
What You Need to Know About STIX and TAXII?
STIX and TAXII were developed to improve cyber threat detection and mitigation. STIX stipulates the details of the threat, while TAXII decides the flow of information. STIX and TAXII are machine-readable and thus conveniently automated, unlike previous sharing methods. They can easily be integrated into systems.
STIX/TAXII is an open, community-driven endeavor, with free guidance to enable the automatic expression of cyber threats.
What’s structured threat information expression (STIX)?
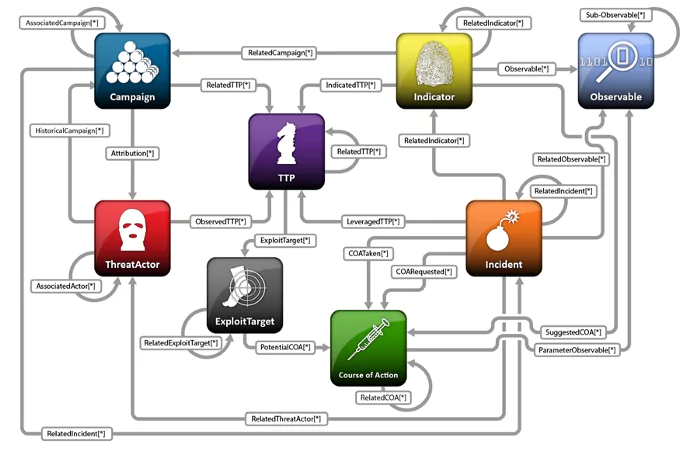
STIX is a standard for defining threat information including threat details with the context of the threat which was first presented in 2012. Describes cyber threat information. It uses cases such as Analyzing Cyber Threats, Specifying Indicator Patterns for Cyber Threats, Managing Cyber Threat Prevention and Response Activities, Sharing Cyber Threat Information. STIX provides a unifying architecture (shown in figure 1[1]) tying together a diverse set of cyber threat information along with:
- Cyber Observables (e.g., a registry key is created, network traffic occurs to specific IP addresses, email from a specific address is observed, etc.).
- Indicators (potential observables with attached meaning and context).
- Incidents (instances of specific adversary actions).
- Adversary Tactics, Techniques, and Procedures (including attack patterns, malware, exploits, kill chains, tools, infrastructure, victim targeting, etc.).
- Exploit Targets (e.g., vulnerabilities, weaknesses, or configurations).
- Courses of Action (e.g., incident response or vulnerability/ weakness remedies).
- Cyber Attack Campaigns (sets of Incidents and/or TTP with a shared intent).
- Cyber Threat Actors (identification and/or characterization of the adversary.
How to use STIX?
STIX Objects categorize each piece of information with specific attributes to be populated. Chaining multiple objects together through relationships allow for easy or complex representations of CTI. Below is a list of what can be represented through STIX.
STIX 2.1 defines 18 STIX Domain Objects (SDOs):
| Object | Name | Description |
|---|---|---|
 |
Attack Pattern | A type of TTP that describes ways that adversaries attempt to compromise targets. |
 |
Campaign | A grouping of adversarial behaviors that describes a set of malicious activities or attacks (sometimes called waves) that occur over a period of time against a specific set of targets. |
 |
Course of Action | A recommendation from a producer of intelligence to a consumer on the actions that they might take in response to that intelligence. |
 |
Grouping | Explicitly asserts that the referenced STIX Objects have a shared context, unlike a STIX Bundle (which explicitly conveys no context). |
 |
Identity | Actual individuals, organizations, or groups (e.g., ACME, Inc.) as well as classes of individuals, organizations, systems, or groups (e.g., the finance sector). |
 |
Indicator | Contains a pattern that can be used to detect suspicious or malicious cyber activity. |
 |
Infrastructure | Represents a type of TTP and describes any systems, software services, and any associated physical or virtual resources intended to support some purpose (e.g., C2 servers used as part of an attack, device or server that are part of the defense, database servers targeted by an attack, etc.). |
