
The Week in Dark Web – 14 March 2022 – Ransomware Attacks and Data Leaks
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. Again, rise of ransomware attacks, some database thefts, and stealing customer data, that took their place on the headlines this week. Click here to read the last weeks post.
Find out if your data has been exposed on the deep web.
The New Ransomware Victim of Conti
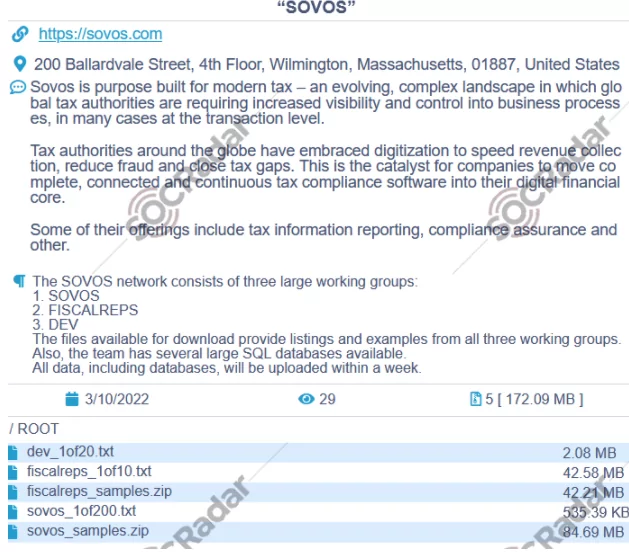
On March 10, a huge database of all working groups of a company was put up for sale on the dark web. The victim company is related to modern tax technology that originated in the USA, and has more than two thousand workers. This leakage allegedly includes SQL databases as well, which would be shared on the dark web within a week. The group behind the attack known as Conti is also responsible for the ransomware attack on the Irish healthcare system. If the victim organization would not cooperate with the ransomware group, the ransom gang threatened to leak banking data, licenses, certificates, agreements, contracts, and similar sensitive information belonging to the victim organization.
SQL Injection Sale Detected For An Ukrainian Firm On The Dark Web
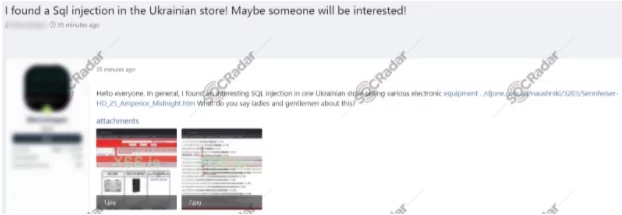
On March 10, a database of electronic equipment-related to a Ukrainian store was put up for sale on the dark web. This database allegedly includes email lists of different customer profiles from various countries, including 1 million consumers from Australia and 300 thousand casino and crypto customers from Germany. According to the vendor’s claim, this database has been acquired by using SQL injection technique. It is not clear that all of these lists have been obtained from the SQL injection attack, the vendor may have taken some of these lists from other attacks or put them for sale by combining the email lists collected from dark web forums. While there is not proper information about the data leakage, according to SOCRadar Analysts, this database could be used in different social engineering campaigns.
Database of Canada-Saskatoon City Airport Publised On The Dark Web
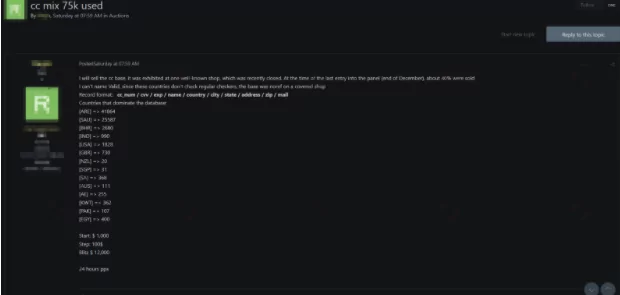
On March 7, SOCRadar detected a post allegedly publishing a stolen database on an underground forum. According to the vendor, there were details of about 75 thousand credit cards in the database. Owners of these credit cards were allegedly from different countries, including The US and Australia. While there is not information about how the vendor obtained the database, it is stated that the database includes credit card number, cvv number, country, city, adress and various personally identifiable information.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.

































