
Top 5 Critical Vulnerabilities Behind Ransomware Attacks
Cybercriminals use encrypted ransomware that has become the most common type because it is difficult to crack the encryption and remove the malware. All the stuff you keep on your PC is encrypted by malicious code for ransom. Ransomware encrypts the files as if they were actively encrypted, but actually, they are hidden in a separate file, which waits for a defined set of conditions to be unlocked before they are decrypted.
Once your files are encrypted, the virus will create a tutorial on how to obtain the decryption key that is available to you if you pay the ransom. You will be shown a link to download the required decoder.

There is plenty of money in ransomware and from the beginning of the decade, the industry developed exponentially. Ransomware resulted in damages of $5 billion in 2017, both for ransom fees and costs and for the lack of time to recover from attacks. From 2015 that’s up fifteen times. Just one kind of ransomware software, SamSam, collected $1 million in ranking money in the first quarter of 2018.
Main reasons for current ransomware attacks
Knowing which attack techniques are most commonly used by ransomware groups is very important in order to take security measurements. Even though email phishing was the top attack vector behind ransomware, RDP is far and away the most common initial attack vector nowadays as can be seen in the following figure.
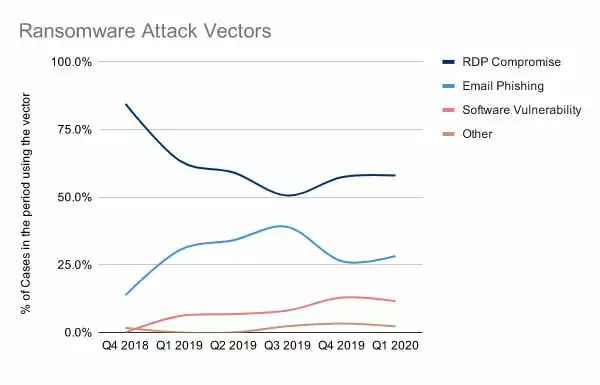
RDP is a formal process for remote system control to IT managers. However, any hackers who have connections to RDP endpoints will use networks to gain territory on an enterprise network and continue to expand their rights and access even further. Organizations can take a variety of actions to lock RDP endpoints, including the security of them with complex passwords and multifactor authentication.
There are an unavoidable range of CVEs for defense teams to look out for these days, but five known vulnerabilities that behind many initial exploitations can be outlined as below for ransomware attacks:
1. Pulse Secure VPN systems affected by CVE-2019-11510
Vuln ID: CVE-2019-11510
CVSS Severity: V3.1: 10.0 CRITICAL – V2.0: 7.5 HIGH
Published: May 08, 2019; 1:29:00 PM -0400
Summary: In Pulse Secure Pulse Connect Secure (PCS) 8.2 before 8.2R12.1, 8.3 before 8.3R7.1, and 9.0 before 9.0R3.4, an unauthenticated remote attacker can send a specially crafted URI to perform an arbitrary file reading vulnerability.
Confidentiality Impact: Partial (There is considerable informational disclosure).
Integrity Impact: Partial (Modification of some system files or information is possible, but the attacker does not have control over what can be modified, or the scope of what the attacker can affect is limited).
Availability Impact: Partial (There is reduced performance or interruptions in resource availability).
Affected Product(s): Pulse Connect Secure (PCS) and Pulse Policy Secure (PPS)
Abused by Ransomware Groups: REvil/Sodinokibi and the Black Kingdom
This vulnerability could cause unauthenticated adversaries to access vulnerable endpoints and gather usernames and plaintext password information remotely. Although in April 2019, Pulse Secure released a vulnerability update, it was paid further attention after the August 2019 release of a Proof of Concept (POC) for the bug. Shortly after the release of POC, rumors started to emerge that attackers attempted to exploit the vulnerability.