 |
Intrusion Set | A grouped set of adversarial behaviors and resources with common properties is believed to be orchestrated by a single organization. |
 |
Location | Represents a geographic location. |
 |
Malware | A type of TTP that represents malicious code. |
 |
Malware Analysis | The metadata and results of a particular static or dynamic analysis performed on a malware instance or family. |
 |
Note | Conveys informative text to provide further context and/or to provide additional analysis not contained in the STIX Objects, Marking Definition objects, or Language Content objects which the Note relates to. |
 |
Observed Data | Conveys information about cybersecurity-related entities such as files, systems, and networks using the STIX Cyber-observable Objects (SCOs). |
 |
Opinion | An assessment of the correctness of the information in a STIX Object produced by a different entity. |
 |
Report | Collections of threat intelligence focused on one or more topics, such as a description of a threat actor, malware, or attack technique, including context and related details. |
 |
Threat Actor | Actual individuals, groups, or organizations believed to be operating with malicious intent. |
 |
Tool | Legitimate software that can be used by threat actors to perform attacks. |
 |
Vulnerability | A mistake in software that can be directly used by a hacker to gain access to a system or network. |
STIX 2 defines two STIX Relationship Objects (SROs):
| Object | Name | Description |
|---|---|---|
 |
Relationship | Used to link together two SDOs or SCOs in order to describe how they are related to each other. |
 |
Sighting | Denotes the belief that something in CTI (e.g., an indicator, malware, tool, threat actor, etc.) was seen. |
What’s trusted automated exchange of indicator information (TAXII)?
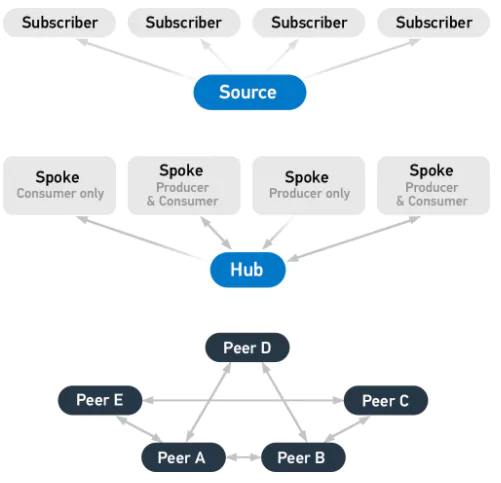
TAXII is a set of services and message exchanges for exchanging cyber threat information. Defines how cyber threat information can be shared. It utilizes a standardized cyber threat information representation and defines a supporting exchange framework. Multiple sharing models are supported by TAXII such as hub and spoke, peer to peer, source/subscriber. Four core services support the model like discovery, feed management, inbox, and poll. XML and HTTP are used by TAXII for transporting messages and their context. TAXII also has been adopted as part of the Microsoft Active Protections Program (MAPP).
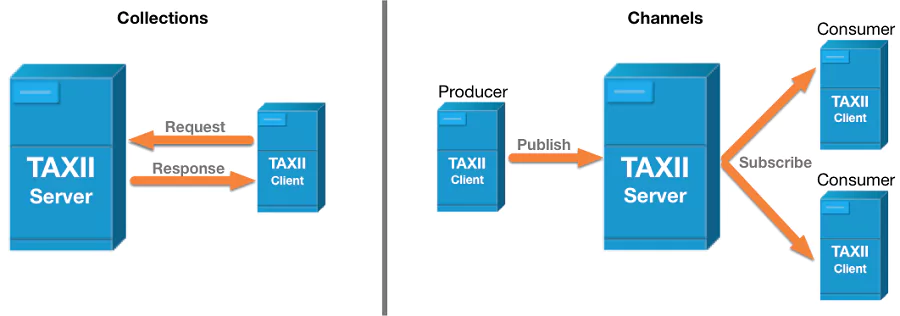
As depicted in figure 2[2], TAXII defines two primary services to support a variety of common sharing models:
- Collection: A Collection is an interface to a logical repository of CTI objects provided by a TAXII Server that allows a producer to host a set of CTI data that can be requested by consumers: TAXII Clients and Servers exchange information in a request-response model.
- Channel: Maintained by a TAXII Server, a Channel allows producers to push data to many consumers and consumers to receive data from many producers: TAXII Clients exchange information with other TAXII Clients in a publish-subscribe model. Note: The TAXII 2.1 specification reserves the keywords required for Channels but does not specify Channel services. Channels and their services will be defined in a later version of TAXII.
