
What Is Cyber Threat Intelligence?
The swift adoption of information technology has coincided with an alarming surge in cyber-attacks, as malicious actors deploy increasingly sophisticated exploits. Therefore, cyber threats have evolved to become more refined and pervasive. In response, organizations strive to develop timely, relevant, and actionable cyber threat intelligence. Organizations face constant challenges in protecting their assets and sensitive data. This is where Cyber Threat Intelligence (CTI) becomes a game-changer. But what exactly is CTI, and why is it crucial?
Defining Cyber Threat Intelligence
Cyber Threat Intelligence is the process of collecting, analyzing, and interpreting data about cyber threats to provide actionable insights. These insights empower organizations to understand potential threats, mitigate risks, and strengthen their cybersecurity posture. CTI doesn’t just react to threats but proactively identifies vulnerabilities and prepares defenses.
Thus, from the perspective of an academic work, CTI is rooted in analyzing a wide array of data sources, including dark web activities, malware analysis, and threat actor profiling. The ultimate goal is to turn raw data into actionable intelligence that helps organizations defend against cyber adversaries.

SOCRadar profiles threat actors, and SOCRadar Platform’s Threat Actor Intelligence serves as a main hub for tracking threat actors
Key Components of Cyber Threat Intelligence
- Data Collection involves gathering information from various sources, such as Open-Source Intelligence (OSINT), Human Intelligence (HUMINT), Technical Intelligence (TECHINT), and social media.
- Analysis: Using advanced analytical tools and techniques to identify patterns, trends, and Indicators of Compromise (IOCs).
- Dissemination: Sharing actionable intelligence with relevant stakeholders to enable informed decision-making.
Why Is Cyber Threat Intelligence Important?
- Proactive Defense: CTI helps organizations anticipate attacks rather than just respond to them.
- Resource Optimization: Companies can allocate resources more efficiently by focusing on specific, credible threats.
- Improved Incident Response: Timely intelligence enables faster detection and mitigation of attacks.
- Enhanced Risk Management: CTI provides a deeper understanding of the threat landscape, allowing for better risk assessment and prioritization.
- Threat Actor Understanding: It offers insights into attackers’ motives, tools, and methods, helping organizations craft more targeted defenses.
Threat Intelligence Lifecycle
The Threat Intelligence Lifecycle is a systematic process that transforms raw data into actionable insights to inform decision-making and enable proactive cybersecurity measures. This lifecycle ensures organizations adapt effectively to the ever-evolving threat landscape while continuously improving their intelligence operations.
Here are the six key steps of the lifecycle:
- Requirements
The process begins by defining the specific objectives of the threat intelligence operation. Stakeholders and teams collaborate to identify key priorities, such as:
- Understanding attacker motivations and methods.
- Identifying the organization’s vulnerabilities or attack surface.
- Determining actionable steps to mitigate risks.
Clear goals set during this phase guide the subsequent steps of the lifecycle.
- Collection
In this phase, teams gather the necessary data to address the defined objectives. Sources may include:
- Network logs and system data.
- Open-Source Intelligence (OSINT) from forums, social media, and blogs.
- Industry reports and threat feeds.
The focus is on collecting relevant, high-quality information efficiently.
- Processing
Collected raw data is organized and converted into a usable format. This phase includes:
- Filtering out irrelevant or duplicate data.
- Structuring datasets for analysis, such as categorizing IOCs.
- Decrypting files or translating foreign-language information.
This step ensures the data is clean, reliable, and ready for detailed examination.
- Analysis
The processed data is analyzed to draw insights and answer the questions established in the requirements phase. Analysts identify patterns, assess risks, and generate actionable intelligence. The outcome includes:
- Identifying TTPs (Tactics, Techniques, and Procedures) of threat actors.
- Prioritized recommendations for stakeholders.
- Contextual insights to guide decision-making.
- Dissemination
Intelligence findings are communicated to the intended audience in a clear, actionable format. Key considerations include:
- Tailoring content to the audience (e.g., executives vs. SOC teams).
- Using concise reports, dashboards, or briefings.
The goal is to present the intelligence in a way that supports timely and informed decisions.
- Feedback
The final stage focuses on reviewing the effectiveness of the intelligence process. Stakeholders provide feedback to refine objectives, improve collection methods, or adjust dissemination strategies. This feedback loop ensures continuous improvement in future operations.
