2019
Sample data: username email address
Over 206k
Sale on XMPP
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.

































