
Who Is the BlackByte Ransomware Group and How Does the Decryptor Works?
Ransomware attacks impact organizations every single day. But it doesn’t always have to be bad news. Victims of BlackByte ransomware can now decrypt and get back their files as a free decryption tool has just been made public this week.
In this blog post you will find information about the ransomware group BlackByte, which has victims in many countries, and how to use the latest released decryptor.
Who is BlackByte?
BlackByte is a ransomware operation that began targeting corporate victims worldwide in July 2021. The first findings regarding this group emerged after victims sought help decrypting their files.
In C#, BlackByte attempts to terminate numerous security, mail server, and database processes to encrypt a device successfully. The BlackByte ransomware group disables Microsoft Defender on target devices before attempting encryption.
According to the information reported so far, BlackByte was not as active as other ransomware operations, but the researchers’ eyes were on it.
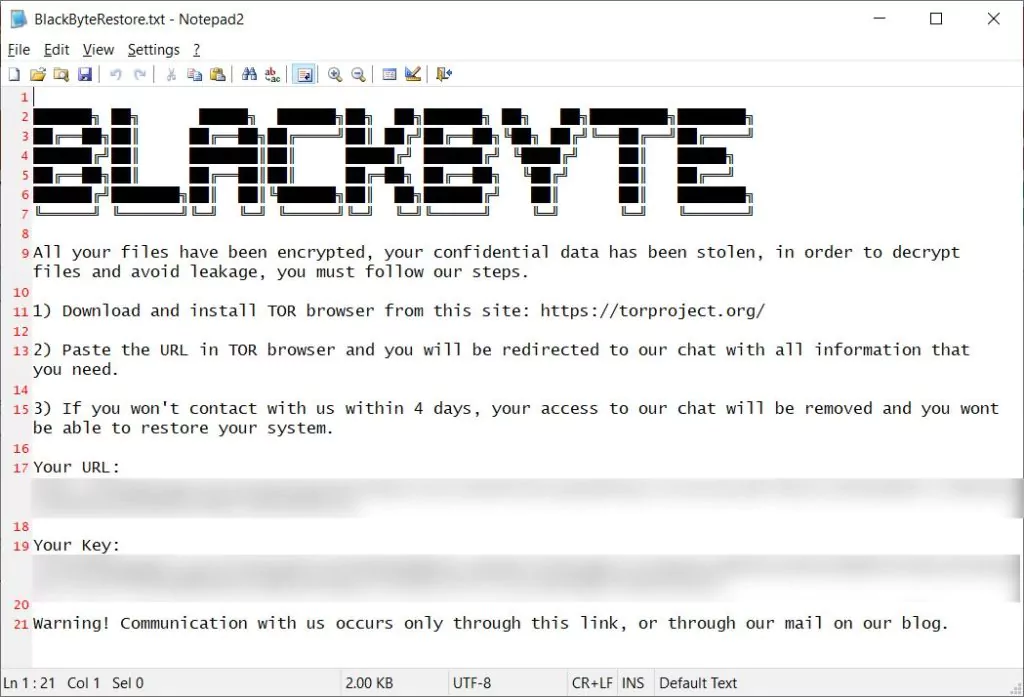
BlackByte ransomware decryptor released
This week, researchers working at a cybersecurity company have released a free decryptor that victims of the BlackByte ransomware can use to restore their files. The free tool is available on GitHub.
Researchers said this process was rather simplistic than the more complex and more secure encryption routines used by other gangs. The ransomware fetches a .PNG file that contains multiple keys, which researchers used to create the decryptor.
After the release of the decryptor, some researchers observed this file, which dissolved Black Byte. According to detailed analyses, the ransomware downloaded a file called ‘forest.png’ from a remote site under their control. Although this file is named to appear as an image file, it contains the AES encryption key used to encrypt a device.
According to the researchers, because BlackByte uses AES symmetric encryption, the same key is used to encrypt and decrypt files.
In the warning message published on the BlackByte Blog, monitored by SOCRadar analysts, threat actors stated they had encountered a decryptor for ransomware. Threat actors also claim that some systems will irreversibly fail if decrypted incorrectly.
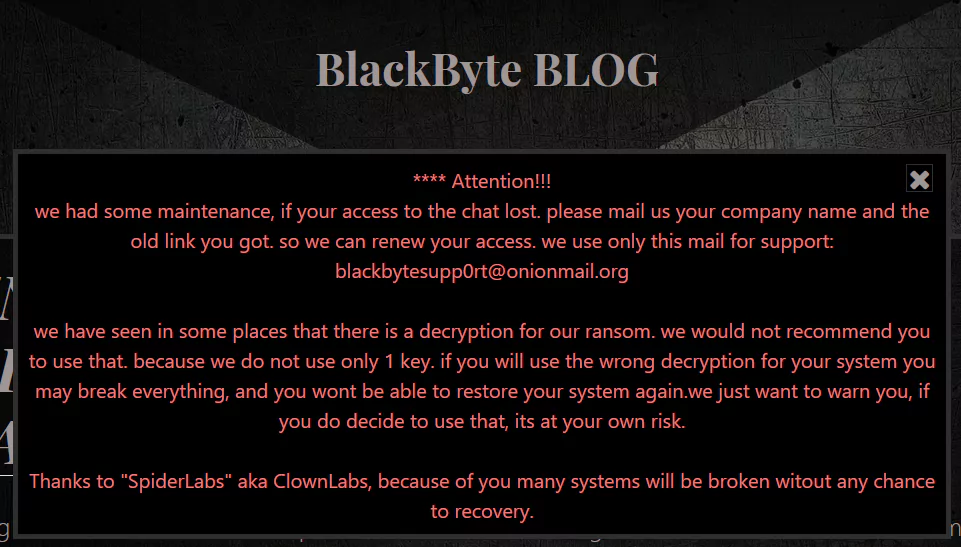
The group also stated that they do not use a single symmetric encryption key as suggested in the research but organize attacks with multiple encryption keys.
