
TorNet Backdoor: A Stealthy Cyber Threat Targeting Poland and Beyond
Put in peril by financial motives, an actor described as a financial threat actor has been conducting an ongoing malicious campaign against users in Poland and Germany since at least July 2024. The objective of these attacks is gleaned from the language of the phishing messages used in the operations.

TorNet backdoor targets Poland and Germany (AI illustration)
How Does TorNet Backdoor Operate?
The TorNet Backdoor is an advanced breed of malware that uses the Tor network to operate undetected, and that poses a grave threat to people and organizations alike.
TorNet Backdoor is notoriously hard to track down and identify, primarily due to it using the Tor network for anonymity. Its malware usually comes in the form of phishing emails where people are tricked into either clicking on links or downloading files from compromised websites. Once executed, the backdoor connects to Tor network, establishing communication with command and control servers while ensuring communication to be untraceable and encrypted.
Cybercriminals can carry out a wide variety of actions remotely, such as stealing sensitive information, gaining control over the hacked device, or even deploying additional malware. The biggest threat this malware poses to society is the fact that it renders traditional security measures useless by hiding your network activity behind encrypted Tor connections.
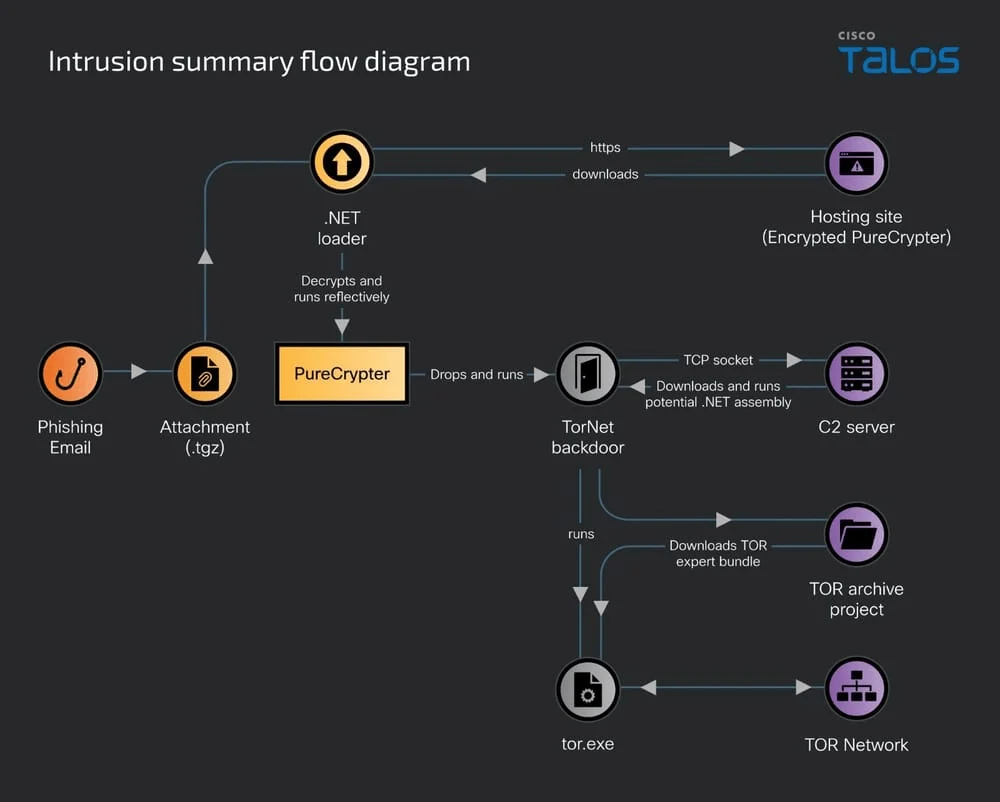
Scheme taken from the Cisco Talos Blog
It’s almost deduced that protecting against TorNet Backdoor requires an extensive cybersecurity plan. These include educating personnel to identify dangers such as phishing, using advanced email phishing filters, examining network traffic for unusual Tor connection patterns, securing endpoints for unusual activity, and deploying constant patch updates.
The Campaign
The initial infection vector is a fraudulent email, which initiates the intrusions. The actor is sending phony order receipts and money transfer confirmations, respectively, in an attempt to impersonate financial institutions and manufacturing and logistics companies. The fraudulent emails are primarily composed in Polish and German, suggesting that the actor’s intention is to primarily target users in those countries. Additionally, we discovered a few fraudulent email samples from the same campaign that were written in English. Based on the filenames of the email attachments and the themes of the fraudulent emails, we have a medium level of confidence that the actor is financially motivated.
The phishing email contains attachments with the file extension “.tgz,” which suggests that the actor has compressed the TAR archive of the malicious attachment file using GZIP to conceal the actual malicious content of the attachment and elude email detections.
