
VMware ESXi, Workstation, Fusion Vulnerabilities Allow Code Execution, Sandbox Escape (CVE-2024-22252 – 22255)
[Update] March 7, 2024: “CISA Urges Swift Patching of VMware Vulnerabilities”
VMware has released an advisory to address multiple security vulnerabilities present in VMware ESXi, Workstation, and Fusion. These vulnerabilities pose significant risks, with severity levels ranging from high to critical, as indicated by their CVSS scores.
The affected product versions are:
- VMware ESXi 7.0, 8.0, and 8.0 [2]
- VMware Workstation Pro / Player (Workstation) 17.x
- VMware Fusion Pro / Fusion (Fusion) 13.x on MacOS
Furthermore, VMware Cloud Foundation versions 4.x and 5.x are also affected, as they deploy the ESXi component.
Details of the Latest VMware Vulnerabilities, CVE-2024-22252, CVE-2024-22253, CVE-2024-22254, and CVE-2024-22255
Below, you can find the details of the latest VMware vulnerabilities. According to the VMware advisory, while the individual vulnerabilities documented for ESXi are rated as ‘Important’ in severity, their combination results in a ‘Critical’ severity level.
CVE-2024-22252:
It is a use-after-free vulnerability found in the XHCI USB controller that affects VMware ESXi, Workstation, and Fusion. Its exploitation could allow an attacker with local administrative privileges to execute code within the virtual machine’s VMX process on the host.
In ESXi, exploitation is limited to the VMX sandbox, whereas in Workstation and Fusion, code execution can occur on the machine where the component is installed.
VMware has rated the severity of this vulnerability as Critical, with a maximum CVSS score of 9.3 for Workstation/Fusion, and Important with a maximum score of 8.4 for ESXi.
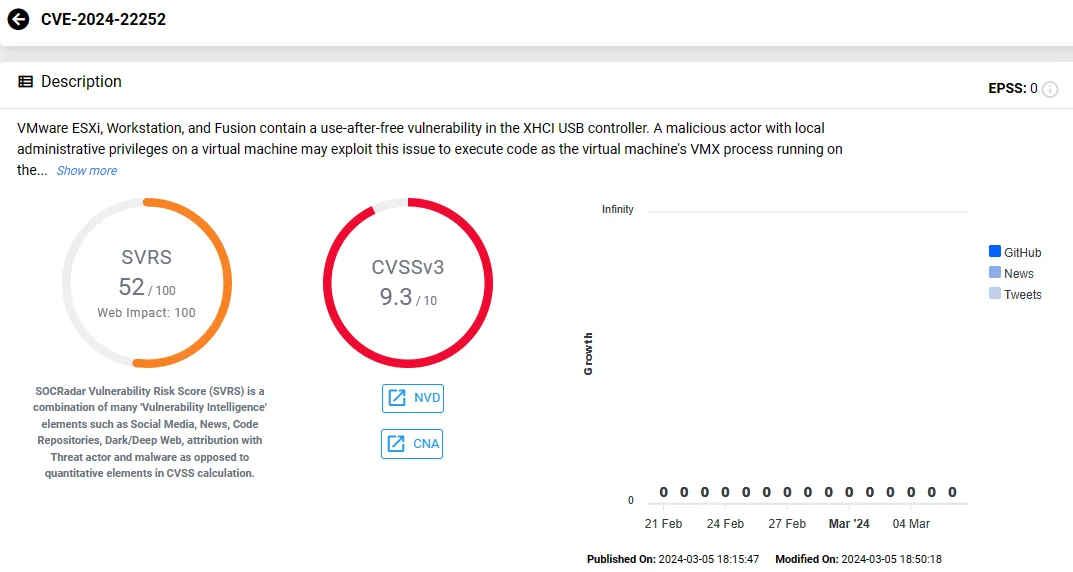
Vulnerability card of CVE-2024-22252 (SOCRadar)
CVE-2024-22253:
Another use-after-free vulnerability, this time found in the UHCI USB controller, affects VMware ESXi, Workstation, and Fusion. Exploitation of this vulnerability is similar to CVE-2024-22252, enabling code execution.
Attacks using CVE-2024-22253 are also restricted to the VMX sandbox on ESXi but allow code execution where Workstation or Fusion is installed.
