
The Week in Dark Web – 21 May 2021 – Deep Web Asia
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. admin access sale, company database theft, and stealing personal data are on the rise and took their place on the headlines this week. Click here to read the last week’s edition. Here are the details of the major events that took place on the deep web this week:
Unauthorized Webmin Root Access Sale Detected for a Saudi Arabian Company On the Dark Web
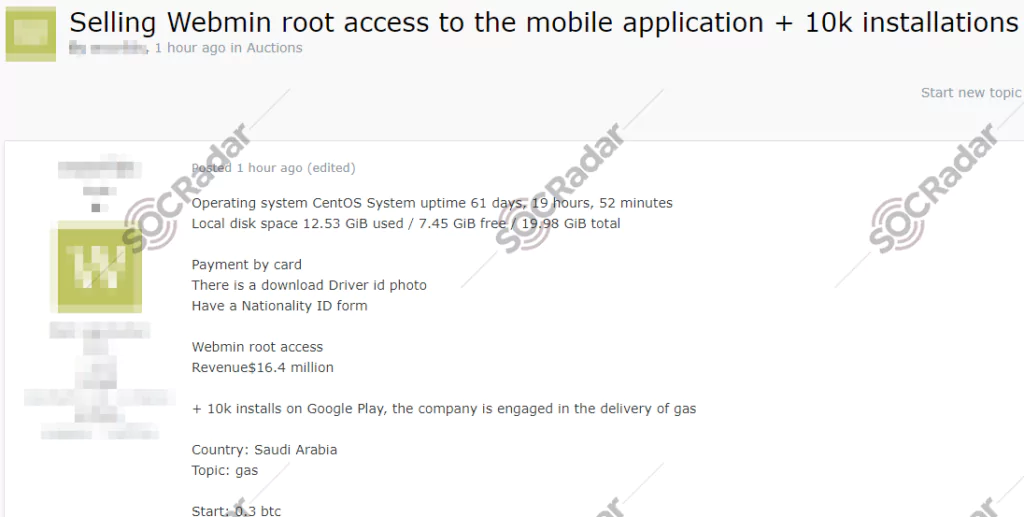
On May 14, 2021, on a dark web forum monitored by SOCRadar, a vendor put unauthorized webmin root access allegedly for a Saudi Arabian company for sale. According to the vendor’s claim, the victim company is engaged in the delivery of gas and petrochemical products with a revenue of $16.4 million. The vendor also stated that the webmin root access was on sale for the mobile application of the company and it comprised 12.5 GB of data.
Sensitive Documents of a Company operating in the UAE Dumped On the Deep Web
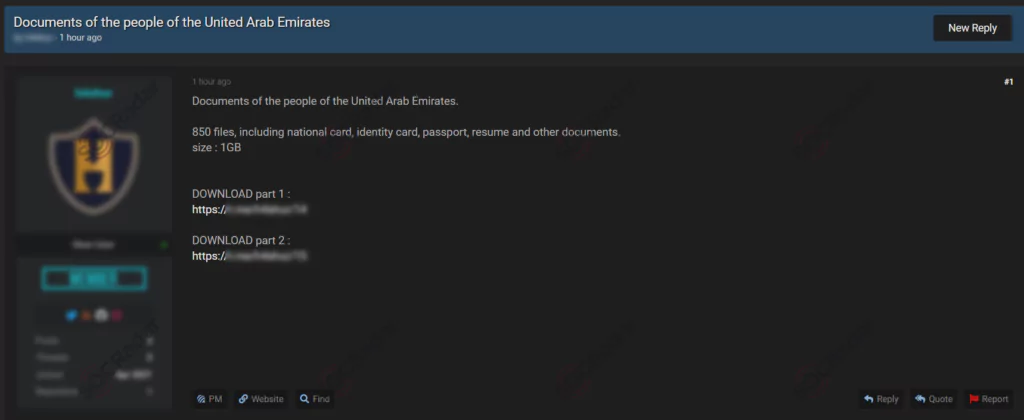
On May 18, 2021, on a dark web forum monitored by SOCRadar, a document database sale was detected for a company from the UAE. The dark web vendor claimed to have 1 GB of 850 files including ID cards, passports, resumes and various sensitive documents in the database. While there is no other information available about the company and the database, according to SOCRadar Analyst these files can be used for different social engineering attacks such as phishing.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.



