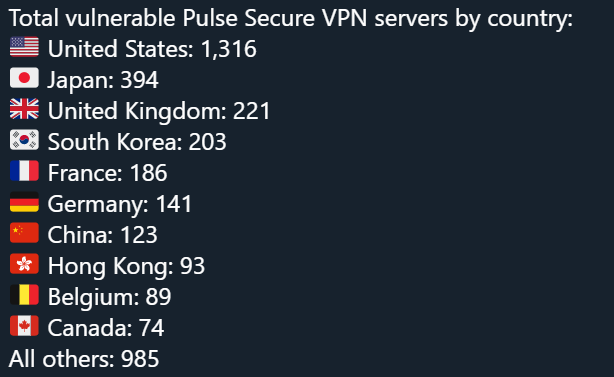
According to the Bad Packets Report published at the beginning of 2020, total vulnerable Pulse Secure VPN servers by country as follow;
2. Microsoft SharePoint Servers affected by CVE-2019-0604
Vuln ID: CVE-2019-0604
CVSS Severity: V3.1: 9.8 CRITICAL – V2.0: 7.5 HIGH
Published: March 05, 2019; 6:29:00 PM -0500
Summary: A remote code execution vulnerability exists in Microsoft SharePoint when the software fails to check the source markup of an application package, aka ‘Microsoft SharePoint Remote Code Execution Vulnerability’. This CVE ID is unique from CVE-2019-0594.
Confidentiality Impact: Partial (There is considerable informational disclosure).
Integrity Impact: Partial (Modification of some system files or information is possible, but the attacker does not have control over what can be modified, or the scope of what the attacker can affect is limited).
Availability Impact: Partial (There is reduced performance or interruptions in resource availability).
Affected Product(s): Microsoft SharePoint Enterprise Server 2016, Microsoft SharePoint Foundation 2010 Service Pack 2, Microsoft SharePoint Foundation 2013 Service Pack 1, Microsoft SharePoint Server 2010 Service Pack 2, Microsoft SharePoint Server 2013 Service Pack 1, Microsoft SharePoint Server 2019.
Vulnerability Type(s): Execute code
A remote code execution vulnerability exists in Microsoft SharePoint when the software fails to check the source markup of an application package. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the SharePoint application pool and the SharePoint server farm account.
Exploitation of this vulnerability requires that a user uploads a specially crafted SharePoint application package to an affected version of SharePoint.
The security update addresses the vulnerability by correcting how SharePoint checks the source markup of application packages.
Many organizations were affected by this vulnerability. For instance, the Canadian Centre for Cyber Security released an alert about ongoing attacks exploiting CVE-2019-0604 to deliver the China Chopper web shell on April 23 and advised administrators to implement all the patches made available by Microsoft.
3. Microsoft Exchange Servers affected by CVE-2020-068
Vuln ID: CVE-2020-0688
CVSS Severity: V3.1: 8.8 HIGH – V2.0: 9.0 HIGH
Published: February 11, 2020; 5:15:15 PM -0500
Summary: A remote code execution vulnerability exists in Microsoft Exchange software when the software fails to properly handle objects in memory, aka ‘Microsoft Exchange Memory Corruption Vulnerability’.
Confidentiality Impact: Partial (There is considerable informational disclosure).
Integrity Impact: Partial (Modification of some system files or information is possible).
Availability Impact: Partial (There is reduced performance or interruptions in resource availability).
Affected Product(s): All versions of the Microsoft Exchange server.
A remote code execution vulnerability exists in Microsoft SharePoint when the software fails to check the source markup of an application package. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the SharePoint application pool and the SharePoint server farm account.
The vulnerability of CVE-2020-0688 affects the component of the Exchange Control Panel (ECP). This flaw affects all Exchange Server deployments because up to the latest fix, the validation key and algorithm of all Exchange Servers were the same on the web.config register.
Using static keys could allow an authenticated attacker with any privilege level to send a specially crafted request to a vulnerable ECP and gain SYSTEM level arbitrary code execution.
4. Exim Mail Server Remote Code Execution Vulnerability affected by CVE-2019-10149

Vuln ID: CVE-2019-10149
CVSS Severity: V3.1: 9.8 CRITICAL – V2.0: 7.5 HIGH
Published: June 05, 2019; 10:29:11 AM -0400
Summary: A flaw was found in Exim versions 4.87 to 4.91 (inclusive). Improper validation of recipient address in deliver_message() function in /src/deliver.c may lead to remote command execution.
Confidentiality Impact: Partial (There is considerable informational disclosure).
Integrity Impact: Partial (Modification of some system files or information is possible, but the attacker does not have control over what can be modified, or the scope of what the attacker can affect is limited).
Availability Impact: Partial (There is reduced performance or interruptions in resource availability).
