
Critical Veeam Vulnerability (CVE-2025-23120) Enables Remote Code Execution by Domain Users
A newly discovered vulnerability in Veeam Backup & Replication, tracked as CVE-2025-23120, has emerged as a critical threat for enterprise environments. With a near-maximum CVSS score, this flaw enables authenticated domain users to execute arbitrary code remotely, exposing a direct path to compromising backup infrastructures.
What Makes CVE-2025-23120 So Dangerous?
The CVE-2025-23120 (CVSS 9.9) vulnerability stems from a deserialization flaw in the Veeam Backup & Replication software’s .NET-based components, specifically within the Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary classes. These components mishandle serialized data, allowing malicious actors to craft input that executes arbitrary code on the server.
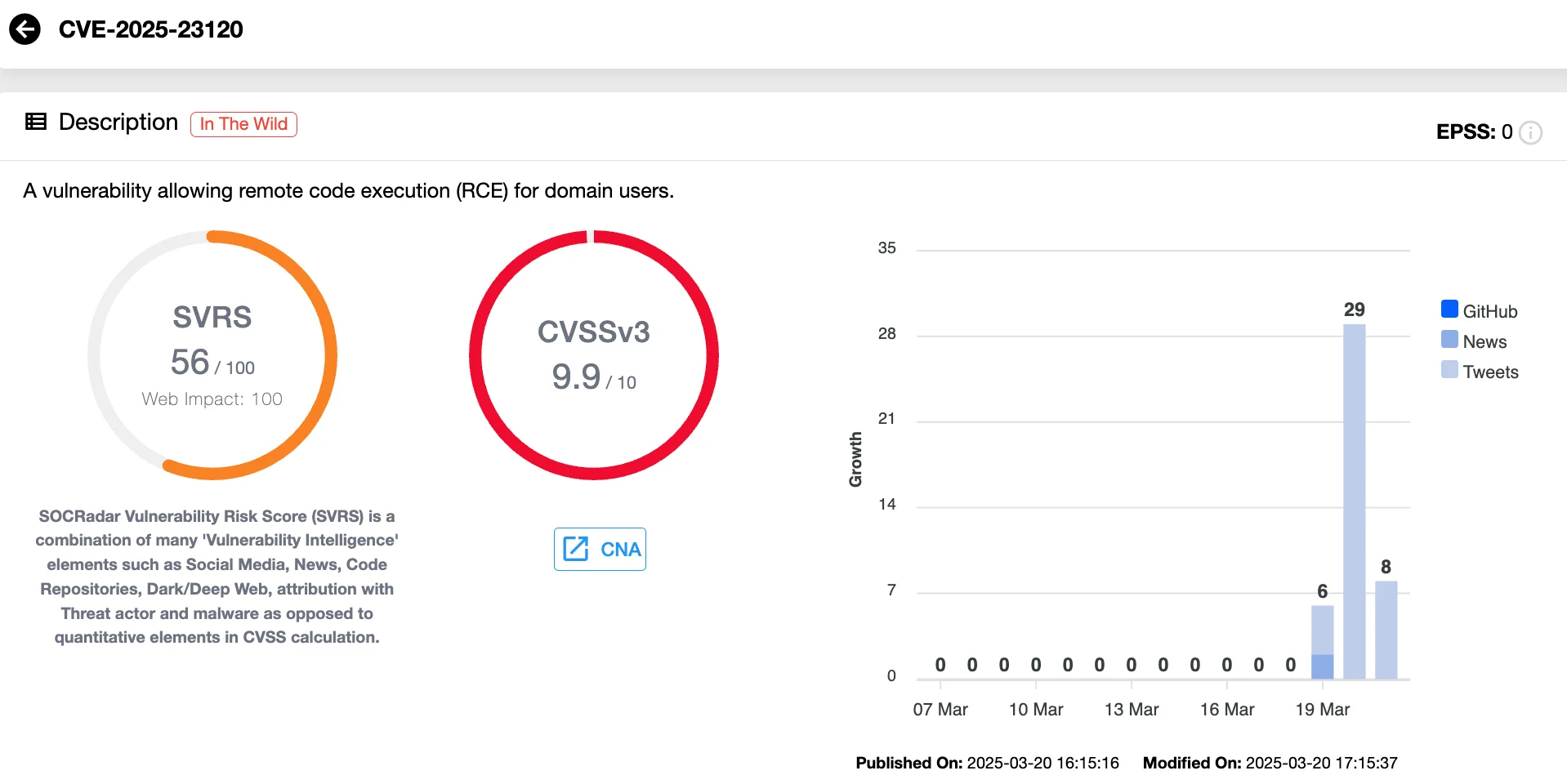
Vulnerability card for CVE-2025-23120 (SOCRadar Vulnerability Intelligence)
Critically, the flaw only affects installations joined to a Windows domain – a configuration many organizations adopt despite Veeam’s longstanding guidance to avoid it. In such cases, any domain user can exploit the vulnerability, regardless of their privilege level.
