What Do You Need to Know About Fortinet Critical Authentication Bypass Vulnerability (CVE-2022-40684)?
1. What are the CVE details and severity status of vulnerabilities?
Last week, Fortinet patched a severe authentication bypass vulnerability. The company confirmed after the patch that the vulnerability is being exploited in the wild.
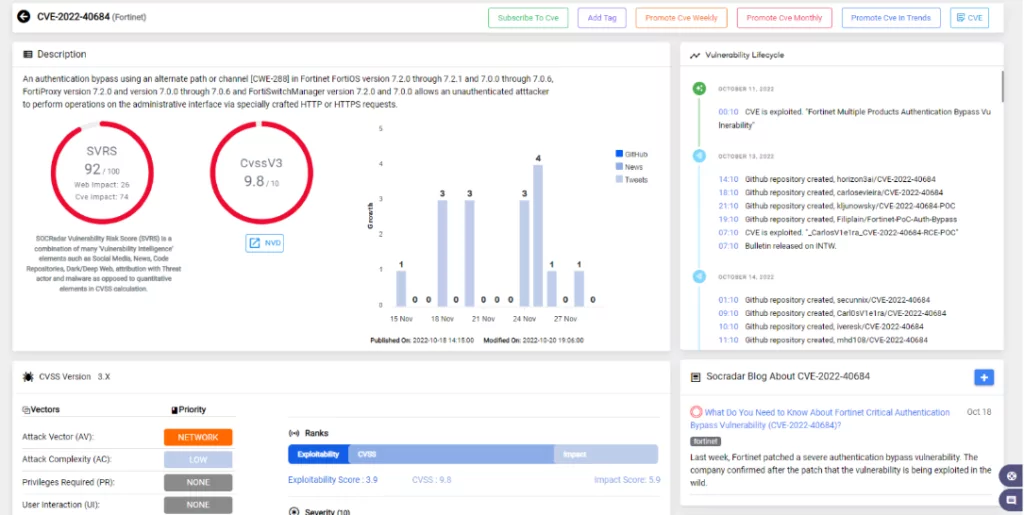
The CVE-2022-40684(CVSS score: 9.6) vulnerability enables an unauthenticated remote attacker to use administrative interfaces by sending specially crafted HTTP or HTTPS requests, allowing them to log in to various products of Fortinet that are unpatched.
2. Which Fortinet product versions are vulnerable?
- FortiOS versions between 7.0.0 – 7.0.6 and 7.2.0 – 7.2.1
- FortiProxy versions between 7.0.0 – 7.0.6 and version 7.2.0
- FortiSwitchManager versions 7.0.0 and 7.2.0
3. Has the security patch update currently been published?
The ultimate solution to CVE-2022-40684 is applying the software updates provided by Fortinet.
Update to:
- FortiOS versions 7.0.7 or 7.2.2 and later
- FortiProxy versions 7.0.7 or 7.2.1 and later
- FortiSwitchManager versions 7.2.1 and later
4. Is reliable evidence of vulnerabilities being exploited in the wild? Has the proof-of-concept exploit code been published?
Proof-of-concept (PoC) exploit code was created by security researchers with the Horizon3 Attack Team. Technical deep dive is also available.
GreyNoise, a cybersecurity firm, also disclosed that it had observed attackers attempting to use CVE-2022-40684 in the wild.
According to a Shodan search, more than 165,000 FortiGate firewalls are reachable from the Internet and might potentially be attacked if their admin management interfaces are made public.
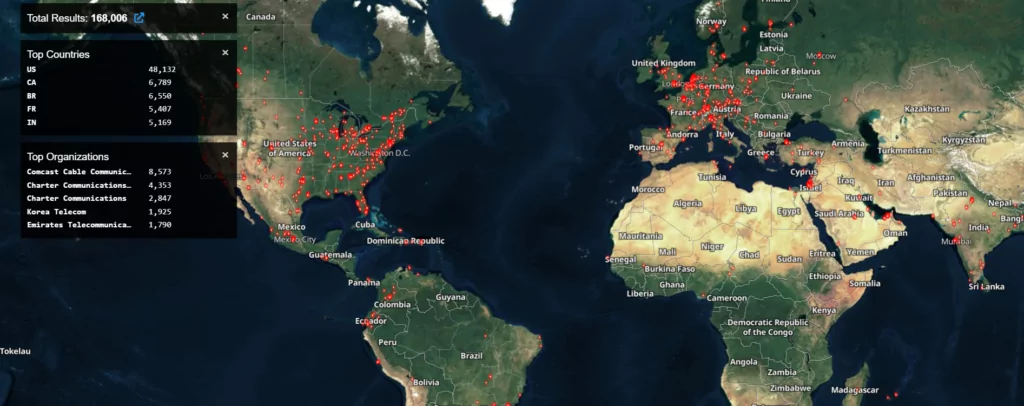
In mid-November, a threat actor on a Russian hacker forum was spotted sharing unauthorized access to some Fortinet VPNs. According to researchers, the attacker could gain access by exploiting CVE-2022-40684 on targets running out-of-date Fortinet software.

5. Are there confirmed workaround and mitigation steps until full patching?
Suppose clients cannot quickly apply security patches. In that case, Fortinet recommends disabling the HTTP/HTTPS administrative interface for all affected products and restricting IP addresses that can have access to prevent remote hackers from logging in. Details about how to disable it can be found in the advisory.
6. Is there any intelligence that notorious threat actors like APT groups exploit vulnerabilities?
It is not known if any APT groups have exploited CVE-2022-40684.
7. How to create and implement an effective action plan to get you over the hump?
“Fortinet is aware of an instance where this vulnerability was exploited,” Fortinet explains in the advisory they published yesterday and recommends checking device logs for the given indicators:
- user=”Local_Process_Access”
- user_interface=” Node.js”
- user_interface=” Report Runner”
Look for other indicators of compromise to apply proper security measures. IoCs can be found here.
Get alerted about the latest threats. SOCRadar’s vulnerability intelligence can provide details and updates on the vulnerabilities. You can access details of the CVE-2022-40684 vulnerability affecting Fortinet on the platform.