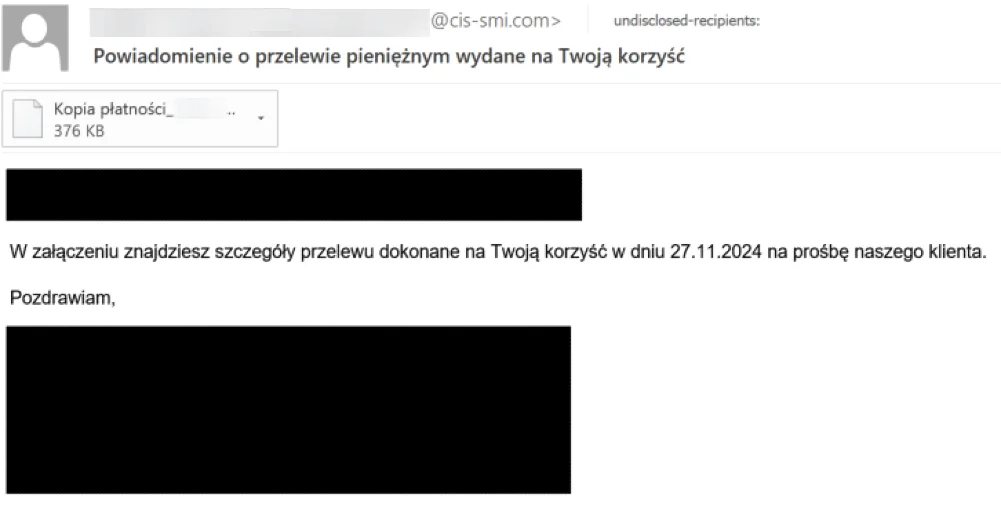
Sample phishing email in Polish.
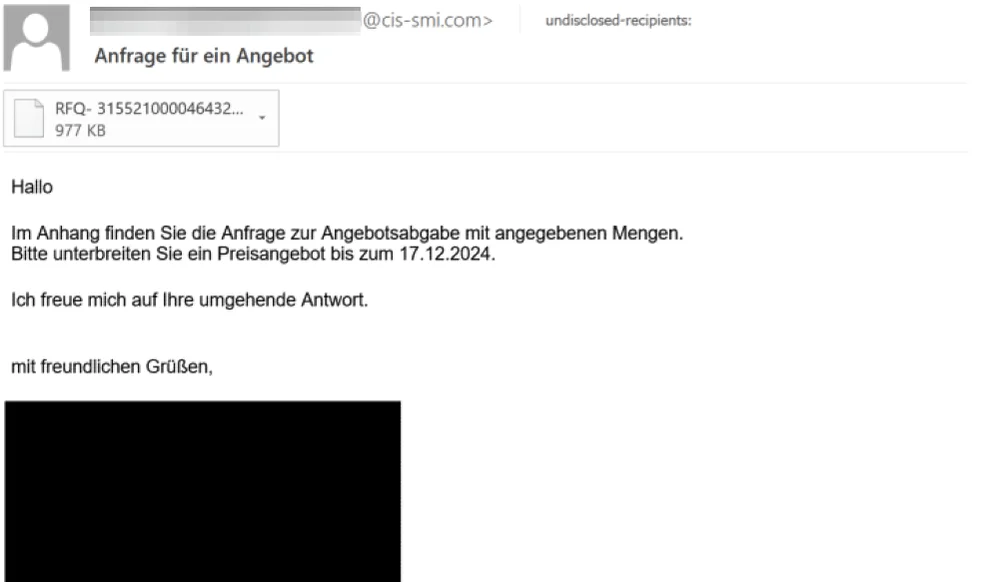
Sample phishing email in German.
Mitigation Strategies to Protect Against TorNet Backdoor
To effectively counter the TorNet Backdoor, organizations and individuals must implement proactive mitigation measures. These strategies include:
- Employee Education – Ensuring employees are trained to recognize common phishing attempts and remain cautious when receiving unsolicited emails, especially from unknown sources.
- Advanced Email Security Solutions – Deploying email filters that can detect malicious attachments or links, minimizing the risk of email-based attacks.
- Network Traffic Analysis – Continuously monitoring and analyzing network traffic to identify any unusual activity, especially communication with the Tor network, which may indicate a breach.
- Endpoint Protection – Installing behavioral detection systems and advanced threat protection to identify anomalies and potential signs of malware on endpoints.
- Regular Updates & Patch Management – Keeping software and operating systems up to date to ensure known vulnerabilities are patched and reduce the likelihood of exploitation.
Additionally, organizations can benefit from powerful cybersecurity services like SOCRadar XTI. With its Digital Risk Protection, Attack Surface Management, and Cyber Threat Intelligence modules, SOCRadar helps manage and reduce the threat profile of your organization, ensuring timely countermeasures against emerging risks.
Conclusion
Organizations and individuals in Poland and Germany are the primary targets of the TorNet Backdoor, but its tactics could potentially extend worldwide. The perpetrator of these assaults has financial motives, and it is very difficult to detect and mitigate them since they use the Tor network for anonymity. Training staff, implementing cutting-edge security measures, and keeping a close eye on things are all necessary to thwart this backdoor. Organizations can lessen their vulnerability to malicious software campaigns like TorNet Backdoor and other complex cyber threats by applying these control measures.