Affected Product(s): Exim 4.87, Exim 4.88, Exim 4.89, Exim 4.90, Exim 4.91, Exim 4.92.
Vulnerability Type(s): Local Privilege Escalation
Exim is wide-ranging. The search results of Shodan indicate over 4.1 million Exim systems operating with vulnerable versions (4.87-4.91), while the current patched update (4.92) occurs for 475.591 systems. In other words, almost 90% of Exim’s devices are vulnerable to local usage and possibly remote configuration-based use.
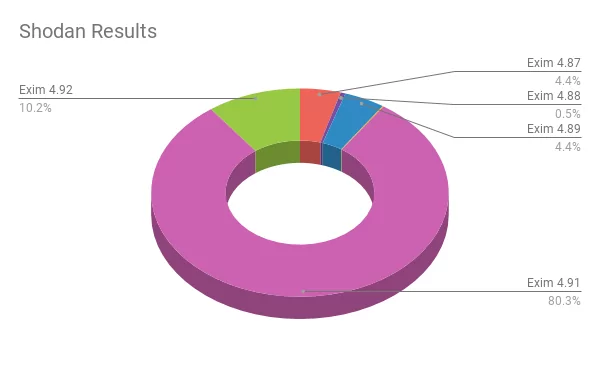
Total results by version number
- Exim 4.87: 206,024
- Exim 4.88: 24,608
- Exim 4.89: 206,571
- Exim 4.90: 5,480
- Exim 4.91: 3,738,863
- Exim 4.92: 475,591
5. Citrix ADC systems affected by CVE-2019-19781

Vuln ID: CVE-2019-19781
CVSS Severity: V3.1: 9.8 CRITICAL – V2.0: 7.5 HIGH
Published: December 27, 2019; 9:15:12 AM -0500
Summary: An issue was discovered in Citrix Application Delivery Controller (ADC) and Gateway 10.5, 11.1, 12.0, 12.1, and 13.0. They allow Directory Traversal.
Confidentiality Impact: Partial (There is considerable informational disclosure).
Integrity Impact: Partial (Modification of some system files or information is possible, but the attacker does not have control over what can be modified, or the scope of what the attacker can affect is limited).
Availability Impact: Partial (There is reduced performance or interruptions in resource availability).
Affected Product(s): All supported versions of Citrix ADC and Citrix Gateway products.
Vulnerability Type(s): Remote code execution
According to Bad Packets, vulnerable hosts were found in 122 countries around the world.
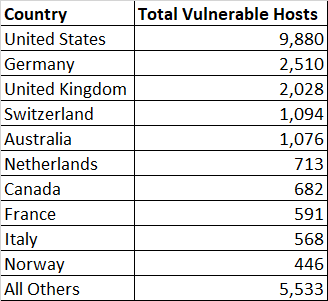
Over 25,000 Citrix (Netscaler) endpoints were vulnerable to CVE-2019-19781. This flaw affected;
- Military, federal, state, and city government agencies,
- Public universities and schools,
- Hospitals and healthcare providers,
- Electric utilities and cooperatives,
- Major financial and banking institutions,
- Numerous Fortune 500 companies.
How to prevent ransomware attacks with the help of SOCRadar
Threat actors are closely monitoring vulnerability trends as much as your public-facing services and technology to find the easy way in. To prevent them disrupt your business, get alerted whenever there’s a new critical vulnerability or exploit for the pre-defined product components and technologies associated with your auto-discovered digital footprint. See which vulnerabilities are being leveraged by threat actors. Get actionable insights and context on potentially vulnerable technologies to speed up the assessment and verification processes.
SOCRadar notifies and informs you immediately when;
- Critical ports are opened such as RDP port,
- There is an critical vulnerability for your attack surface,
- Any sensitive information or data available about your organization on the dark web.
SOCRadar vulnerability intelligence;
- Tailored for you: Select products and technologies you’d like to monitor.
- Twitter CVE trends: See the worldwide vulnerability trends by monitoring millions of tweets.
- Instant alerting; Rapid data collection, structuring, and analysis to notify on-time.
- Filter and search: Find vulnerability information by filtering based on keyword, CVSS score, or report time.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































