
Workarounds for Microsoft Office Zero-Day RCE Vulnerability “Follina” has Released
The Follina zero-day vulnerability in Microsoft Office allows threat actors to perform remote code execution. Cybersecurity researchers discovered the vulnerability when the Word document “05-2022-0438.doc” was uploaded to VirusTotal from an IP address in Belarus.
Microsoft Windows Support Diagnostic Tool (MSDT) RCE vulnerability with code CVE-2022-30190 is risky with a CVSS score of 7.8.
PoC on GitHub
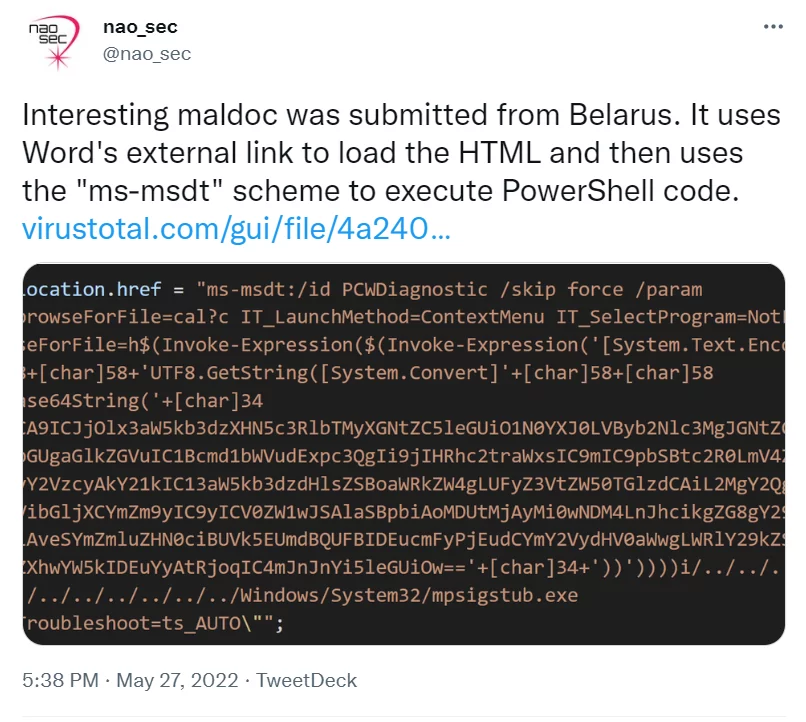
According to Kevin Beaumont, who named the vulnerability “Follina” because “0438” at the end of the malicious Word file is the area code for the municipality of Follina in Treviso, Italy, the Word document uses the remote template feature to retrieve an HTML file from a remote server. It uses the ms-msdt MSProtocol URI scheme to load some code and execute PowerShell.
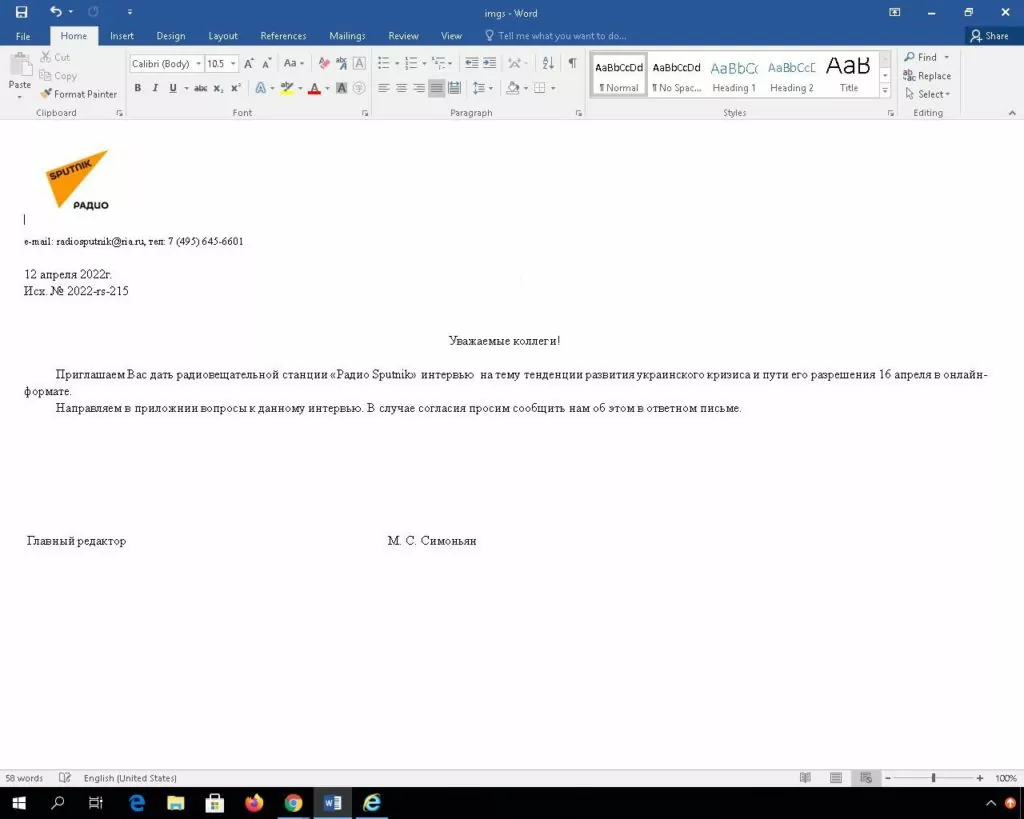
Beaumont says the vulnerability goes back more than a month. Underlining that the Word file named “interview invitation” targeting a user in Russia under the name of Sputnik Radio was uploaded to VirusTotal, the researcher states that this document directly exploits the Follina vulnerability.
In Microsoft’s statement, threat actors who exploit the vulnerability gain opportunities such as RCE, installing random programs, being able to view, modify or delete data, and creating new accounts.
The PoC on the actively exploited Follina zero-day vulnerability has also been published. You can find the relevant repository on GitHub here.
Microsoft Releases Workarounds for Follina Vulnerability
Microsoft has released additional guidance to mitigate the vulnerability affecting Office 2013, 2016, 2019, 2021, and Professional Plus versions. Customers are strongly encouraged to follow the precautions suggested in this guide.
Additionally, customers can implement Microsoft Attack Surface Reduction measures.
Cybersecurity researcher Florian Roth and his team also created YARA rules to detect some documents exploiting the Follina vulnerability and shared it on Roth’s Twitter account.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.




































