
The Week in Dark Web – 30 January 2023 – KillNet Targets Germany!
Powered by DarkMirror™
Former DDoS provider, nowadays a pro-Russian threat actor KillNet continues targeting western organizations. Since Russia’s invasion of Ukraine started, the group added many victims to its list. Last week, multiple German companies also got their share of attacks.
There are other things to mention about what happened on the dark web last week. Here’s a brief summary.
Find out if your data has been exposed on the deep web.
KillNet Targeting Multiple German Organizations
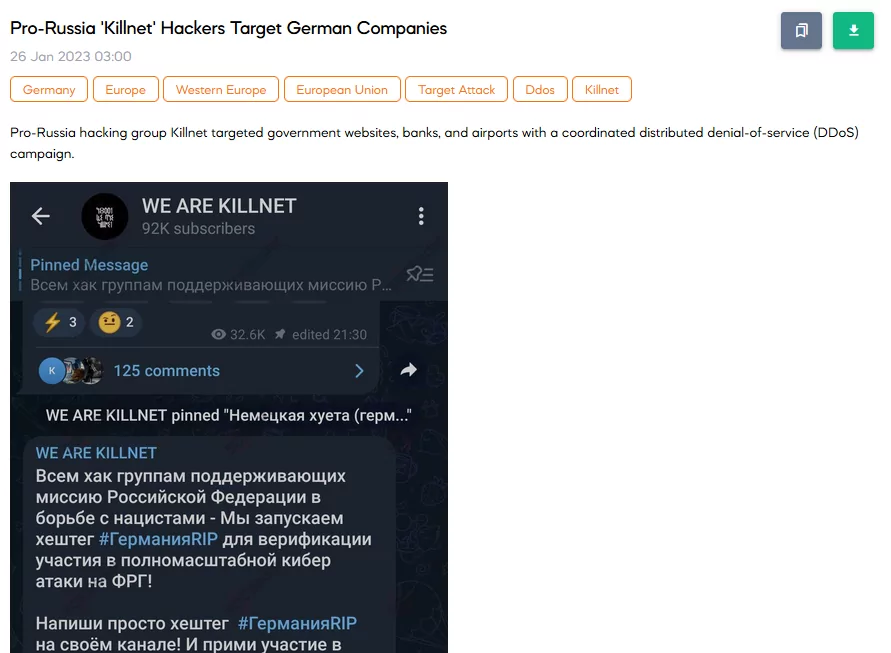
SOCRadar noticed a new post on pro-Russian threat actor Killnet’s Telegram channel. The post targets German organizations, including governmental, financial websites, and major airport domains. Shortly, Killnet stated they started a full-scale cyber attack on Germany to support Russia. They also encouraged any participants who joined their campaign to use the #GermanyRIP hashtag on their posts.
You can read a detailed analysis of Killnet on our blog.
Database of Duolingo for Sale
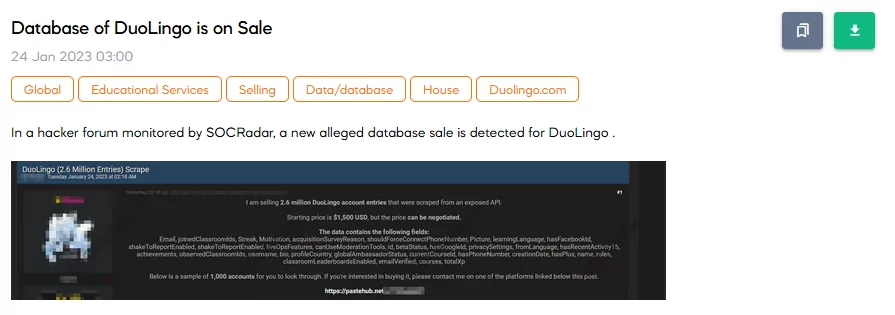
SOCRadar has detected a post that sells a database related to a popular mobile application. According to the threat actor, it is stated that the database is new and obtained from an exposed API. The database contains 2.6M users’ information, and the price for the database is $1500. The database contains mostly information about the application itself, yet still, there is some information about users (mail addresses, names, etc.)
