
VMware Fusion Receives Fix for a Severe Code Execution Vulnerability, CVE-2024-38811
Recently, Broadcom has addressed a significant security vulnerability in VMware Fusion. Tracked as CVE-2024-38811, the flaw bears high severity, and its exploitation could compromise critical systems.
VMware Fusion is a powerful virtualization software for macOS that enables users to run multiple operating systems on a single device. It’s popular among developers, IT professionals, and enterprises for tasks ranging from testing new environments to managing critical infrastructure.
What is CVE-2024-38811?
CVE-2024-38811 (CVSS: 8.8) is a high-severity code execution vulnerability in VMware Fusion due to improper handling of environment variables.
This flaw enables attackers to execute arbitrary code within the context of the Fusion application. Concerningly, an attacker does not require any elevated privileges to exploit CVE-2024-38811, meaning attackers with standard user rights can target it as well.
Once exploited, the attacker could manipulate VMware Fusion and execute malicious code in the context of the application.
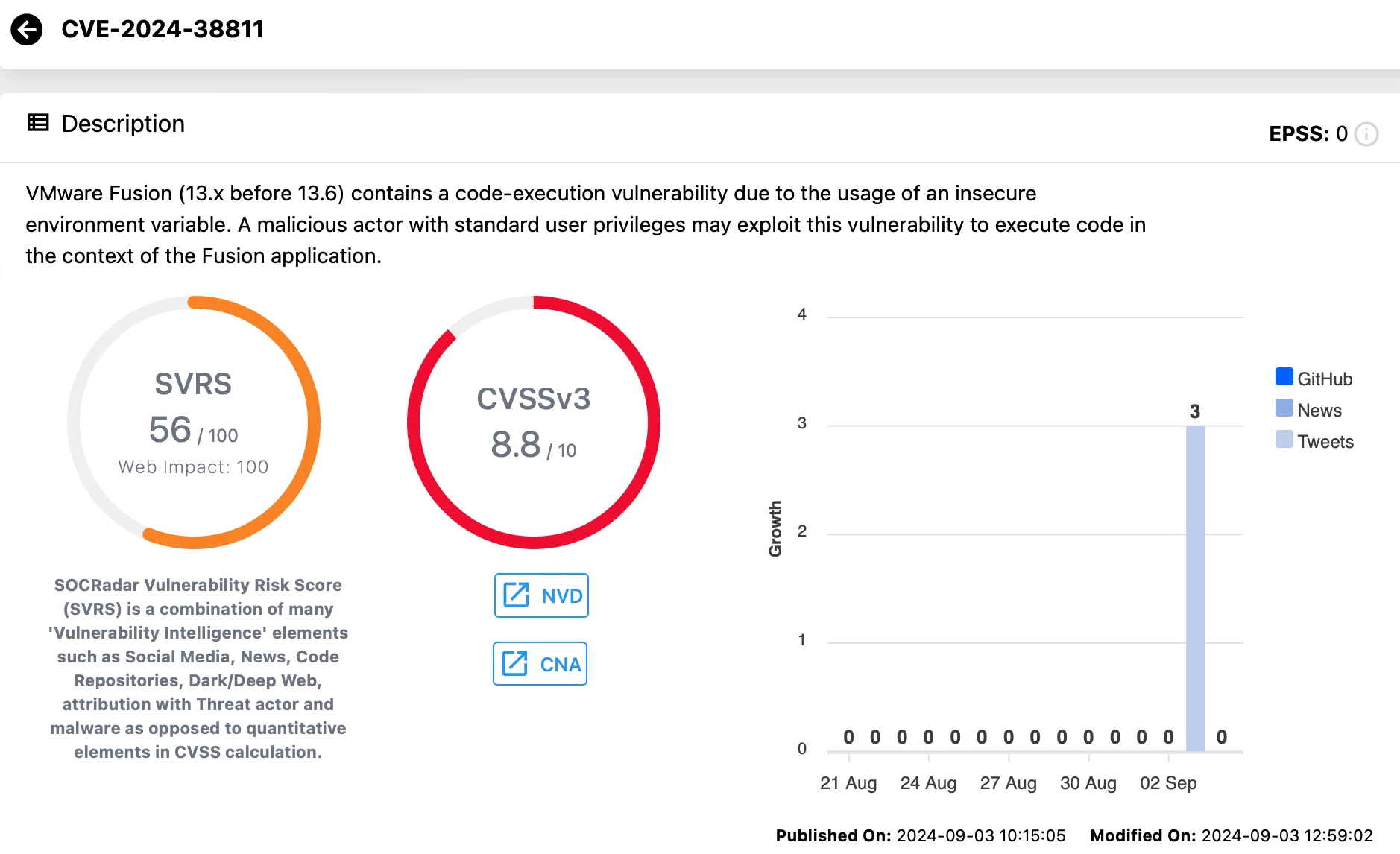
Vulnerability card for CVE-2024-38811 (Vulnerability Intelligence)
The vulnerability stems from the software’s insecure use of an environment variable, allowing attackers to take control of the Fusion application, potentially leading to full system compromise.
