
The Week in Dark Web – 26 February 2021 – 37M LinkedIn User Data Leaked
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. Linkedin user data leak, RDP credential sales, ransomware attacks on worldwide companies and government institutions were among them Here is the detailed list of the events that took place on the deep web this week:
Database of Ecuador Ministry of Finance Leaked on Dark Web
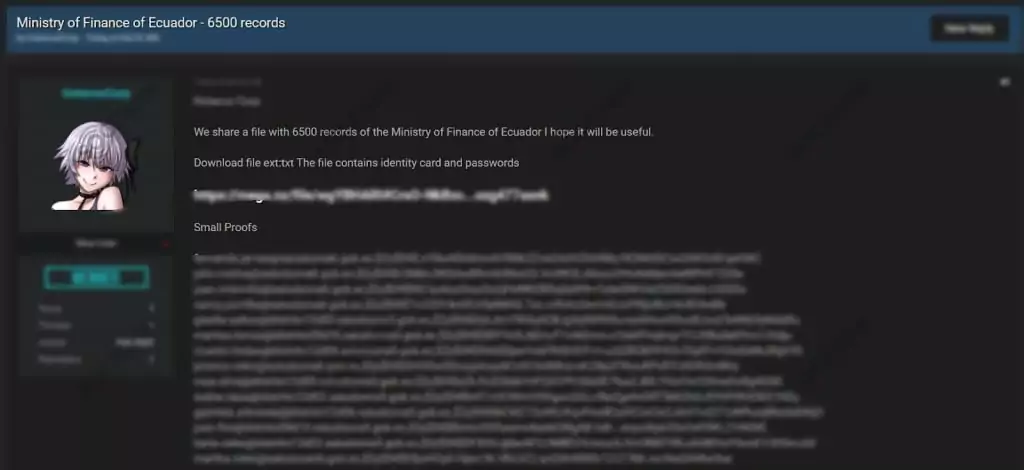
On Feb. 23, 2021, an official database owned by the Ministry of Finance of Ecuador was leaked by the actor group on a dark web forum monitored by SOCRadar. The threat actor group claimed to have ID cards and passwords of 6500 people. The actor, who shared the database in .txt format, also shared a sample with email addresses and hashed passwords. The authenticity of the records has not been verified by any official authority.
Private Diplomatic and Political Materials of EU Countries on Sale
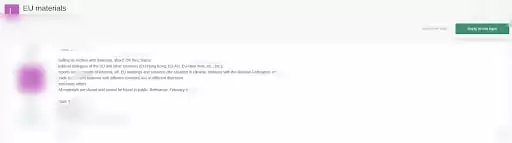
Darknet is not just a place for illegal business where drugs are sold. Serious information that will deeply affect the political strategies of the countries can also be spread on the darknet. On Feb. 25, 2021, the actor put an archive containing political materials for sale assertedly obtained from diplomatic dialogues of the EU and other countries on a dark web forum monitored by SOCRadar. According to the threat actor’s claim, the database contains 700 files from February and the archive consisted of EU meetings and sessions about the situation in Ukraine, relations with the Russian Federation, moreover trade issues with different countries.
Threat Actors Seeking Software Development Capabilities on Dark Web
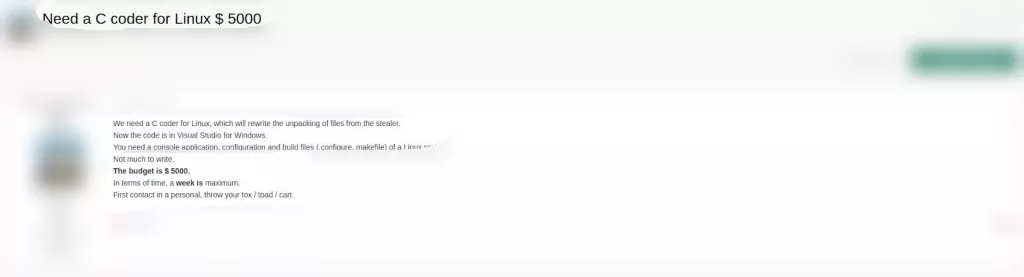
On Feb. 25, 2021, the actor advertised a threat actor job opportunity on a dark web forum monitored by SOCRadar. The actor explained job qualification as C coder for Linux having capability to rewrite an unpacking operation for hacking files and offered a salary of $5000 for the job that would take less than a week. For the past 6 months, SOCRadar Analysts have observed different actors looking for specific software development capabilities to be leveraged for their malicious operations.
37 Million LinkedIn Users’ Profile Information for Sale on a Dark Web Forum
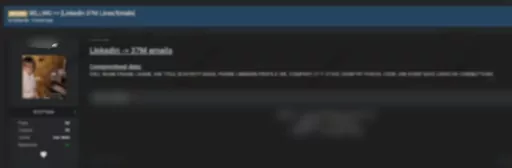
On Feb. 23, 2021, the actor attempted to sell a database allegedly belonging to LinkedIn on a dark web forum monitored by SOCRadar. According to the threat actor claiming to have profile information of 37 million users, the buyer would be able to obtain compromised data containing full name, email, phone number, and hidden LinkedIn data. This kind of information could frequently be used for phishing and business email compromise (BEC) attacks.
Same Threat Actor – Different Companies



On Feb. 25, 2021, the actor attempted to allegedly sell remote access to many organizations through Citrix gateway appliances on a dark web forum monitored by SOCRadar. According to the threat actor, the first victim is a firm with 67.000 employees and a $97 billion revenue. The second victim is an insurance company that has global customers and 73.000 employees with a $79 billion revenue. Another company is engaged in allegedly the sale and production of solar, wind, geothermal and hydro energy. Threat actors selling remote accesses are called initial access brokers who are connected to targeted attackers such as ransomware operators.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.



































