
X Faces Cyberattack: Dark Storm Team Takes Credit, Musk Blames Ukraine
Yesterday, X (formerly Twitter) allegedly suffered a large-scale cyberattack, causing widespread outages. While Elon Musk claimed the attack was linked to Ukraine, but the pro-Palestinian and pro-Russian hacker group Dark Storm Team stepped forward, taking responsibility.
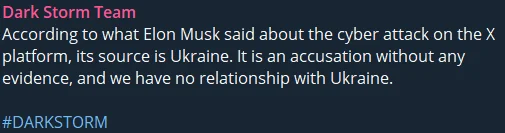
This contradiction adds to the confusion surrounding the incident—Musk blames Ukraine, yet a group with pro-Russian ties claims credit. Whether this is a deliberate misdirection, multiple actors working toward the same goal, or an entirely different player using Dark Storm as a cover remains unclear.
A Coordinated DDoS Attack Disrupts X
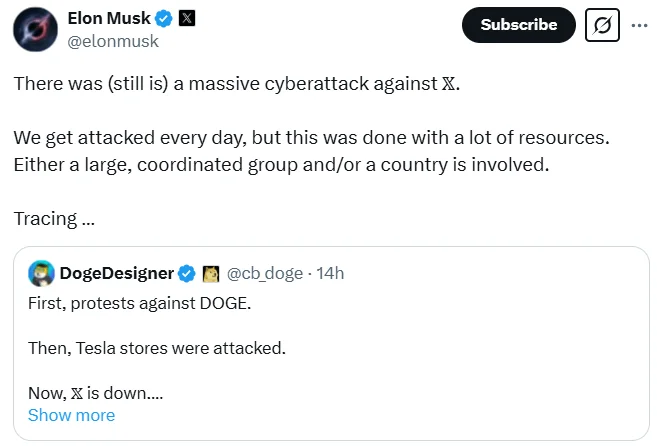
Users worldwide reported issues accessing X, with pages failing to load and services becoming unresponsive. Musk later confirmed the platform was under a Distributed Denial-of-Service (DDoS) attack, describing it as an operation requiring “vast resources” and suggesting that a “large, coordinated group and/or a country” was behind it.
Elon Musk’s X post
He later pointed to “IP addresses in the Ukraine area” as the origin of the attack. However, cybersecurity experts caution that IP-based attribution is unreliable, as attackers frequently use proxies or compromised servers to mislead investigators.
Dark Storm’s Telegram post
Who is the Dark Storm Team?
Shortly after Musk’s statement, Dark Storm Team, a hacker group with a pro-Palestinian stance, claimed responsibility. Active since 2023, the group has previously targeted entities in Israel, NATO-aligned nations, and Western companies.
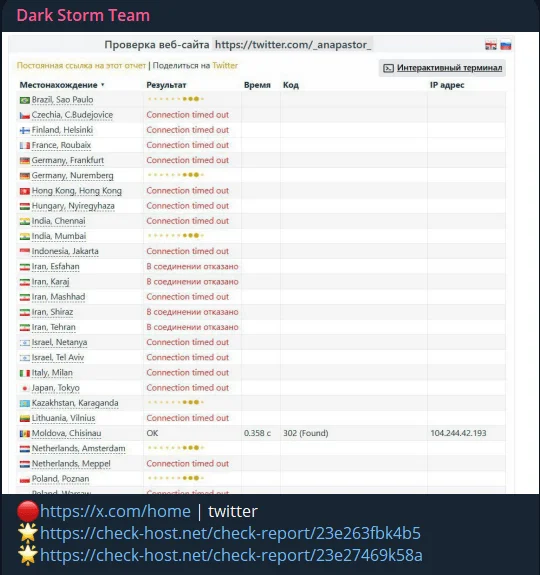
Dark Storm’s Telegram post, check-host.net is a platform that enables users to test a website’s availability from various servers across the globe.
Dark Storm operates primarily through Telegram, where they posted screenshots and technical details allegedly proving their involvement in the attack. However, their claim raises questions—was this a solo operation, or were other actors involved? And if Musk’s attribution to Ukraine holds weight, could there be a more complex network behind the attack?
A Telegram channel post of Dark Storm Team
Thus, here is the thing with many hacktivist groups, Dark Storm Team’s statements should be taken with a grain of salt. They have a track record of targeting social media platforms while providing little concrete evidence. Additionally, the group has been known to generate mass attention to promote their DDoS tools and push their cryptocurrency projects.
Attribution Challenges
This incident underscores the growing risks major platforms face as cyberattacks become more politically motivated. The conflicting claims—Dark Storm’s self-attribution versus Musk’s Ukraine accusations—highlight the difficulties in determining the true origins of an attack.
In response, X has strengthened its defenses, reportedly implementing additional DDoS protection through Cloudflare. Meanwhile, cybersecurity researchers continue to investigate.
With hacktivist groups and potential state-backed actors increasingly targeting high-profile platforms, this attack serves as another reminder of the evolving threat landscape and the urgent need for stronger cyber defenses.
Tracking Threat Actors with SOCRadar
In cases like this, where attribution is murky and multiple narratives emerge, platforms like SOCRadar and its Threat Actor Intelligence and Dark Web Monitoring play a crucial role.
SOCRadar continuously tracks cybercriminal groups, including hacktivist collectives like Dark Storm Team, providing real-time insights into their activities, tactics, and underground discussions.
By monitoring deep and dark web forums, Telegram channels, and illicit marketplaces, SOCRadar helps organizations stay ahead of emerging threats, assess the credibility of attack claims, and mitigate risks before they escalate.



