Types of Cyber Threat Intelligence
Cyber Threat Intelligence (CTI) encompasses a wide range of insights, from high-level strategic information to granular technical details about specific attacks. These intelligence types cater to different audiences and serve unique purposes within an organization’s cybersecurity framework.
CTI evolves along a maturity curve, progressing from basic indicators to comprehensive analysis. As intelligence becomes more detailed and contextual, it also becomes more valuable and resource-intensive to produce. Below are the main types of CTI and their key characteristics:
Basic diagram for types, created by DALL-E
Strategic: Strategic intelligence offers a high-level overview of the threat landscape, helping organizations understand long-term risks and plan accordingly. It connects cyber threats to broader trends, such as geopolitical events or industry-specific developments.
This intelligence is tailored for executives and decision-makers, helping them prioritize cybersecurity investments and align them with organizational goals. Strategic intelligence typically comes in the form of detailed reports and requires expertise to produce, as it involves analyzing complex global and industry dynamics.
Key Points:
- Focuses on long-term risk analysis and mitigation.
- Links cybersecurity threats to global and industry trends.
- Informs business and security strategy at the executive level.
Operational: Operational intelligence goes beyond technical indicators to explore the context of attacks. It provides insights into adversaries’ Tactics, Techniques, and Procedures (TTPs), as well as their motivations and objectives.
This type of intelligence often involves campaign analysis and threat actor profiling, offering valuable information for Incident Response, Threat Hunting, and Vulnerability Management. Unlike Tactical Intelligence, Operational Intelligence has a longer lifespan, as it focuses on understanding the behavior and intent of threat actors rather than their tools.
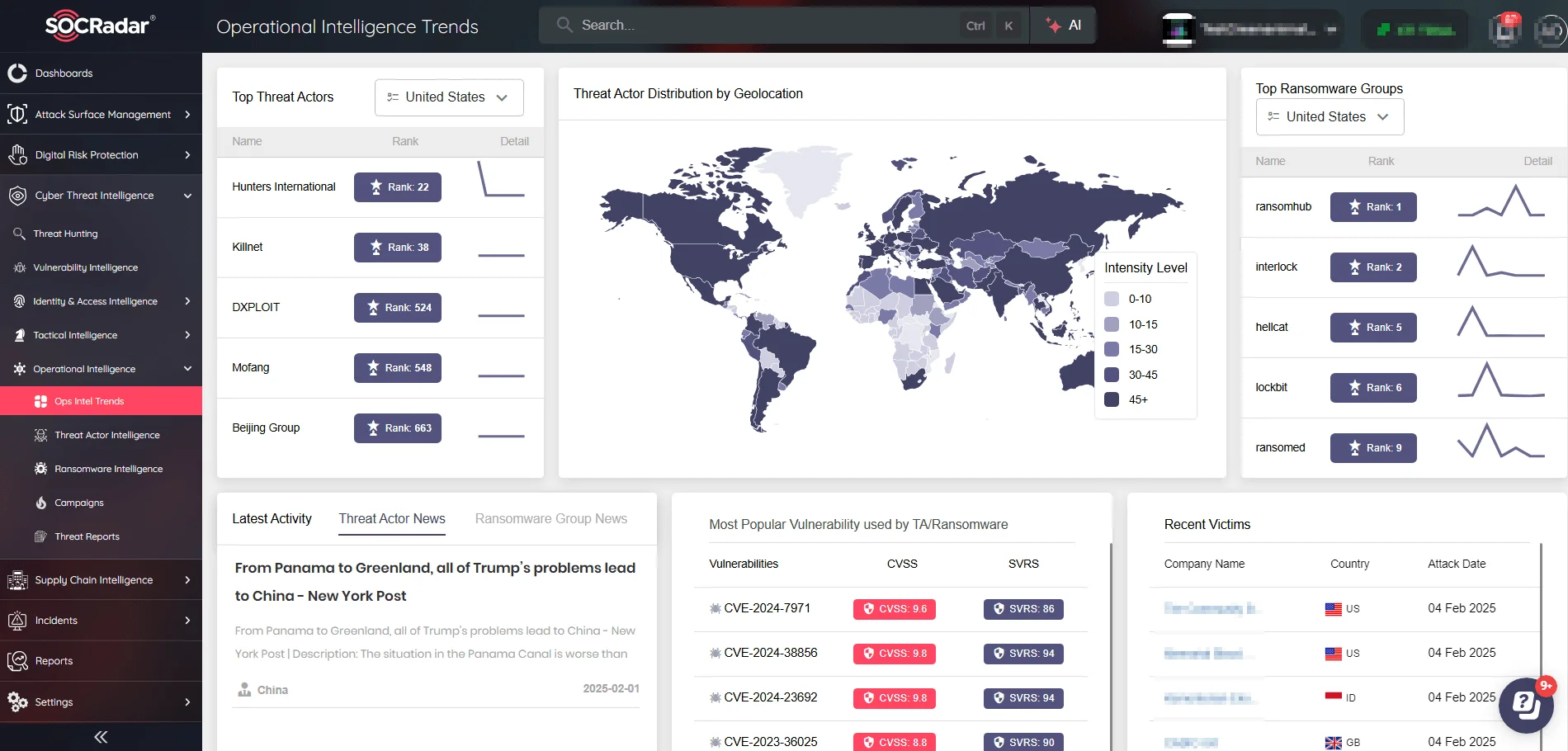
Operational Intelligence Trends in SOCRadar’s Operational Intelligence module
Key Points:
- Provides context about adversaries and their methods.