Indicators of Compromise
Below are the Indicators of Compromise (IoCs) related to the TorNet backdoor campaign, as listed by Cisco Talos.
- 3b4e709768d7cd0cb895de74267f45a6ef6565ebed445393878f17ae02a983e3
- 9d33726fc1d39fdc0426c70ed0cfb515e15f50d39c46d8ff38025b4faf8811dc
- 75d2d368d735fca2bad0155510cb4a927f7f246ea72299395990027264056521
- 84570dac910557d0d8217db746c9a8fd4a27cd3db89135731c7f3584b37df533
- 7ce9af599857827317a444c5a63a08929ec97765bc2624076f4834f323a41da2
- e9ab4772ba6de2db9add3d4bbd3ce0f2dd899f16399b57fd2a539769e6ee973a
- 2f9c2e0bef460a7623954d65f10e6e5993c01d25e6f2905a5dc911639ca2ea75
- dc513e35a6d96933e7af2b300782a32131d31445a6d1e2bbca9604128c92e7c6
- 57543fd3673c9595a73c836b153faf68e23938662c5a4b6675205734b688ae95
- 898d0451bd52c466d2284091be928f8ec1ced2184b205d903a04a747e67763ea
- 53e7b3b72695a1eaea7146ec3cbd05d0ce2a1eba87f035ae07849feb4f59ec63
- bff0ec65af8b2bb37fcc5202f823b5877ebdcc8efbd32e08f309cbcb4dc2570c
- 6774a822d9c66951be95341d50c1f876a9373fefef52f68f29eaae4efc621817
- c32d97fb9a1681a7bea3f417abde0264a2332221e317c8543e337baac9307c67
- 075737b17ba72aed5f45d227bf91dd5744914308e1468717a8f3100a0cca8156
- a85423a1a37f604e492ee58920178080f0da306750a356ddfe1b695c12becd07
- 4a5b8442dc2b34a270acdcd8a14cce573d59dc0922c9e49cda8fe2dd8e4a3862
- 80b80e15f605f0b8740e1989e505280394d746e8a8ee37cdb9b009d745e42da0
- 4280eb4cfa0445a40d8e1dfafdc0eb24613f3536c5959270ef0079034b30e653
- 2f1cb29e47c5b07fba3070d6a5339b00d2f3075eb7717438cf5cf53679793919
- 252d9ed583bbd2e5d75ae5167feb393bd50b44933594f9586aaf5d9987cf78ec
- edac6216665f1c8b0a09158abdd5e7fab63a386a1c9ad31ddd5ee92a6aa811fc
- 13ac538c8c6696a59f890677cf451db77b7c33539da1d380640ce549b2b70ca4
- italzformendinggallores[.]duckdns[.]org
- humblecrazeforeal8897[.]accesscam[.]org
- sertiscoppersail432[.]freeddns[.]org
- moristaetdfertal9002[.]ddnsgeek[.]com
- paradoncalleke5689[.]camdvr[.]org
- greeslieforreallcul5672[.]casacam[.]net
- blissfulzerooooos690[.]ddnsfree[.]com
- www[.]blissfulzerooooos690[.]ddnsfree[.]com
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Sjydgbr[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Guwasd[.]dat
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Fwudzwsfsp[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Dyvfi[.]dat
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Iicivjzqdma[.]mp3
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Dewsmwflw[.]vdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Xlkythleoq[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Zerwfilj[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Sfrnotlay[.]mp3
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Jovjvwp[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Vmoeykn[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Wyvmy[.]wav
- hxxp[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Zafvlztxj[.]vdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Gikwomjv[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Zafvlztxj[.]vdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Qecvodcnuz[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Hlynogyqp[.]dat
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Uvkoiguq[.]dat
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Awtvbihi[.]vdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Oqjhea[.]mp3
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Ztpcwfowiiu[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Bonhowau[.]mp4
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Qcqvzdtpln[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Jlhwfgnnyms[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Otmaq[.]mp4
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Elxrh[.]vdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Rxmjavdc[.]mp3
- hxxp[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Elxrh[.]vdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Cfyenm[.]mp4
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Bibyep[.]mp4
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Lcrakntjck[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Atcbgl[.]mp4
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Rspfqdltykq[.]mp3
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Fxsovxc[.]pdf
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Bnvqyotgu[.]mp3
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Rmtafnw[.]mp3
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Lmshcchh[.]wav
- hxxps[://]sanel[.]net[.]pl/filescontentgalleries/pictorialcoversoffiles/Ibesc[.]wav
- hxxps[://]cud-senegal[.]org/post-postlogin/Oojhwcym[.]wav
- hxxps[://]cud-senegal[.]org/post-postlogin/Cpoewtupeck[.]mp4
- hxxps[://]cud-senegal[.]org/post-postlogin/Nrileknnlgv[.]vdf
- hxxps[://]cud-senegal[.]org/post-postlogin/Izevzxvwkpf[.]pdf



































