
Top 5 Paste Sites Used by Threat Actors
Paste sites are increasingly being utilized as hubs for disseminating code snippets, configuration files, and assorted textual data. While they offer valuable resources for developers and researchers, they also pose a threat when sensitive information is uploaded either inadvertently or maliciously.
They are often used to operate without the need for registration or authentication, offering users swift and uncomplicated access. Therefore, admins typically do not actively monitor or remove content from these sites, fostering an environment conducive to illicit activities.
Moreover, while most paste sites are situated on the clear web, some can also be found on encrypted networks like .onion links. Given that these sites afford users a higher degree of anonymity when sharing pastes.
Frequently, these paste sites morph into goldmines for attackers seeking sensitive passwords, proprietary data, or exploitable code fragments. Hence, organizations must vigilantly monitor these platforms to detect and address potential data breaches proactively.
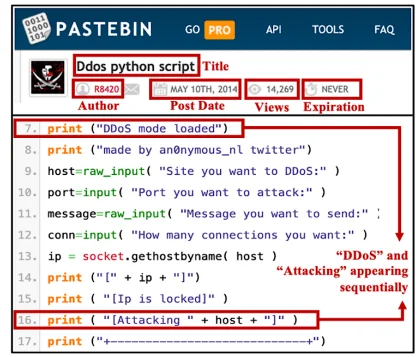
Malicious scripts habited on Pastebin (Identifying and Categorizing Malicious Content on Paste Sites: A Neural Topic Modeling Approach)
However, the danger is not limited to this, Cybercriminals are progressively leveraging paste sites to disseminate malicious content aimed at cyber-attacks and data breaches.
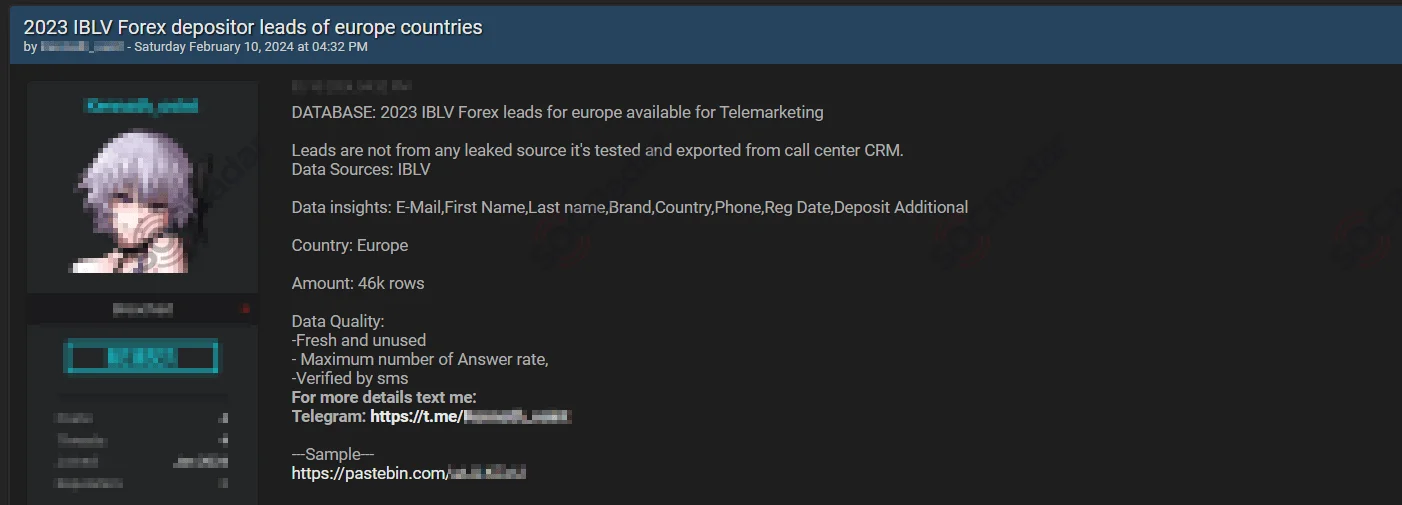
Threat actor sharing the sample data on paste site
Now that we understand this huge threat landscape, let’s look at the most popular paste sites, their content, and proactive security actions that can be taken.
#1 Pastebin.com
A pastebin or text storage platform is an online service designed for hosting various forms of plain text content. The inaugural instance of such a platform is the well-known pastebin.com.
Although Pastebin.com emerged as a legitimate service, nowadays Pastebin.com is renowned for being a prominent source of .onion links leading to the dark web and data leaks.
Pastebin.com’s main page
Pastebin.com, established on September 3, 2002 by Paul Dixon, serves as a platform for storing text content. The site offers syntax highlighting for various programming and markup languages, along with view counters for pastes and user profiles. While users can submit pastes as guests without registration, having an account enables paste management.
In April 2020, Pastebin.com removed its built-in search feature and imposed restrictions on its web scraping API, including for paid lifetime subscribers of Pastebin Pro. Additionally, as a spam prevention measure, pastes from non-logged-in users were concealed from the list of recent pastes visible in the site’s sidebar.
It is also frequently used by threat actors for anonymity, as private links can be created via paste exposure and accessibility to the page can be restricted based on time. There are also country specific versions of Pastebin; the most known ones are Pastebin.pl and .fr.