- Helps track threat campaigns and profile attackers.
- Supports proactive defenses, such as threat hunting.
Tactical: Tactical threat intelligence focuses on immediate and actionable insights. It is often technical and includes Indicators of Compromise (IOCs) such as malicious IPs, URLs, file hashes, and domain names.
This type of intelligence is typically automated and is widely available through free or commercial feeds. However, its relevance can be short-lived, as attackers frequently update their methods. Tactical intelligence is ideal for enhancing real-time defense mechanisms, such as intrusion detection systems or endpoint security solutions.
Key Points:
- Consists of IOCs like IP addresses and file hashes.
- Suitable for automated integration into security systems.
- Best used for immediate threat detection and response.
Technical: Technical intelligence delves deeper into the specifics of an attack, focusing on the tools, vulnerabilities, and methodologies used by threat actors. It provides in-depth knowledge about exploit kits, malware behavior, and attack infrastructures.
This type of intelligence is invaluable for vulnerability management, malware analysis, and enhancing an organization’s defensive capabilities. Unlike tactical intelligence, technical insights are less time-sensitive and more focused on understanding the underlying mechanisms of threats.
Key Points:
- Explores malware, exploits, and attack methods.
- Supports vulnerability patching and malware defenses.
- Typically requires expertise in cybersecurity analysis.
Applications of Cyber Threat Intelligence
Cyber Threat Intelligence has become a cornerstone of modern cybersecurity strategies, offering diverse applications to safeguard organizations against evolving threats. Key applications include:
- Enhancing Threat Detection: By leveraging threat intelligence, organizations can identify patterns and indicators that signify malicious activities. This enables early detection and allows security teams to act before significant damage occurs.
- Optimizing Security Operations: CTI provides valuable context to security alerts, reducing false positives and enabling Security Operations Centers (SOCs) to prioritize genuine threats effectively. This improves operational efficiency and prevents alert fatigue among analysts.
- Incident Response and Recovery: Timely intelligence enhances an organization’s ability to respond to incidents swiftly and effectively. It provides critical information about the nature of the attack, the methods used, and potential remediation steps.
- Vulnerability Management: CTI helps identify vulnerabilities that are actively being exploited in the wild. This allows organizations to prioritize patching efforts, ensuring that critical weaknesses are addressed first.
- Third-Party Risk Management: By assessing and monitoring the cybersecurity posture of third-party vendors and partners, CTI helps organizations identify risks stemming from their supply chain.
- Protecting Intellectual Property: CTI enables organizations to monitor underground markets and forums for signs of intellectual property theft or counterfeit products, helping protect their brand and reputation.
- Securing Remote Work Environments: With the rise of remote work, CTI helps detect potential risks associated with distributed networks and ensures that employees’ endpoints are secure against emerging threats.
- Regulatory Compliance: Organizations can use CTI to meet compliance requirements by demonstrating proactive measures to identify and mitigate threats, ensuring adherence to industry standards and regulations.
- Cybersecurity Training and Awareness: Threat intelligence provides real-world examples of attacks and threat actor behavior, which can be used to educate employees and improve their ability to recognize and respond to threats.
- Strategic Planning and Investment: High-level intelligence informs decision-makers about long-term trends in the threat landscape, helping organizations plan their cybersecurity investments more effectively and allocate resources to critical areas.