Which VMware Fusion Versions Are Affected?
CVE-2024-38811 affects all versions of VMware Fusion before version 13.6. Users running these older versions are exposed to potential attacks.
To check if your version is affected, you can open VMware Fusion, go to “About VMware Fusion,” and verify your version number. If your version is below 13.6, it is critical to update as soon as possible.
Are There Any Reports of Exploitation?
Currently, there are no known reports of active exploitation for CVE-2024-38811. However, since the vulnerability is severe, it is possible that attackers may develop exploits soon. This makes it vital to update VMware Fusion without delay to avoid future attacks.
SOCRadar’s Vulnerability Intelligence module offers real-time insights into emerging threats by continuously tracking new CVEs, their severity, and exploitation trends. It empowers security teams with detailed information on each vulnerability, allowing you to prioritize patches.
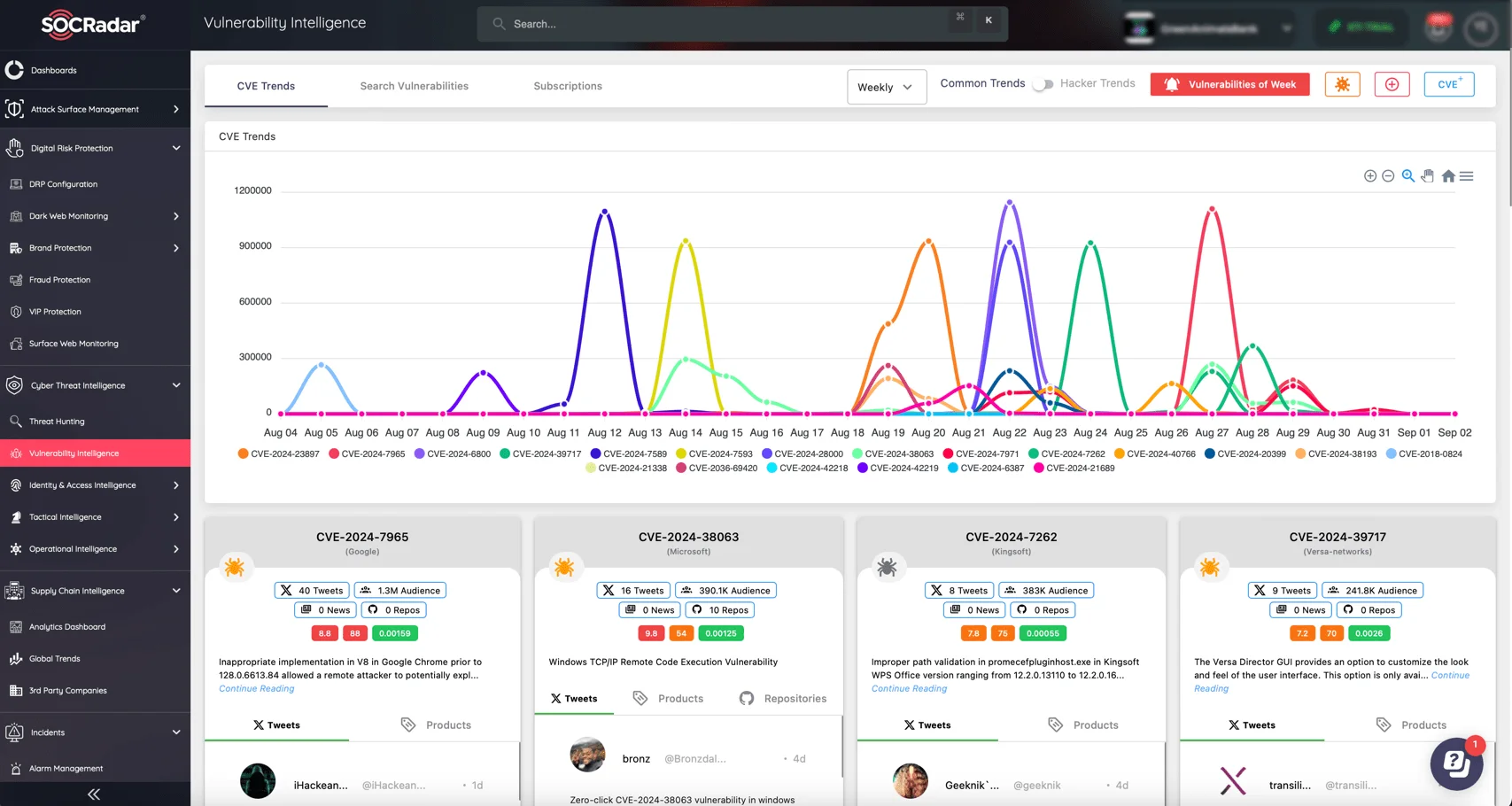
SOCRadar’s Vulnerability Intelligence module
With automated alerts and reports, SOCRadar ensures that no vulnerability goes unnoticed, helping businesses stay ahead of potential threats and apply the necessary patches before attackers can exploit them.
How to Address CVE-2024-38811
Broadcom, the parent company of VMware, has addressed this vulnerability in VMware Fusion 13.6, and it’s crucial for users to update their software to this version immediately to mitigate any risks.
If updating is not immediately possible, it is advised to minimize usage of VMware Fusion for sensitive operations. However, since there are no workarounds for this vulnerability, updating remains the only direct solution.
For organizations relying on VMware Fusion in enterprise settings, prioritizing this patch is important to avoid potential breaches. The vulnerability’s accessibility and potential for exploitation make timely updates essential for maintaining security.
VMware products are typically targeted by cybercriminals due to their widespread use. Previously, CISA has issued alerts for several vulnerabilities in VMware Fusion, ESXi, and Workstation, which allowed for code execution and information disclosure. It is essential for organizations to maintain up-to-date patches to secure their systems against such security vulnerabilities. You can read more about these previous vulnerabilities here: VMware ESXi, Workstation, Fusion Vulnerabilities Allow Code Execution, Sandbox Escape (CVE-2024-22252 – 22255).
Prioritize Your Patches with SOCRadar’s Attack Surface Management (ASM) Module
Monitor your digital footprint in real-time with SOCRadar’s Attack Surface Management (ASM) module, identifying exposed assets and associated vulnerabilities.