TAXII defines four services;
- Discovery: a way to learn what services an entity supports and how to interact with them
- Collection Management: a way to learn about and request subscriptions to data collections
- Inbox: a way to receive content (push messaging)
- Poll: a way to request content (pull messaging)
The three principal models for TAXII include:
- Hub and spoke: one repository of information
- Source/subscriber: one single source of information
- Peer-to-peer: multiple groups share information
Why do we need STIX/TAXII?
Standards such as STIX and TAXII enable effective sharing of cyber threat intelligence in automated ways between different products, people, and organizations. They also help security professionals to communicate and share information more effectively that also increases the power of defense.
What are the benefits of using STIX/TAXII?
STIX 2 describes cyber threat intelligence in a repeatable way that both users and machines understand. TAXII 2 provides the ability for you to share timely intelligence with relevant user groups in a standardised format.
Both STIX 2 and TAXII 2 help you to reduce manual administration of cyber threat intelligence.
- The STIX 2 format reduces the need for you to create documents in multiple formats
- TAXII 2 reduces the need for you to distribute information by email
Wider use of these standards makes it easier to share analysis of threat intelligence.
These standards provide a way to link indicators of compromise (evidence of a cyber attack) to tactics, techniques and procedures (the techniques regularly used by threat actors or groups of threat actors). This will allow you to:
- Identify the source of a cyber attack
- Increase the view of the threats your organisation faces
- Link previously un-associated events
These standards increase levels of automation but should not replace user interaction, as full automation risks creating a self-inflicted denial of service.
What are the use cases for STIX/TAXII?
The STIX Language is targeted to support a range of core use cases involved in cyber threat management, including analyzing cyber threats, specifying indicator patterns, managing response activities, and sharing cyber threat information.
Analyzing cyber threats
A cyber threat analyst reviews structured and unstructured information regarding cyber threat activity from a variety of manual or automated input sources. The analyst seeks to understand the nature of relevant threats, identify them, and fully characterize them such that all of the relevant knowledge of the threat can be fully expressed and evolved over time. This relevant knowledge includes threat-related actions, behaviors, capabilities, intents, attributed actors, etc. From this understanding and characterization, the analyst may then specify relevant threat indicator patterns, suggest courses of action for threat response activities, and/or share the information with other trusted parties.
Example: In the case of a potential phishing attack, a cyber threat analyst may analyze and evaluate a suspected phishing email, analyze any email attachments and links to determine if they are malicious, determine if the email was sent to others, assess the commonality of who/what is being targeted in the phishing attack, determine whether malicious attachments were opened or links followed, and keep a record of all analysis performed.
Specifying indicator patterns for cyber threats
A cyber threat analyst specifies measurable patterns representing the observable characteristics of specific cyber threats along with their threat context and relevant metadata for interpreting, handling, and applying the pattern and its matching results. This may be done manually or with the assistance of automated tooling and structured instantiate threat information.
Example: In the case of a confirmed phishing attack, a cyber threat analyst may harvest the relevant set of observables (e.g., to or from addresses, actual source, subject, embedded URLs, type of attachments, specific attachment, etc.) from the performed analysis of the phishing email, identify the relevant TTPs exhibited in the phishing attack, perform kill chain correlation of the attack, assign appropriate confidence for the indicator, determine appropriate handling guidance, generate any relevant automated rule patterns for the indicator (e.g., Snort, YARA, OVAL, etc.), assign any suggested courses of action, and package it all up as a coherent record for sharing (i.e., Sharing Cyber Threat Information) and future reference.
Managing cyber threat response activities
Cyber decision-makers and cyber operations personnel work together to prevent or detect cyber threat activity and to investigate and respond to any detected incidences of such activity. Preventative courses of action may be remedial in nature to mitigate vulnerabilities, weaknesses, or misconfigurations that may be targets of exploit. After detection and investigation of specific incidents, reactive courses of action may be pursued.
Example: In the case of a confirmed phishing attack with defined indicators, cyber decision makers and cyber operations personnel work together to fully understand the effects of the phishing attack within the environment including malware installed or malware executed, to assess the cost and efficacy of potential courses of action, and to implement appropriate preventative or detective courses of action.