Why SOCRadar is a Game-Changer in Cyber Threat Intelligence?
SOCRadar goes a step further by incorporating proactive threat hunting. This approach helps organizations detect advanced threats or malicious activities before they impact critical systems. With a proactive strategy, businesses can address potential vulnerabilities early and reduce the risk of successful attacks.
In essence, SOCRadar’s integrated platform is a game-changer for organizations seeking to enhance their cybersecurity posture by providing timely, actionable intelligence that helps defend against emerging threats.
SOCRadar stands out as a comprehensive cyber threat intelligence platform designed to empower organizations with actionable insights. Its key offerings include:
- Threat Actor Monitoring: Real-time tracking of threat actor activities across the surface, deep, and dark web.
- Attack Surface Management: Identifying vulnerabilities and weak points in an organization’s digital footprint.
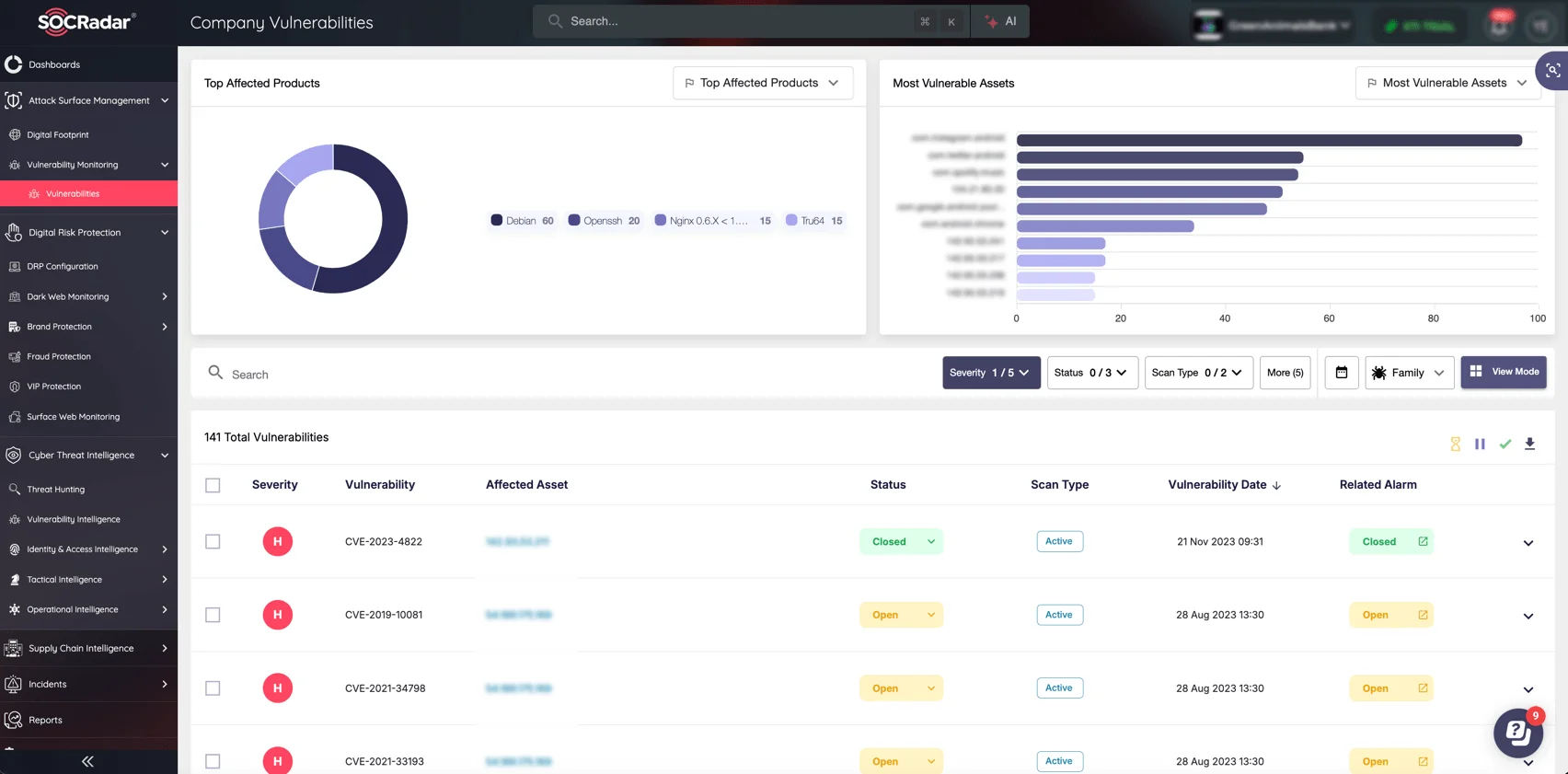
SOCRadar Attack Surface Management module
- Dark Web Monitoring: Scanning underground forums, marketplaces, and chat platforms for potential threats.
