
The Week in Dark Web – 31 January 2022 – Ransomware Attacks and Data Leaks
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. Again, rise of ransomware attacks, some database thefts, and stealing customer data, that took their place on the headlines this week. Click here to read last week’s post.
Find out if your data has been exposed on the deep web.
Unauthorised RDP Access Sale Detected For an Agriculture Company From Denmark
On January 29, a dark web vendor attempted to sell unauthorised RDP access for an agriculture firm from Denmark on a dark web forum monitored by SOCRadar. While the dark web vendor gave any detail about how the access was obtained, stated that the victim agriculture company has a revenue of $5 million.
Database Including Customer Details For Various Countries Put For Sale On The Dark Web
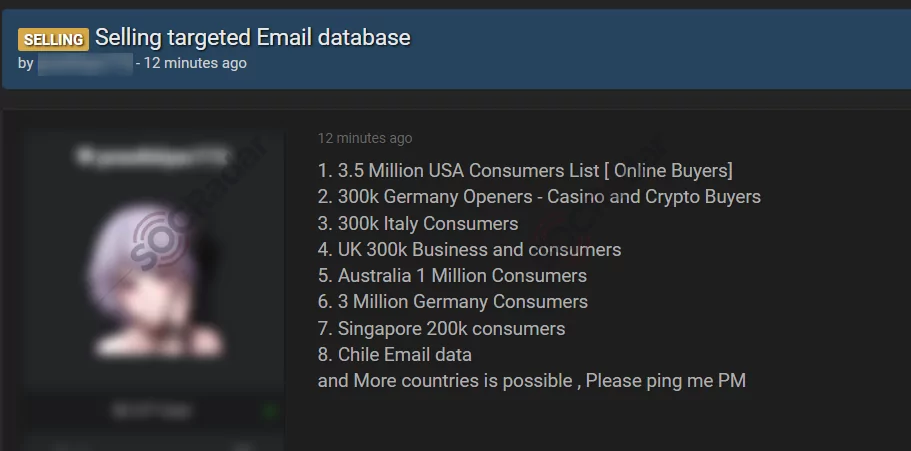
On January 29, a database of emails was put up for sale on the dark web. The database includes email lists of different customer profiles from several countries, such as 300 thousand casino and crypto customers from Germany or 3.5 million consumers from the USA. It is unknown whether the vendor may have obtained these lists in different attacks or may have put them for sale by combining the email lists collected from dark web forums. However, according to SOCRadar analysts, the buyer could perform social engineering attacks using these email lists in the database.
Unauthorised VPN Access For A Law Firm From Mexico Put On Sale

On January 30, a vendor offered to sell unauthorised virtual private network (VPN) access allegedly for a law company from Mexico on an underground forum tracked by SOCRadar. While the dark web vendor did not detail how this access has been seized, it is stated that the victim has more than 300 employees. The vendor also wanted $1000 for the access.
LockBit 2.0 Ransomware Targeting Europe Countries
Ville de Saint-Cloud
London
Germany
Italy
On January 27, a ransomware post allegedly announcing an attack that targeted the French Ministry of Justice was detected in the LockBit 2.0 ransomware gang site monitored by SOCRadar. The notorious group claimed to publish sensitive data belonging to the ministry if their demands not met. However, the French ministry was not the only victim of LockBit 2.0 last week. The ransomware group hits various top businesses from Germany, Italy and The United Kingdom.
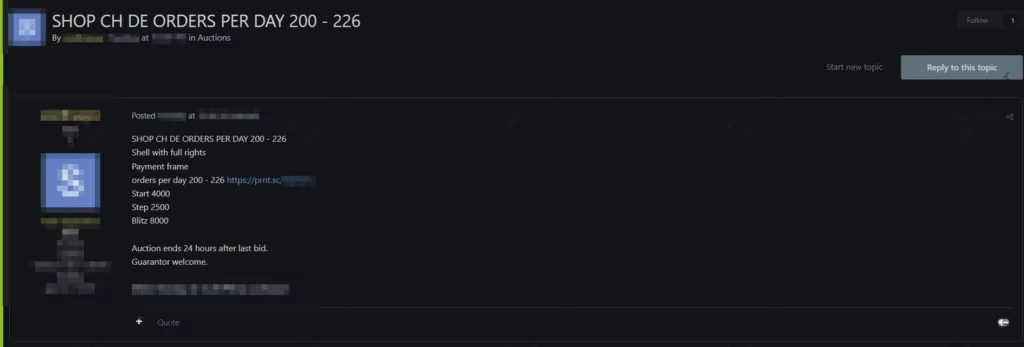
Unauthorised Shell Access For A Swiss E-Commerce Put On Sale

On January 28, a vendor offered to sell unauthorised shell accesses allegedly for a Swiss e-commerce company on a Russian-speaking dark web forum monitored by SOCRadar. The dark web vendor claimed that the shell access includes the access to the payment infrastructure with admin rights. According to the dark web post, the victim shop has more than 200 orders daily.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.



