VMware has classified the severity of this vulnerability as ‘Critical’, with a CVSS score of 9.3 for Workstation/Fusion, and as ‘Important’, with a score of 8.4 for ESXi.
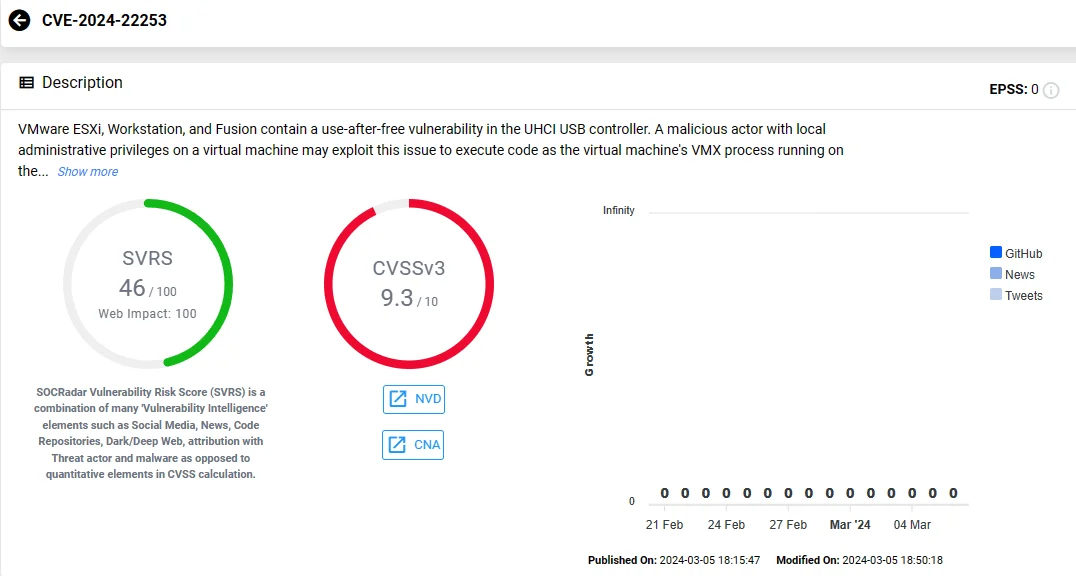
Vulnerability card of CVE-2024-22253 (SOCRadar)
CVE-2024-22254:
A high-severity out-of-bounds write vulnerability, with a CVSS score of 7.9, impacts VMware ESXi.
If exploited, this vulnerability could allow a threat actor with privileges within the VMX process to trigger an out-of-bounds write, potentially leading to sandbox escape.
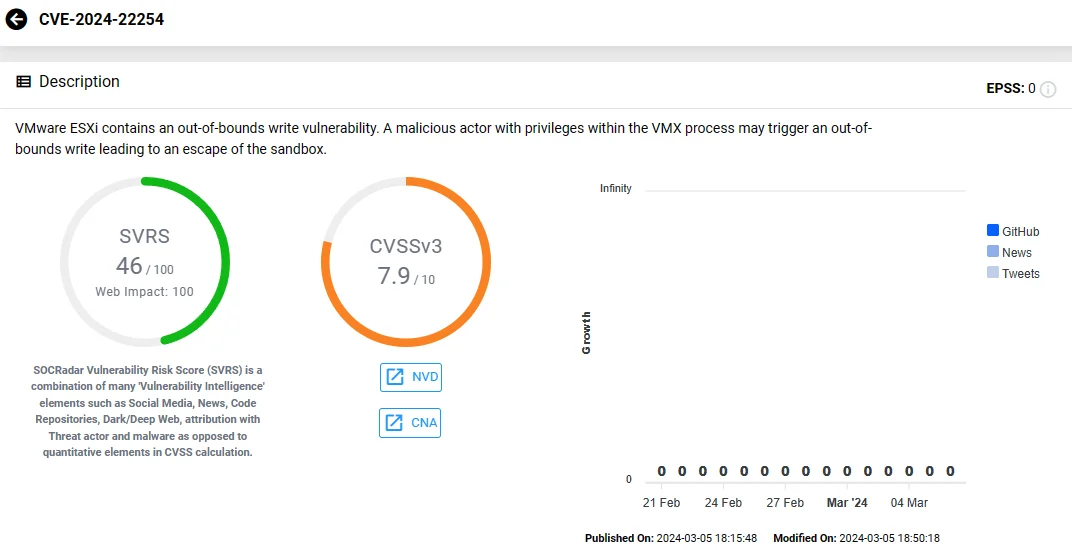
Vulnerability card of CVE-2024-22254 (SOCRadar)
CVE-2024-22255:
An information disclosure vulnerability, identified as CVE-2024-22255, is present in the UHCI USB controller and affects VMware ESXi, Workstation, and Fusion. VMware assigned a CVSS score of 7.1 to this issue.