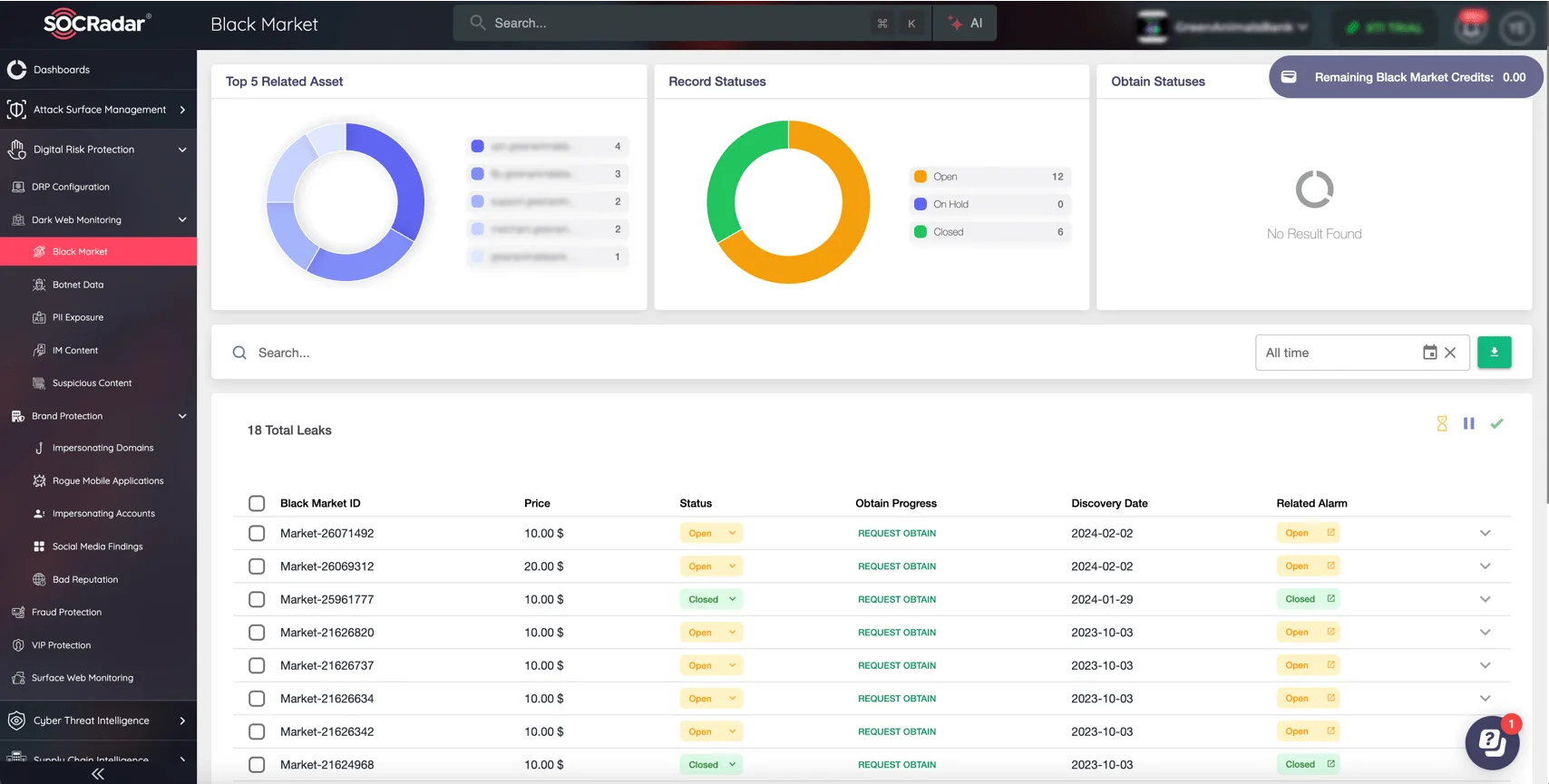
SOCRadar Dark Web Monitoring module
- Early Warning System: Providing alerts for imminent threats tailored to the organization’s industry and geography.
