
Top Threat Intelligence Use Cases for the Finance Sector-II
Security departments in the financial industry are facing a daunting mission. They have to defend the company from an immense amount of indiscriminate attacks, which is the price of simply being an online enterprise. At the same time, they still have to ensure that their planned business activities are as robust as possible. Security experts in the financial industry are trying to reclaim the effort to collect threat intelligence to detect and prevent threats more efficiently than ever before while defending the integrity of their company and corporate life. However, it can be a struggle to decide which solution to choose. A comparison of threat intelligence products can help these professionals by providing the most reliable and productive way to manage their time and money.

What are the cyber threat intelligence use-cases for the finance industry?
The financial services market is one of the most focused on organized crimes, which tries to pillage confidential details that are monetized rapidly.
One of the biggest cyber challenges in the financial services industry is the theft of personally identifiable information (PII) by mostly organized crime groups, who infiltrate networks with the aim of rapidly monetizing the data that they steal. They threaten not only business networks, but also individuals by going after their identities, usernames, and passwords for account takeovers.
Third-party attacks
Third-party attacks are drastically changing the threat landscape for organizations. Attackers can infiltrate the infrastructure of a third party who has access to the ultimate target.

After a suspected Shiny Hunters malicious hacker leaked 7 million customer information to an illegal website, the digital banking platform Dave.com exposes a security breach. Dave reported the incident to the police and launched an official investigation into the offense. The business already suspects that attackers want to sell Dave’s customer data.
The threat intelligence targeting diverse sectors and third parties must be included in a successful third-party risk program. The vulnerability data will then be used to model hacker workflows for identified attack scenarios. The threat information is comprehensive. This review helps to recognize measures for security that can prevent and avoid these attacks both in business and across portfolios critical of third parties.
SSL monitoring
SSL certificates provide confidentially for connections over the internet. They are commonly used for connecting to websites but they may be used to secure any communication over the internet. They are also used for validating software. Maintaining an SSL certificate has many aspects. They expire, they can be misconfigured, or they may be compromised. Any of these issues can create serious problems for businesses.

Millions of British mobile phones went offline due to an expired Ericsson software certificate in 2018. The downtime was caused by European telecom carriers using Ericsson’s software, whose certificate expired. Softbank, a bank in Japan, was also impacted by the same issue.
SSL monitoring can help organizations to stay ahead of malicious cyber-attacks and business disruptions.
Phishing detection
Phishing is an attempt to trick users into revealing sensitive information such as PII, account credentials, or credit card details.

The finance industry is the top target of phishing attacks by many measures. Security researchers detected a total of 19,800 unique phishing URLs spoofing Bank of America in 2019. One of the phishing links leads to a sophisticated Bank of America website that would not be expected by the ordinary person. Unlike legitimate company websites, phishing pages allow random text formats, including email addresses and passwords, A typical person couldn’t spot this kind of attacks.
Fast phishing detection is very important for financial organizations to prevent fraud. CTI solutions can alert organizations to newly created phishing domains or subdomains within hours allowing them to take necessary precautions.
Zero-day vulnerability detection
A zero-day vulnerability is a cyber-security bug known to the software supplier but not patched by the update.

Many Asian and African banks were attacked using a zero-day vulnerability in the InPage text editor.
The zero-day potential of accused private corporations’ clients is gradually commoditized by the number of zero-days found in the wild. The number of zero-days used by organizations suspected or believe to be clients of private corporations who are offering aggressive cyber services has risen dramatically. Threat intelligence platforms can alert organizations to zero-day vulnerabilities as soon as they are known.
Domain monitoring
In April 2013, the Regions Bank in America, which has more than 1700 branches and 2400 ATMs forgot to renew its main domain. Customers have been unable to access the main bank website for their transactions. The bank had to issue an apology to the public while its website remained inaccessible for a week.

Cyber threat intelligence platforms can monitor WHOIS records for expiration dates or important changes and can alert the organizations immediately.
DDoS attacks
In 2014, a group of hacktivists known as the European Cyber Army organized a Distributed-Denial-of-Service attack targeting Bank of America and JPMorgan Chase. The attacks used an old SQL injection vulnerability to install “backdoors” that ran traffic generating code.

