
The Week in Dark Web – 19 February 2021 – RDP Credential Sales on the Rise
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week, including major RDP credential sales, ransomware attacks on global corporations, and even some government organizations. Here is the breakdown of the events that took place on the deep web this week:
Database of UAE’s Telecommunication Giant Etisalat on Sale
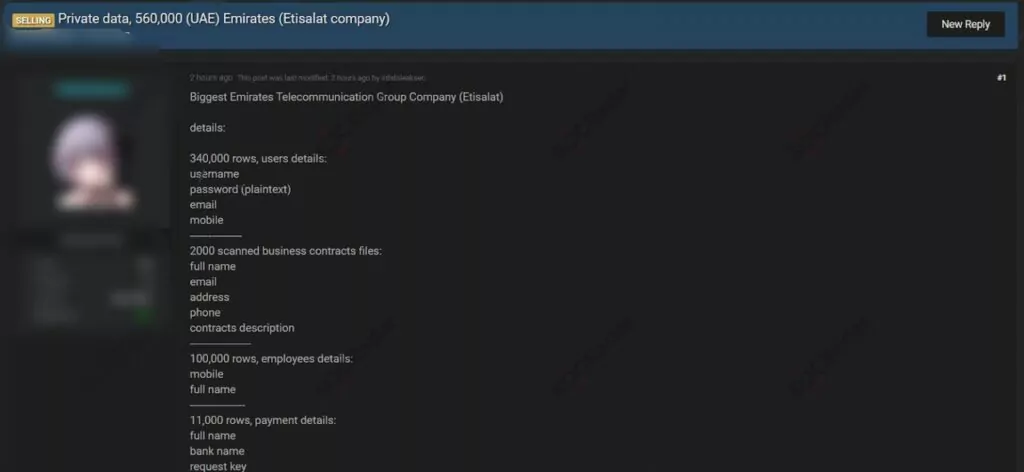
On Feb. 13, 2021, the actor put a database for sale assertedly obtained from UAE telecommunication giant Etisalat on a dark web forum monitored by SOCRadar. Etisalat, the largest mobile operator company in UAE with an income of over $14 billion, is among the world’s leading companies. According to the threat actor’s claim, the database contains 340,000 users with passwords, emails, and mobile numbers, and 100,000 employees with emails and mobile numbers. The actor also claims to have 11,000 payment details and 2000 contracts of the company. Moreover, samples prove these claims with ID card photos, contract scans, and various PII tables.
Official Immigration Data of Thailand Dumped on a Dark Web Forum
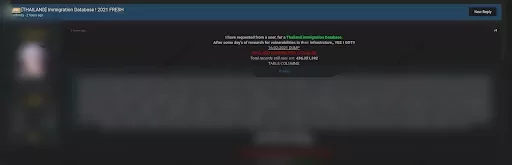
On Feb. 16, 2021, a new database from Thailand’s official immigration agency was leaked by the actor on a dark web forum monitored by SOCRadar. Claiming to have seized the database by using a vulnerability in the infrastructure, the threat actor shared titles of the database columns. According to the actor’s claim, the immigration database comprises full names, birthdates, country IDs, and much more immigrant information of more than 436 million people.
Philippines FinTech Company Cashalo’s Database for Sale
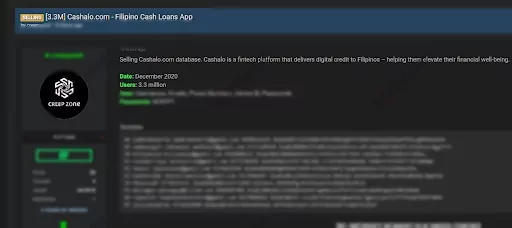
On Feb. 17, 2021, the actor offered to sell Cashalo’s data on a dark web forum monitored by SOCRadar. Cashalo, as a FinTech platform with over 5 million users from the Philippines, provides digital loans and offers different products to improve users’ financial situation. The data to be sold by the actor involves complete information that can be used for malicious purposes, such as phone numbers, emails, and credential data of 3.3 million users. The passwords in the database, obtained in December 2020, are allegedly encrypted with BCRYPT.