All sorts of content listed on the paste site, including malicious scripts, piracy, and legitimate usage
#2 JustPaste.it
JustPaste.it is an online platform designed for sharing text and images. It allows users to publish content without creating an account and offers features such as preserving text formatting, embedding images and YouTube videos, generating short URLs for sharing, downloading notes as PDF files, setting expiry terms, and implementing Captcha verification. Registered users can create private notes and subscribe to specific topics, while premium users have access to advanced features like encryption and content change history tracking.
JustPaste.it’s main page
Justpaste.it is a useful tool and is widely used to convert texts into HTML format. Of course, it has also been frequently preferred by threat actors, who are inevitable customers of paste sites.
#3 dpaste
dpaste.org is a versatile platform powered by the dpaste open-source Pastebin application. It enables users to effortlessly share code snippets and text passages while offering transparency through its open-source nature. Users can access the source code, contribute, or provide feedback via GitHub.
dpaste’s main page
With dpaste.org, users benefit from an intuitive API for pasting snippets directly from their shell or editor, comprehensive documentation, and available plugins. Notably, users have full control over their content, with the ability to delete snippets and address legal concerns through the platform’s legal team.
In terms of privacy, dpaste.org prioritizes user security by abstaining from tracking behavior and only collecting IP addresses for diagnosing website issues. While cookies may enhance user experience, blocking them does not affect site functionality.
Also Mozilla Firefox has a Pastebin project that is based on dpaste.
#4 PrivateBin & ZeroBin
ZeroBin developed by Sébastien Sauvage, is a simple open-source Pastebin project with a .onion link as well. ZeroBin allegedly has zero knowledge of hosted data and data is encrypted/decrypted in the browser using 256 bits AES but it is no longer maintained.
ZeroBin’s main page
On the other hand, PrivateBin is a more updated open-source Pastebin that ensures data privacy through client-side encryption. Derived from ZeroBin, it offers enhanced features and easy extension. Admins have no access to paste content, and users can set passwords for added security. However, trust in server admins and HTTPS usage is vital. It provides various features like discussions, expiration times, file uploads, and customizable templates, prioritizing user privacy while offering convenient text storage and sharing.
PrivateBin’s main page
#5 GitHub Gist
A surprising one is GitHub Gist. Gist offers a straightforward method for sharing code snippets and pastes with others. Each gist functions as a git repository, ensuring automatic versioning, forking capabilities, and usability as a git repository. However, there is a growing trend among threat actors to exploit GitHub for nefarious activities, employing innovative tactics such as misusing secret Gists and delivering malicious commands through git commit messages.
A PoC shared on hacker forum with gist.github link
In addition to these instances, GitHub has been utilized for numerous malicious activities and has recently been implicated as a host platform for a significant data breach, notably the I-SOON data leaks.
Conclusion
Many paste platforms are quite clear about their defined boundaries for acceptable use of the service, which nearly all explicitly exclude email lists, login credentials, password lists, and personal information. Nevertheless, these types of data are commonly posted on numerous paste sites each day along with many other malicious data. Therefore, the surveillance of paste sites has emerged as a crucial aspect of safeguarding companies and brands against potential cyber and digital risks.
SOCRadar: Monitoring Every Layer of the Web
SOCRadar offers comprehensive monitoring solutions that cover every layer of the web, from the surface to the deep and dark. Our vigilant surveillance extends across widely accessible websites, deep web platforms, and concealed realms of the dark web. With SOCRadar, your organization can stay ahead of cyber threats by detecting and addressing risks across all layers of the digital landscape.
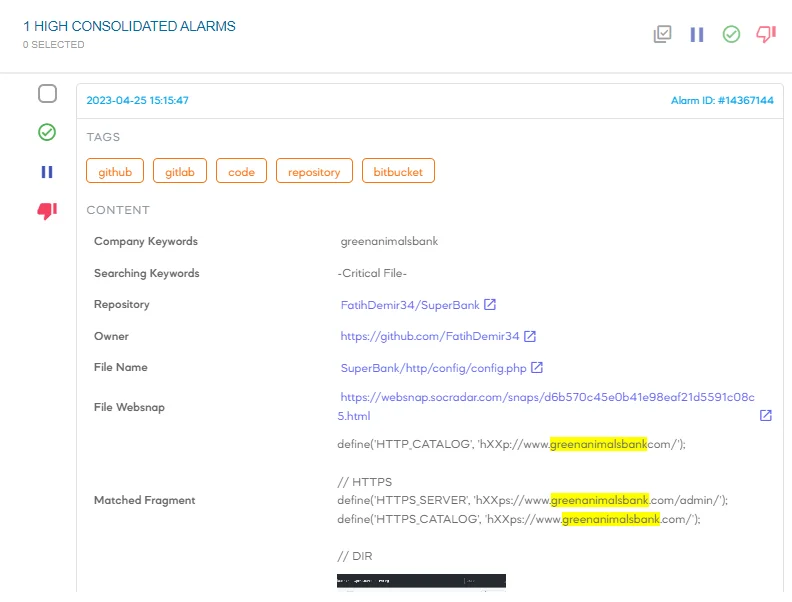
SOCRadar sends timely alerts for critical findings indexed on any layer of the web
The Surface Web Monitoring feature provided by SOCRadar delivers an essential level of security. It actively examines websites and online platforms indexed by search engines like GitHub, acting as a vigilant watchtower. Beyond simply detecting source code leakages, it reveals a broad spectrum of vulnerabilities and exposures that frequently evade conventional security protocols.




