- Collaboration and Sharing: Enabling organizations to share intelligence securely and collaborate on mitigation strategies.
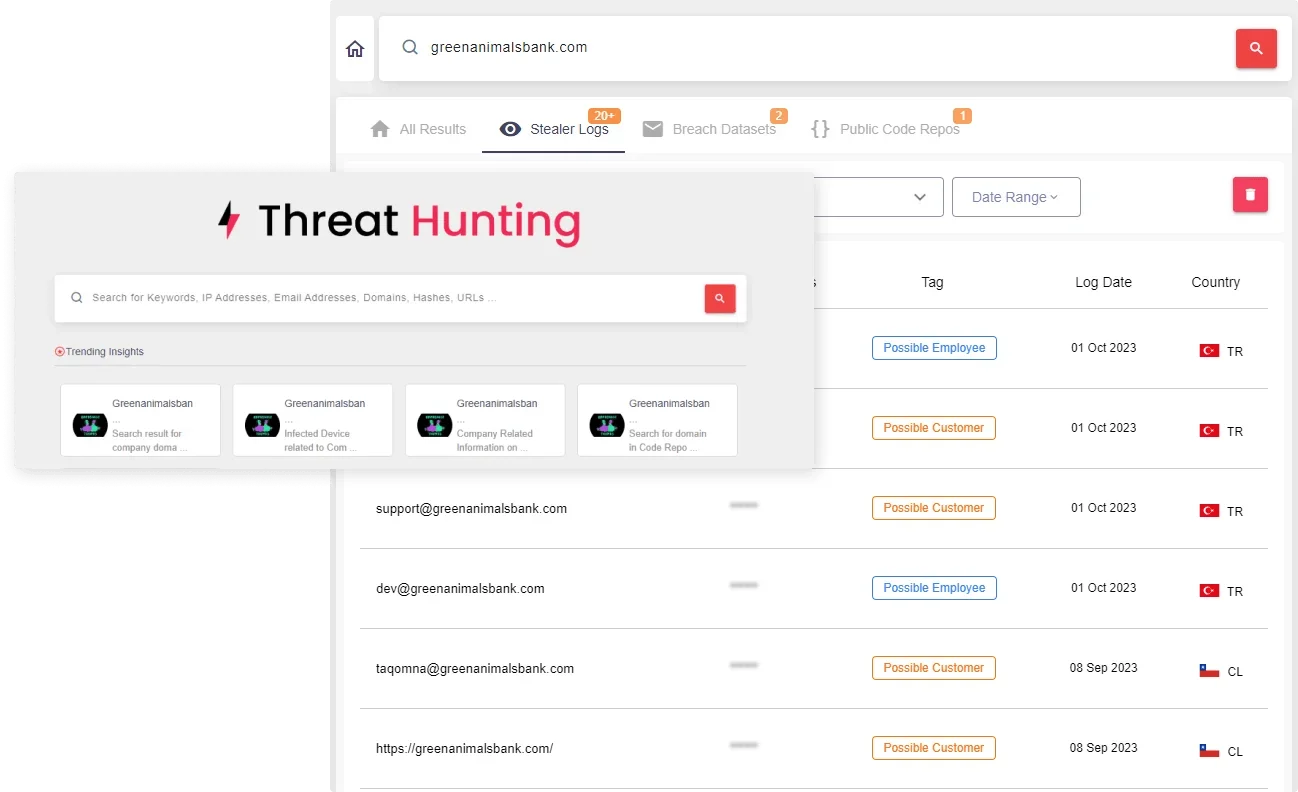
One step further, detect advanced threats or malicious activities with proactive threat hunting
SOCRadar’s integrated approach combines advanced analytics, machine learning, and a rich repository of threat data to deliver actionable intelligence that helps businesses proactively defend against cyber adversaries.
In Summary
Cyber Threat Intelligence is no longer optional for organizations aiming to stay ahead of cyber adversaries. By leveraging actionable intelligence, businesses can proactively defend against emerging threats, optimize their security operations, and enhance their resilience. In a world where cyber threats constantly evolve, CTI serves as a vital shield against potential attacks.




