Unauthorized Network Access To the Slovakian and Czech E-Commerce Companies on Sale
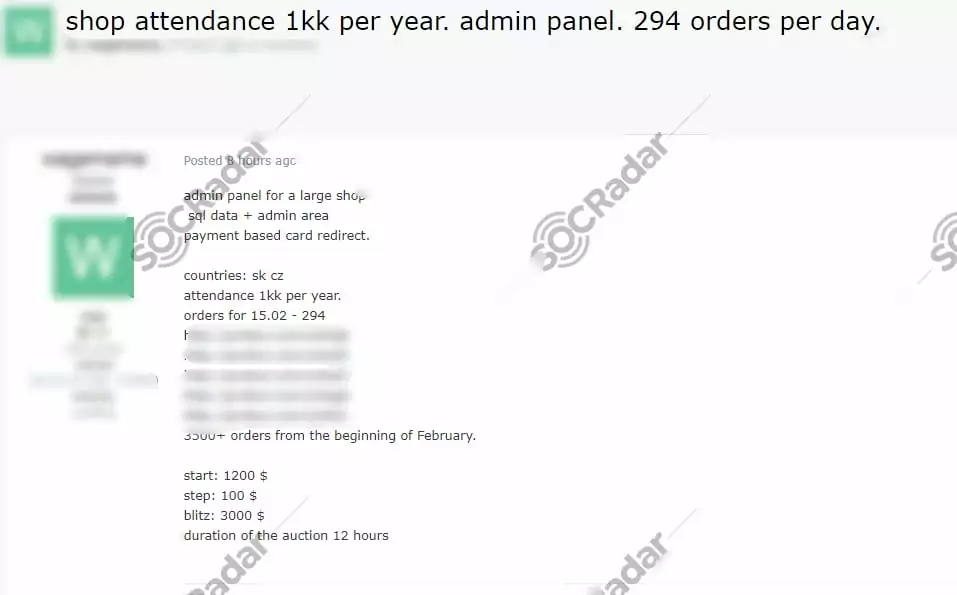
On Feb. 16, 2021, the actor attempted to sell network access for allegedly belonging to Slovakian and Czech E-Commerce firms on a Russian dark web forum monitored by SOCRadar. According to the threat actor claiming to have access to the administrator panel, the buyer would be able to reach SQL data. The actor also added that the payment page redirection would be possible.
SQLi Vulnerability of Nissan Motor Corporation on Sale
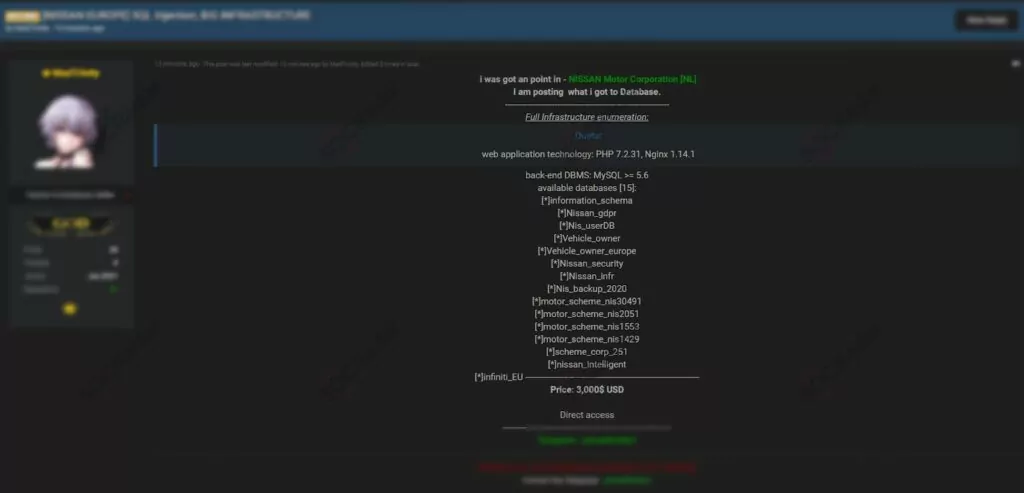
On Feb. 16, 2021, many databases owned by Japanese automotive giant NISSAN were leaked by the actor on a dark web forum monitored by SOCRadar. Threat actor claimed to have a variety of databases including users, vehicle owners, and backup files. The actor, who set a price of $ 3,000 for databases, also shared the web application technologies like PHP and Nginx with the version information.
DLL Hijacking Technique Using Kaspersky Posted on Dark Web
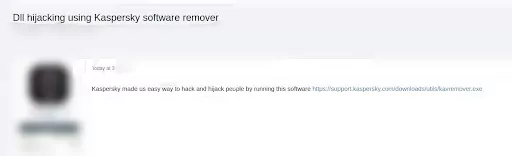
On Feb. 17, 2021, on a Russian dark web forum monitored by SOCRadar, the actor shared a DLL Hijacking technique related to the product removal tool of Kaspersky – Kavremover. In Windows environments when an application is starting, it searches for a number of DLLs to function properly. If these DLLs don’t exist or are implemented in an insecure way (DLL are called without using a fully qualified path) then it is possible to escalate privileges by forcing the application to load and execute a malicious DLL file. According to the threat actor’s claim, one can sniff and monitor all those DLLs that are called by Kaspersky software to replace them with malicious ones.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.



