OpenCart Zero Day Exploit is Shared
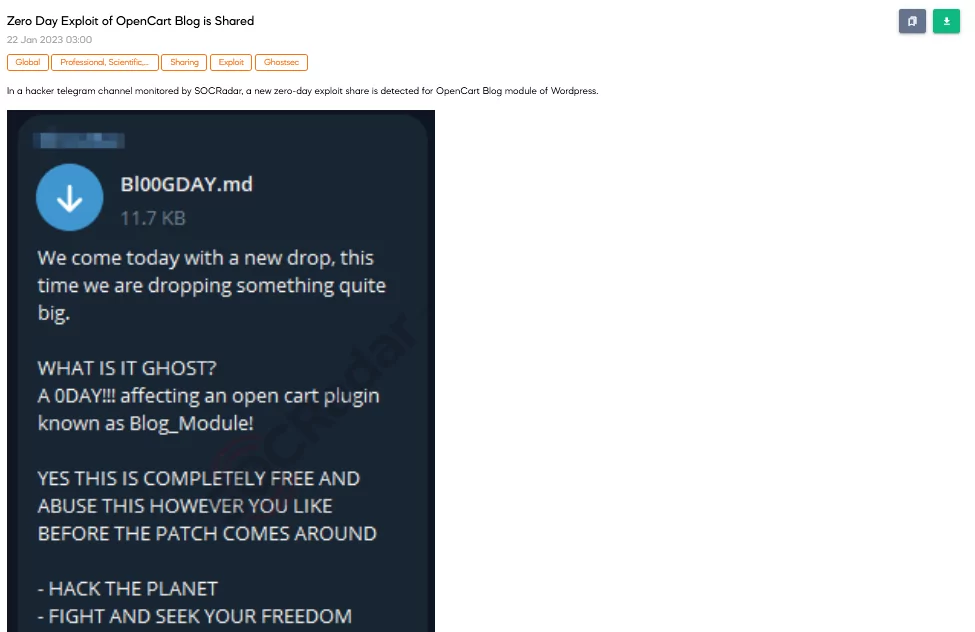
SOCRadar dark web team has detected a new Telegram post that shares information about a zero-day of OpenCart. The shared zero-day exploit is claimed to be about a plugin of OpenCart known as Blog_Module. Then, the followers are encouraged to use this exploit in the later part of the post.
A New DDoS Service is Detected
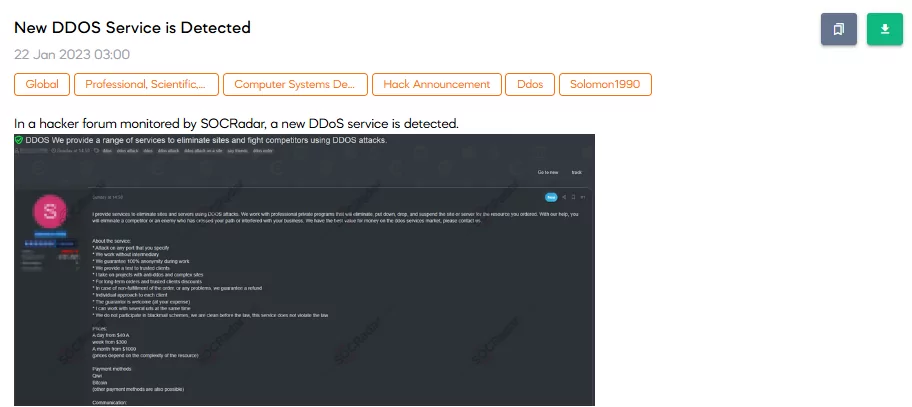
SOCRadar has noticed a post related to selling a new DDoS service. The threat actor shortly summarizes all the capabilities of their services on the post. They share the service price, which is calculated based on the time and difficulty of the target domain. Posts like these are increasing on the dark web, which enables individuals with no or fewer skills to make more complex attacks.
Unauthorized Access Sale for a European Healthcare Company
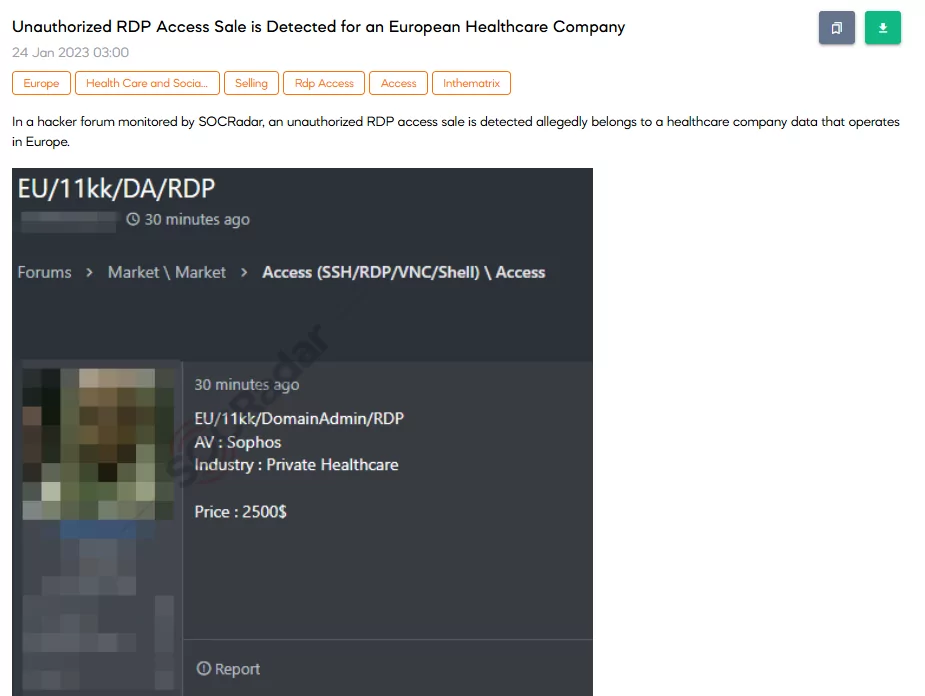
On 24 January, the SOCRadar dark web team detected an unauthorized access sale about a private healthcare company that works in Europe. It is claimed that the company has $ 11 million in revenue and uses Sophos’s antivirus services. The price for the access is $2500.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