CVE-2025-23120 impacts Veeam Backup & Replication version 12.3.0.310 and all earlier builds of version 12.
Rapidly identifying vulnerabilities like CVE-2025-23120 is vital to protecting critical assets. SOCRadar’s Vulnerability Intelligence, part of the Cyber Threat Intelligence module, provides real-time alerts, detailed exploit insights, and clear mitigation steps. Security teams can prioritize high-risk vulnerabilities, understand attacker behaviors, and promptly apply fixes, moving faster than threat actors and significantly reducing the likelihood of exploitation.
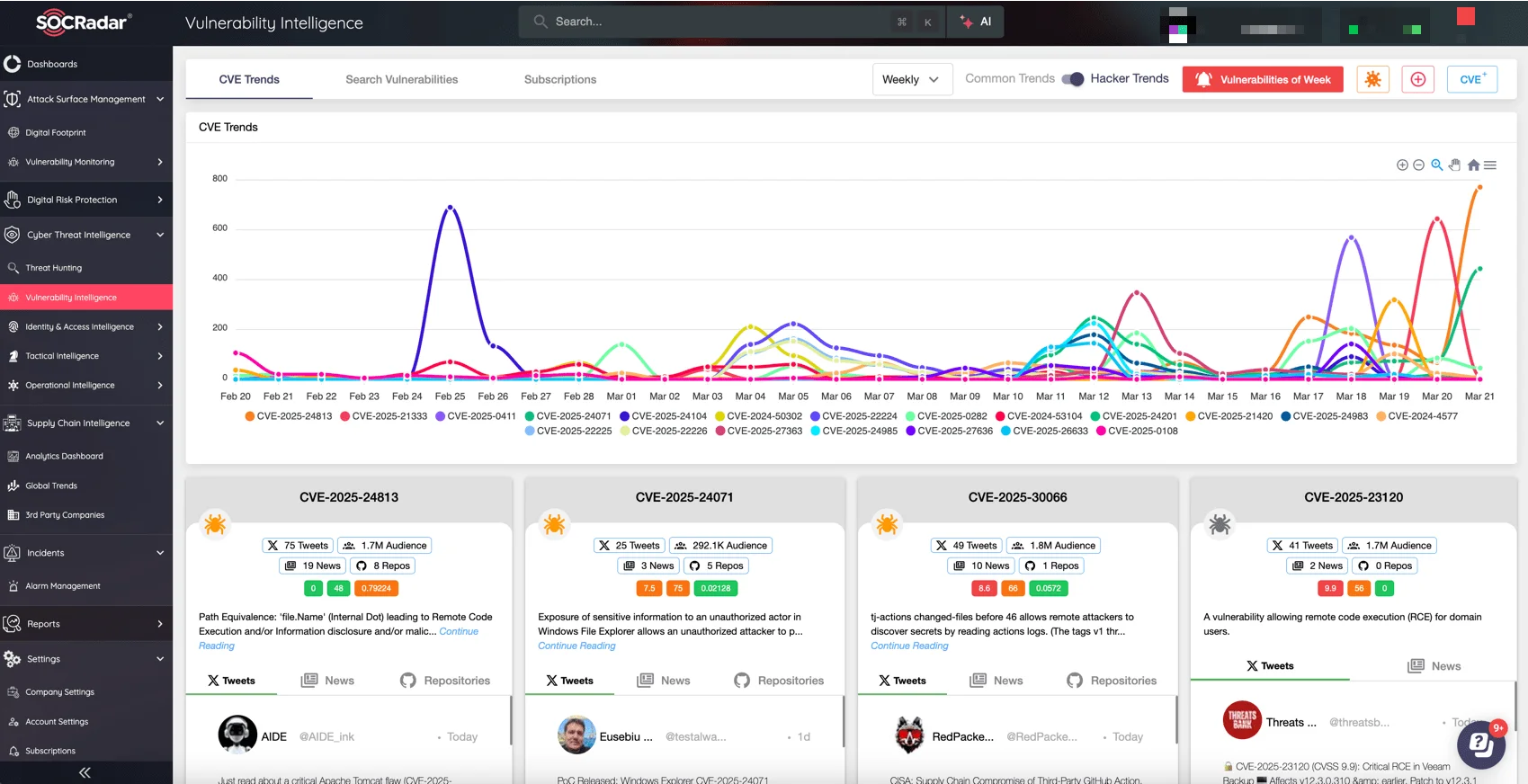
SOCRadar’s Vulnerability Intelligence: Track the latest CVEs and hacker trends
How the Exploit Works
At the core of this vulnerability is Veeam’s reliance on a blacklist approach to prevent insecure deserialization. While this method blocks known dangerous object types, it leaves room for attackers to identify unlisted gadgets. In this case, researchers at watchTowr Labs discovered a gadget chain that bypasses the blacklist by abusing the .NET DataSet class – well-known in the security community for its Remote Code Execution (RCE) capabilities.
This attack vector can be used by anyone with access to the Domain Users group, which typically includes all standard domain accounts. Once exploited, it could provide complete control over the backup server, potentially allowing attackers to delete backups, manipulate data, or establish persistence.
Immediate Mitigation Steps for CVE-2025-23120
Veeam has issued a patch via Backup & Replication version 12.3.1 (build 12.3.1.1139), and all users of affected versions are strongly encouraged to update immediately. The software vendor has not reported any exploitation in the wild as of now, but the public availability of technical details makes this vulnerability highly likely to be weaponized soon.
Here are the best practices going forward:
- Update to version 12.3.1 immediately. Delaying patches in this case may leave critical infrastructure vulnerable to ransomware and other advanced attacks.
- Avoid domain-joined installations unless absolutely necessary. Veeam has long advised against this configuration for good reason.
- Review server exposure and privileges. Ensure backup servers are segmented from general user access and are not accessible externally.
See the official Veeam advisory for CVE-2025-23120 here.
Why This Matters for Security Teams
Backup infrastructure represents a high-value target for attackers, especially ransomware operators. If they can control or disable backups, the odds of a successful extortion increase dramatically. Given the history of actively exploited vulnerabilities in Veeam products, CVE-2025-23120 should not be taken lightly. Organizations relying on Veeam must not only patch promptly but also reassess their architectural decisions, especially those involving domain integration and internal user access.
SOCRadar’s Attack Surface Management (ASM) module
Backup systems are increasingly targeted by threat actors, making your external exposure critical. SOCRadar’s Attack Surface Management continuously monitors your externally accessible systems and infrastructure, quickly identifying vulnerable services, exposed ports, and configuration weaknesses. Gain full visibility into your attack surface, prioritize remediation effectively, and prevent threats from compromising critical infrastructure such as your backup and disaster recovery solutions.



