Exploiting this vulnerability, a threat actor with administrative access to a virtual machine may leak memory from the VMX process, as highlighted in the advisory.
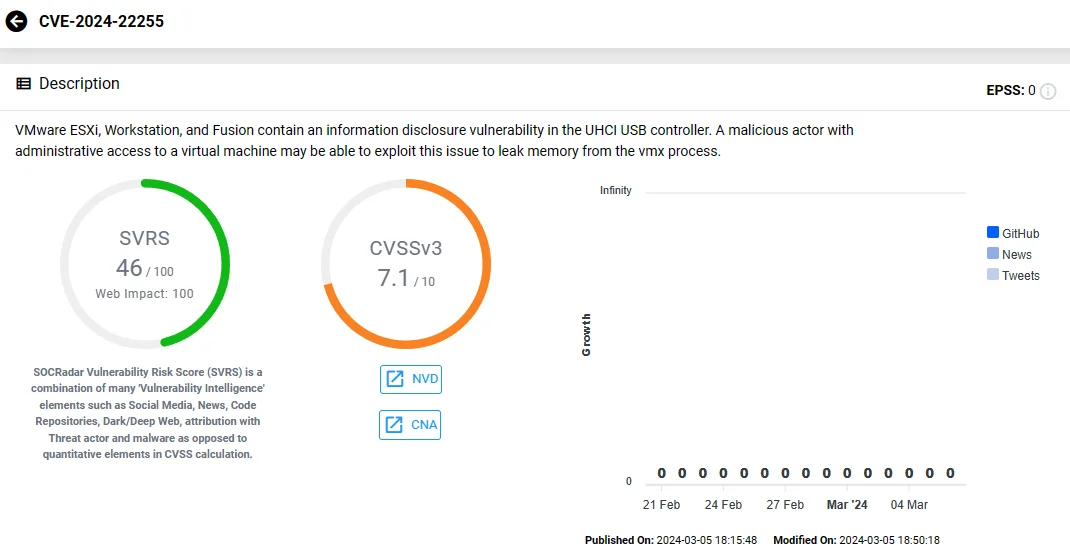
Vulnerability card of CVE-2024-22255 (SOCRadar)
Use SOCRadar’s Attack Surface Management (ASM) module to automate the monitoring of vulnerabilities in your assets and components. The platform quickly sends alerts for emerging security issues, providing valuable insights to help prioritize patching processes.
SOCRadar’s Attack Surface Management
How to Fix These Vulnerabilities? Are There Any Workarounds?
VMware has devised a workaround for the CVE-2024-22252, CVE-2024-22253, and CVE-2024-22255 vulnerabilities associated with the USB controller. This solution eliminates the risk of exploitation, although it is still recommended that users implement permanent fixes when feasible.
The workaround involves removing all USB controllers from the Virtual Machine, disabling USB passthrough functionality, and rendering virtual USB devices inaccessible. Default keyboard and mouse input devices remain unaffected because they operate independently of the USB protocol.
VMware notes that certain guest operating systems, such as MacOS, do not support PS/2 mouse and keyboard usage without a USB controller, thus losing functionality.
You can access the workaround guides for specific products through the following links: VMware ESXi, VMware Fusion, VMware Workstation Player, VMware Workstation Pro.
For updates and additional documentation, please refer to the official VMware security advisory.
SOCRadar’s Vulnerability Intelligence module offers in-depth insights into vulnerabilities, encompassing exploitability, available exploits, repositories, and updates. Users can conveniently search for specific products or vendors on the platform, accessing comprehensive details about related vulnerabilities.