In 2020, Akamai reported that an unidentified European bank was the victim of a DDoS attack, which had the largest ever packet per second (PPS) recorded on their platform. The attack produced 809 million packets per second (Mpps)—a new high for PPS-oriented attacks and well over twice as large as the previous Akamai recorded the attack. The “huge rise” in the amount of source IP addresses detected also renders this DDoS attack special.
CTI can provide preemptive protection against DDoS attacks by providing real-time monitoring of botnets and their activities.
How threat intelligence can help the finance industry?
The finance industry should give cyber threat intelligence (CTI) a better view of their market challenges. CTI offers actionable intelligence that can help executives make well-grounded strategic decisions. CTI monitors the public internet, deep web, and dark web for sensitive data exposure and imminent cyber-attacks.
In a nutshell, cyber threat intelligence can help the finance sector as follows;
- CTI lets organizations rapidly identify digital risks and concentrate their resources and energy where it’s most required, thus discarding others that are unimportant. Alert fatigue and SOC are the weakest possible choice for the financial sector. The rapid denial of false-positive warnings, which may otherwise waste thousands of analysts’ hours in one year, is one of the main roles of SOC analyst threat-intelligence.
- CTI improves vulnerability management by allowing SOC teams to prioritize tasks.
- Threat intelligence assists security leaders in determining whom they need to recruit, what security technology to procure, and where to spend their resources to reduce cyber risk.
SOCRadar helps SOC teams by providing unified threat intelligence solutions
SOCRadar provides the actionable and timely intelligence context you need to support financial services with external attack surface management, digital risk protection, and threat intelligence capabilities modules.
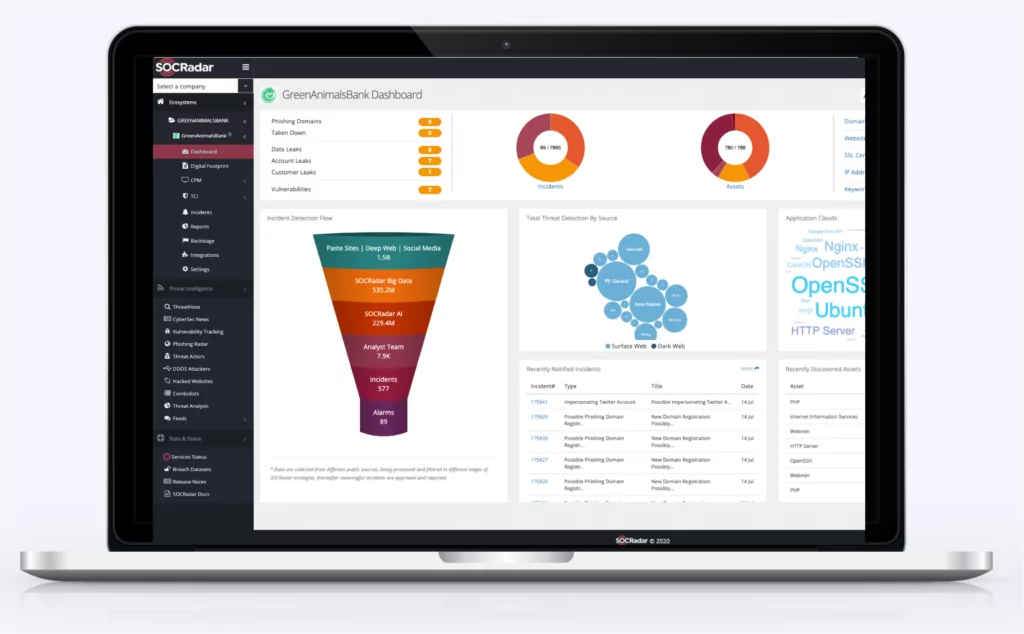
SOCRadar Cyber Threat Intelligence provides actionable insights into future cybersecurity threats with a big data-powered threat investigation module to assist in searching deeper context, real-time threat investigation, and analysis.
SOCRadar Brand Protection builds on industry-leading instant phishing domain identification, credit card monitoring, customers’ PII protecting, and compromised credential detection technologies by aggregating and correlating massive data points into actionable intelligence alerts.
SOCRadar Attack Surface Management provides insight and visibility into these assets to discover and monitor everything related to your organization on the Internet to bring the enormous scale of your attack surface into focus.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.

