When the BlackByte ransomware gang became aware of the researchers’ report and decryption tool, they cautioned that they had used multiple keys and that utilizing the decryptor with the wrong key might damage the victim’s files.
BlackByte software also disables Microsoft Defender software before encrypting files on targeted systems. Also, like RYUK, it has a wormable feature that can infect another from the infected system.
SOCRadar analysts found that the BlackByte group has reduced its time to pay the ransom from 30 days to 12 days.
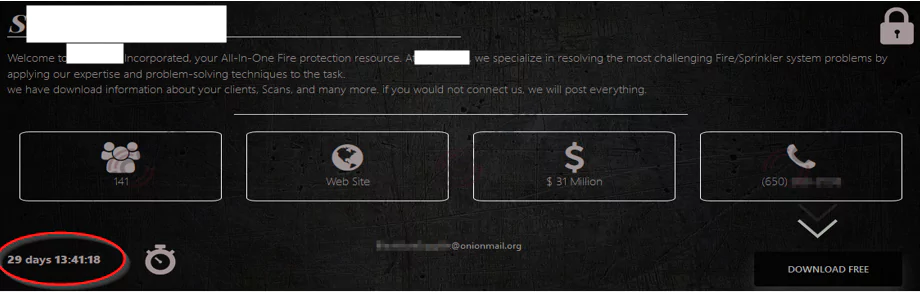
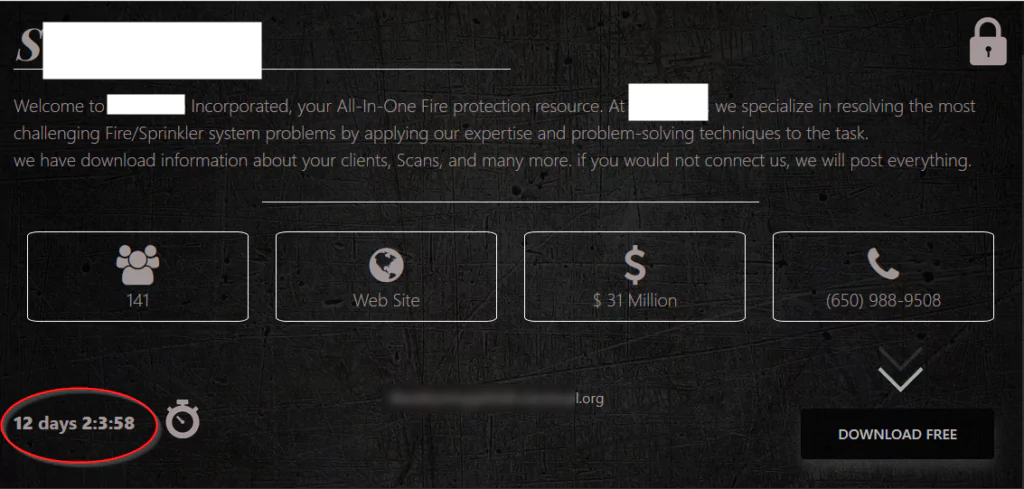
Which Companies Did BlackByte Ransomware Target?
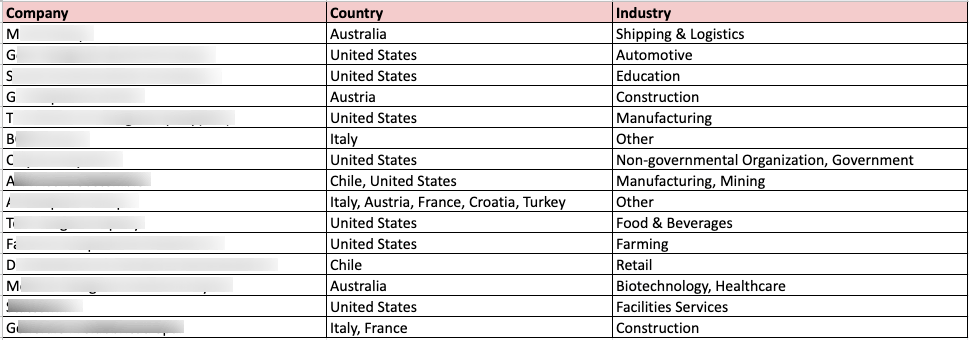
According to information obtained by SOCRadar, the BlackByte ransomware group has so far attacked companies in the manufacturing, mining, food, beverage, healthcare, and construction sectors from the USA, France, Australia, Italy, Austria, Croatia, Chile, and Turkey.
What Can You Do If You Are a Victim of BlackByte?
If you are a BlackByte victim and want to use a decryptor, you will need to download the source code from Github and compile it yourself.
While researchers have included a default ‘forest.png’ file that will be used to extract the decryption key, it may be possible that BlackByte rotated the encryption keys downloaded in that file. Due to this, it is strongly advised that your backup files before attempting to decrypt them.
Furthermore, if you have a ‘forest.png’ file on an encrypted device, you should use that file rather than the one bundled with the decryptor.
You can also follow these tips to avoid BlackByte and other ransomware gangs:
- Ransomware threats often exploit known vulnerabilities. Therefore, robust patch management procedures need to be implemented to secure exposed infrastructure.
- Unusual behavior such as endpoint security events and excessive file operations must be continuously monitored to identify a security breach early.
- Sensitive data should be adequately secure, such as through the use of encryption or additional controls by any legal or regulatory requirements.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