Cyber threat prevention
Cyber decision makers evaluate potential preventative courses of action for identified relevant threats and select appropriate actions for implementation. Cyber operations personnel implement selected courses of action in order to prevent the occurrence of specific cyber threats whether through general prophylactic application of mitigations or through specific targeted mitigations initiated by predictive interpretation of leading indicators.
Example: In the case of a confirmed phishing attack with defined indicators, a cyber decision maker may evaluate a suggested preventative course of action (e.g., implementing a blocking rule at the email gateway) defined within an indicator for the phishing attack, determine its relevant cost and risk, and decide whether or not to implement it. If it is decided to implement the suggested course of action, cyber operations personnel carry out the implementation.
Cyber threat detection
Cyber operations personnel apply mechanisms (both automated and manual) to monitor and assess cyber operations in order to detect the occurrence of specific cyber threats whether in the past through historical evidence, currently ongoing through dynamic situational awareness, or apriori through predictive interpretation of leading indicators. This detection is typically via cyber threat indicator patterns.
Example: In the case of a confirmed phishing attack with defined indicators, cyber operations personnel may harvest any specified observable patterns from defined indicators of the attack and apply them appropriately within the operational environment to detect any evidence of the phishing attack occurring.
Incident response
Cyber operations personnel respond to detections of potential cyber threats, investigate what has occurred or is occurring, attempt to identify and characterize the nature of the actual threat, and potentially carry out specific mitigating or corrective courses of action.
Example: In the case of a confirmed phishing attack, cyber operations personnel may conduct investigative activities to determine whether the phishing attack was successful in carrying out negative effects within the target environment (e.g., was malware installed or run) and if so, attempt to characterize in detail those effects (e.g., which systems were affected by malware, what data was exfiltrated, etc.). Once the effects are understood, cyber operations personnel would implement appropriate mitigating or corrective courses of action (e.g., wipe and restore systems, block exfil channels, etc.).
Sharing cyber threat information
Cyber decision-makers establish policy for what sorts of cyber threat information will be shared with which other parties and how it should be handled based on agreed to frameworks of trust in such a way as to maintain appropriate levels of consistency, context, and control. This policy is then implemented to share the appropriate cyber threat indicators and other cyber threat information.
Example: In the case of a confirmed phishing attack with defined indicators, the policies predefined by cyber decision-makers could enable the relevant indicators to be automatically or manually shared with trusted partners or communities such that they could take advantage of the knowledge gained by the sharing organization.
What are the online STIX/TAXII resources?
Overviews
Free STIX/TAXII tools
What are the STIX/TAXII open-source projects?
- Carbon Black Enterprise Response STIX/TAXII Connector: VMware Carbon Black EDR connector for pulling and converting STIX information from TAXII Service Providers into EDR Feeds.
- Cabby: Python TAXII client implementation from EclecticIQ.
- MISP – Threat Intelligence Sharing Platform: MISP allows organizations to share, store, and correlate information about malware and threats and their indicators, including STIX export.
- Ce1sus: Ce1sus is an open source threat information database based on STIX. When the development of Ce1sus started there were not many tools available to store Indicators of compromise (IOCs) available. Moreover the shared IOCs were received in many different formats, and often there was no real context given.
- FLAREclient: FLARE is used for exchanging messages in a publish/subscribe model, and includes support for STIX and TAXII.
- FreeTAXII: A TAXII client, server and APIs for generating TAXII messages to share Cyber Threat Intelligence.
- Pan-stix: A package to convert Palo Alto Networks threat information into STIX/MAEC format.
SOCRadar ThreatFusion
ThreatFusion provides a big-data powered threat investigation module to help Threat Intelligence Teams searching for deeper context, real-time threat research and analysis. The suite is fed by massive data sources across surface, deep and dark web from Paste Sites to Underground Dark Web forums. The module also includes API-ready intelligence feeds pulled from a broad variety of sources to provide IOCs of potential threats and threat actors targeting your industry.
SOCRadar ThreatFusion enables to define and share threats in STIX and TAXII format to make it much easier for your organization. Want to know more about it? Click here
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.



