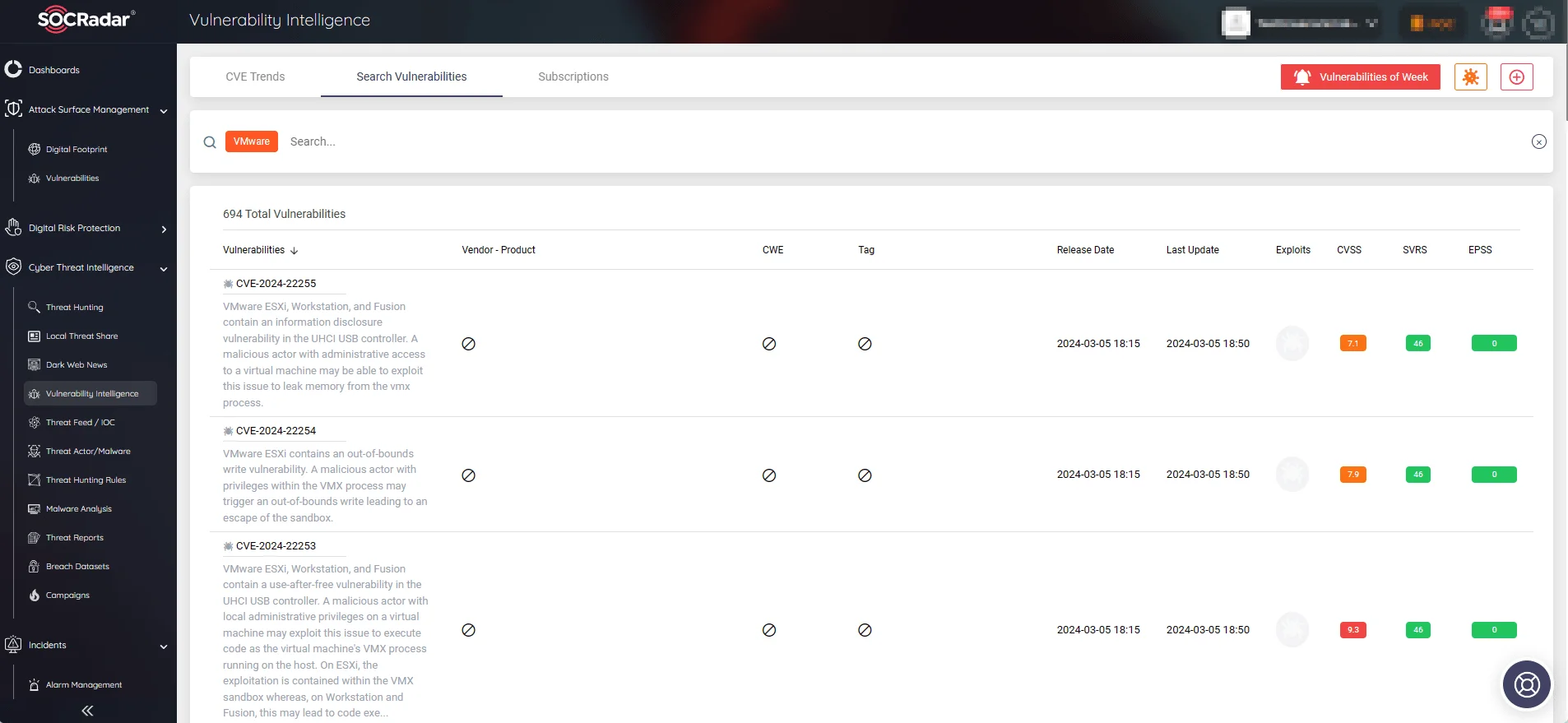
SOCRadar’s Vulnerability Intelligence
CISA Urges Swift Patching of VMware Vulnerabilities
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert, emphasizing critical VMware security updates addressing vulnerabilities in ESXi, Workstation, and Fusion, from CVE-2024-22252 to CVE-2024-22255.
The agency warns that these vulnerabilities could enable threat actors to seize control of impacted systems, and urges users and administrators to promptly review the VMware security advisory and implement the updates accordingly.



































