
The Week in Dark Web – 3 October 2022 – Data Leaks and Access Sales
Powered by DarkMirror™
Threat actors sold which companies’ or governments’ data on the dark web in the first week of October? Are there any access sales that attackers can use for potential breaches? Here’s a quick look at The Week in Dark Web.
Find out if your data has been exposed on the deep web.
Database of a Ukrainian Governmental Website is Leaked
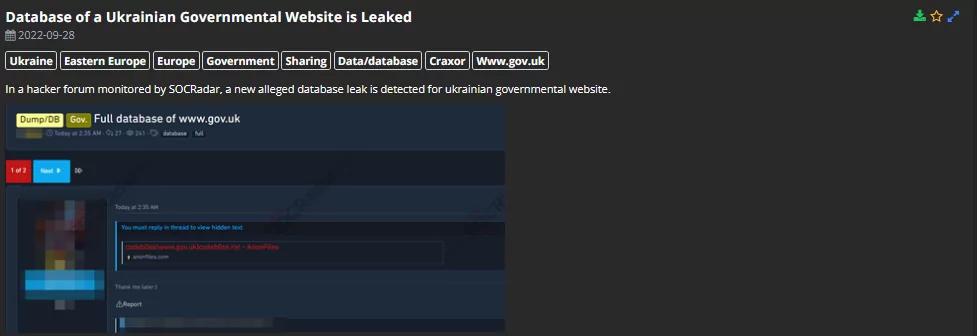
SOCRadar Analysts has found a post on a dark web forum that shares a database claimed to be from a website with a “gov[.]uk” extension. The vendor does not elaborate on the topic further and shares the link as a complete website database.
Unauthorized Access Sale for a Kuwaiti Shop
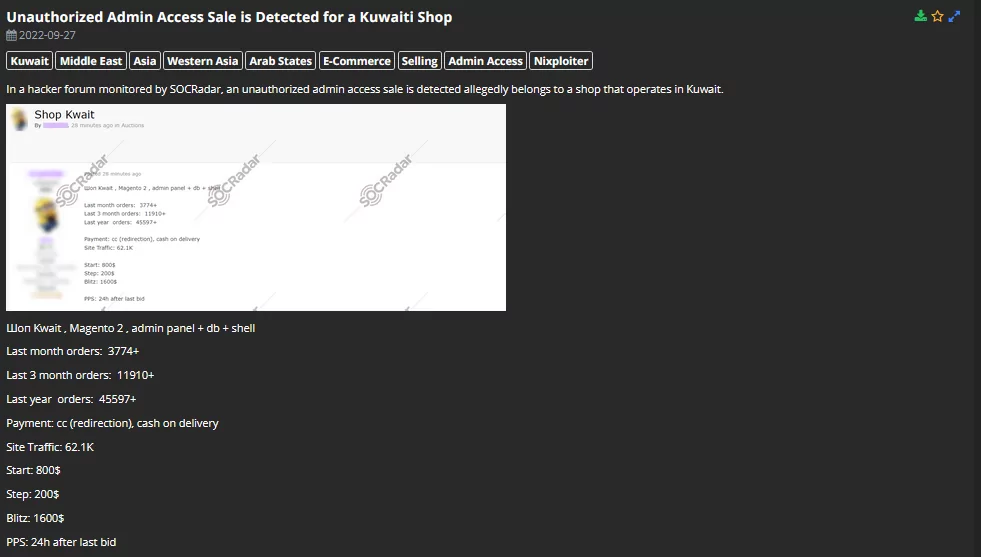
On 27 September, a post for selling an unauthorized admin access sale for a Kuwaiti e-shopping site was detected on the dark web. The vendor explains the access types and attack methods along with the ordering data of the website. The access is auctioned with the given start, step, and blitz amounts.
Database of a Power Company in Belgium Leaked
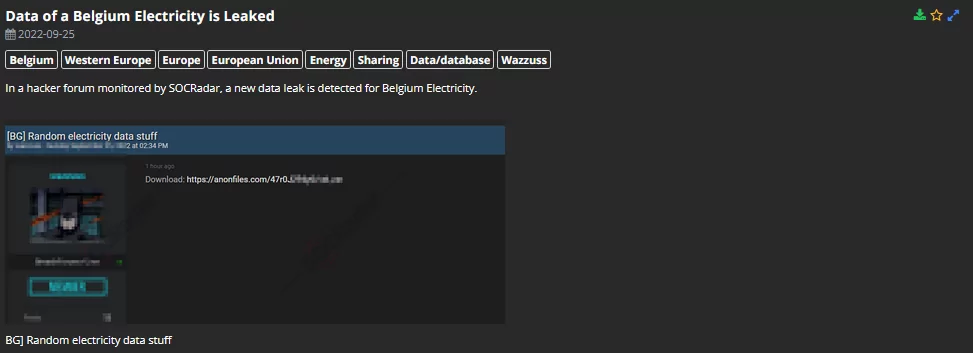
SOCRadar detected a database leak of a Belgian power company on a hacker forum on 25 September 2022. The post’s creator describes the database as “random electricity data stuff” and shares it directly.
Unauthorized Network Access Sale for an Israeli Company
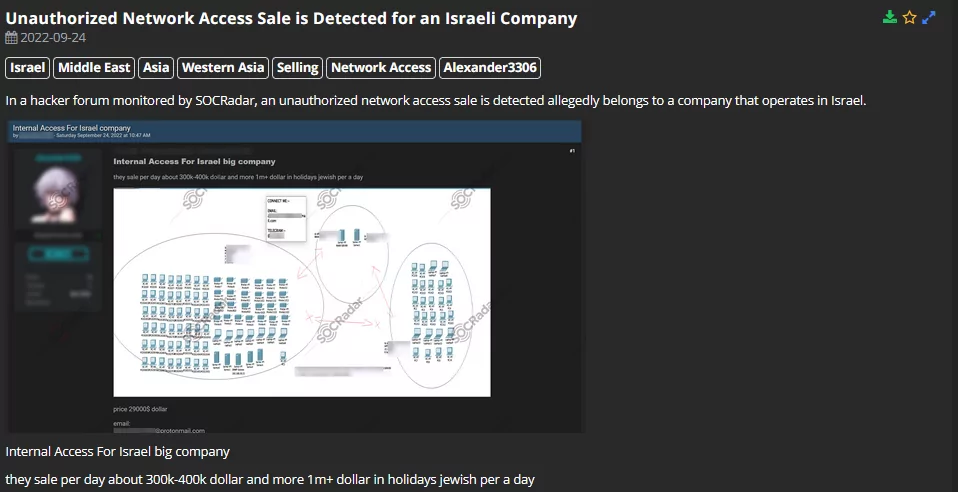
SOCRadar detected an unauthorized network access sale of an Israeli Company on a hacker forum on 24 September 2022. The victim is believed to have 300~400 thousand dollars of daily revenue on regular days, which can go up to a million during the religious holidays in Israel. The price of the access is set as $29.000.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