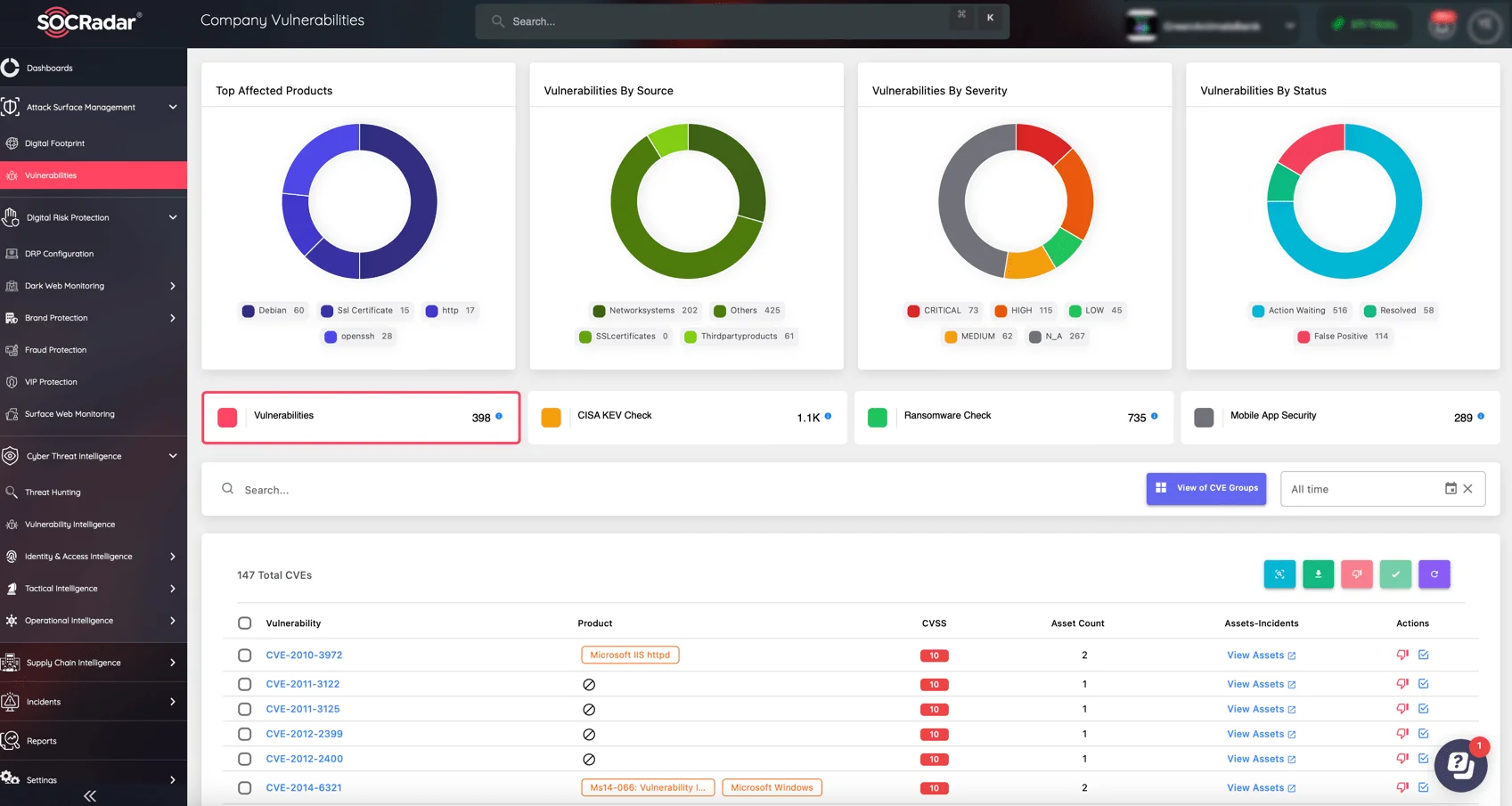
SOCRadar’s Attack Surface Management module
By scanning external-facing assets and alerting on potential weak points, ASM helps security teams understand their attack surface better, allowing for timely remediation and patching.


































